Powerpoint Templates and Google slides for Trusted Computing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Confidential Computing Market Intel Sgx With A Smaller Trusted Computing Base Tcb
Confidential Computing Market Intel Sgx With A Smaller Trusted Computing Base TcbThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Market Intel Sgx With A Smaller Trusted Computing Base Tcb. Dispense information and present a thorough explanation of Application, Environment, Experience using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Process Of Using Intel Sgx Based Trusted Applications
Confidential Computing Market Process Of Using Intel Sgx Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Deliver an outstanding presentation on the topic using this Confidential Computing Market Process Of Using Intel Sgx Based Trusted Applications. Dispense information and present a thorough explanation of Applications, Process, Development using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Trust Boundary Across Azure Confidential Computing Services
Confidential Computing Market Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Deliver an outstanding presentation on the topic using this Confidential Computing Market Trust Boundary Across Azure Confidential Computing Services. Dispense information and present a thorough explanation of Confidential, Computing, Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Trusted Execution Environment Tee Hardware Platform
Confidential Computing Market Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Present the topic in a bit more detail with this Confidential Computing Market Trusted Execution Environment Tee Hardware Platform. Use it as a tool for discussion and navigation on Execution, Environment, Hardware Platform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market What Is Trusted Execution Environment Tee In Confidential Computing
Confidential Computing Market What Is Trusted Execution Environment Tee In Confidential ComputingThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present the topic in a bit more detail with this Confidential Computing Market What Is Trusted Execution Environment Tee In Confidential Computing. Use it as a tool for discussion and navigation on Execution, Environment, Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB
Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCBThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB. This template helps you present information on two stages. You can also present information on Operating System, Virtual Machine Monitor, Hardware, Cloud Vendors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications
Confidential Computing Hardware Process Of Using Intel SGX Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on SGX Based Trusted Applications, Installing The Environment, Developing, Computing And Building, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing Services
Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing Services. Dispense information and present a thorough explanation of Trust Boundary Architecture, Azure Confidential Computing Services, Demonstrate The Trust Boundary, Sensitive Data, Sensitive Application Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform
Confidential Computing Hardware Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform. This template helps you present information on three stages. You can also present information on Protects Guest Memory, Provide Virtual Machine Isolation, Secure Memory Encryption, Encrypted State Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware What Is Trusted Execution Environment Tee In Confidential
Confidential Computing Hardware What Is Trusted Execution Environment Tee In ConfidentialThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware What Is Trusted Execution Environment Tee In Confidential. This template helps you present information on five stages. You can also present information on Code Confidentiality, Authenticated Launch, Programmability, Confidential Computing Consortium using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Consortium What Is Trusted Execution Environment TEE In Confidential
Confidential Computing Consortium What Is Trusted Execution Environment TEE In ConfidentialThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Introducing Confidential Computing Consortium What Is Trusted Execution Environment TEE In Confidential to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Code Confidentiality, Authenticated Launch, Programmability, Confidential Computing, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium Intel SGX With A Smaller Trusted Computing Base TCB
Confidential Computing Consortium Intel SGX With A Smaller Trusted Computing Base TCBThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Intel SGX With A Smaller Trusted Computing Base TCB. Dispense information and present a thorough explanation of Operating System, Virtual Machine Monitor, Cloud Vendors, Trusted Computing Base using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Process Of Using Intel SGX Based Trusted Applications
Confidential Computing Consortium Process Of Using Intel SGX Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing Consortium Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Install The Environment, SGX Based Trusted Applications, Installing The Environment, Developing, Computing And Building Executing, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium Trust Boundary Across Azure Confidential Computing Services
Confidential Computing Consortium Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Present the topic in a bit more detail with this Confidential Computing Consortium Trust Boundary Across Azure Confidential Computing Services. Use it as a tool for discussion and navigation on Sensitive Data, Sensitive Application Code, Sensitive Application Logs, Confidential Computing Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Trusted Execution Environment Tee Hardware Platform
Confidential Computing Consortium Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Introducing Confidential Computing Consortium Trusted Execution Environment Tee Hardware Platform to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Execution Environment, Hardware Platform, Advanced Micro Devices, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base Tcb
Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base TcbThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Present the topic in a bit more detail with this Confidential Computing System Technology Intel Sgx With A Smaller Trusted Computing Base Tcb. Use it as a tool for discussion and navigation on Deployment, Environment, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted Applications
Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Process Of Using Intel Sgx Based Trusted Applications. Dispense information and present a thorough explanation of Applications, Install The Environment, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing Services
Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Present the topic in a bit more detail with this Confidential Computing System Technology Trust Boundary Across Azure Confidential Computing Services. Use it as a tool for discussion and navigation on Confidential, Computing, Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing System Technology Trusted Execution Environment Tee Hardware Platform
Confidential Computing System Technology Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology Trusted Execution Environment Tee Hardware Platform. Dispense information and present a thorough explanation of Environment, Information, Application using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Intel Sgx With A Smaller Trusted Computing Base TCB
Confidential Computing V2 Intel Sgx With A Smaller Trusted Computing Base TCBThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Intel Sgx With A Smaller Trusted Computing Base TCB. Dispense information and present a thorough explanation of Operating System, Virtual Machine Monitor, Applications And Hardware, Virtual Machine Monitor using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications
Confidential Computing V2 Process Of Using Intel SGX Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Installing The Environment, Developing, Computing And Building, Signature Encryption, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing V2 Trust Boundary Across Azure Confidential Computing Services
Confidential Computing V2 Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Trust Boundary Across Azure Confidential Computing Services. Dispense information and present a thorough explanation of Sensitive Data, Sensitive Application Code, Sensitive Application Logs, Confidential Computing Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Trusted Execution Environment TEE Hardware Platform
Confidential Computing V2 Trusted Execution Environment TEE Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Increase audience engagement and knowledge by dispensing information using Confidential Computing V2 Trusted Execution Environment TEE Hardware Platform. This template helps you present information on three stages. You can also present information on Trusted Execution Environment, Hardware Platform, Confidential Computing, Perform Ordinary Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing V2 What Is Trusted Execution Environment Tee In Confidential Computing
Confidential Computing V2 What Is Trusted Execution Environment Tee In Confidential ComputingThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Increase audience engagement and knowledge by dispensing information using Confidential Computing V2 What Is Trusted Execution Environment Tee In Confidential Computing. This template helps you present information on five stages. You can also present information on Code Confidentiality, Authenticated Launch, Programmability, Attestability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trusted computing technology ppt powerpoint presentation inspiration outfit cpb
Trusted computing technology ppt powerpoint presentation inspiration outfit cpbPresenting Trusted Computing Technology Ppt Powerpoint Presentation Inspiration Outfit Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Trusted Computing Technology. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
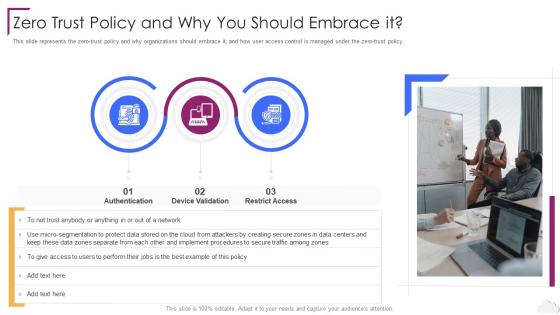 Cloud Computing Security Zero Trust Policy And Why You Should Embrace It
Cloud Computing Security Zero Trust Policy And Why You Should Embrace ItThis slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero trust policy. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Zero Trust Policy And Why You Should Embrace It. This template helps you present information on three stages. You can also present information on Authentication, Device Validation, Restrict Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trust Boundary Across Azure Confidential Computing Services Confidential Cloud Computing
Trust Boundary Across Azure Confidential Computing Services Confidential Cloud ComputingThis slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Present the topic in a bit more detail with this Trust Boundary Across Azure Confidential Computing Services Confidential Cloud Computing. Use it as a tool for discussion and navigation on Confidential, Computing, Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Cloud Computing Intel Sgx With A Smaller Trusted Computing Base Tcb
Confidential Cloud Computing Intel Sgx With A Smaller Trusted Computing Base TcbThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Deliver an outstanding presentation on the topic using this Confidential Cloud Computing Intel Sgx With A Smaller Trusted Computing Base Tcb. Dispense information and present a thorough explanation of Sensitive Applications, Environment, Experience using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Cloud Computing Process Of Using Intel Sgx Based Trusted Applications
Confidential Cloud Computing Process Of Using Intel Sgx Based Trusted ApplicationsThis slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Deliver an outstanding presentation on the topic using this Confidential Cloud Computing Process Of Using Intel Sgx Based Trusted Applications. Dispense information and present a thorough explanation of Applications, Process, Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Cloud Computing Trusted Execution Environment Tee Hardware Platform
Confidential Cloud Computing Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Deliver an outstanding presentation on the topic using this Confidential Cloud Computing Trusted Execution Environment Tee Hardware Platform. Dispense information and present a thorough explanation of Execution, Environment, Hardware Platform using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Cloud Computing What Is Trusted Execution Environment Tee In Confidential Computing
Confidential Cloud Computing What Is Trusted Execution Environment Tee In Confidential ComputingThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Deliver an outstanding presentation on the topic using this Confidential Cloud Computing What Is Trusted Execution Environment Tee In Confidential Computing. Dispense information and present a thorough explanation of Execution, Environment, Confidential Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Intel SGX With A Smaller Trusted Computing Base TCB Confidential Computing IT
Intel SGX With A Smaller Trusted Computing Base TCB Confidential Computing ITThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Present the topic in a bit more detail with this Intel SGX With A Smaller Trusted Computing Base TCB Confidential Computing IT. Use it as a tool for discussion and navigation on Operating System, Virtual Machine Monitor, Hardware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process Of Using Intel SGX Based Trusted Applications Confidential Computing IT
Process Of Using Intel SGX Based Trusted Applications Confidential Computing ITThis slide outlines the process of using Intel SGX based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Process Of Using Intel SGX Based Trusted Applications Confidential Computing IT to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Application, Signature Encryption, Program Status, using this template. Grab it now to reap its full benefits.
