Powerpoint Templates and Google slides for Threats
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
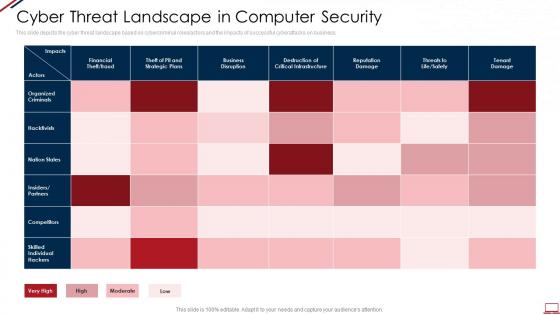 Computer system security cyber threat landscape in computer security
Computer system security cyber threat landscape in computer securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Computer System Security Cyber Threat Landscape In Computer Security. Use it as a tool for discussion and navigation on Financial, Business, Tenant Damage, Organized Criminals, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security latest threats in computer security
Computer system security latest threats in computer securityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Increase audience engagement and knowledge by dispensing information using Computer System Security Latest Threats In Computer Security. This template helps you present information on three stages. You can also present information on Dridex Malware, Romance Scams, Emotet Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security types of threats in computer security
Computer system security types of threats in computer securityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Computer System Security Types Of Threats In Computer Security. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Threats Cyber Security In Powerpoint And Google Slides Cpb
Security Threats Cyber Security In Powerpoint And Google Slides CpbPresenting Security Threats Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Threats Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Security Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting our Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Threats Vulnerabilities. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Confidential Computing Market In And Out Scope Threat Vectors For Confidential Computing
Confidential Computing Market In And Out Scope Threat Vectors For Confidential ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Deliver an outstanding presentation on the topic using this Confidential Computing Market In And Out Scope Threat Vectors For Confidential Computing. Dispense information and present a thorough explanation of Confidential, Computing, Production using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Gathering And Analyzing Threat Intelligence How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Gathering And Analyzing Threat Intelligence How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various data sources that are leveraged by ChatGPT for threat intelligence to tack cyber attack on organization. Various data sources for threat intelligence are security blogs, social media and security forums. Introducing Gathering And Analyzing Threat Intelligence How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security, Information, Updates, using this template. Grab it now to reap its full benefits.
-
 How ChatGPT Can Strengthen Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
How ChatGPT Can Strengthen Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases ChatGPT usage for threat intelligence for tackling cyber attacks on organizations. Its key elements are generate threat reports, analyze threat intelligence data and answer threat related queries. Introducing How ChatGPT Can Strengthen Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Reports, Intelligence, Queries, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Overview And Importance Of Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases threat intelligence overview which can help organization to tackle the cyber attack. It also highlights key importance of threat intelligence that are tackle ongoing attacks, make informed decisions, formulate threat mitigation strategies etc. Present the topic in a bit more detail with this Overview And Importance Of Threat How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. Use it as a tool for discussion and navigation on Security, Behavior, Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Business Threats Strategic Plan For Company Growth Strategy SS V
Competitive Business Threats Strategic Plan For Company Growth Strategy SS VThis slide showcases strengths analysis comparison matrix of own business and competitors to identify risks. It assess businesses based on competition, economic downtowns, change in regulations, technology evolution, supply chain disruptions.Introducing Competitive Business Threats Strategic Plan For Company Growth Strategy SS V to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Product Portfolio Focusing, Brand Recognition, Customer Retention, using this template. Grab it now to reap its full benefits.
