Powerpoint Templates and Google slides for Threats Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Identifying Threats As A Step For Cybersecurity Risk Identification Training Ppt
Identifying Threats As A Step For Cybersecurity Risk Identification Training PptPresenting Identifying Threats as a Step for Cybersecurity Risk Identification. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V
Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V. Dispense information and present a thorough explanation of Likelihood Of Occurring, Mitigation Plan, Inaccurate Forecasting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats
Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And ThreatsThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats. Dispense information and present a thorough explanation of System Misconfigurations, Continuous Integration And Development, Supply Chain Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS V
Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS V. Dispense information and present a thorough explanation of Risk Analysis, Potential, Disruptions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS V
Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS V. Dispense information and present a thorough explanation of Likelihood Of Occurring, Severity, Mitigation Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks Management
Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks ManagementThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Vulnerability, Threat Source, Appropriate Structure, Privilege Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks Management
Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks ManagementThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes elements such as reputational damage, theft, financial losses, fines etc. Introducing Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Financial Losses, Security Threats, using this template. Grab it now to reap its full benefits.
-
 Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V
Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Attack Vectors, Causes, using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Analyzing Risk Probabilities With Impact Matrix BCT SS V
Cyber Threats In Blockchain Analyzing Risk Probabilities With Impact Matrix BCT SS VThe following slide showcases blockchain cybersecurity risk probabilities matrix. it includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Analyzing Risk Probabilities With Impact Matrix BCT SS V Dispense information and present a thorough explanation of Private Key, Digital Wallets, Smart Contracts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
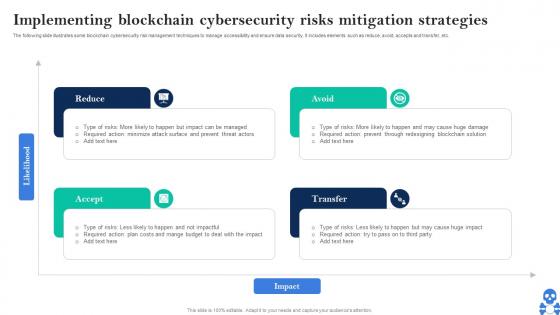 Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V
Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Introducing Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reduce, Avoid, Transfer, Accept using this template. Grab it now to reap its full benefits.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process
Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management ProcessThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Deliver an outstanding presentation on the topic using this Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Threat, Threat Source, Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process
Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management ProcessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Present the topic in a bit more detail with this Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Cloud Security Risks And Threats Next Generation CASB
Emerging Cloud Security Risks And Threats Next Generation CASBThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats Next Generation CASB Use it as a tool for discussion and navigation on Virtual Private Networks, System Misconfigurations, Perimeter Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment
Analyze And Rank Impact Of Cyber Threat Cyber Risk AssessmentThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment Use it as a tool for discussion and navigation on Framework, Appropriate Structure, Internet Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
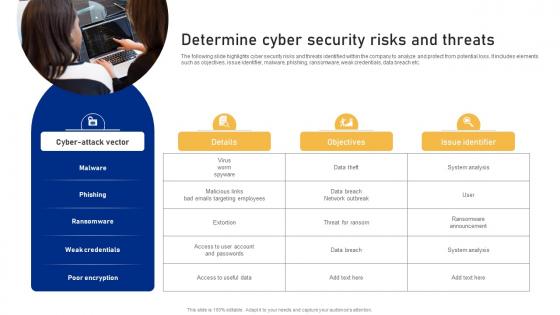 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment
Identify Threat And Vulnerabilities Within Information System Cyber Risk AssessmentThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Introducing Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on No Framework, Monitor User Behavior, Vulnerability using this template. Grab it now to reap its full benefits.
