Powerpoint Templates and Google slides for Vulnerabilities
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Selecting secured threat management managing critical threat vulnerabilities and security threats
Selecting secured threat management managing critical threat vulnerabilities and security threatsThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Security Incident, Automated Workflows, Access Rights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics associated to workplace managing critical threat vulnerabilities and security threats
Statistics associated to workplace managing critical threat vulnerabilities and security threatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Increase audience engagement and knowledge by dispensing information using Statistics Associated To Workplace Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on five stages. You can also present information on Cyber Attacks Cost, Organizations Face, Data Records using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table of contents managing critical threat vulnerabilities and security threats
Table of contents managing critical threat vulnerabilities and security threatsIntroducing Table Of Contents Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario Assessment, Digital Assets, Physical Security, using this template. Grab it now to reap its full benefits.
-
 Technological assessment of managing critical threat vulnerabilities and security threats
Technological assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Technological Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Industry Standard, Firms Standard, Customer Satisfaction Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management action managing critical threat vulnerabilities and security threats
Threat management action managing critical threat vulnerabilities and security threatsThe threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an outstanding presentation on the topic using this Threat Management Action Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Threat Identification, Threat Treatment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various types of workplace violence managing critical threat vulnerabilities and security threats
Various types of workplace violence managing critical threat vulnerabilities and security threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Workplace Violence Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on six stages. You can also present information on Threatening Behavior Stalking, Physical Assault, Harassment And Intimidation, Property Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace employee assistance managing critical threat vulnerabilities and security threats
Workplace employee assistance managing critical threat vulnerabilities and security threatsThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Workplace Employee Assistance Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Clinical Services, Online Resources, Offline Resources, Employer Services, using this template. Grab it now to reap its full benefits.
-
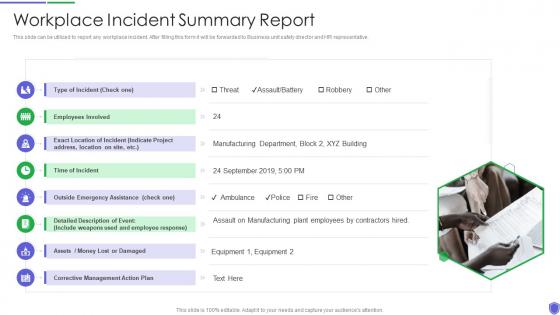 Workplace incident summary managing critical threat vulnerabilities and security threats
Workplace incident summary managing critical threat vulnerabilities and security threatsThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Increase audience engagement and knowledge by dispensing information using Workplace Incident Summary Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on one stages. You can also present information on Employees, Corrective Management, Time Of Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat vulnerability asset matrix managing cyber risk in a digital age
Threat vulnerability asset matrix managing cyber risk in a digital ageMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Threat Vulnerability Asset Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operating System Vulnerabilities Ppt Powerpoint Presentation Inspiration Template Cpb
Operating System Vulnerabilities Ppt Powerpoint Presentation Inspiration Template CpbPresenting our Operating System Vulnerabilities Ppt Powerpoint Presentation Inspiration Template Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operating System Vulnerabilities This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk threat vulnerability ppt powerpoint presentation portfolio graphics design cpb
Risk threat vulnerability ppt powerpoint presentation portfolio graphics design cpbPresenting our Risk Threat Vulnerability Ppt Powerpoint Presentation Portfolio Graphics Design Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Risk Threat Vulnerability. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Improve it security with vulnerability management how siem works
Improve it security with vulnerability management how siem worksIncrease audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management How Siem Works. This template helps you present information on four stages. You can also present information on Databases, Applications, Security Device using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key vulnerabilities that ethical hackers check ppt outline graphics template
Key vulnerabilities that ethical hackers check ppt outline graphics templateThis slide describes the critical vulnerabilities that ethical hackers check, such as injection attacks, modification in security configuration, exposure of critical information, and so on. Introducing Key Vulnerabilities That Ethical Hackers Check Ppt Outline Graphics Template to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Injection Attacks, Authentication Standard Breach, Exposure Of Critical Information, Modification In Security Configurations, using this template. Grab it now to reap its full benefits.
