Powerpoint Templates and Google slides for Threat Response
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Managed Detection And Response Dashboard For Tracking Threats
Managed Detection And Response Dashboard For Tracking ThreatsThis slide showcases MDR dashboard for remediation threats. The main purpose of this template is risk-level threats and threat performance. This includes threats, performance of threat, asset group of threats, etc. Presenting our well structured Managed Detection And Response Dashboard For Tracking Threats. The topics discussed in this slide are Managed, Response, Tracking. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Triage Cyber Security Dashboard To Response Phishing Threats
Triage Cyber Security Dashboard To Response Phishing ThreatsThis slide represents triage cyber security dashboard to response phishing threats which assists to analyse and response to phishing attacks. It includes key components such as active clusters, processed reports, etc Presenting our well structured Triage Cyber Security Dashboard To Response Phishing Threats The topics discussed in this slide are Active Clusters, Categorized Reports. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat
Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about key roles, responsibilities, and accountability across the different team in the recovery plan. It includes key team such as executive, crisis management, business continuity experts, etc. Deliver an outstanding presentation on the topic using this Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Executive Team, Crisis Management, Business Continuity Expert using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Dashboard For Threat Detection And Response
Network Security Dashboard For Threat Detection And ResponseThis slide illustrates KPI Dashboard of network security including attack type, authentication, firewall events, and attack rates. Introducing our Network Security Dashboard For Threat Detection And Response set of slides. The topics discussed in these slides are Attack Type, Authentication, Firewall Events. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook
Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook. Use it as a tool for discussion and navigation on Stakeholders, Overview, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managed Detection And Response Icon For Early Threat Identification
Managed Detection And Response Icon For Early Threat IdentificationPresenting our set of slides with Managed Detection And Response Icon For Early Threat Identification. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Managed, Identification, Response.
-
 Micro Managed Strategies Detection And Response For Finding Threats
Micro Managed Strategies Detection And Response For Finding ThreatsThis slide showcases micro MDR for detecting threats. The main purpose of this template is to find abnormal pattern of devices and behaviour. This includes behavioural analytics, threat intelligence integration, cloud native solution, etc. Presenting our well structured Micro Managed Strategies Detection And Response For Finding Threats. The topics discussed in this slide are Analytics, Integration, Solutions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Emergency Response Plan Icon For Security Threats
Emergency Response Plan Icon For Security ThreatsPresenting our set of slides with name Emergency Response Plan Icon For Security Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Emergency Response Plan, Icon For Security Threats.
-
 Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats
Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Deliver an outstanding presentation on the topic using this Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Technical Directors, Team Leads, Engineers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats
Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Deliver an outstanding presentation on the topic using this Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Incident Identified, Initial Assessment, Classify Incident using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat
Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the key components of cyber security threat response plan. It includes key elements such as identify attack source, limit damage, damage scope assessment, consulting, clean up system, and future action plan. Increase audience engagement and knowledge by dispensing information using Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on six stages. You can also present information on Identify The Attack Source, Limit Additional Damage, Damage Scope Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Disaster Management Threat Response Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Disaster Management Threat Response Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Emergency Response Plan icon for security threats is a must-have for any presentation or document related to emergency preparedness. The bright and bold color scheme makes it easily visible and recognizable, while the clear design conveys the importance of having a plan in place for potential security threats.
-
 Disaster Management Threat Response Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Disaster Management Threat Response Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon features an Emergency response plan icon for security threats. It is designed to visually represent the importance of having a plan in place to respond to potential security threats. The simple yet impactful design makes it suitable for use in presentations and documents related to emergency preparedness and security protocols.
-
 Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS
Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Incident Response and Recovery Strategies for cyber terrorism. It includes strategies such as Incident Identification, Containment and Mitigation, Data Restoration and Resilience.Present the topic in a bit more detail with this Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Containment And Mitigation, Incident Identification, Eradication, Forensics And Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
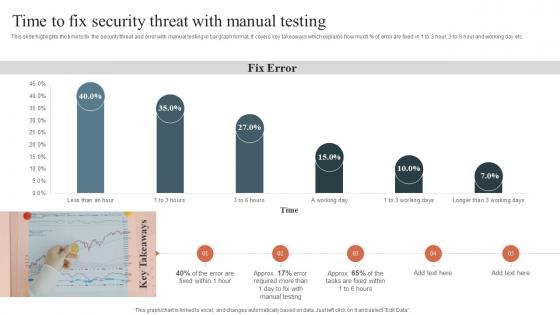 Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide
Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response GuideThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide. Use it as a tool for discussion and navigation on Time To Fix, Security Threat, Manual Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace roles and responsibilities ensure work
Cyber threat management workplace roles and responsibilities ensure workThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Introducing Cyber Threat Management Workplace Roles And Responsibilities Ensure Work to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Responsibilities, Unit Supervisor, Manager Responsibilities, Internal Investigations Unit Responsibilities, Human Resources Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Icon of information security response plan to prevent threats
Icon of information security response plan to prevent threatsIntroducing our premium set of slides with Icon Of Information Security Response Plan To Prevent Threats. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Information Security Response Plan To Prevent Threats. So download instantly and tailor it with your information.
