Powerpoint Templates and Google slides for Threat Modeling
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook
Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook. Use it as a tool for discussion and navigation on Stakeholders, Overview, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
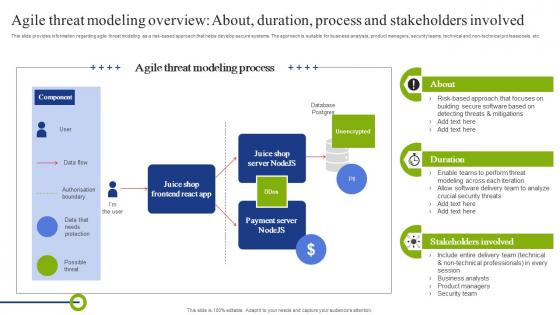 Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of Technology
Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Duration Playbook To Mitigate Negative Of Technology. Dispense information and present a thorough explanation of Overview, Process, Stakeholders using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology. Use it as a tool for discussion and navigation on Collaborate, Prioritization, Initiate Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values , using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS V
Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS V Use it as a tool for discussion and navigation on Designer, Blockchain, BAD Actor This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Hunting Model Types
Cyber Threat Hunting Model TypesThis slide represents the various cyber threat hunting model types, such as intel-based hunting, hypothesis hunting, and custom hunting. Increase audience engagement and knowledge by dispensing information using Cyber Threat Hunting Model Types. This template helps you present information on three stages. You can also present information on Hypothesis Hunting, Custom Hunting, Intel Based Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Hunting Maturity Model Stages
Threat Hunting Maturity Model StagesThis slide represents the levels of cyber threat hunting maturity model, such as initial, minimal, procedural, innovative, and leading. Increase audience engagement and knowledge by dispensing information using Threat Hunting Maturity Model Stages. This template helps you present information on five stages. You can also present information on Threat Hunting, Maturity Model Stages, Procedural, Innovative using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process of threat risk modeling presentation pictures
Process of threat risk modeling presentation picturesPresenting process of threat risk modeling presentation pictures. This is a process of threat risk modeling presentation pictures. This is a six stage process. The stages in this process are identify vulnerabilities, decompose application, risk, application overview, possibility, impact, farming.
-
 Process of threat risk modeling diagram powerpoint images
Process of threat risk modeling diagram powerpoint imagesPresenting process of threat risk modeling diagram powerpoint images. This is a process of threat risk modeling diagram powerpoint images. This is a five stage process. The stages in this process are risk, impact, degree of mitigating, exploitability, damage potential, possibility, identify vulnerabilities, application overview, identify threats, decompose application.
-
 Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity
Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat IntensityMentioned slide displays phase model that can be used by an organization to visualize corporate crisis threat intensity with respect to time. Increase audience engagement and knowledge by dispensing information using Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity. This template helps you present information on four stages. You can also present information on Strategic Crisis, Threat To Viability, Liquidity Crisis, Insolvency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber threat security maturity model with protection levels
Cyber threat security maturity model with protection levelsThe following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Presenting our well structured Cyber Threat Security Maturity Model With Protection Levels. The topics discussed in this slide are Security Management Technology, Threat Management Platform, Threat Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Critical security threats ppt powerpoint presentation model mockup cpb
Critical security threats ppt powerpoint presentation model mockup cpbPresenting our Critical Security Threats Ppt Powerpoint Presentation Model Mockup Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Critical Security Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Automating threat identification cloud siem model
Automating threat identification cloud siem modelThis slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Present the topic in a bit more detail with this Automating Threat Identification Cloud Siem Model. Use it as a tool for discussion and navigation on Vulnerability, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automating threat identification fully managed service model
Automating threat identification fully managed service modelThis slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Present the topic in a bit more detail with this Automating Threat Identification Fully Managed Service Model. Use it as a tool for discussion and navigation on Vulnerability, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automating threat identification hybrid managed siem model
Automating threat identification hybrid managed siem modelThis slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Present the topic in a bit more detail with this Automating Threat Identification Hybrid Managed Siem Model. Use it as a tool for discussion and navigation on Vulnerability, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automating threat identification traditional siem deployment model
Automating threat identification traditional siem deployment modelThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an outstanding presentation on the topic using this Automating Threat Identification Traditional Siem Deployment Model. Dispense information and present a thorough explanation of Expensive, Infrastructure, Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification which hosting model is right for you
Automating threat identification which hosting model is right for youThis slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. Increase audience engagement and knowledge by dispensing information using Automating Threat Identification Which Hosting Model Is Right For You. This template helps you present information on three stages. You can also present information on Infrastructure, Premises, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benchmarking with security operations maturity model automating threat identification
Benchmarking with security operations maturity model automating threat identificationThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Benchmarking With Security Operations Maturity Model Automating Threat Identification to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Centralized Forensic Visibility, Mean Time To Detect, Mean Time To Respond, using this template. Grab it now to reap its full benefits.
