Powerpoint Templates and Google slides for Trusts
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 On Ramp Option 1 User And Device Identity Zero Trust Architecture ZTA
On Ramp Option 1 User And Device Identity Zero Trust Architecture ZTAThis slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Introducing On Ramp Option 1 User And Device Identity Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Practices, Technologies, Biometrics, Device Certification, using this template. Grab it now to reap its full benefits.
-
 On Ramp Option 2 Applications And Data Zero Trust Architecture ZTA
On Ramp Option 2 Applications And Data Zero Trust Architecture ZTAThis slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Introducing On Ramp Option 2 Applications And Data Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Classification, Container Security, Practices And Technologies, using this template. Grab it now to reap its full benefits.
-
 On Ramp Option 3 The Network Zero Trust Architecture ZTA
On Ramp Option 3 The Network Zero Trust Architecture ZTAThis slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, micro segmentation, stateful session management, network encryption and secure routing, and so on. Introducing On Ramp Option 3 The Network Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Automation, Micro segmentation, session management, using this template. Grab it now to reap its full benefits.
-
 Other ZTNA Architecture Deployment Approaches Zero Trust Architecture ZTA
Other ZTNA Architecture Deployment Approaches Zero Trust Architecture ZTAThis slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Introducing Other ZTNA Architecture Deployment Approaches Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Identity Governance, Micro Segmentation, Network Perimeters, using this template. Grab it now to reap its full benefits.
-
 Overview Of Zero Trust Solution Categories Zero Trust Architecture ZTA
Overview Of Zero Trust Solution Categories Zero Trust Architecture ZTAThis slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Deliver an outstanding presentation on the topic using this Overview Of Zero Trust Solution Categories Zero Trust Architecture ZTA. Dispense information and present a thorough explanation of Accounts Authorization, Login Credentials, Enterprise Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pro Browser Based Approach Of ZTNA Architecture Zero Trust Architecture ZTA
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Architecture ZTAThis slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Present the topic in a bit more detail with this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Architecture ZTA. Use it as a tool for discussion and navigation on Vision, Internet Browser, Web Apps. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTA
Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTAThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Network, Apps Directly, VPN, using this template. Grab it now to reap its full benefits.
-
 Service Initiated Zero Trust Network Topology Model Ppt File Professional
Service Initiated Zero Trust Network Topology Model Ppt File ProfessionalThis slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Present the topic in a bit more detail with this Service Initiated Zero Trust Network Topology Model Ppt File Professional. Use it as a tool for discussion and navigation on Model, Computers, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step 1 Form A Dedicated Zero Trust Team Ppt File Slides
Step 1 Form A Dedicated Zero Trust Team Ppt File SlidesThis slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Introducing Step 1 Form A Dedicated Zero Trust Team Ppt File Slides to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Application, Data Security, Network, Infrastructure Security, using this template. Grab it now to reap its full benefits.
-
 Step 2 Choose Zero Trust Implementation On Ramp Ppt File Summary
Step 2 Choose Zero Trust Implementation On Ramp Ppt File SummaryThis slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Introducing Step 2 Choose Zero Trust Implementation On Ramp Ppt File Summary to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Biometrics, Multifactor Authentication, Device Certification, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTA
Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTAThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Architecture ZTA. Use it as a tool for discussion and navigation on Protection Surface, Security Model, Mapping Transaction Flows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Zero Trust Architecture ZTA Ppt File Background
Table Of Contents For Zero Trust Architecture ZTA Ppt File BackgroundIntroducing Table Of Contents For Zero Trust Architecture ZTA Ppt File Background to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on ZTNA Overview, ZTNA Importance, ZTNA Architecture, using this template. Grab it now to reap its full benefits.
-
 Technologies Used In Zero Trust Network Access Ppt File Clipart
Technologies Used In Zero Trust Network Access Ppt File ClipartThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Present the topic in a bit more detail with this Technologies Used In Zero Trust Network Access Ppt File Clipart. Use it as a tool for discussion and navigation on Network Access Control, Device Access Control, Microsegmentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Ppt File Designs
Timeline To Implement Zero Trust Network Access Model Ppt File DesignsThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Ppt File Designs to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Zero Trust Team, Network, Applications, using this template. Grab it now to reap its full benefits.
