Powerpoint Templates and Google slides for Threat Modeling Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Process of threat risk modeling presentation pictures
Process of threat risk modeling presentation picturesPresenting process of threat risk modeling presentation pictures. This is a process of threat risk modeling presentation pictures. This is a six stage process. The stages in this process are identify vulnerabilities, decompose application, risk, application overview, possibility, impact, farming.
-
 Process of threat risk modeling diagram powerpoint images
Process of threat risk modeling diagram powerpoint imagesPresenting process of threat risk modeling diagram powerpoint images. This is a process of threat risk modeling diagram powerpoint images. This is a five stage process. The stages in this process are risk, impact, degree of mitigating, exploitability, damage potential, possibility, identify vulnerabilities, application overview, identify threats, decompose application.
-
 Best Practices For Threat Modeling Process
Best Practices For Threat Modeling ProcessThis slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method. Presenting our set of slides with name Best Practices For Threat Modeling Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Documentation, Threat Modeling, Suitable Method.
-
 Business Application Threat Modeling Process
Business Application Threat Modeling ProcessThis slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Introducing our premium set of slides with name Business Application Threat Modeling Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine, Security Profiles, Recommendations, Data Flow. So download instantly and tailor it with your information.
-
 Business Threat Modeling Process Icon
Business Threat Modeling Process IconPresenting our set of slides with name Business Threat Modeling Process Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Threat, Modeling, Process Icon.
-
 Key Steps Of Threat Modelling Process
Key Steps Of Threat Modelling ProcessThis slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate. Presenting our set of slides with name Key Steps Of Threat Modelling Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualize, Validate, Analyse Risks, Mitigate.
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
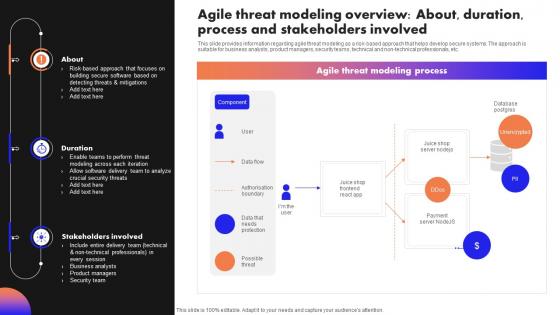
 Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process
Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process. Use it as a tool for discussion and navigation on Stakeholders Involved, Duration, Agile Threat, Modeling Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook
Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook. Use it as a tool for discussion and navigation on Overview, Process, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Responsible Organization Agile Threat Modeling Overview About Duration Process
Building Responsible Organization Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Building Responsible Organization Agile Threat Modeling Overview About Duration Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agile Threat Modeling Overview, Stakeholders Involved, Security Teams, Technical And Non Technical Professionals , using this template. Grab it now to reap its full benefits.
-
 Digital Safety Control Threat Modeling Process Flowchart
Digital Safety Control Threat Modeling Process FlowchartThis slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Introducing our Digital Safety Control Threat Modeling Process Flowchart set of slides. The topics discussed in these slides are Process, Flowchart, Attack Probability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
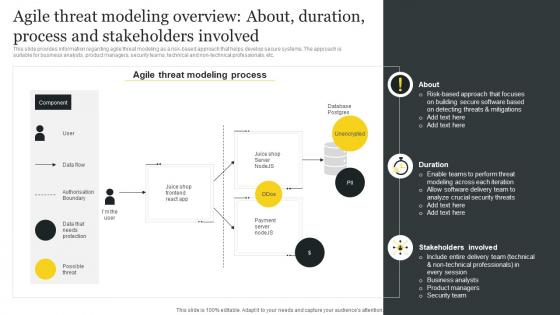
 Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process
Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process. Dispense information and present a thorough explanation of Database Postgres, Unencrypted, Stakeholders Involved, Crucial Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools
Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech ToolsThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Stakeholders Involved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook
Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on bout, Duration, Stakeholders Involved, using this template. Grab it now to reap its full benefits.
-
 Threat modeling process ppt powerpoint presentation outline deck cpb
Threat modeling process ppt powerpoint presentation outline deck cpbPresenting our Threat Modeling Process Ppt Powerpoint Presentation Outline Deck Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Threat Modeling Process This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.



