Powerpoint Templates and Google slides for Threats.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber threats management dashboard corporate security management
Cyber threats management dashboard corporate security managementThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Threats Management Dashboard Corporate Security Management. Dispense information and present a thorough explanation of Cyber Threats Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics associated to workplace threats corporate security management
Statistics associated to workplace threats corporate security managementThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Corporate Security Management. Use it as a tool for discussion and navigation on Cyber Attacks Costs, Organizations, Data Records. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat compliance dashboard with risk and standard control
Cyber threat compliance dashboard with risk and standard controlThe following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Introducing our Cyber Threat Compliance Dashboard With Risk And Standard Control set of slides. The topics discussed in these slides are Risk Control Issue, Review Effectiveness, Regulation Control Issue. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat dashboard with current risks and security service
Cyber threat dashboard with current risks and security serviceThe following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Presenting our well structured Cyber Threat Dashboard With Current Risks And Security Service. The topics discussed in this slide are Current Risks, Current Threats, Security Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security market growth with current trends
Cyber threat security market growth with current trendsThe following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Introducing our Cyber Threat Security Market Growth With Current Trends set of slides. The topics discussed in these slides are Cyber Security Market Share, Market Growth, Banking And Finance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyberterrorism it dashboard for threat tracking of cyber terrorism
Cyberterrorism it dashboard for threat tracking of cyber terrorismThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Dashboard For Threat Tracking Of Cyber Terrorism. Dispense information and present a thorough explanation of Threats Per Month, Top Threat, Average Threats Detection Per Day using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Dashboard Snapshot For Threat Tracking In Information Security
Information Security Dashboard Snapshot For Threat Tracking In Information SecurityThis slide depicts the dashboard snapshot for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Information Security Dashboard For Threat Tracking In Information Security. Dispense information and present a thorough explanation of Dashboard, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
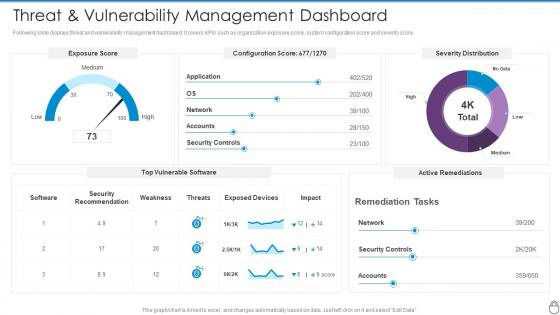 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical current potential implications faced by firm as threats
Threat management for organization critical current potential implications faced by firm as threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Threat Management For Organization Critical Current Potential Implications Faced By Firm As Threats. Dispense information and present a thorough explanation of Current Potential Implications Faced By Firm As Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management for organization critical cyber threats management dashboard
Threat management for organization critical cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives.Present the topic in a bit more detail with this Threat Management For Organization Critical Cyber Threats Management Dashboard. Use it as a tool for discussion and navigation on Average Risk Threshold, Risk Rating Breakdown, Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical financial performance tracking dashboard
Threat management for organization critical financial performance tracking dashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Threat Management For Organization Critical Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Financial Performance Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management for organization critical incident reporting dashboard
Threat management for organization critical incident reporting dashboardThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Threat Management For Organization Critical Incident Reporting Dashboard. Use it as a tool for discussion and navigation on Incident Reporting Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management current potential implications faced by firm threats
Cyber security risk management current potential implications faced by firm threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Security Risk Management Current Potential Implications Faced By Firm Threats. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management cyber threats management dashboard
Cyber security risk management cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks, Threshold Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hacking it dashboard snapshot for threat tracking ppt slides demonstration
Hacking it dashboard snapshot for threat tracking ppt slides demonstrationThis slide depicts the dashboard snapshot for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Hacking It Dashboard For Threat Tracking Ppt Slides Demonstration. Dispense information and present a thorough explanation of Dashboard For Threat Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification event management dashboard sanpshot
Automating threat identification event management dashboard sanpshotThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an outstanding presentation on the topic using this Automating Threat Identification Event Management Dashboard Snapshot. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification information and event management dashboard
Automating threat identification information and event management dashboardThis slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an outstanding presentation on the topic using this Automating Threat Identification Information And Event Management Dashboard. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information and event management dashboard automating threat identification
