Powerpoint Templates and Google slides for Threats
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Features Of Cyber Threat Intelligence Tools
Features Of Cyber Threat Intelligence ToolsThis slide showcases the various characteristics of cyber threat intelligence tools such as data-driven, flexibility, comprehensiveness, etc. Introducing Features Of Cyber Threat Intelligence Tools to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on External Focused, Cyber Threat Intelligence Tools, Comprehensive, using this template. Grab it now to reap its full benefits.
-
 Features Of Strategic Cyber Threat Intelligence
Features Of Strategic Cyber Threat IntelligenceThis slide discusses the characteristics of strategic cyber threat intelligence which includes the features and objectives. Increase audience engagement and knowledge by dispensing information using Features Of Strategic Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Analyzes Geopolitics And Cybersecurity, Aids Decision Making, Guides Cybersecurity Investments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Features Of Tactical Cyber Threat Intelligence
Features Of Tactical Cyber Threat IntelligenceThis slide showcases the characteristics of tactical cyber threat intelligence which includes its features such as machine readable, automated, etc. Introducing Features Of Tactical Cyber Threat Intelligence to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Intelligence, Easily Generated, Mostly Automated, Machine Readable, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cyber Threat Intelligence
Icons Slide For Cyber Threat IntelligenceIntroducing our well researched set of slides titled Icons Slide For Cyber Threat Intelligence. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
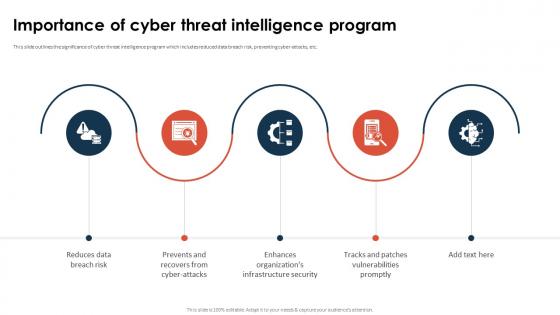 Importance Of Cyber Threat Intelligence Program
Importance Of Cyber Threat Intelligence ProgramThis slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber-attacks, etc. Increase audience engagement and knowledge by dispensing information using Importance Of Cyber Threat Intelligence Program. This template helps you present information on five stages. You can also present information on Tracks And Patches Vulnerabilities Promptly, Reduces Data Breach Risk, Prevents And Recovers From Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction Of Cyber Threat Intelligence For Data Security
Introduction Of Cyber Threat Intelligence For Data SecurityThis slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Introducing Introduction Of Cyber Threat Intelligence For Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Evolving Threats Demand Intelligence, Vital For Security Architecture, Proactively Blocks Attacks, using this template. Grab it now to reap its full benefits.
-
 Key Objectives Of Cyber Threat Intelligence
Key Objectives Of Cyber Threat IntelligenceThis slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Increase audience engagement and knowledge by dispensing information using Key Objectives Of Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Robust Fraud Prevention, Powerful Vulnerability Management, Effective Security Operations, Efficient Incident Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Main Benefits Of Cyber Threat Intelligence
Main Benefits Of Cyber Threat IntelligenceThis slide highlights the advantages of cyber threat intelligence which include early identification of threats, danger awareness, etc. Introducing Main Benefits Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Early Identification Of Threats, Precise Danger Awareness, Autonomous Reactions, Cyber Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Objectives Of Technical Cyber Threat Intelligence
Objectives Of Technical Cyber Threat IntelligenceThis slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Technical Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Secures Against Malicious Properties, Protects Against Control Of Systems, Block Access To Threat Actors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Primary Tools For Cyber Threat Intelligence
Primary Tools For Cyber Threat IntelligenceThis slide represents the various tools used for cyber threat intelligence along with their features and cost. Present the topic in a bit more detail with this Primary Tools For Cyber Threat Intelligence. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Isolated Browser, Data Collection Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Primary Types Of Cyber Threat Intelligence
Primary Types Of Cyber Threat IntelligenceThis slide highlights the various types if cyber threat intelligence which include strategic, operational, technical, and tactical. Introducing Primary Types Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Intelligence, Strategic, Operational, Technical, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Deploy Cyber Threat Intelligence