-
 Business Strategy Best Practice Model With Threats Of New Entrants
Business Strategy Best Practice Model With Threats Of New EntrantsThis slide provides information regarding five forces model framework which analyzes firms competitive environment in terms of threat of new entrants, threat of substitute products, etc. Increase audience engagement and knowledge by dispensing information using Business Strategy Best Practice Model With Threats Of New Entrants This template helps you present information on four stages. You can also present information on Determine Organizational, Process Oriented Implementation, Collaboration Among using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat monitoring response ppt powerpoint presentation model icons cpb
Threat monitoring response ppt powerpoint presentation model icons cpbPresenting Threat Monitoring Response Ppt Powerpoint Presentation Model Icons Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Monitoring Response. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis Threats
Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis ThreatsThis slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Increase audience engagement and knowledge by dispensing information using Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis Threats. This template helps you present information on four stages. You can also present information on High Competition, Regulations International Trade, Suppliers, Threat using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Threat Modeling Process
Best Practices For Threat Modeling ProcessThis slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method. Presenting our set of slides with name Best Practices For Threat Modeling Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Documentation, Threat Modeling, Suitable Method.
-
 Business Application Threat Modeling Process
Business Application Threat Modeling ProcessThis slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Introducing our premium set of slides with name Business Application Threat Modeling Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine, Security Profiles, Recommendations, Data Flow. So download instantly and tailor it with your information.
-
 Business Threat Modeling Process Icon
Business Threat Modeling Process IconPresenting our set of slides with name Business Threat Modeling Process Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Threat, Modeling, Process Icon.
-
 Key Steps Of Threat Modelling Process
Key Steps Of Threat Modelling ProcessThis slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate. Presenting our set of slides with name Key Steps Of Threat Modelling Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualize, Validate, Analyse Risks, Mitigate.
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
 Threat And Vulnerability Management Model To Measure Program Maturity
Threat And Vulnerability Management Model To Measure Program MaturityThis slide defines the vulnerability management model adopted to measure the maturity of program. It includes information related to different levels from scanning to risk management. Introducing our premium set of slides with Threat And Vulnerability Management Model To Measure Program Maturity. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Non Existent, Scanning, Assessment. So download instantly and tailor it with your information.
-
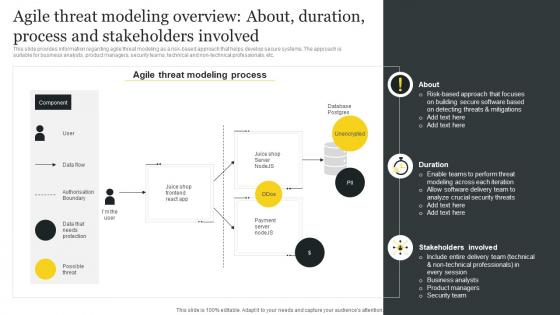 Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process
Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process. Use it as a tool for discussion and navigation on Stakeholders Involved, Duration, Agile Threat, Modeling Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips
Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas TipsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips. Dispense information and present a thorough explanation of Collaborate With Delivery Team, Analyze Threats, Prioritization And Resolve Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat Modelling
Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat Modelling to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mitigate Critical Risks, Consider Stakeholder Values, Agile Threat Modelling, using this template. Grab it now to reap its full benefits.
