Powerpoint Templates and Google slides for Terrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V
Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Monitor New Advancements using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS V
Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS VThe following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS V This template helps you present information on Five stages. You can also present information on Copycatting, Spelling, Ambiguous Links using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview And Categories Of Sybil Attack On Blockchain Network BCT SS V
Cyber Threats In Blockchain Overview And Categories Of Sybil Attack On Blockchain Network BCT SS VThe following slide illustrates brief introduction of sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Categories Of Sybil Attack On Blockchain Network BCT SS V This template helps you present information on Two stages. You can also present information on Direct Sybil Attack, Indirect Sybil Attack using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview And Impact Of Blockchain Routing Attacks BCT SS V
Cyber Threats In Blockchain Overview And Impact Of Blockchain Routing Attacks BCT SS VThe following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Introducing Cyber Threats In Blockchain Overview And Impact Of Blockchain Routing Attacks BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Service Providers, Partial Proceedings, Routing Attack using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Overview And Key Levels Of Honeypot Crypto Frauds BCT SS V
Cyber Threats In Blockchain Overview And Key Levels Of Honeypot Crypto Frauds BCT SS VThe following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as Ethereum virtual machine, solidity compiler, Ethers can blockchain explorer, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Key Levels Of Honeypot Crypto Frauds BCT SS V This template helps you present information on Four stages. You can also present information on Solidity Compiler, Etherscan, Blockchain Explorer using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V
Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V This template helps you present information on One stages. You can also present information on Node Validates Transaction, Existing Blockchain, Transaction Completed using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V
Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Target Node, Attacker Nodes, Participating Nodes using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V
Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V This template helps you present information on Three stages. You can also present information on Internet Traffic, Perform Operations, Website Hostage using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V
Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS VThe following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview Of Blockchain 51 Percent Attack With Workflow BCT SS V This template helps you present information on Four stages. You can also present information on Mining Capability, Mining Capabilities, Much Faster Rate using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Opportunities, Fake Website, Data Breach using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Performing Threat Assessment For Cause Identification BCT SS V
Cyber Threats In Blockchain Performing Threat Assessment For Cause Identification BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V Dispense information and present a thorough explanation of Double Spending, Mining Threats, Wallet Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V
Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS VThe following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V Dispense information and present a thorough explanation of Services, Features, Reviews using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Reporting Analyzing Vulnerabilities Through Penetration Testing Summary BCT SS V
Cyber Threats In Blockchain Reporting Analyzing Vulnerabilities Through Penetration Testing Summary BCT SS VThe following slide depicts brief summary of penetration testing report. it includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Reporting Analyzing Vulnerabilities Through Penetration Testing Summary BCT SS V Use it as a tool for discussion and navigation on Vulnerabilities, Description, Severity This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS V
Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS VThe following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work pow, proof of stake pos, delegated pos, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS V This template helps you present information on Three stages. You can also present information on Proof Of Work, Proof Of Stake, Delegated POS using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capability, Mining Capabilities, Much Faster Rate using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS V
Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS VThe following slide highlights major issues faced by users due to sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS V Dispense information and present a thorough explanation of Block Users From Network, Breach Of Privacy, Attack Edge using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V
Cyber Threats In Blockchain Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS VThe following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Cyber Threats In Blockchain Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Application Attacks, Fragmentation Attacks using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V