-
 Top Zero Trust Network Access Software Solutions Ppt File Graphics
Top Zero Trust Network Access Software Solutions Ppt File GraphicsThis slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Present the topic in a bit more detail with this Top Zero Trust Network Access Software Solutions Ppt File Graphics. Use it as a tool for discussion and navigation on SSO Authentication, MFA Verification, Scalable. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTA
Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTAThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Protect, Detect, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Table Of Contents Ppt File Background Designs
Zero Trust Architecture ZTA Table Of Contents Ppt File Background DesignsIntroducing Zero Trust Architecture ZTA Table Of Contents Ppt File Background Designs to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on ZTNA Overview, Network Access Model, ZTNA Solution, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Architectural Models Ppt File Inspiration
Zero Trust Network Access Architectural Models Ppt File InspirationThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing Zero Trust Network Access Architectural Models Ppt File Inspiration to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Verification, Access Control, Data Encryption, Decryption, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Architecture Overview Ppt File Introduction
Zero Trust Network Access Architecture Overview Ppt File IntroductionThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Architecture Overview Ppt File Introduction. Dispense information and present a thorough explanation of Mitigate Network Attacks, Security Paradigm, Multifactor Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Network Access Architecture Workflow Ppt File Picture
Zero Trust Network Access Architecture Workflow Ppt File PictureThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Introducing Zero Trust Network Access Architecture Workflow Ppt File Picture to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Resources, Tasks, Programmes, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Implementation Challenges Ppt File Rules
Zero Trust Network Access Implementation Challenges Ppt File RulesThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Present the topic in a bit more detail with this Zero Trust Network Access Implementation Challenges Ppt File Rules. Use it as a tool for discussion and navigation on Hardware, Security Vulnerabilities, Software Modifications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Network Access Performance Tracking Dashboard Ppt File Samples
Zero Trust Network Access Performance Tracking Dashboard Ppt File SamplesThis slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Performance Tracking Dashboard Ppt File Samples. Dispense information and present a thorough explanation of Security Rating, Device Risk, Threats Flow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Network Access System Use Cases Ppt File Template
Zero Trust Network Access System Use Cases Ppt File TemplateThis slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Introducing Zero Trust Network Access System Use Cases Ppt File Template to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Business Security, Cyberattacks, Data Breaches, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access User Flow Overview Zero Trust Architecture ZTA
Zero Trust Network Access User Flow Overview Zero Trust Architecture ZTAThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Introducing Zero Trust Network Access User Flow Overview Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security, Policy, Cloud Data Center, Branch Office, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Vs Virtual Private Network Zero Trust Architecture ZTA
Zero Trust Network Access Vs Virtual Private Network Zero Trust Architecture ZTAThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Introducing Zero Trust Network Access Vs Virtual Private Network Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Iaas Settings, Data Centers, Apps, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access ZTNA Introduction Ppt File Influencers
Zero Trust Network Access ZTNA Introduction Ppt File InfluencersThis slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Deliver an outstanding presentation on the topic using this Zero Trust Network Access ZTNA Introduction Ppt File Influencers. Dispense information and present a thorough explanation of IT Security Solution, Virtual Private Network, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
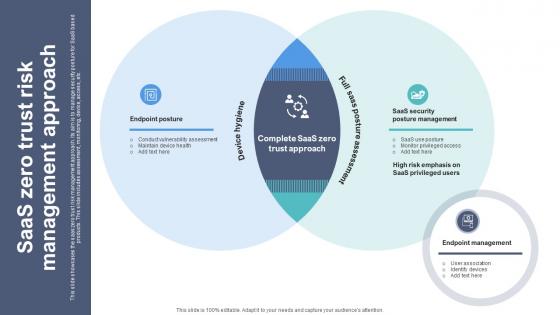 SaaS Zero Trust Risk Management Approach
SaaS Zero Trust Risk Management ApproachThis slide showcases the saas zero trust risk management approach. Its aim is to manage security posture for SaaS based products. This slide includes assessment, monitoring, device, access, etc. Introducing SaaS Zero Trust Risk Management Approach to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Posture, Endpoint Management, Complete Saas Zero Trust Approach, using this template. Grab it now to reap its full benefits.