-
 Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook
Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook. Use it as a tool for discussion and navigation on Stakeholders, Overview, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern Network
Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern NetworkThis slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Deliver an outstanding presentation on the topic using this Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern Network. Dispense information and present a thorough explanation of Traditional Firewall Systems, Compromised Systems, Potential Threats, Network Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall As A Service Fwaas Threats Mitigation Through Firewall As A Service
Firewall As A Service Fwaas Threats Mitigation Through Firewall As A ServiceThis slide outlines the threats that can be avoided by installing Firewall-as-a-Service around the organizational networks. The purpose of this slide is to explain how FWaaS assist in establishing security filters to avoid threats such as backdoors, macros, spam etc. Increase audience engagement and knowledge by dispensing information using Firewall As A Service Fwaas Threats Mitigation Through Firewall As A Service. This template helps you present information on five stages. You can also present information on Execute Harmful Software, Service Interruption, Confidential Data, Firewall As A Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Threat Prevention Quarterly Action Plan
IT Threat Prevention Quarterly Action PlanThis slide represents quarterly action plan for prevention from for IT threats. It further includes threats such as insider threats, viruses And worms, botnets, and ransomware. Presenting our well structured IT Threat Prevention Quarterly Action Plan. The topics discussed in this slide are Time, Priority Level, Action Taken. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Quarterly Action Plan For Cloud Security Threats
Quarterly Action Plan For Cloud Security ThreatsThis slide showcases quarterly action plan for resolving issues and threats of cloud security. It further includes cloud security threats such as unauthorized data access, DDoS, etc And respective action taken, date of completion, status, and add comments. Introducing our Quarterly Action Plan For Cloud Security Threats set of slides. The topics discussed in these slides are Quarter, Cloud Security Threats, Status. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Core Competencies Of Digital Security Threat
Core Competencies Of Digital Security ThreatThis slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management Introducing our premium set of slides with Core Competencies Of Digital Security Threat. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Development, Security, Mythology. So download instantly and tailor it with your information.
-
 Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing
Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing. This template helps you present information on four stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks, Physical Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Building Security Awareness To Minimize Cybersecurity Threats Illustration
Building Security Awareness To Minimize Cybersecurity Threats IllustrationThis colourful PowerPoint icon is a great visual aid for building security awareness among the workforce to minimize cybersecurity threats. It is designed to help educate employees on the importance of cybersecurity and how to protect their data and systems from malicious attacks.
-
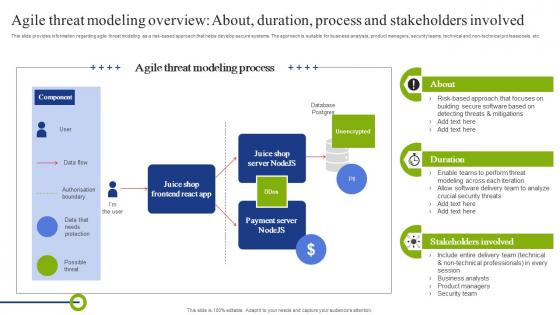 Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of Technology
Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of Technology. Dispense information and present a thorough explanation of Overview, Process, Stakeholders using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology. Use it as a tool for discussion and navigation on Collaborate, Prioritization, Initiate Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values , using this template. Grab it now to reap its full benefits.
-
 Strength WeakneSS Opportunity And Threat Swot Starbucks Marketing Strategy SS
Strength WeakneSS Opportunity And Threat Swot Starbucks Marketing Strategy SSThis slide showcases SWOT analysis of Starbucks marketing efforts which can help guide related companies about their internal and external environment. It provides details about brand recognition, pricing, diversification, competition, etc.Introducing Strength WeakneSS Opportunity And Threat Swot Starbucks Marketing Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Increasing Competition, Global Presence, Offerings Including, using this template. Grab it now to reap its full benefits.
-
 Insider Threat Information Security In Powerpoint And Google Slides Cpb
Insider Threat Information Security In Powerpoint And Google Slides CpbPresenting our Insider Threat Information Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Insider Threat Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Potential Future Threats To Microsoft Strategy Analysis To Understand Strategy Ss V
Potential Future Threats To Microsoft Strategy Analysis To Understand Strategy Ss VThis slide shows four major threats to microsoft in coming years which can effect Microsoft adversely in terms of revenues as well as brand image. It includes competition, changing customer needs, open sources projects and potential lawsuits. Introducing Potential Future Threats To Microsoft Strategy Analysis To Understand Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Customer, Source, using this template. Grab it now to reap its full benefits.