Roadmap To Deploy Cyber Threat IntelligenceThis slide showcases the steps that an organization should take while deploying cyber threat intelligence such as recognizing needs, assembling data, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Deploy Cyber Threat Intelligence. This template helps you present information on seven stages. You can also present information on Assemble Data Sources, Recognize Needs And Goals, Gathering And Analyzing Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Build Cyber Threat Intelligence Framework
Steps To Build Cyber Threat Intelligence FrameworkThis slide outlines the process phases to construct cyber threat intelligence framework such as threat vector identification, compiling intelligence, etc. Introducing Steps To Build Cyber Threat Intelligence Framework to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Threat Vector Identification, Compile Intelligence, Cyber Threat Intelligence Framework, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Threat Intelligence Reports
Strategic Cyber Threat Intelligence ReportsThis slide represents what all is included in strategic cyber threat intelligence reports such as policy documents, research reports, etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Threat Intelligence Reports. This template helps you present information on five stages. You can also present information on Policy Documents, Whitepaper And Research Reports, Data Loss Statistics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Cyber Threat Intelligence
Table Of Contents Cyber Threat IntelligenceIntroducing Table Of Contents Cyber Threat Intelligence to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Introduction, Importance, Benefits, Objectives, Cyber Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cyber Threat Intelligence
Table Of Contents For Cyber Threat IntelligenceIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cyber Threat Intelligence. This template helps you present information on twelve stages. You can also present information on Cyber Threat Intelligence Overview, Framework And Deployment, Training And Budget, Relevant Use Cases using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Cyber Threat Intelligence
Use Cases Of Cyber Threat IntelligenceThis slide discusses the various use cases of cyber threat analysis which include cyber threat feeds, real time alerts, patch prioritization, etc. Introducing Use Cases Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Monitoring, Patch Prioritization, Strategic Intelligence Reporting, Operational Intelligence Reporting, using this template. Grab it now to reap its full benefits.
-
 Various Platform Of Cyber Threat Intelligence
Various Platform Of Cyber Threat IntelligenceThis slide discusses the different platforms of cyber threat intelligence which include Anomali ThreatStream, Dataminr Pulse, etc. Deliver an outstanding presentation on the topic using this Various Platform Of Cyber Threat Intelligence. Dispense information and present a thorough explanation of Visualizes Real Time Information, Automatically Updates Data Feeds, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Threat Intelligence Teams In Security Operation Center
Comparative Assessment Of Threat Intelligence Teams In Security Operation CenterThe below slide highlights the threat intelligence types that offer a foundation for establishment of security operation center. The parameters for evaluation are description, use case, and benefit. Introducing our premium set of slides with name Comparative Assessment Of Threat Intelligence Teams In Security Operation Center. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Tactical, Strategic, Operational. So download instantly and tailor it with your information.
-
 Security Operations Center Threat Level Assessment
Security Operations Center Threat Level AssessmentThe below slide provides various risks associated with security operations that helps to analyze the severity level and resolutions status. The different threats are APT, phishing, malware, ransomware, etc. Introducing our Security Operations Center Threat Level Assessment set of slides. The topics discussed in these slides are Ransomware, Malware, Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Integrate Threat Intelligence Into Security Operations Center
Steps To Integrate Threat Intelligence Into Security Operations CenterThis slide provides a monthly timeline of steps to be implemented for integration of threat intelligence into security operation center that ensures response efficiency. Key steps are define requirements, data collection, analysis, etc. Presenting our set of slides with name Steps To Integrate Threat Intelligence Into Security Operations Center. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Requirements, Analysis, Evaluate, Optimize.
-
 Emergency Preparedness Icon For Cyber Threat
Emergency Preparedness Icon For Cyber ThreatPresenting our set of slides with Emergency Preparedness Icon For Cyber Threat. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Emergency, Preparedness, Cyber Threat.