-
 Strategies For Trusting Employees With Implementing Strategies To Enhance Employee Rating Strategy SS
Strategies For Trusting Employees With Implementing Strategies To Enhance Employee Rating Strategy SSThis slide showcases techniques for trusting employees with time management. It includes strategies such as flexible work arrangements, goal oriented time management, provide time management training and encourage regular breaks. Present the topic in a bit more detail with this Strategies For Trusting Employees With Implementing Strategies To Enhance Employee Rating Strategy SS Use it as a tool for discussion and navigation on Strategy, Description, Impact This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Real Estate Social Media Portfolio For Building Trust
Real Estate Social Media Portfolio For Building TrustThis slide highlights digital portfolio for enhancing credibility. The purpose of this slide is to aid professionals in displaying authentic content for fostering confidence in potential buyers and sellers. It includes elements such as transparency, educational content, etc. Introducing our premium set of slides with Real Estate Social Media Portfolio For Building Trust. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Educational Content, Provide Comprehensive Guides, Market Data. So download instantly and tailor it with your information.
-
 Case Study Ibm Food Trust Project Complete Guide To Blockchain In Cloud BCT SS V
Case Study Ibm Food Trust Project Complete Guide To Blockchain In Cloud BCT SS VThis slide provides a case study of IBMs food trust project that implemented blockchain enabled cloud computing technology. It includes information about the project. How blockchain cloud computing is used and benefits generated. Introducing Case Study Ibm Food Trust Project Complete Guide To Blockchain In Cloud BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cloud Computing, Contaminated Products, Blockchain Network, using this template. Grab it now to reap its full benefits.
-
 IBM Food Trust And Coricelli Case Study Exploring Diverse Blockchain BCT SS
IBM Food Trust And Coricelli Case Study Exploring Diverse Blockchain BCT SSThis slide covers the use case of IBM food trust. It includes application steps such as adoption, implementation, product focus, brand expansion, technology integration, etc. Present the topic in a bit more detail with this IBM Food Trust And Coricelli Case Study Exploring Diverse Blockchain BCT SS Use it as a tool for discussion and navigation on Product Focus, Brand Expansion, Technology Integration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture ZTA Case Study Intellectual Property Protection With Zero Trust Model
Zero Trust Architecture ZTA Case Study Intellectual Property Protection With Zero Trust ModelThis slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Introducing Zero Trust Architecture ZTA Case Study Intellectual Property Protection With Zero Trust Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Solutions, Workstations, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Critical Principles Of Zero Trust Network Access Model
Zero Trust Architecture ZTA Critical Principles Of Zero Trust Network Access ModelThis slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Deliver an outstanding presentation on the topic using this Zero Trust Architecture ZTA Critical Principles Of Zero Trust Network Access Model. Dispense information and present a thorough explanation of Privilege Access, Micro Segmentation, Device Validation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Architecture ZTA Difference Between ZTNA And Software Defined Perimeter
Zero Trust Architecture ZTA Difference Between ZTNA And Software Defined PerimeterThis slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Present the topic in a bit more detail with this Zero Trust Architecture ZTA Difference Between ZTNA And Software Defined Perimeter. Use it as a tool for discussion and navigation on Key Features, Deployment, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture ZTA Endpoint Initiated Zero Trust Network Topology Model
Zero Trust Architecture ZTA Endpoint Initiated Zero Trust Network Topology ModelThis slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Introducing Zero Trust Architecture ZTA Endpoint Initiated Zero Trust Network Topology Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Computer, service, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture Microsegmentation Overview And Working In ZTNA Model
Zero Trust Architecture Microsegmentation Overview And Working In ZTNA ModelThis slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Present the topic in a bit more detail with this Zero Trust Architecture Microsegmentation Overview And Working In ZTNA Model. Use it as a tool for discussion and navigation on Cybersecurity, Zero Trust Architecture, Separate Zones. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access Model
Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access ModelThis slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Introducing Zero Trust Architecture ZTA Roadmap To Implement Zero Trust Network Access Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Infrastructure, Ztna Solution, Configure Policies, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security
Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Introducing Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Method, ZTNA Approach, Login Capability, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
Zero Trust Architecture ZTA Step 4 And 5 Available Technology Review And Zero Trust Initiatives LaunchThis slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Introducing Zero Trust Architecture ZTA Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Microsegmentation, Virtual Routing, Stateful Session Management, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Step 6 And 7 Define Operational Changes And Implement Rinse Repeat
Zero Trust Architecture ZTA Step 6 And 7 Define Operational Changes And Implement Rinse RepeatThis slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Introducing Zero Trust Architecture ZTA Step 6 And 7 Define Operational Changes And Implement Rinse Repeat to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security Operations, Zero Trust Model, Security Processes, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide
Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File GuideThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Introducing Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Limitations, Solution, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Architecture ZTA Zero Trust Network Access Vs Virtual Private Network
Zero Trust Architecture ZTA Zero Trust Network Access Vs Virtual Private NetworkThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Introducing Zero Trust Architecture ZTA Zero Trust Network Access Vs Virtual Private Network to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Iaas Settings, Data Centers, Apps, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Exchange Overview And Benefits Zero Trust Architecture ZTA
Zero Trust Exchange Overview And Benefits Zero Trust Architecture ZTAThis slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Introducing Zero Trust Exchange Overview And Benefits Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on VPNs, Network Perimeter, Firewall Regulations, using this template. Grab it now to reap its full benefits.