-
 Determine Cyber Security Risks And Threats Creating Cyber Security Awareness
Determine Cyber Security Risks And Threats Creating Cyber Security AwarenessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Human Errors, Factor Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Company Profile SWOT Analysis Threats CP SS V
Risk Management Company Profile SWOT Analysis Threats CP SS VFollowing slide provides information about threats faced by company. It includes threats such as high competition, economic decline, regulatory and legal risk. Increase audience engagement and knowledge by dispensing information using Risk Management Company Profile SWOT Analysis Threats CP SS V. This template helps you present information on Four stages. You can also present information on Strengths, Weaknesses, Opportunities, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Cloud Security Risks And Threats CASB Cloud Security
Emerging Cloud Security Risks And Threats CASB Cloud SecurityThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats CASB Cloud Security. Use it as a tool for discussion and navigation on System Misconfigurations, Lack Of Edge Or Perimeter Security, Risks And Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V
Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various data sources that are leveraged by ChatGPT for threat intelligence to tack cyber attack on organization. Various data sources for threat intelligence are security blogs, social media and security forums. Introducing Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Blogs, Security Forums, Security Media, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V
Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS VThis slide showcases threat intelligence overview which can help organization to tackle the cyber attack. It also highlights key importance of threat intelligence that are tackle ongoing attacks, make informed decisions, formulate threat mitigation strategies etc. Present the topic in a bit more detail with this Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V. Use it as a tool for discussion and navigation on Security Operation Center, Security Analyst, Computer Security Incident Response Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Matrix To Mitigate Threats Implementing Crisis Management Plan For Potential Risk DTE SS
Risk Management Matrix To Mitigate Threats Implementing Crisis Management Plan For Potential Risk DTE SSThis slide presents a risk management matrix template, ranking identified risks by severity, likelihood, and level, including department-specific mitigation strategies in a concise format.Deliver an outstanding presentation on the topic using this Risk Management Matrix To Mitigate Threats Implementing Crisis Management Plan For Potential Risk DTE SS. Dispense information and present a thorough explanation of Risk Severity, Risk Likelihood, Risk Level, Mitigation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS
Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SSThis slide represents best practices for mitigating threats that originate from within the targeted organization. It includes best practices such as perform enterprise-wide risk assessment etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enforce Policies And Controls, Establish Physical Security, Harden Network Perimeter Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Optimizing Project Success Rates Risk Registers For Identifying Potential Threats PM SS
Optimizing Project Success Rates Risk Registers For Identifying Potential Threats PM SSThis slide shows risk register for the different potential risks associated with the project auditing process with different amount of impacts. It includes different threats such as unavailability of key team members, incomplete and inaccurate information and regulatory changes affecting the project scope, etc. Present the topic in a bit more detail with this Optimizing Project Success Rates Risk Registers For Identifying Potential Threats PM SS. Use it as a tool for discussion and navigation on Probability, Impact, Mitigation Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process of threat risk modeling presentation pictures
Process of threat risk modeling presentation picturesPresenting process of threat risk modeling presentation pictures. This is a process of threat risk modeling presentation pictures. This is a six stage process. The stages in this process are identify vulnerabilities, decompose application, risk, application overview, possibility, impact, farming.
-
 Process of threat risk modeling diagram powerpoint images
Process of threat risk modeling diagram powerpoint imagesPresenting process of threat risk modeling diagram powerpoint images. This is a process of threat risk modeling diagram powerpoint images. This is a five stage process. The stages in this process are risk, impact, degree of mitigating, exploitability, damage potential, possibility, identify vulnerabilities, application overview, identify threats, decompose application.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat compliance dashboard with risk and standard control
Cyber threat compliance dashboard with risk and standard controlThe following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Introducing our Cyber Threat Compliance Dashboard With Risk And Standard Control set of slides. The topics discussed in these slides are Risk Control Issue, Review Effectiveness, Regulation Control Issue. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat dashboard with current risks and security service
Cyber threat dashboard with current risks and security serviceThe following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Presenting our well structured Cyber Threat Dashboard With Current Risks And Security Service. The topics discussed in this slide are Current Risks, Current Threats, Security Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
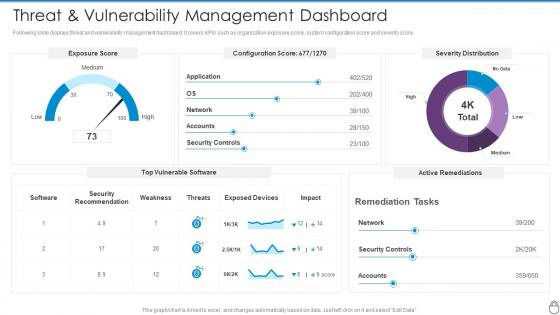 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management current potential implications faced by firm threats
Cyber security risk management current potential implications faced by firm threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Security Risk Management Current Potential Implications Faced By Firm Threats. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management cyber threats management dashboard
Cyber security risk management cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks, Threshold Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Dashboard Of It Department With Threat Frequency