-
 Threat Of Substitute Products Or Services Microsoft Strategy Analysis To Understand Strategy Ss V
Threat Of Substitute Products Or Services Microsoft Strategy Analysis To Understand Strategy Ss VThis slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Increase audience engagement and knowledge by dispensing information using Threat Of Substitute Products Or Services Microsoft Strategy Analysis To Understand Strategy SS V. This template helps you present information on three stages. You can also present information on Factors, Influence, Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threats Of New Entrants Against Microsoft In Microsoft Strategy Analysis To Understand Strategy Ss V
Threats Of New Entrants Against Microsoft In Microsoft Strategy Analysis To Understand Strategy Ss VThis slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business. Introducing Threats Of New Entrants Against Microsoft In Microsoft Strategy Analysis To Understand Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Entrants, Microsoft, Industry, using this template. Grab it now to reap its full benefits.
-
 Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V
Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V. Dispense information and present a thorough explanation of Likelihood Of Occurring, Mitigation Plan, Inaccurate Forecasting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Threats Organizations In Powerpoint And Google Slides Cpb
Cyber Security Threats Organizations In Powerpoint And Google Slides CpbPresenting our Cyber Security Threats Organizations In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Threats Organizations. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Potential Future Threats To Microsoft Business Strategy To Stay Ahead Strategy SS V
Potential Future Threats To Microsoft Business Strategy To Stay Ahead Strategy SS VThis slide shows four major threats to Microsoft in coming years which can effect Microsoft adversely in terms of revenues as well as brand image. It includes competition, changing customer needs, open sources projects and potential lawsuits. Introducing Potential Future Threats To Microsoft Business Strategy To Stay Ahead Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Customer, Project, using this template. Grab it now to reap its full benefits.
-
 Threat Of Substitute Products Or Services Microsoft Business Strategy To Stay Ahead Strategy SS V
Threat Of Substitute Products Or Services Microsoft Business Strategy To Stay Ahead Strategy SS VThis slide shows details regarding substitute products and services which may or may not become a threat for Microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Introducing Threat Of Substitute Products Or Services Microsoft Business Strategy To Stay Ahead Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Influence, Performance, Products, using this template. Grab it now to reap its full benefits.
-
 Threats Of New Entrants Against Microsoft Business Strategy To Stay Ahead Strategy SS V
Threats Of New Entrants Against Microsoft Business Strategy To Stay Ahead Strategy SS VThis slide shows two key factors related to threat of new entry in the existing market where Microsoft is major player. These factors are high cost of brand development and moderate cost of doing business. Increase audience engagement and knowledge by dispensing information using Threats Of New Entrants Against Microsoft Business Strategy To Stay Ahead Strategy SS V. This template helps you present information on three stages. You can also present information on Influence, Technology, Contribute using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Cryptocurrency Security Threats Exploring The Role BCT SS
Common Cryptocurrency Security Threats Exploring The Role BCT SSThis slide covers major crypto security risks faced by investors and companies. It includes threats such as phishing attacks, malware and keyloggers, hacks and data breaches, social engineering, fake wallets and apps, insider threats, and unsecure smart contracts. Introducing Common Cryptocurrency Security Threats Exploring The Role BCT SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Malware And Keyloggers, Insider Threats, using this template. Grab it now to reap its full benefits.
-
 Measures To Prevent Cryptocurrency Security Threats Exploring The Role BCT SS
Measures To Prevent Cryptocurrency Security Threats Exploring The Role BCT SSThis slide covers various methods to avoid crypto security risks. It includes solutions such as phishing attacks prevention, malware and keyloggers protection, hacks and data breaches mitigation, social engineering defense, fake wallets and apps vigilance, etc. Introducing Measures To Prevent Cryptocurrency Security Threats Exploring The Role BCT SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks Prevention, Breaches Mitigation, Social Engineering Defense, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium In And Out Scope Threat Vectors For Confidential Computing
Confidential Computing Consortium In And Out Scope Threat Vectors For Confidential ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Introducing Confidential Computing Consortium In And Out Scope Threat Vectors For Confidential Computingm to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Sophisticated Physical Attacks, Cryptographic Attacks, Protocol Attacks, Physical Attacks, using this template. Grab it now to reap its full benefits.