Information and event management dashboard automating threat identificationThis slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Present the topic in a bit more detail with this Information And Event Management Dashboard Automating Threat Identification. Use it as a tool for discussion and navigation on Information, Management, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Dashboard For Threat Tracking In Network Security
Network Security Dashboard For Threat Tracking In Network SecurityThis slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Network Security Dashboard For Threat Tracking In Network Security. Use it as a tool for discussion and navigation on Dashboard For Threat Tracking In Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Dashboard Snapshot Threat Tracking Information Technology Security
Information Technology Security Dashboard Snapshot Threat Tracking Information Technology SecurityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Information Technology Security Dashboard Threat Tracking Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As Threats
Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As ThreatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As Threats. Dispense information and present a thorough explanation of Potential, Implications, Ineffectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Cyber Threats Management Dashboard
Vulnerability Administration At Workplace Cyber Threats Management DashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Management, Dashboard, Portrays Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Statistics Associated To Workplace Threats
Vulnerability Administration At Workplace Statistics Associated To Workplace ThreatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Statistics Associated To Workplace Threats. Use it as a tool for discussion and navigation on Cyber Attacks Costs, Organizations, Organizations Have. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Threat Tracking Cyber Terrorism Attacks
Dashboard For Threat Tracking Cyber Terrorism AttacksThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Dashboard For Threat Tracking Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Dashboard For Threat Tracking Of Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Opportunities and threats entering new markets new geos target market size
Opportunities and threats entering new markets new geos target market sizeDeliver an outstanding presentation on the topic using this Opportunities And Threats Entering New Markets New Geos Target Market Size. Dispense information and present a thorough explanation of Target Market Size using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Target growth rate opportunities and threats entering new markets new geos
Target growth rate opportunities and threats entering new markets new geosDeliver an outstanding presentation on the topic using this Target Growth Rate Opportunities And Threats Entering New Markets New Geos. Dispense information and present a thorough explanation of Target Market Size And Growth Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Hacker Dashboard For Threat Tracking Ppt Powerpoint Presentation Professional File
Security Hacker Dashboard For Threat Tracking Ppt Powerpoint Presentation Professional FileThis slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Security Hacker Dashboard For Threat Tracking Ppt Powerpoint Presentation Professional File. Use it as a tool for discussion and navigation on Threat Dashboard, Current Risk Status, Threats Based On Role. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Insider Threat Cases Management
Dashboard For Insider Threat Cases ManagementThis slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Introducing our Dashboard For Insider Threat Cases Management set of slides. The topics discussed in these slides are Dashboard, Insider Threat, Cases Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Impact Of Insider Threat On Business Operations
Impact Of Insider Threat On Business OperationsThis slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Introducing our Impact Of Insider Threat On Business Operations set of slides. The topics discussed in these slides are Operational Disruption, Brand Damage, Loss Critical Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Insider Threat Detection And Prevention Dashboard
Insider Threat Detection And Prevention DashboardThis slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Introducing our Insider Threat Detection And Prevention Dashboard set of slides. The topics discussed in these slides are Insider Threat Detection, Prevention Dashboard . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Insider Threat Latest Trends And Landscape
Insider Threat Latest Trends And LandscapeThis slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Introducing our Insider Threat Latest Trends And Landscape set of slides. The topics discussed in these slides are Insider Threat, Trends, Landscape. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Insider Threat Tracking Dashboard With User Details
Insider Threat Tracking Dashboard With User DetailsThis slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Introducing our Insider Threat Tracking Dashboard With User Details set of slides. The topics discussed in these slides are Insider Threat, Tracking Dashboard, User Details. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistics For Root Causes Of Insider Threat
Statistics For Root Causes Of Insider ThreatThis slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Introducing our Statistics For Root Causes Of Insider Threat set of slides. The topics discussed in these slides are Statistics Root, Causes Insider Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Dashboard Of It Department With Threat Frequency
Risk Management Dashboard Of It Department With Threat FrequencyThis slide shows dashboard of risk management of IT department representing net critical risks, threat and vulnerability frequency in last 60 days, open audit findings, open and vendor risks etc. Presenting our well-structured Risk Management Dashboard Of It Department With Threat Frequency. The topics discussed in this slide are Open Risks, Risk Organization Level, Net Critical Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quarterly Comparison Of Information Technology Security Threats