-
 Roles and responsibilities to managing critical threat vulnerabilities and security threats
Roles and responsibilities to managing critical threat vulnerabilities and security threatsThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Introducing Roles And Responsibilities To Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Responsibilities, Manager Responsibilities, Unit Responsibilities, Human Resources Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Response Of Different Geographies Against Russias Aggression Ukraine Vs Russia Analyzing Conflict
Response Of Different Geographies Against Russias Aggression Ukraine Vs Russia Analyzing ConflictThis slide provides information regarding the responses of various geographies against Russias aggression. Most of the nations imposed several sanctions over Russia and halted existing trade ties with it.Introducing Response Of Different Geographies Against Russias Aggression Ukraine Vs Russia Analyzing Conflict to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Semiconductors Exports, Suspension Of Russian, Imposed Sanctions using this template. Grab it now to reap its full benefits.
-
 Threat monitoring response ppt powerpoint presentation model icons cpb
Threat monitoring response ppt powerpoint presentation model icons cpbPresenting Threat Monitoring Response Ppt Powerpoint Presentation Model Icons Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Monitoring Response. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats
Incident Response Playbook Checklist To Ensure Asset Protection From Internal ThreatsFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Introducing Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Devices, Company Assets, Employees, using this template. Grab it now to reap its full benefits.
-
 Incident Response Playbook Cyber Threat Facts Figures And Statistics
Incident Response Playbook Cyber Threat Facts Figures And StatisticsThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Cyber Threat Facts Figures And Statistics. This template helps you present information on six stages. You can also present information on Ransomware Attacks, Security Professional, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook
Checklist To Ensure Asset Protection From Internal Threats Security Incident Response PlaybookFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Deliver an outstanding presentation on the topic using this Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook. Dispense information and present a thorough explanation of Protection, Measures, Ensure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Facts Figures And Statistics Security Incident Response Playbook
Cyber Threat Facts Figures And Statistics Security Incident Response PlaybookThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Cyber Threat Facts Figures And Statistics Security Incident Response Playbook. This template helps you present information on six stages. You can also present information on Cyberattacks, Ransomware, Statistics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threat Facts Figures And Statistics Upgrading Cybersecurity With Incident Response Playbook
Cyber Threat Facts Figures And Statistics Upgrading Cybersecurity With Incident Response PlaybookThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Cyber Threat Facts Figures And Statistics Upgrading Cybersecurity With Incident Response Playbook. This template helps you present information on six stages. You can also present information on Professionals, Experienced, Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
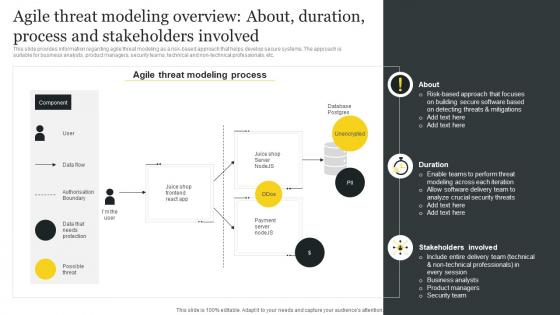 Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process
Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process. Use it as a tool for discussion and navigation on Stakeholders Involved, Duration, Agile Threat, Modeling Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips
Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas TipsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips. Dispense information and present a thorough explanation of Collaborate With Delivery Team, Analyze Threats, Prioritization And Resolve Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Responsible Organization Agile Threat Modeling Overview About Duration Process
Building Responsible Organization Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Building Responsible Organization Agile Threat Modeling Overview About Duration Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agile Threat Modeling Overview, Stakeholders Involved, Security Teams, Technical And Non Technical Professionals , using this template. Grab it now to reap its full benefits.
-
 Building Responsible Organization Checklist To Manage Agile Threat Modelling
Building Responsible Organization Checklist To Manage Agile Threat ModellingThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Building Responsible Organization Checklist To Manage Agile Threat Modelling. Use it as a tool for discussion and navigation on Threat Modeling Sessions, Technical Diagram Highlighting, Agile Threat Modelling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Responsible Organization Key Principles Associated With Agile Threat Modelling
Building Responsible Organization Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Building Responsible Organization Key Principles Associated With Agile Threat Modelling to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Threats Detection Techniques Incident Response Strategies Deployment
Cyber Security Threats Detection Techniques Incident Response Strategies DeploymentThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Introducing Cyber Security Threats Detection Techniques Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Threat, Analytics, Intruder, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques
Cyber Security Attacks Response Plan Cyber Security Threats Detection TechniquesThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques. Dispense information and present a thorough explanation of Cyber Security Threats, Detection Techniques, Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Threat Detection And Response
Cyber Security Threat Detection And ResponseThis slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Presenting our set of slides with Cyber Security Threat Detection And Response. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Reduce Access Time, Set Intruder Traps.