-
 Hazard Vulnerability Analysis Ppt Powerpoint Presentation Ideas Display Cpb
Hazard Vulnerability Analysis Ppt Powerpoint Presentation Ideas Display CpbPresenting Hazard Vulnerability Analysis Ppt Powerpoint Presentation Ideas Display Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Hazard Vulnerability Analysis. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Targeting Vulnerable Consumers For Fulfilling Requirements
Targeting Vulnerable Consumers For Fulfilling RequirementsThis slide covers targeting vulnerable consumers for fulfilling requirements which includes understand need of vulnerable customers, skill with capability and taking practical action Introducing our premium set of slides with Targeting Vulnerable Consumers For Fulfilling Requirements. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerable Customers, Capability Of Staff, Practical Action. So download instantly and tailor it with your information.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria
Risk Management Framework For Information Security Defining Vulnerability Rating With CriteriaFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria. Use it as a tool for discussion and navigation on Vulnerability Ranking, Organization, High, Low, Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Threat Identification And Vulnerability
Risk Management Framework For Information Security Threat Identification And VulnerabilityFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Threat Identification And Vulnerability. Dispense information and present a thorough explanation of Communication And Network, Database, Failure To Segment Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework Defining Vulnerability Rating
Cybersecurity Risk Management Framework Defining Vulnerability RatingFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Defining Vulnerability Rating. Dispense information and present a thorough explanation of Occurrence Attack, Asset Moderately Susceptible, Asset Highly Susceptible using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
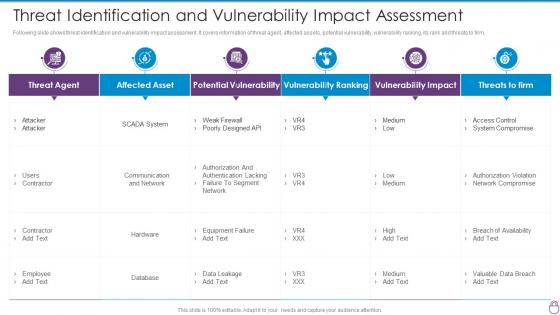 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Vulnerability Asset Matrix Risk Based Methodology To Cyber
Threat Vulnerability Asset Matrix Risk Based Methodology To CyberMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least.Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Social Engineering, Ranked Critical Resources, Present IT Safeguards This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security
Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least.Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on System Redundancy, Incident Response Plan, Security Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise vulnerability management determine tools aligned to the strategy
Enterprise vulnerability management determine tools aligned to the strategyIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Determine Tools Aligned To The Strategy. This template helps you present information on five stages. You can also present information on Publish Authorized, Exception Process, Conduct Periodic Reviews using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise vulnerability management develop a plan revision process
Enterprise vulnerability management develop a plan revision processIntroducing Enterprise Vulnerability Management Develop A Plan Revision Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Review The Changes, Vulnerability Information, Update Toolset If Necessary, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management icons slide
Enterprise vulnerability management icons slideIntroducing our well researched set of slides titled Enterprise Vulnerability Management Icons Slide. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Enterprise vulnerability management identify sources of vulnerability information
Enterprise vulnerability management identify sources of vulnerability informationDeliver an outstanding presentation on the topic using this Enterprise Vulnerability Management Identify Sources Of Vulnerability Information. Dispense information and present a thorough explanation of Location Of The Component, Vulnerability Information, Vulnerability Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise vulnerability management improve the capability
Enterprise vulnerability management improve the capabilityIntroducing Enterprise Vulnerability Management Improve The Capability to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Deficiencies In The Pro, Measures Of Effectiveness, Measurements Is Negative, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management manage exposure to discovered vulnerabilities
Enterprise vulnerability management manage exposure to discovered vulnerabilitiesIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Manage Exposure To Discovered Vulnerabilities This template helps you present information on four stages. You can also present information on Test Disposition, Deploy Disposition Method, Track To Resolution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise vulnerability management need for vulnerability management
Enterprise vulnerability management need for vulnerability managementIntroducing Enterprise Vulnerability Management Need For Vulnerability Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Detective And Responsive, Responsive Controls, Preventative Approaches, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management overview assets
Enterprise vulnerability management overview assetsIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Overview Assets This template helps you present information on five stages. You can also present information on Identify Stakeholder, Scoping Statement, Management Involvement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise vulnerability management overview list