-
 Types Of Zero Trust Network Access ZTNA Models Zero Trust Architecture ZTA
Types Of Zero Trust Network Access ZTNA Models Zero Trust Architecture ZTAThis slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Introducing Types Of Zero Trust Network Access ZTNA Models Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on User Protection, Workload protection, Device Protection, using this template. Grab it now to reap its full benefits.
-
 Reference Marketing Methods To Build Trust Hospital Startup Business Plan Revolutionizing
Reference Marketing Methods To Build Trust Hospital Startup Business Plan RevolutionizingThe following slide illustrates some reference promotional techniques to boost visibility and build trust. It includes elements such as referral cards, patient testimonials, physician referrals, community partnerships, etc. Increase audience engagement and knowledge by dispensing information using Reference Marketing Methods To Build Trust Hospital Startup Business Plan Revolutionizing. This template helps you present information on four stages. You can also present information on Referral Cards, Patient Testimonials, Physician Referrals, Community Partnerships using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA
M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTAThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA. Dispense information and present a thorough explanation of Factors, Traditional Security Model, ZTNA using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 M73 Training Program For Zero Trust Network Access Model Zero Trust Architecture ZTA
M73 Training Program For Zero Trust Network Access Model Zero Trust Architecture ZTAThis slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Present the topic in a bit more detail with this M73 Training Program For Zero Trust Network Access Model Zero Trust Architecture ZTA. Use it as a tool for discussion and navigation on Agenda, Objectives, System Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 M74 Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTA
M74 Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTAThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing M74 Working Functions Of Zero Trust Network Access Architecture Zero Trust Architecture ZTA to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Protect, Detect, using this template. Grab it now to reap its full benefits.
-
 Solutions To Lack Of Trust Financial Inclusion To Promote Economic Fin SS
Solutions To Lack Of Trust Financial Inclusion To Promote Economic Fin SSThis slide shows various solutions which can be used to resolve the challenge of lack of trust in financial institutions. These solutions includes transparency, regulatory oversight, etc. Increase audience engagement and knowledge by dispensing information using Solutions To Lack Of Trust Financial Inclusion To Promote Economic Fin SS. This template helps you present information on four stages. You can also present information on Transparency, Description, Customer Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Conceptual Architecture Of Trusted Virtual Server
Conceptual Architecture Of Trusted Virtual ServerThis slide highlights trusted virtual servers conceptual design. The purpose of this template is to help businesses in protecting sensitive data from unauthorized access by complying with data security regulations. It includes elements such as MH client, key management service, etc. Presenting our well structured Conceptual Architecture Of Trusted Virtual Server. The topics discussed in this slide are Conceptual, Architecture, Key Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Choose Best Crypto Wallet Trust Unlocking New Opportunities With NFTs BCT SS
Choose Best Crypto Wallet Trust Unlocking New Opportunities With NFTs BCT SSThe following slide showcases key details about Trust crypto wallet to manage private keys and store currencies. It includes elements such as overview, pros, cons, features, fee, reviews, easy setup, decentralized exchange, staking options, customer support, etc. Increase audience engagement and knowledge by dispensing information using Choose Best Crypto Wallet Trust Unlocking New Opportunities With NFTs BCT SS. This template helps you present information on two stages. You can also present information on Cryptocurrencies, Private Keys, Charges Network Fee using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sales Territory Planning To Enhance Lead Nurturing Email Samples To Build Trust SA SS