-
 How Apple Competent Addressing Threats Associated With Apple Branding SS V
How Apple Competent Addressing Threats Associated With Apple Branding SS VThis slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Increase audience engagement and knowledge by dispensing information using How Apple Competent Addressing Threats Associated With Apple Branding SS V This template helps you present information on Four stages. You can also present information on Rigorous Competition, Lawsuits, Pandemic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Opportunities Threats Clipart In Powerpoint And Google Slides Cpb
Opportunities Threats Clipart In Powerpoint And Google Slides CpbPresenting Opportunities Threats Clipart In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Opportunities Threats Clipart. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Protect Against Internal Cyber Threats In Powerpoint And Google Slides Cpb
Protect Against Internal Cyber Threats In Powerpoint And Google Slides CpbPresenting our Protect Against Internal Cyber Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Protect Against Internal Cyber Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threat Intelligence Maturity In Powerpoint And Google Slides Cpb
Threat Intelligence Maturity In Powerpoint And Google Slides CpbPresenting our Threat Intelligence Maturity In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Threat Intelligence Maturity This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information Security Vulnerabilities Threats In Powerpoint And Google Slides Cpb
Information Security Vulnerabilities Threats In Powerpoint And Google Slides CpbPresenting Information Security Vulnerabilities Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Vulnerabilities Threats. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat Sustainability In Powerpoint And Google Slides Cpb
Threat Sustainability In Powerpoint And Google Slides CpbPresenting our Threat Sustainability In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Threat Sustainability. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cybersecurity Threats Vulnerabilities. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Challenges Threats Global Retailing In Powerpoint And Google Slides Cpb
Challenges Threats Global Retailing In Powerpoint And Google Slides CpbPresenting Challenges Threats Global Retailing In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Challenges Threats Global Retailing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 IKEA Marketing Strategy Major Threats Restricting Brand Growth Strategy SS
IKEA Marketing Strategy Major Threats Restricting Brand Growth Strategy SSThe following slide highlights year over year net income growth of IKEA to analyze annual performance summary and profitability trends. It includes elements such as net income over years along with key takeaways etc. Present the topic in a bit more detail with this IKEA Marketing Strategy Major Threats Restricting Brand Growth Strategy SS Use it as a tool for discussion and navigation on Focus Towards, Quality And Durability, Affordable Pricing Strategy, Chinese Market This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Capability Intent In Powerpoint And Google Slides Cpb
Threat Capability Intent In Powerpoint And Google Slides CpbPresenting our Threat Capability Intent In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Threat Capability Intent. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Puma Marketing Strategies Opportunities And Threats
Puma Marketing Strategies Opportunities And ThreatsThis slide showcase opportunities and threat that are been covered by puma and marketing strategies to promote and cover the threat and attain opportunities for market expansion Introducing our premium set of slides with Puma Marketing Strategies Opportunities And Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Technological Forces, Environments Forces. So download instantly and tailor it with your information.
