Powerpoint Templates and Google slides for Threat Risk Assessment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V
Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Attack Vectors, Causes, using this template. Grab it now to reap its full benefits.
-
 Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment
Analyze And Rank Impact Of Cyber Threat Cyber Risk AssessmentThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment Use it as a tool for discussion and navigation on Framework, Appropriate Structure, Internet Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
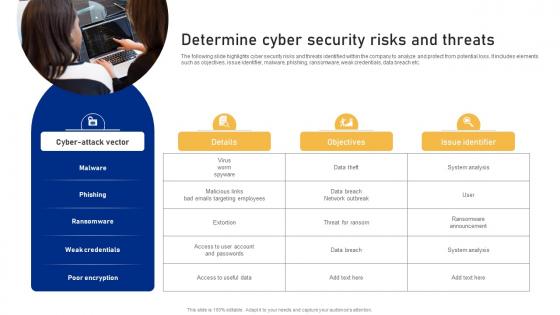 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment
Identify Threat And Vulnerabilities Within Information System Cyber Risk AssessmentThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Introducing Identify Threat And Vulnerabilities Within Information System Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on No Framework, Monitor User Behavior, Vulnerability using this template. Grab it now to reap its full benefits.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment risk assessment ppt powerpoint presentation portfolio grid cpb
Threat assessment risk assessment ppt powerpoint presentation portfolio grid cpbPresenting Threat Assessment Risk Assessment Ppt Powerpoint Presentation Portfolio Grid Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Assessment Risk Assessment. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber security risk management comparative assessment various threat agents
Cyber security risk management comparative assessment various threat agentsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Comparative Assessment Various Threat Agents. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Acceptance Icon Indicating Threat Assessment
Risk Acceptance Icon Indicating Threat AssessmentPresenting our set of slides with name Risk Acceptance Icon Indicating Threat Assessment. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Acceptance, Icon, Indicating Threat Assessment.
-
 Identifying Information Security Threats And Risk Assessment And Management Plan For Information Security
Identifying Information Security Threats And Risk Assessment And Management Plan For Information SecurityThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Deliver an outstanding presentation on the topic using this Identifying Information Security Threats And Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Organization, Errors And Omissions, Employee Sabotage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security
Matrix For Threat Solution And Risk Assessment And Management Plan For Information SecurityThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Protocols, Management, Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Risk Identification
Threat Identification And Vulnerability Assessment For Risk IdentificationThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment For Risk Identification. Use it as a tool for discussion and navigation on Identification, Vulnerability, Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Scorecard For Strategic Threat
Risk Assessment Scorecard For Strategic ThreatThis slide shows scorecard for procurement of risk assessment used by organizations to eliminate potential threats. This slide provides data regarding area, scorecard criteria, risk rating scale, remarks, area wise weight and rating, week to date rating and overall rating. Introducing our Risk Assessment Scorecard For Strategic Threat set of slides. The topics discussed in these slides are Scorecard Criteria, Supply Risk Rating, Strategic Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat Risk Assessment In Powerpoint And Google Slides Cpb
Threat Risk Assessment In Powerpoint And Google Slides CpbPresenting our Threat Risk Assessment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Threat Risk Assessment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
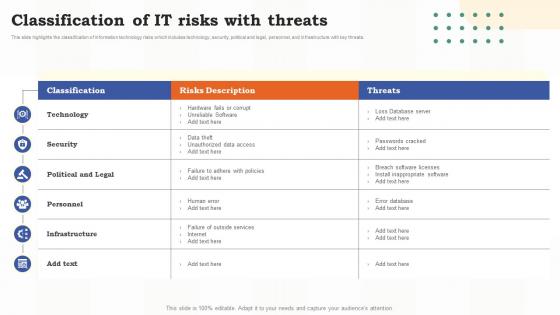 Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides Backgrounds
Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides BackgroundsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides Backgrounds. Use it as a tool for discussion and navigation on Technology, Political And Legal, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems
Information Technology Risks Form Human Threat Source Risk Assessment Of It SystemsThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Information, Technology, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction
It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides IntroductionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction. Use it as a tool for discussion and navigation on Vulnerabilities, Source, Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level
Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat LevelThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level. Use it as a tool for discussion and navigation on Treat Level, Vulnerability Level, Risk Assessment Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan
Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Vulnerability Severity, Threat Source, Risk Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat
Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And ThreatThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat. Dispense information and present a thorough explanation of Assessment, Vulnerability, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan
Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity PlanThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Assessment Matrix, Vulnerability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Market Abuse Risk Assessment Template In Powerpoint And Google Slides Cpb
Market Abuse Risk Assessment Template In Powerpoint And Google Slides CpbPresenting Market Abuse Risk Assessment Template In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Market Abuse Risk Assessment Template. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat risk assessment ppt powerpoint presentation gallery slide cpb
Threat risk assessment ppt powerpoint presentation gallery slide cpbPresenting this set of slides with name Threat Risk Assessment Ppt Powerpoint Presentation Gallery Slide Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Threat Risk Assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Operational Risk Management Risk Register To Assess Operational Threats
Operational Risk Management Risk Register To Assess Operational ThreatsThis slide shows the risk register to identify and analyze the probability and impact of the risks associated with day to day business operations of the organization. It includes details related to risk category, description, probability, impact etc. Present the topic in a bit more detail with this Operational Risk Management Risk Register To Assess Operational Threats. Use it as a tool for discussion and navigation on Risk Register, Assess Operational Threats, Consequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Digital Safety Threat And Risk Assessment
Checklist For Digital Safety Threat And Risk AssessmentThis slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Introducing our Checklist For Digital Safety Threat And Risk Assessment set of slides. The topics discussed in these slides are Conduct Assessment, Perform Threat Analysis, Result And Completion. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Safety Threat And Risk Assessment Matrix
Digital Safety Threat And Risk Assessment MatrixThis slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Introducing our Digital Safety Threat And Risk Assessment Matrix set of slides. The topics discussed in these slides are Information Misuse, Malicious Attacks, Assessment Matrix. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Insider threat risk assessment ppt powerpoint presentation outline objects cpb
Insider threat risk assessment ppt powerpoint presentation outline objects cpbPresenting Insider Threat Risk Assessment Ppt Powerpoint Presentation Outline Objects Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Insider Threat Risk Assessment. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat identification assessment information security risk management program
Threat identification assessment information security risk management programThreat Agent, Potential Vulnerability, Vulnerability Ranking Deliver an outstanding presentation on the topic using this Threat Identification Assessment Information Security Risk Management Program. Dispense information and present a thorough explanation of Threat Agent, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