Sales Territory Planning To Enhance Lead Nurturing Email Samples To Build Trust SA SSThis slide includes an email targeting samples to introduce brand to potential customers including personalized emails and follow-up emails. Deliver an outstanding presentation on the topic using this Sales Territory Planning To Enhance Lead Nurturing Email Samples To Build Trust SA SS. Dispense information and present a thorough explanation of Personalised Email, Follow Up Email, Lead Nurturing Email using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
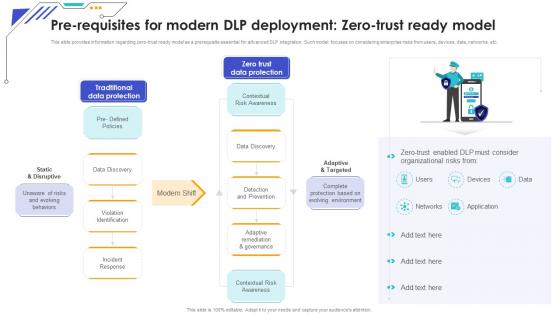 Pre Requisites For Modern Dlp Deployment Zero Trust Safeguarding Business With Data Loss Cybersecurity SS
Pre Requisites For Modern Dlp Deployment Zero Trust Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding zero-trust ready model as a prerequisite essential for advanced DLP integration. Such model focuses on considering enterprise risks from users, devices, data, networks, etc.Increase audience engagement and knowledge by dispensing information using Pre Requisites For Modern Dlp Deployment Zero Trust Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Tradtitional Data Protection, Data Discovery, Incident Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trusted Reliability Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Trusted Reliability Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a reliable and efficient tool for creating professional presentations. Its vibrant colours and sleek design make it eye-catching and easy to use. With a variety of features and options, this icon is perfect for any presentation needs, ensuring a polished and reliable final product.
-
 Trusted Reliability Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Trusted Reliability Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a reliable and essential tool for any presentation. Its sleek and simple design allows for easy navigation and use, making it perfect for professionals and students alike. With this icon, you can create impactful and effective presentations with confidence and ease.
-
 Real Estate Investment Trust Company Framework
Real Estate Investment Trust Company FrameworkThis slide shows a diagram that can be used to highlight the framework of a typical REIT. It includes various personnel, such as investors, managers, trustees, sponsors, etc. It also includes various tasks such as providing management services, distribution of shares, etc. Introducing our premium set of slides with Real Estate Investment Trust Company Framework. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Unit Holders, Trustee, Reit. So download instantly and tailor it with your information.
-
 Real Estate Investment Trust Company Icon
Real Estate Investment Trust Company IconPresenting our set of slides with Real Estate Investment Trust Company Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Real Estate Investment, Trust Company, Icon.
-
 Real Estate Investment Trust Model
Real Estate Investment Trust ModelThis slide shows a diagram that can be used to represent how real estate investment trusts process works. It includes various people, which are investors, trustees, managers, and others and tasks such as providing management services, distributing cashflows, etc. Presenting our set of slides with Real Estate Investment Trust Model. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Trustee, Investor, Manager.
-
 Factors Affecting Real Estate Investment Trust
Factors Affecting Real Estate Investment TrustThis slide highlights various factors that affect investment decisions in real estate property. It includes key components such as property location, valuation of property, investment purpose and expected cash flows, and profit opportunities. Introducing our premium set of slides with Factors Affecting Real Estate Investment Trust Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Property Location, Investment Purpose, Property Valuation So download instantly and tailor it with your information.
-
 Impact Of Real Estate Investment Trust
Impact Of Real Estate Investment TrustThe following slide explains various advantages of real estate investment trusts to analyze its income-generating potential. It includes information about diversification, inflation protection, performance, transparency, liquidity, etc. Presenting our set of slides with Impact Of Real Estate Investment Trust This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Diversification, Liquidity, Performance