-
 Trust Boundary Across Azure Confidential Computing Services Ppt Slides Example Introduction
Trust Boundary Across Azure Confidential Computing Services Ppt Slides Example IntroductionThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Present the topic in a bit more detail with this Trust Boundary Across Azure Confidential Computing Services Ppt Slides Example Introduction. Use it as a tool for discussion and navigation on Computing Services, Sensitive Data, Sensitive Application Logic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Trusted Execution Environment Tee Hardware Platform Confidential Computing IT
Trusted Execution Environment Tee Hardware Platform Confidential Computing ITThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Introducing Trusted Execution Environment Tee Hardware Platform Confidential Computing IT to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Set Of Guidelines, Security Of Application, Enclave Environment, using this template. Grab it now to reap its full benefits.
-
 What Is Trusted Execution Environment Tee In Confidential Computing
What Is Trusted Execution Environment Tee In Confidential ComputingThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Introducing What Is Trusted Execution Environment Tee In Confidential Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Computing Consortium, Secure Environment, Overview, using this template. Grab it now to reap its full benefits.
-
 Trust management cloud computing ppt powerpoint presentation professional layouts cpb
Trust management cloud computing ppt powerpoint presentation professional layouts cpbPresenting this set of slides with name Trust Management Cloud Computing Ppt Powerpoint Presentation Professional Layouts Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Trust Management Cloud Computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Trusted computing ppt powerpoint presentation styles design ideas cpb
Trusted computing ppt powerpoint presentation styles design ideas cpbPresenting Trusted Computing Ppt Powerpoint Presentation Styles Design Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Trusted Computing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Trusted subsystem cloud computing standard architecture patterns ppt powerpoint slide
Trusted subsystem cloud computing standard architecture patterns ppt powerpoint slideHere is a slide titled Trusted Subsystem Cloud Computing Standard Architecture Patterns Ppt Powerpoint Slide. Describe cloud computing patterns and their applications using this contemporary presentation template available in standard and widescreen sizes. Topics such as Database, Service, Consumer can be discussed with the help of this PowerPoint theme. Hit the download button and instantly elevate your presentation with our customizable PPT template.
-
 Isolated trust boundary cloud computing standard architecture patterns ppt diagram
Isolated trust boundary cloud computing standard architecture patterns ppt diagramShowcase your expertise on cloud computing patterns by introducing this slide titled Isolated Trust Boundary Cloud Computing Standard Architecture Patterns Ppt Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Geotagging, Hypervisor Protection, Independent Cloud Auditing with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
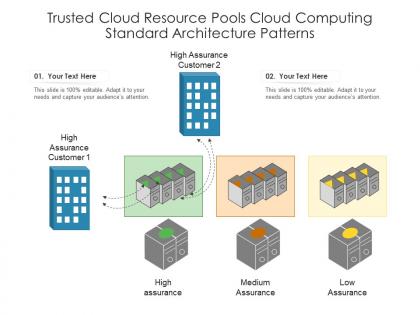 Trusted cloud resource pools cloud computing standard architecture patterns ppt powerpoint slide
Trusted cloud resource pools cloud computing standard architecture patterns ppt powerpoint slideUtilize this visually appealing slide titled Trusted Cloud Resource Pools Cloud Computing Standard Architecture Patterns Ppt Powerpoint Slide. Elucidate the concept of cloud computing patterns using this editable PowerPoint presentation. Explain High Assurance, Medium Assurance, Low Assurance using this PPT theme. Instantly grab the attention of your audience by downloading this professionally designed PPT template.
-
 Trusted platforms bios cloud computing standard architecture patterns ppt presentation diagram
Trusted platforms bios cloud computing standard architecture patterns ppt presentation diagramShowcase your expertise on cloud computing patterns by introducing this slide titled Trusted Platforms BIOS Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Third Party Drivers, System Files, Firmware Boot with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Trust attestation service cloud computing standard architecture patterns ppt slide
Trust attestation service cloud computing standard architecture patterns ppt slideShowcase your expertise on cloud computing patterns by introducing this slide titled Trust Attestation Service Cloud Computing Standard Architecture Patterns Ppt Slide. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Signed Attestation, Verified Boot, Attestation Service with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Trusted computing base ppt powerpoint presentation layouts ideas cpb
Trusted computing base ppt powerpoint presentation layouts ideas cpbPresenting Trusted Computing Base Ppt Powerpoint Presentation Layouts Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Trusted Computing Base. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.