Enterprise vulnerability management overview listIntroducing Enterprise Vulnerability Management Overview List to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Management Support, Vulnerability Management, Vulnerability Management Strategy, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management provide training
Enterprise vulnerability management provide trainingIntroducing Enterprise Vulnerability Management Provide Training to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Personnel On The Process, Train Personnel, Perform Them According, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management record discovered vulnerabilities
Enterprise vulnerability management record discovered vulnerabilitiesIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Record Discovered Vulnerabilities. This template helps you present information on five stages. You can also present information on Management Should Understand, Perform Them According, Personnel Need To Understand using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise vulnerability management vulnerability management levels
Enterprise vulnerability management vulnerability management levelsIntroducing Enterprise Vulnerability Management Vulnerability Management Levels to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Categorization, Affected Assets, Discovery Date And Time, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management vulnerability management model
Enterprise vulnerability management vulnerability management modelIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Vulnerability Management Model. This template helps you present information on five stages. You can also present information on Proactive Execution, Purpose Driven Compliance, Primitive Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise vulnerability management overview plan
Enterprise vulnerability management overview planIntroducing Enterprise Vulnerability Management Overview Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Management, Vulnerability Information, Definition Of Roles And Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management overview program
Enterprise vulnerability management overview programIncrease audience engagement and knowledge by dispensing information using Enterprise Vulnerability Management Overview Program. This template helps you present information on four stages. You can also present information on Identified Stakeholders, Vulnerability Management, Established Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview enterprise vulnerability management
Overview enterprise vulnerability managementIntroducing Overview Enterprise Vulnerability Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Thousands Of Vulnerabilities, Vulnerability Mana, Elements Connected, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management sim vs sem vs siem
Improve it security with vulnerability management sim vs sem vs siemDeliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Sim Vs Sem Vs Siem. Dispense information and present a thorough explanation of Security, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management software challenges with solutions
Improve it security with vulnerability management software challenges with solutionsThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Software Challenges With Solutions. Use it as a tool for discussion and navigation on Workforce Limitations, Responsiveness, Limitations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management threat intelligence services
Improve it security with vulnerability management threat intelligence servicesThis slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Threat Intelligence Services. This template helps you present information on three stages. You can also present information on Global Intelligence, Local Intelligence, Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management traditional siem deployment model
Improve it security with vulnerability management traditional siem deployment modelThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Traditional Siem Deployment Model. Dispense information and present a thorough explanation of Vulnerability, Management, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
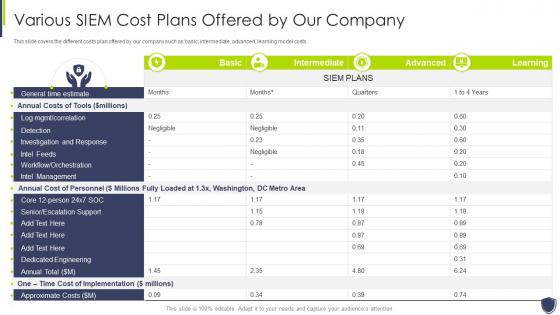 Improve it security with vulnerability management various siem cost plans offered company
Improve it security with vulnerability management various siem cost plans offered companyThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Various Siem Cost Plans Offered Company. Use it as a tool for discussion and navigation on Various SIEM Cost Plans Offered By Our Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management what sets us apart
Improve it security with vulnerability management what sets us apartThis slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management What Sets Us Apart. This template helps you present information on four stages. You can also present information on Productivity, Improvement, Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
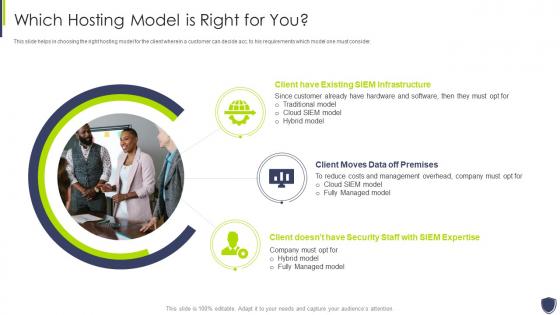 Improve it security with vulnerability management which hosting model is right for you
Improve it security with vulnerability management which hosting model is right for youThis slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. Introducing Improve It Security With Vulnerability Management Which Hosting Model Is Right For You to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Premises, Management, using this template. Grab it now to reap its full benefits.