-
 Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook
Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook. Use it as a tool for discussion and navigation on Overview, Process, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook
Checklist To Manage Agile Threat Modelling Ethical Tech Governance PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook. Dispense information and present a thorough explanation of Analyze Threats, Prioritization And Resolve Issues, Collaborate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Principles Associated With Agile Threat Modelling Ethical Tech Governance Playbook
Key Principles Associated With Agile Threat Modelling Ethical Tech Governance PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Ethical Tech Governance Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Building Responsible Organization Agile Threat Modeling Overview About Duration Process
Building Responsible Organization Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Building Responsible Organization Agile Threat Modeling Overview About Duration Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agile Threat Modeling Overview, Stakeholders Involved, Security Teams, Technical And Non Technical Professionals , using this template. Grab it now to reap its full benefits.
-
 Building Responsible Organization Checklist To Manage Agile Threat Modelling
Building Responsible Organization Checklist To Manage Agile Threat ModellingThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Building Responsible Organization Checklist To Manage Agile Threat Modelling. Use it as a tool for discussion and navigation on Threat Modeling Sessions, Technical Diagram Highlighting, Agile Threat Modelling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Responsible Organization Key Principles Associated With Agile Threat Modelling
Building Responsible Organization Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Building Responsible Organization Key Principles Associated With Agile Threat Modelling to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Intelligence Maturity Model
Cyber Threat Intelligence Maturity ModelThis slide showcases a maturity model to truly keep track of the costs associated with companys intelligence operations and to choose between buying and not buying intelligence services. It covers two critical areas operational and process maturity. Introducing our premium set of slides with Cyber Threat Intelligence Maturity Model. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Process Maturity, Operational Maturity, Risk Management. So download instantly and tailor it with your information.
-
 Digital Safety Control Threat Modeling Process Flowchart
Digital Safety Control Threat Modeling Process FlowchartThis slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Introducing our Digital Safety Control Threat Modeling Process Flowchart set of slides. The topics discussed in these slides are Process, Flowchart, Attack Probability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
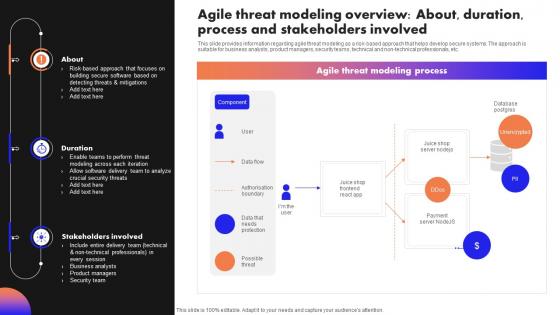 Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process
Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process. Dispense information and present a thorough explanation of Database Postgres, Unencrypted, Stakeholders Involved, Crucial Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ultimate Guide To Handle Business Key Principles Associated With Agile Threat Modelling
Ultimate Guide To Handle Business Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Ultimate Guide To Handle Business Key Principles Associated With Agile Threat Modelling. This template helps you present information on three stages. You can also present information on Consider Stakeholder Values, Mitigate Critical Risks, Open Up Perspectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook
Agile Threat Modeling Overview About Guide To Manage Responsible Technology PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook. Dispense information and present a thorough explanation of Overview, Stakeholders, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook. Use it as a tool for discussion and navigation on Analysis, Collaboration, Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ultimate Guide To Handle Business Checklist To Manage Agile Threat Modelling
Ultimate Guide To Handle Business Checklist To Manage Agile Threat ModellingThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Ultimate Guide To Handle Business Checklist To Manage Agile Threat Modelling. Use it as a tool for discussion and navigation on Agile Threat Modelling, Prioritization And Resolve Issues, Brainstorm Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Responsible Technology Techniques Playbook Agile Threat Modeling Overview
Responsible Technology Techniques Playbook Agile Threat Modeling OverviewThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Technology Techniques Playbook Agile Threat Modeling Overview. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Business Analysts, Product Managers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools
Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech ToolsThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Stakeholders Involved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech Tools
Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech ToolsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Playbook For Responsible Tech Tools. Dispense information and present a thorough explanation of Modeling Sessions, Technical Diagram, Project using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech Tools
Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech ToolsThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Playbook For Responsible Tech Tools. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agile Threat Modeling Overview About Usage Of Technology Ethically
Agile Threat Modeling Overview About Usage Of Technology EthicallyThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.Present the topic in a bit more detail with this Agile Threat Modeling Overview About Usage Of Technology Ethically. Use it as a tool for discussion and navigation on Modeling Across, Building Secure, Crucial Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Usage Of Technology Ethically
Checklist To Manage Agile Threat Modelling Usage Of Technology EthicallyThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc.Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Usage Of Technology Ethically. Dispense information and present a thorough explanation of Prioritization Resolve Issues, Analyze Threats, Modeling Sessions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook
Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on bout, Duration, Stakeholders Involved, using this template. Grab it now to reap its full benefits.
-
 Checklist To Manage Agile Threat Modelling Manage Technology Interaction With Society Playbook
Checklist To Manage Agile Threat Modelling Manage Technology Interaction With Society PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Manage Technology Interaction With Society Playbook. Use it as a tool for discussion and navigation on Focus Area, Initiatives, Checked. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Manage Technology Interaction With Society Playbook
Key Principles Associated With Agile Threat Modelling Manage Technology Interaction With Society PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Manage Technology Interaction With Society Playbook. This template helps you present information on Three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 4 quadrant model to determine strength weakness opportunity and threat
4 quadrant model to determine strength weakness opportunity and threatPresenting this set of slides with name - 4 Quadrant Model To Determine Strength Weakness Opportunity And Threat. This is a four stage process. The stages in this process are 4 Quadrant Model, 4 Quadrant Framework, 4 Quadrant Structure.
-
 Health care solution product security policy threat modeling
Health care solution product security policy threat modelingPresenting this set of slides with name - Health Care Solution Product Security Policy Threat Modeling. This is an editable two stages graphic that deals with topics like Health Care Solution, Product Security Policy, Threat Modeling to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Threat modeling static code analysis define recruitment standard cpb
Threat modeling static code analysis define recruitment standard cpbPresenting this set of slides with name - Threat Modeling Static Code Analysis Define Recruitment Standard Cpb. This is an editable three stages graphic that deals with topics like Threat Modeling, Static Code Analysis, Define Recruitment Standard to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Brand threat analysis ppt powerpoint presentation model designs cpb
Brand threat analysis ppt powerpoint presentation model designs cpbPresenting this set of slides with name - Brand Threat Analysis Ppt Powerpoint Presentation Model Designs Cpb. This is an editable five stages graphic that deals with topics like Brand Threat Analysis to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Swot threats h108 ppt powerpoint presentation file model
Swot threats h108 ppt powerpoint presentation file modelPresenting this set of slides with name Swot Threats H108 Ppt Powerpoint Presentation File Model. This is a four stage process. The stages in this process are Swot, Planning, Management, Business, Strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Succession planning modelling chart threat ppt powerpoint presentation infographic template
Succession planning modelling chart threat ppt powerpoint presentation infographic templatePresenting this set of slides with name Succession Planning Modelling Chart Threat Ppt Powerpoint Presentation Infographic Template. The topics discussed in these slides are Business, Planning, Strategy, Marketing, Management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.