Cyber Threats In Blockchain Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS VThe following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Introducing Cyber Threats In Blockchain Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Constant Updates, Network System, Perform Security Audits using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS V
Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS V This template helps you present information on Four stages. You can also present information on Blockchain Routing Attacks, Strong Passwords, Manage Access Control List using this PPT design. This layout is completely editable so personaize it now
-
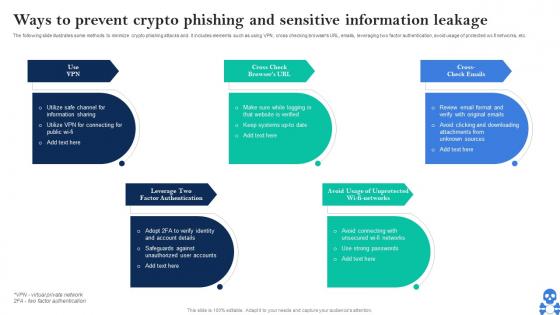 Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use VPN, Factor Authentication, Avoid Usage Of Unprotected using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cyber Threats In Blockchain World Best Practices BCT SS V
Icons Slide For Cyber Threats In Blockchain World Best Practices BCT SS VIntroducing our well researched set of slides titled Icons Slide For Cyber Threats In Blockchain World Best Practices BCT SS V It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents Cyber Threats In Blockchain World Best Practices BCT SS V
Table Of Contents Cyber Threats In Blockchain World Best Practices BCT SS VIncrease audience engagement and knowledge by dispensing information using Table Of Contents Cyber Threats In Blockchain World Best Practices BCT SS V This template helps you present information on One stages. You can also present information on Industry Overview, Cybersecurity Scams using this PPT design. This layout is completely editable so personaize it now
-
 Table Of Contents For Cyber Threats In Blockchain World Best Practices BCT SS V
Table Of Contents For Cyber Threats In Blockchain World Best Practices BCT SS VIntroducing Table Of Contents For Cyber Threats In Blockchain World Best Practices BCT SS V to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cybersecurity, Workflow Model using this template. Grab it now to reap its full benefits.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process
Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management ProcessThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Deliver an outstanding presentation on the topic using this Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Threat, Threat Source, Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process
Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management ProcessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Present the topic in a bit more detail with this Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SWOT Analysis Threat Business Strategy Consulting Company Profile CP SS V
SWOT Analysis Threat Business Strategy Consulting Company Profile CP SS VThis slide represents SWOT analysis highlighting threats to the company. It includes details regarding intense competition and political uncertainty. Introducing SWOT Analysis Threat Business Strategy Consulting Company Profile CP SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Companies, Business, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Threat Protection Next Generation CASB
Cloud Access Security Broker Pillar Threat Protection Next Generation CASBThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Next Generation CASB This template helps you present information on five stages. You can also present information on Services, Cloud Storage, Compromised Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Cloud Security Risks And Threats Next Generation CASB
Emerging Cloud Security Risks And Threats Next Generation CASBThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats Next Generation CASB Use it as a tool for discussion and navigation on Virtual Private Networks, System Misconfigurations, Perimeter Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Modern Threats Exploiting Firewall Vulnerabilities
Firewall Network Security Modern Threats Exploiting Firewall VulnerabilitiesThis slide represents the various modern risks that can take advantage of firewall weaknesses. The purpose of this slide is to showcase the different current threats that can exploit firewall vulnerabilities, including insider attacks, DDoS attacks, malware and patching and configuration. Introducing Firewall Network Security Modern Threats Exploiting Firewall Vulnerabilities to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Requested Data, NAT Firewall, Forwarding Table using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Next Generation Firewalls Vs Unified Threat Management
Firewall Network Security Next Generation Firewalls Vs Unified Threat ManagementThis slide showcases the comparison between Next-Generation Firewalls and United Threat Management. This slide aims to highlight the key differences between NGFWs and UTMs based on definition, market focus, features, scalability, customization, management complexity, deployment, and cost. Present the topic in a bit more detail with this Firewall Network Security Next Generation Firewalls Vs Unified Threat Management Use it as a tool for discussion and navigation on Firewall, Features, Providers This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SWOT Analysis Threats Alibaba Company Profile Ppt Clipart CP SS
SWOT Analysis Threats Alibaba Company Profile Ppt Clipart CP SSThis slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Introducing SWOT Analysis Threats Alibaba Company Profile Ppt Clipart CP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Politics, Online Buying, Fake Products, using this template. Grab it now to reap its full benefits.