-
 Log management services improve it security with vulnerability management
Log management services improve it security with vulnerability managementIncrease audience engagement and knowledge by dispensing information using Log Management Services Improve It Security With Vulnerability Management. This template helps you present information on eight stages. You can also present information on Virtualization, Application, Databases using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Our management team improve it security with vulnerability management
Our management team improve it security with vulnerability managementIntroducing Our Management Team Improve It Security With Vulnerability Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Our Management Team, using this template. Grab it now to reap its full benefits.
-
 Siem competitive advantage improve it security with vulnerability management
Siem competitive advantage improve it security with vulnerability managementThis slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Present the topic in a bit more detail with this Siem Competitive Advantage Improve It Security With Vulnerability Management. Use it as a tool for discussion and navigation on Experience, Management, Competitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents improve it security with vulnerability management
Table of contents improve it security with vulnerability managementIncrease audience engagement and knowledge by dispensing information using Table Of Contents Improve It Security With Vulnerability Management. This template helps you present information on eleven stages. You can also present information on Vulnerability, Management, Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What our clients say about us improve it security with vulnerability management
What our clients say about us improve it security with vulnerability managementThis slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. Deliver an outstanding presentation on the topic using this What Our Clients Say About Us Improve It Security With Vulnerability Management. Dispense information and present a thorough explanation of What Our Clients Say About Us using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda of improve it security with vulnerability management
Agenda of improve it security with vulnerability managementIntroducing Agenda Of Improve It Security With Vulnerability Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability, Management, Agenda, using this template. Grab it now to reap its full benefits.
-
 Architecture flowchart improve it security with vulnerability management
Architecture flowchart improve it security with vulnerability managementThis slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Present the topic in a bit more detail with this Architecture Flowchart Improve It Security With Vulnerability Management. Use it as a tool for discussion and navigation on Security Device, Network Devices, Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Estimating total cost of ownership improve it security vulnerability management
Estimating total cost of ownership improve it security vulnerability managementThis slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support. Deliver an outstanding presentation on the topic using this Estimating Total Cost Of Ownership Improve It Security Vulnerability Management. Dispense information and present a thorough explanation of Estimating Total Cost Of Ownership Of SIEM using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons slide for improve it security with vulnerability management
Icons slide for improve it security with vulnerability managementIntroducing our well researched set of slides titled Icons Slide For Improve It Security With Vulnerability Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Improve it security vulnerability management calculating network device velocity sizing
Improve it security vulnerability management calculating network device velocity sizingThis slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Present the topic in a bit more detail with this Improve It Security Vulnerability Management Calculating Network Device Velocity Sizing. Use it as a tool for discussion and navigation on Calculating Network Device Velocity Sizing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security vulnerability management companys enhanced features capabilities
Improve it security vulnerability management companys enhanced features capabilitiesThis slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Deliver an outstanding presentation on the topic using this Improve It Security Vulnerability Management Companys Enhanced Features Capabilities. Dispense information and present a thorough explanation of Threat Detection, Investigation, Time To Respond using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security vulnerability management estimating total cost ownership siem
Improve it security vulnerability management estimating total cost ownership siemThis slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Present the topic in a bit more detail with this Improve It Security Vulnerability Management Estimating Total Cost Ownership Siem. Use it as a tool for discussion and navigation on Management, Engineering, Ownership. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability benchmarking security operations maturity model
Improve it security with vulnerability benchmarking security operations maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Improve It Security With Vulnerability Benchmarking Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Visibility, Quickly Identify Threats, Decrease Response Time, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability benefits of choosing our company siem services
Improve it security with vulnerability benefits of choosing our company siem servicesThis slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Benefits Of Choosing Our Company Siem Services. This template helps you present information on four stages. You can also present information on Cost Saving, Reduction In The Impact Of Security Events, Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.