-
 Mitigating Cybersecurity Threats With Data Loss Prevention Solutions
Mitigating Cybersecurity Threats With Data Loss Prevention SolutionsThis slide represents various data loss prevention strategies that assist companies in mitigating multiple cybersecurity threats to enhance information protection. It includes threats such as extrusion, insider threats, and unintended exposure. Introducing our Mitigating Cybersecurity Threats With Data Loss Prevention Solutions set of slides. The topics discussed in these slides are Extrusion, Insider Threats, Unintended Exposure. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Based Mobile Security Threats Mobile Security
Application Based Mobile Security Threats Mobile SecurityThis slide represents the different types of application based mobile security threats which include malicious apps, fake or clone apps and app spoofing. Increase audience engagement and knowledge by dispensing information using Application Based Mobile Security Threats Mobile Security This template helps you present information on Five stages. You can also present information on Simplicity, Ubiquitousness, Cost Effective using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Threats Addressed By Two Factor Authentication Mobile Security
Common Threats Addressed By Two Factor Authentication Mobile SecurityThis slide discusses the common threats addressed by two factor authentication which includes stolen passwords, social engineering, key logging, etc. Increase audience engagement and knowledge by dispensing information using Common Threats Addressed By Two Factor Authentication Mobile Security This template helps you present information on Six stages. You can also present information on Sandbox Isolation, Robust Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Mobile Security Threats Mobile Security
Various Types Of Mobile Security Threats Mobile SecurityThis slide outlines the different types of mobile security threats which includes malicious apps and websites, mobile ransomware, phishing and MITM attacks. Increase audience engagement and knowledge by dispensing information using Various Types Of Mobile Security Threats Mobile Security This template helps you present information on Five stages. You can also present information on Phishing Website, Victim, Legitimate Website using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Vs Opportunity Matrix As Tool For Change Management CM SS
Threat Vs Opportunity Matrix As Tool For Change Management CM SSThe slide introduces a threat vs. opportunity matrix as a tool for change management. The purpose is to present a visual framework that allows organizations to assess and categorize elements of change as either threats or opportunities. Introducing Threat Vs Opportunity Matrix As Tool For Change Management CM SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Opportunities, Threats, Enhanced Efficiency, Reduced Errors, using this template. Grab it now to reap its full benefits.
-
 Threats Faced In Fintech Cyber Security
Threats Faced In Fintech Cyber SecurityThis slide showcases the threats faced in fintech cyber security. Its use is to face threats in fintech cyber security and help protect against zero day attacks. This slide includes spoofing, ransomware, organisation, malware, etc. Introducing our premium set of slides with name Threats Faced In Fintech Cyber Security. Ellicudate the nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like DDOS, Advanced Threats, Phishing, Sniffing, Malware. So download instantly and tailor it with your information.
-
 Wireless LAN Security Threats And Tactics Wireless LAN Controller
Wireless LAN Security Threats And Tactics Wireless LAN ControllerThe purpose of this slide is to highlight the wireless LAN security threats and tactics such as IP and MAC spoofing, DODOS botnets and name in the middle attacks, etc. Present the topic in a bit more detail with this Wireless LAN Security Threats And Tactics Wireless LAN Controller. Use it as a tool for discussion and navigation on Deceiving Connected Clients, Distributed Denial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Solutions For Threat Of Cyber Security In Digital Banking
Solutions For Threat Of Cyber Security In Digital BankingThis slide represents remedies to cyber security problem in internet banking. It aims to adopt holistic and proactive approach to cyber security that encompasses technology, processes, and people. It includes various solutions such as integrated security, protecting information, etc. Introducing our premium set of slides with Solutions For Threat Of Cyber Security In Digital Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Integrated Security, Security Integration, Spent Money. So download instantly and tailor it with your information.
-
 Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS
Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SSThis slide represents best practices for mitigating threats that originate from within the targeted organization. It includes best practices such as perform enterprise-wide risk assessment etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enforce Policies And Controls, Establish Physical Security, Harden Network Perimeter Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS
Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SSThis slide represents details related to training program for mitigating threats that arises from within the targeted organization. It includes details related to mode of training, key learnings etc. Introducing Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Insider Threats Awareness, Training Program, Key Learnings, Mitigating Threats, using this template. Grab it now to reap its full benefits.