-
 Threats Cisco Company Profile CP SS
Threats Cisco Company Profile CP SSThe following slide showcases the threats to Cisco Systems and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as economic slowdown, security breaches and regulatory changes. Introducing Threats Cisco Company Profile CP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security, Economic, Regulatory, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Understanding The Cyber Threats Prevented By Waf
Firewall Network Security Understanding The Cyber Threats Prevented By WafThis slide represents the many cyberattacks that a WAF is designed to stop. The purpose of this slide is to showcase the various cyber attacks that can avoided with the help of WAF, such as DDoS attacks, zero-day threats, cross-site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Introducing Firewall Network Security Understanding The Cyber Threats Prevented By Waf to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Cookie Poisoning, Sql Injection, Parameter Tampering using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Unified Threat Management UTM Firewall System Overview
Firewall Network Security Unified Threat Management UTM Firewall System OverviewThis slide provides an introduction to the Unified Threat Management firewall system. The purpose of this slide is to showcase the features, benefits, and inspection methods of Unified Threat Management firewall systems, such as flow-based and proxy-based inspection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Understanding Critical Risks Of Firewall Absence This template helps you present information on Three stages. You can also present information on Content Filtering, Faster Security, Flexibility And Adaptability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security About Threat Intelligence Overview And Types
Firewall Network Security About Threat Intelligence Overview And TypesThis slide talks about threat intelligence by giving its overview and types. The purpose of this slide is to introduce threat intelligence features used in Next Generation Firewall, including its types, such as strategic intelligence, operational intelligence, and tactical intelligence. Present the topic in a bit more detail with this Firewall Network Security About Threat Intelligence Overview And Types Use it as a tool for discussion and navigation on Strategic Intelligence, Operational Intelligence, Tactical Intelligence This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Future Social Engineering Trends And Threats
Future Social Engineering Trends And ThreatsThe purpose of this slide is to emphasize how understanding future social engineering trends enables proactive cybersecurity preparedness, staying ahead of emerging risks and implementing effective preventive measures. Introducing our premium set of slides with Future Social Engineering Trends And Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Deepfakes, Personalized Attacks, Swapping. So download instantly and tailor it with your information.
-
 Social Engineering Attacks Prevention Understanding Social Engineering Threat Landscape
Social Engineering Attacks Prevention Understanding Social Engineering Threat LandscapeThis slide shows the threat landscape for social engineering. The key components included are email, social media and the internet, trends, criminal groups, malicious insiders, and attack vectors such as physical on-site attacks, mobile, network, cloud, etc. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Understanding Social Engineering Threat Landscape. Dispense information and present a thorough explanation of Social Media And Internet, Social Engineering Threat Landscape, Search Result Poisoning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 National Security Threat In Powerpoint And Google Slides Cpb
National Security Threat In Powerpoint And Google Slides CpbPresenting our National Security Threat In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on National Security Threat This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Performing Threat Assessment For Cause Identification Guide For Blockchain BCT SS V
Performing Threat Assessment For Cause Identification Guide For Blockchain BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Present the topic in a bit more detail with this Performing Threat Assessment For Cause Identification Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Double Spending, Mining Threats, Wallet Threats, Network Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V
Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS VThe following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51 percent attack, etc. Increase audience engagement and knowledge by dispensing information using Threats Imposed By Sybil Attack On Blockchain Network Guide For Blockchain BCT SS V This template helps you present information on three stages. You can also present information on Block Users From Network, Breach Of Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methamphetamine Substance Abuse In Powerpoint And Google Slides Cpb
Methamphetamine Substance Abuse In Powerpoint And Google Slides CpbPresenting Methamphetamine Substance Abuse In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Methamphetamine Substance Abuse. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Life Threatening Examples In Powerpoint And Google Slides Cpb
Life Threatening Examples In Powerpoint And Google Slides CpbPresenting our Life Threatening Examples In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Life Threatening Examples. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threats Dell Company Profile Ppt Information CP SS
Threats Dell Company Profile Ppt Information CP SSThe following slide showcases the threats to Dell company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition, changing customer preferences and technological requirements. Introducing Threats Dell Company Profile Ppt Information CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Market Competition, Changing Customer Preferences, Technological Requirements, using this template. Grab it now to reap its full benefits.