Risk Management Dashboard Of It Department With Threat FrequencyThis slide shows dashboard of risk management of IT department representing net critical risks, threat and vulnerability frequency in last 60 days, open audit findings, open and vendor risks etc. Presenting our well-structured Risk Management Dashboard Of It Department With Threat Frequency. The topics discussed in this slide are Open Risks, Risk Organization Level, Net Critical Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Risk Management Dashboard For Tracking Threats And Attacks
Digital Risk Management Dashboard For Tracking Threats And AttacksThe purpose of this slide is to represent dashboard to monitor risks and cyber threats for efficient risk management. It includes various types of key performance indicators such as types of risks, severities, sources and risk meter. Introducing our Digital Risk Management Dashboard For Tracking Threats And Attacks set of slides. The topics discussed in these slides are Severities, Types Of Risk This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat management workplace how financial risk can be controlled
Cyber threat management workplace how financial risk can be controlledThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using Cyber Threat Management Workplace How Financial Risk Can Be Controlled. This template helps you present information on three stages. You can also present information on Handling Liquidity Risk, Handling Foreign Exchange Risk, Handling Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risks involved and mitigation strategies minimize cybersecurity threats in healthcare company
Risks involved and mitigation strategies minimize cybersecurity threats in healthcare companyThe slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Present the topic in a bit more detail with this Risks Involved And Mitigation Strategies Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Intellectual Property Risk, Malware Infection Risk, Customer Churn Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining security threats effective information security risk management process
Defining security threats effective information security risk management processThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.Introducing Defining Security Threats Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Mitigation plan for threat effective information security risk management process
Mitigation plan for threat effective information security risk management processMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver an outstanding presentation on the topic using this Mitigation Plan For Threat Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Resources Required, Expected Resolution Time, Communication Mode using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icon showcasing data availability security against risks and threats
Icon showcasing data availability security against risks and threatsPresenting our set of slides with Icon Showcasing Data Availability Security Against Risks And Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Showcasing Data Availability Security Against Risks And Threats.
-
 How financial risk can be controlled managing critical threat vulnerabilities and security threats
How financial risk can be controlled managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on three stages. You can also present information on Liquidity Risk, Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat management action plan risk ppt powerpoint formates icons slides
Threat management action plan risk ppt powerpoint formates icons slidesThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Risk Ppt Powerpoint Formates Icons Slides. Use it as a tool for discussion and navigation on Risk Treated, Risk Rating, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management action plan risk corporate security management
Threat management action plan risk corporate security managementThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Risk Corporate Security Management. Use it as a tool for discussion and navigation on Threat Management Action Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat drivers and emerging managing cyber risk in a digital age
Threat drivers and emerging managing cyber risk in a digital ageMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Introducing Threat Drivers And Emerging Managing Cyber Risk In A Digital Age to increase your presentation threshold. Encompassed with threee stages, this template is a great option to educate and entice your audience. Dispence information on Internet Of Things, Artificial Intelligence, Human Machine Interface, using this template. Grab it now to reap its full benefits.
-
 Threat vulnerability asset matrix managing cyber risk in a digital age
Threat vulnerability asset matrix managing cyber risk in a digital ageMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Threat Vulnerability Asset Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management framework for threat protection
Cyber security risk management framework for threat protectionThis slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting our set of slides with Cyber Security Risk Management Framework For Threat Protection. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Governance, Security Assessment, Independent Audit.
-
 Cyber threat report with risk indicator and affected systems
Cyber threat report with risk indicator and affected systemsPresenting our well structured Cyber Threat Report With Risk Indicator And Affected Systems. The topics discussed in this slide are Risk Level, Risk Indication, Potential Affected Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security
Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security.Increase audience engagement and knowledge by dispensing information using Risk Based Methodology To Cyber Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security security This template helps you present information on one stage. You can also present information on Artificial Intelligence, Human Machine Interface, Internet Of Things using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk threat vulnerability ppt powerpoint presentation portfolio graphics design cpb
Risk threat vulnerability ppt powerpoint presentation portfolio graphics design cpbPresenting our Risk Threat Vulnerability Ppt Powerpoint Presentation Portfolio Graphics Design Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Risk Threat Vulnerability. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.