-
 IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS
IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SSThis slide represents details related to ways security awareness training helps in preventing and mitigating common threats faced by organization such as data breaches, phishing attacks etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS. Dispense information and present a thorough explanation of Data Breaches, Phishing Attacks, Insider Threats, Social Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS
Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SSThis slide represents objectives of providing training for mitigating treats that originates from within the targeted organization. It includes objectives such as identify and report behaviors of insider threats etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Unintentional Insider Threats, Malicious Or Unintentional Insider, Public And National Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS
Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases deploying endpoint detection and response EDR for advanced threat protection. It provides details about alert triage, containment, incident data search, etc.Deliver an outstanding presentation on the topic using this Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Advanced Threat Detection, Incident Data Search, Alert Triage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS
Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security information and event management SIEM tools which can help endpoint security teams detect and address potential security threats.Present the topic in a bit more detail with this Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Collection, Detection, Investigation, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Existing Web Security Infrastructure Threats
Web Security Upgradation Existing Web Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Present the topic in a bit more detail with this Web Security Upgradation Existing Web Security Infrastructure Threats. Use it as a tool for discussion and navigation on Constituents, Problems Observed, Number Of Problems Observed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 AI Chatbot Security Threat Icon
AI Chatbot Security Threat IconPresenting our set of slides with AI Chatbot Security Threat Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Chatbot Security, Threat Icon.
-
 Potential Security Threats To Ai Chatbots
Potential Security Threats To Ai ChatbotsThis slide shows extensive information regarding multiple types of security threats associated with artificial intelligence-powered chatbots. These chatbot threats are ransomware, malware, and phishing. It also includes potential impact of these threats. Introducing our premium set of slides with Potential Security Threats To Ai Chatbots. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ransomware, Malware, Phishing. So download instantly and tailor it with your information.
-
 Addressing Wireless Lan Security Threats And Vulnerabilities
Addressing Wireless Lan Security Threats And VulnerabilitiesThis slide showcases the security strategies that help companies to mitigate wireless LAN threats and vulnerabilities effectively. It includes threads such as IP, MAC spoofing, DNS cache spoofing, and Rogueevil twin access points. Introducing our Addressing Wireless Lan Security Threats And Vulnerabilities set of slides. The topics discussed in these slides are Threats And Vulnerabilities, Details, Security StrategiesThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hacking Threat Icon Affecting Wireless Lan Security
Hacking Threat Icon Affecting Wireless Lan SecurityPresenting our set of slides with Hacking Threat Icon Affecting Wireless Lan Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hacking Threat Icon Affecting, Wireless LAN Security
-
 Cyber Crisis Management Icon For Threat Mitigation
Cyber Crisis Management Icon For Threat MitigationIntroducing our premium set of slides with name Cyber Crisis Management Icon For Threat Mitigation. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Crisis Management, Threat Mitigation. So download instantly and tailor it with your information.
-
 Environment Threat Opportunity Analysis Of Education Sector
Environment Threat Opportunity Analysis Of Education SectorThis slide highlights ETOP analysis of the education sector to identify factors that impact educational institutions. It includes environmental sectors such as economic, market, political etc. Introducing our Environment Threat Opportunity Analysis Of Education Sector set of slides. The topics discussed in these slides are Economic, Market, Political, Social. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Environment Threat Opportunity Profile Of Textile Industry
Environment Threat Opportunity Profile Of Textile IndustryThis slide outlines ETOP analysis of the textile industry to to assess external factors impacting sustainability and competitiveness. It includes environmental threat and opportunities in textile market segment. Introducing our premium set of slides with name Environment Threat Opportunity Profile Of Textile Industry. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Environmental Threat, Environmental Opportunities. So download instantly and tailor it with your information.
-
 Environmental Threat Opportunity Profile Analysis Icon
Environmental Threat Opportunity Profile Analysis IconIntroducing our Environmental Threat Opportunity Profile Analysis Icon set of slides. The topics discussed in these slides are Environmental, Threat, Opportunity, Profile Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Environmental Threat Opportunity Profile Factors
Environmental Threat Opportunity Profile FactorsThis slide covers the factors involved in ETOP analysis to assess risks and opportunities posed by environmental factors on business operations. It includes economic factors, technological factors, political factors, etc. Introducing our premium set of slides with name Environmental Threat Opportunity Profile Factors. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Economical Factors, Political Factors, Social Factors. So download instantly and tailor it with your information.
-
 Healthcare Environmental Threat Opportunity Profile
Healthcare Environmental Threat Opportunity ProfileThis slide covers an environmental threat opportunity profile analysis of healthcare sector to identify external factors impacting the industrys growth and sustainability. Introducing our premium set of slides with name Healthcare Environmental Threat Opportunity Profile. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Environmental Opportunities, Environmental Threat. So download instantly and tailor it with your information.