-
 Salmonella Life Threatening In Powerpoint And Google Slides Cpb
Salmonella Life Threatening In Powerpoint And Google Slides CpbPresenting our Salmonella Life Threatening In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Salmonella Life Threatening This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Night Terrors Sleep Disturbances In Powerpoint And Google Slides Cpb
Night Terrors Sleep Disturbances In Powerpoint And Google Slides CpbPresenting our Night Terrors Sleep Disturbances In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Night Terrors Sleep Disturbances This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Detoxification Services Substance Abuse In Powerpoint And Google Slides Cpb
Detoxification Services Substance Abuse In Powerpoint And Google Slides CpbPresenting Detoxification Services Substance Abuse In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Detoxification Services Substance Abuse. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Psychological Abuse Cycle In Powerpoint And Google Slides Cpb
Psychological Abuse Cycle In Powerpoint And Google Slides CpbPresenting our Psychological Abuse Cycle In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Psychological Abuse Cycle This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Aggression Simply Psychology In Powerpoint And Google Slides Cpb
Aggression Simply Psychology In Powerpoint And Google Slides CpbPresenting Aggression Simply Psychology In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Aggression Simply Psychology This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Environmental Threats Examples In Powerpoint And Google Slides Cpb
Environmental Threats Examples In Powerpoint And Google Slides CpbPresenting Environmental Threats Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Environmental Threats Examples This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Forcepoint Insider Threat In Powerpoint And Google Slides Cpb
Forcepoint Insider Threat In Powerpoint And Google Slides CpbPresenting Forcepoint Insider Threat In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Forcepoint Insider Threat. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Gun Violence Statistics Year In Powerpoint And Google Slides Cpb
Gun Violence Statistics Year In Powerpoint And Google Slides CpbPresenting our Gun Violence Statistics Year In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Gun Violence Statistics Year. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Articles Domestic Violence In Powerpoint And Google Slides Cpb
Articles Domestic Violence In Powerpoint And Google Slides CpbPresenting Articles Domestic Violence In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Articles Domestic Violence. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 SWOT Opportunities And Threats Sap Company Profile Ppt Icons CP SS
SWOT Opportunities And Threats Sap Company Profile Ppt Icons CP SSFollowing slide provides information about company external analysis based on the following parameters such as opportunities and threats. Introducing SWOT Opportunities And Threats Sap Company Profile Ppt Icons CP SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Opportunities, Threats, using this template. Grab it now to reap its full benefits.
-
 Swot Analysis Threats E Commerce Company Profile Ppt Professional CP SS
Swot Analysis Threats E Commerce Company Profile Ppt Professional CP SSThis slide showcase SWOT Strengths, Weaknesses, Opportunities and Threats analysis of ecommerce giant that helps in converting company weakness into strengths and threats into opportunities. Introducing Swot Analysis Threats E Commerce Company Profile Ppt Professional CP SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Dependence On Technology, Shipping Complexities, using this template. Grab it now to reap its full benefits.
-
 Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V
Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Increase audience engagement and knowledge by dispensing information using Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on one stages. You can also present information on Double Spending, Mining Threats, Wallet Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threats Imposed By Sybil Attack Securing Blockchain Transactions A Beginners Guide BCT SS V
Threats Imposed By Sybil Attack Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Introducing Threats Imposed By Sybil Attack Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Block Users Network, Foster Attack, Breach Privacy, using this template. Grab it now to reap its full benefits.
-
 Network Security Threats And Optimization Techniques
Network Security Threats And Optimization TechniquesThis slide presents optimization strategies to prevent network security attacks. The purpose of this slide is to help businesses in securing their digital infrastructure against security threats through these optimization techniques. It covers solutions to prevent threats such as malware, phishing, DDoS and social engineering attacks. Introducing our premium set of slides with Network Security Threats And Optimization Techniques. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure, Software, Employees. So download instantly and tailor it with your information.
-
 Threats Huawei Ppt Sample Company Profile CP SS
Threats Huawei Ppt Sample Company Profile CP SSThe following slide showcases the threats to Huawei company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as geopolitical and regulatory challenges and increased competition. Introducing Threats Huawei Ppt Sample Company Profile CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Events, Expansion, using this template. Grab it now to reap its full benefits.
-
 Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment
Analyze And Rank Impact Of Cyber Threat Cyber Risk AssessmentThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyze And Rank Impact Of Cyber Threat Cyber Risk Assessment Use it as a tool for discussion and navigation on Framework, Appropriate Structure, Internet Access This template is free to edit as deemed fit for your organization. Therefore download it now.