Quarterly Comparison Of Information Technology Security ThreatsThis slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Introducing our Quarterly Comparison Of Information Technology Security Threats set of slides. The topics discussed in these slides are Quarterly Comparison, Information Technology, Security Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Threat Activity Discovery Dashboard
Cyber Security Threat Activity Discovery DashboardThe following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Presenting our well structured Cyber Security Threat Activity Discovery Dashboard. The topics discussed in this slide are Cyber Security, Threat Activity, Discovery Dashboard. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Management
Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat ManagementThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Management. Use it as a tool for discussion and navigation on KPI Metrics Dashboard, Effectively Track Cyber, Threat Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threat Dashboard With KPI Metrics
Cyber Security Threat Dashboard With KPI MetricsThis slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Introducing our Cyber Security Threat Dashboard With KPI Metrics set of slides. The topics discussed in these slides are Cyber Security Threat, Dashboard, KPI Metrics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing
Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing. Use it as a tool for discussion and navigation on Manual, Testing, Security Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness
KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security AwarenessThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Deliver an outstanding presentation on the topic using this KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based Role using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats
Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Firewall KPIs Dashboard for Threat Tracking in WAF
Application Firewall KPIs Dashboard for Threat Tracking in WAFThis slide depicts how threat risk will be monitored and threat detection will be done in the organization through web application firewall implementation. Present the topic in a bit more detail with this Application Firewall KPIs Dashboard for Threat Tracking in WAF. Use it as a tool for discussion and navigation on Monthly Threat Status, Current Risk Status, Threats Based On Role. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training
KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness TrainingThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Current Risk Status, Threats By Owners, Risk By Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
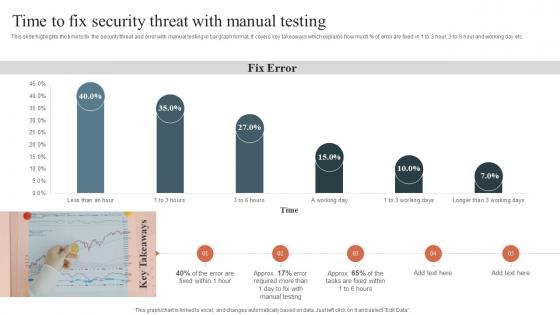 Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide
Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response GuideThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide. Use it as a tool for discussion and navigation on Time To Fix, Security Threat, Manual Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat And Vulnerability Management Program Analysis Dashboard
Threat And Vulnerability Management Program Analysis DashboardThis slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Presenting our well structured Threat And Vulnerability Management Program Analysis Dashboard. The topics discussed in this slide are Exposure Score, Top Vulnerable Software, Severity Distribution. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Quarterly Comparison Of Cloud Security Threats
Quarterly Comparison Of Cloud Security ThreatsThis slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Presenting our well structured Quarterly Comparison Of Cloud Security Threats. The topics discussed in this slide are Quarterly, Comparison Of Cloud Security, Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity
Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat IntensityMentioned slide displays phase model that can be used by an organization to visualize corporate crisis threat intensity with respect to time. Increase audience engagement and knowledge by dispensing information using Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity. This template helps you present information on four stages. You can also present information on Strategic Crisis, Threat To Viability, Liquidity Crisis, Insolvency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
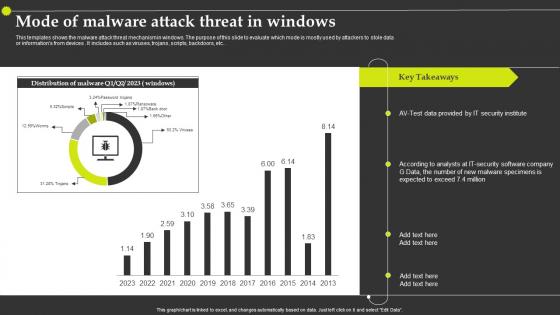 Mode Of Malware Attack Threat In Windows
Mode Of Malware Attack Threat In WindowsThis templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices . It includes such as viruses, trojans, scripts, backdoors, etc.Introducing our Mode Of Malware Attack Threat In Windows set of slides. The topics discussed in these slides are Security Institute, Malware Specimens, Security Software Company. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview
Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace OverviewThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Employees, Financial, Records using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats Management Dashboard Managing It Threats At Workplace Overview
Cyber Threats Management Dashboard Managing It Threats At Workplace OverviewThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Present the topic in a bit more detail with this Cyber Threats Management Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Rating, Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview
Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Present the topic in a bit more detail with this Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Cybersecurity, Management, Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview
Financial Performance Tracking Dashboard Managing It Threats At Workplace OverviewThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Present the topic in a bit more detail with this Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Receivables, Revenue, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Reporting Dashboard Managing IT Threats At Workplace Overview
Incident Reporting Dashboard Managing IT Threats At Workplace OverviewThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Incident Reporting Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Assignee, Resolved, Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview
Statistics Associated To Workplace Threats Managing IT Threats At Workplace OverviewThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Statistics, Workplace, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.