-
 Strategies For Environmental Threat Opportunity Profile Analysis
Strategies For Environmental Threat Opportunity Profile AnalysisThis slide highlights key tactics for environmental threat opportunity profile analysis. It includes strategies such as matching strategy, conversion strategy, defence strategies etc Introducing our premium set of slides with name Strategies For Environmental Threat Opportunity Profile Analysis. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Matching Strategies, Neutralization Strategies, Defence Strategies, Conversion Strategies. So download instantly and tailor it with your information.
-
 Various Common Threats In Web Security Solution
Various Common Threats In Web Security SolutionThis slide outlines the different hazards in web security which include ransomware, malware, phishing, SQL injection, and so on. Introducing Various Common Threats In Web Security Solution to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Malware, Phishing, Sql Injection, Denial Of Service, using this template. Grab it now to reap its full benefits.
-
 Web Security Threats And Possible Solutions
Web Security Threats And Possible SolutionsThis slide showcases the problems and possible solutions of web security. The threats include code injection, data breach, etc. Present the topic in a bit more detail with this Web Security Threats And Possible Solutions. Use it as a tool for discussion and navigation on Threats, Solutions, Code Injection, Data Breach, Malware Infection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatSecure your digital assets with our Cloud-based endpoint cyber security icon for PowerPoint. Featuring a bold and vibrant design, this icon represents the protection and peace of mind offered by our cutting-edge security solutions. Perfect for presentations on cloud security, data protection, and cyber threats. Download now and enhance your slides.
-
 Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents a cloud-based endpoint cyber security solution. It is designed to protect your digital assets from external threats, providing real-time monitoring and threat detection. With its user-friendly interface and advanced features, it offers a comprehensive and reliable solution for safeguarding your data and devices.
-
 Cyber Threats Digital Resilience Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threats Digital Resilience Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your digital transformation journey with our vibrant cyber security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of protecting your digital assets. Perfect for presentations and reports on cyber security, this icon will add a professional touch to your content.
-
 Cyber Threats Digital Resilience Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threats Digital Resilience Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is designed to represent cyber security in the context of digital transformation. It features a simple yet impactful design, making it perfect for use in presentations, reports, and other digital materials related to cyber security and its role in modern technology.
-
 Disaster Management Threat Response Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Disaster Management Threat Response Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Emergency Response Plan icon for security threats is a must-have for any presentation or document related to emergency preparedness. The bright and bold color scheme makes it easily visible and recognizable, while the clear design conveys the importance of having a plan in place for potential security threats.
-
 Disaster Management Threat Response Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Disaster Management Threat Response Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon features an Emergency response plan icon for security threats. It is designed to visually represent the importance of having a plan in place to respond to potential security threats. The simple yet impactful design makes it suitable for use in presentations and documents related to emergency preparedness and security protocols.
-
 Threat Intelligence Security Analytics Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Intelligence Security Analytics Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents EDR solutions for monitoring threat detection. It is designed to provide a visual representation of the product, showcasing its features and benefits. The icon is perfect for use in presentations, reports, and marketing materials related to cybersecurity and threat detection.
-
 Threat Intelligence Security Analytics Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Intelligence Security Analytics Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon represents EDR solutions for monitoring threat detection. It is a powerful tool for businesses to stay ahead of potential cyber threats and keep their data safe. With its sleek and professional design, this icon is perfect for presentations and marketing materials related to EDR solutions.
-
 Web Security Threat Prevention Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Web Security Threat Prevention Colored Icon In Powerpoint Pptx Png And Editable Eps FormatProtect your digital assets with our Web Security PowerPoint icon. Featuring a bold and vibrant design, this icon serves as a visual reminder to stay vigilant against cyber attacks. Use it to enhance your presentations on online safety and safeguard your business from potential threats.
-
 Web Security Threat Prevention Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Web Security Threat Prevention Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to represent the importance of web security in preventing cyber attacks. With its sleek and minimalistic design, it serves as a visual reminder to prioritize online safety. Use it in your presentations to educate and raise awareness about the need for strong web security measures.