-
 Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook
Agile Threat Modeling Overview About Guide To Manage Responsible Technology PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook. Dispense information and present a thorough explanation of Overview, Stakeholders, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook. Use it as a tool for discussion and navigation on Analysis, Collaboration, Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Responsible Technology Techniques Playbook Agile Threat Modeling Overview
Responsible Technology Techniques Playbook Agile Threat Modeling OverviewThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Technology Techniques Playbook Agile Threat Modeling Overview. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Business Analysts, Product Managers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools
Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech ToolsThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Stakeholders Involved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech Tools
Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech ToolsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech Tools. Dispense information and present a thorough explanation of Modeling Sessions, Technical Diagram, Project using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech Tools
Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech ToolsThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech Tools. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident response showing identification of threats and recovery
Incident response showing identification of threats and recoveryPresenting this set of slides with name - Incident Response Showing Identification Of Threats And Recovery. This is a five stage process. The stages in this process are Incident Response, Incident Reaction, Incident Reply.
-
 Analyse threat intelligence start up marketing challenges corporate responsibility cpb
Analyse threat intelligence start up marketing challenges corporate responsibility cpbPresenting this set of slides with name - Analyse Threat Intelligence Start Up Marketing Challenges Corporate Responsibility Cpb. This is an editable six stages graphic that deals with topics like Analyse Threat Intelligence, Start Up Marketing Challenges, Corporate Responsibility to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Response level normal operations threat ppt powerpoint presentation gallery skills
Response level normal operations threat ppt powerpoint presentation gallery skillsPresenting this set of slides with name Response Level Normal Operations Threat Ppt Powerpoint Presentation Gallery Skills. This is a four stage process. The stages in this process are Business, Management, Planning, Strategy, Marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Response level potential actual threat ppt powerpoint presentation icon deck
Response level potential actual threat ppt powerpoint presentation icon deckPresenting this set of slides with name Response Level Potential Actual Threat Ppt Powerpoint Presentation Icon Deck. The topics discussed in these slides are In Progress, Response, Activities, Operations, Actual Threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Application threat detection response ppt powerpoint presentation file cpb
Application threat detection response ppt powerpoint presentation file cpbPresenting this set of slides with name Application Threat Detection Response Ppt Powerpoint Presentation File Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Application Threat Detection Response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Online threat response ppt powerpoint presentation portfolio visuals cpb
Online threat response ppt powerpoint presentation portfolio visuals cpbPresenting this set of slides with name Online Threat Response Ppt Powerpoint Presentation Portfolio Visuals Cpb. This is an editable Powerpoint two stages graphic that deals with topics like Online Threat Response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Threat detection response ppt powerpoint presentation styles aids cpb
Threat detection response ppt powerpoint presentation styles aids cpbPresenting this set of slides with name Threat Detection Response Ppt Powerpoint Presentation Styles Aids Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Threat Detection Response Services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Threat detection response services ppt powerpoint presentation slides example cpb
Threat detection response services ppt powerpoint presentation slides example cpbPresenting this set of slides with name Threat Detection Response Services Ppt Powerpoint Presentation Slides Example Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Threat Detection Response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber threat detection response ppt powerpoint presentation show clipart images cpb
Cyber threat detection response ppt powerpoint presentation show clipart images cpbPresenting this set of slides with name Cyber Threat Detection Response Ppt Powerpoint Presentation Show Clipart Images Cpb. This is an editable Powerpoint eight stages graphic that deals with topics like Cyber Threat Detection Response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Response level actual threat ppt powerpoint presentation example topics
Response level actual threat ppt powerpoint presentation example topicsPresenting this set of slides with name Response Level Actual Threat Ppt Powerpoint Presentation Example Topics. This is a four stage process. The stages in this process are Response Activities, Threat, Normal Operations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Managed application threat detection response ppt powerpoint presentation layouts slide cpb
Managed application threat detection response ppt powerpoint presentation layouts slide cpbPresenting our Managed Application Threat Detection Response Ppt Powerpoint Presentation Layouts Slide Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Managed Application Threat Detection Response This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threat matrix for incident response reporting to management
Threat matrix for incident response reporting to managementPresenting our well-structured Threat Matrix For Incident Response Reporting To Management. The topics discussed in this slide are Sophistication, Impact, Compromise, Degradation, Destruction. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Threat detection response ppt powerpoint presentation portfolio files cpb
Threat detection response ppt powerpoint presentation portfolio files cpbPresenting Threat Detection Response Ppt Powerpoint Presentation Portfolio Files Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Detection Response. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat response ppt powerpoint presentation ideas graphics pictures cpb
Threat response ppt powerpoint presentation ideas graphics pictures cpbPresenting Threat Response Ppt Powerpoint Presentation Ideas Graphics Pictures Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Response. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Ai threat detection response ppt powerpoint presentation outline graphics download cpb
Ai threat detection response ppt powerpoint presentation outline graphics download cpbPresenting our AI Threat Detection Response Ppt Powerpoint Presentation Outline Graphics Download Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on AI Threat Detection Response This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Circle process to manage threat detection and response infographic template
Circle process to manage threat detection and response infographic templateDeploy our Circle Process To Manage Threat Detection And Response Infographic Template to present high quality presentations. It is designed in PowerPoint and is available for immediate download in standard and widescreen sizes. Not only this, but this layout is also 100 percent editable, giving you full control over its applications.