-
 Network Security Threats In Powerpoint And Google Slides Cpb
Network Security Threats In Powerpoint And Google Slides CpbPresenting Network Security Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat Social Security In Powerpoint And Google Slides Cpb
Threat Social Security In Powerpoint And Google Slides CpbPresenting our Threat Social Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Threat Social Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Healthcare Cloud Cybersecurity Threat Mitigation Plan
Healthcare Cloud Cybersecurity Threat Mitigation PlanThis slide presents healthcare cloud cybersecurity threat mitigation plan, helpful in protecting medical records and lab results from potential threats. It includes threat level, threat and solutions for facilitating technological advancement and security. Presenting our well structured Healthcare Cloud Cybersecurity Threat Mitigation Plan. The topics discussed in this slide are Healthcare Cloud Security, Threat Level, Algorithmic Process. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Solutions For Insider Threats In Healthcare Cybersecurity
Solutions For Insider Threats In Healthcare CybersecurityThis slide presents healthcare cybersecurity plan for insider threats, helpful in highlighting main concerns and appropriate solutions for tackling risks. It includes risks, type of insider threats faced, indicators of such risks and appropriate solutions. Presenting our well structured Solutions For Insider Threats In Healthcare Cybersecurity. The topics discussed in this slide are Reputational Damage, Business Operations, Patient Trust. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Sony Company Profile SWOT Analysis Threats CP SS
Sony Company Profile SWOT Analysis Threats CP SSFollowing slides includes information about company threats from external environment. It includes threats such as intense competition and rapid technology advancement. Increase audience engagement and knowledge by dispensing information using Sony Company Profile SWOT Analysis Threats CP SS. This template helps you present information on four stages. You can also present information on Strengths, Weaknesses, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Kpi Icon Showcasing Threat Protection
Cybersecurity Kpi Icon Showcasing Threat ProtectionIntroducing our Cybersecurity Kpi Icon Showcasing Threat Protection set of slides. The topics discussed in these slides are Cybersecurity Kpi Showcasing, Threat Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Kpis Used By Threat Analysts
Cybersecurity Kpis Used By Threat AnalystsThis slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc. Presenting our set of slides with Cybersecurity Kpis Used By Threat Analysts. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cost Per Incident, Regulatory Requirements.
-
 In And Threat Vectors For Confidential Computing Confidential Computing System Technology
In And Threat Vectors For Confidential Computing Confidential Computing System TechnologyThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using In And Threat Vectors For Confidential Computing Confidential Computing System Technology. This template helps you present information on seven stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comprehensive Guide To Understand Solutions To Protect Bitcoin Against Security Threats Fin SS
Comprehensive Guide To Understand Solutions To Protect Bitcoin Against Security Threats Fin SSThis slide shows solutions to various types of threats associated with Bitcoins security which can be used by individuals to secure their digital currencies. It incudes protection against frauds such as malware attacks, fake wallets, SIM swapping, etc. Introducing Comprehensive Guide To Understand Solutions To Protect Bitcoin Against Security Threats Fin SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware Attacks, Social Engineering Attacks, Bitcoin Against Security Threats, using this template. Grab it now to reap its full benefits.
-
 Snowflake Company Profile Our Threats Ppt Icons CP SS
Snowflake Company Profile Our Threats Ppt Icons CP SSThe following slide showcases the threats to Snowflake company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition market competition and technology disruptions. Increase audience engagement and knowledge by dispensing information using Snowflake Company Profile Our Threats Ppt Icons CP SS. This template helps you present information on four stages. You can also present information on Strengths, Weakness, Opportunities, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ashok Leyland Company Profile Threats Ppt Download CP SS
Ashok Leyland Company Profile Threats Ppt Download CP SSThe following slide showcases the threats to Ashok Leyland company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as rising input costs and rising fuel prices. Increase audience engagement and knowledge by dispensing information using Ashok Leyland Company Profile Threats Ppt Download CP SS. This template helps you present information on four stages. You can also present information on Strengths, Weakness, Threats, Opportunities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Fashion Company Profile Business Threats Ppt Sample CP SS
Fashion Company Profile Business Threats Ppt Sample CP SSThe following slide showcases the threats to a fashion retail company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as changing consumer preferences, online security and privacy and supply chain disruptions. Introducing Fashion Company Profile Business Threats Ppt Sample CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weakness, Opportunity, Threats, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats
Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And ThreatsThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Emerging Cloud Security Risks And Threats. Dispense information and present a thorough explanation of System Misconfigurations, Continuous Integration And Development, Supply Chain Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction
Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon IntroductionThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction. This template helps you present information on four stages. You can also present information on Threat Protection Pillar, Cloud Access Security Broker, Machine Learning Algorithms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secops V2 Security Operations Threat Management Process
Secops V2 Security Operations Threat Management ProcessThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Deliver an outstanding presentation on the topic using this Secops V2 Security Operations Threat Management Process. Dispense information and present a thorough explanation of Extended Investigation, Preliminary Investigation, Security Operations Threat





