Powerpoint Templates and Google slides for Terrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 General Equal Treatment Act Against Sexual Harassment In Germany Training Ppt
General Equal Treatment Act Against Sexual Harassment In Germany Training PptPresenting General Equal Treatment Act in Germany against Sexual Harassment in the Workplace. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Sexual Harassment Legislation In India POSH Act Training Ppt
Sexual Harassment Legislation In India POSH Act Training PptPresenting Sexual Harassment Legislation in India POSH Act. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Deadweight Losses Caused By Sexual Harassment In Workplace Training Ppt
Deadweight Losses Caused By Sexual Harassment In Workplace Training PptPresenting Deadweight Losses Caused by Sexual Harassment in the Workplace. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Blockchain Use Cases In Anti Money Laundering And Counter Terrorist Funding Training Ppt
Blockchain Use Cases In Anti Money Laundering And Counter Terrorist Funding Training PptPresenting Blockchain Use Cases in Anti-Money Laundering and Counter Terrorist Funding. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Manage Passive Aggression Technique For Conflict Prevention At Workplace Training Ppt
Manage Passive Aggression Technique For Conflict Prevention At Workplace Training PptPresenting Recognize and Manage Passive Aggression Technique for Conflict Prevention at Workplace. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Avoid Using Coercion And Intimidation Technique For Conflict Prevention Training Ppt
Avoid Using Coercion And Intimidation Technique For Conflict Prevention Training PptPresenting Avoid using Coercion and Intimidation Technique for Conflict Prevention. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Segmented Circle Training Development Process Opportunity Threat Weakness Strength
Segmented Circle Training Development Process Opportunity Threat Weakness StrengthThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Segmented Circle Training Development Process Opportunity Threat Weakness Strength and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Cyber Security Icon Network Protection Threat Server Database Software
Cyber Security Icon Network Protection Threat Server Database SoftwareKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Drug Abuse Awareness Medicinal Measuring Individual Spreading
Drug Abuse Awareness Medicinal Measuring Individual SpreadingIf you require a professional template with great design, then this Drug Abuse Awareness Medicinal Measuring Individual Spreading is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Threat Technology Security Displaying Cybersecurity Companies
Threat Technology Security Displaying Cybersecurity CompaniesIntroduce your topic and host expert discussion sessions with this Threat Technology Security Displaying Cybersecurity Companies. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 HR SWOT Strengths Weaknesses Opportunities Threats Strategy Marketing Management
HR SWOT Strengths Weaknesses Opportunities Threats Strategy Marketing ManagementKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Vulnerability Analyzing Dashboard For Cyber Threat Intelligence
Vulnerability Analyzing Dashboard For Cyber Threat IntelligenceThis slide showcases the vulnerability analyzing dashboard for cyber threat intelligence based on various parameters such as issue status, severity, etc. Present the topic in a bit more detail with this Vulnerability Analyzing Dashboard For Cyber Threat Intelligence. Use it as a tool for discussion and navigation on Vulnerability Analyzing Dashboard, Cyber Threat Intelligence, Issue Status, Severity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it dashboard snapshot for threat tracking in data security
Data security it dashboard snapshot for threat tracking in data securityThis slide depicts the dashboard snapshot for threat tracking in data security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Data Security IT Dashboard For Threat Tracking In Data Security. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based On Role, Threats Owners, Risk Threats, Threat Report using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security dashboard snapshot for threat tracking in computer security
Computer system security dashboard snapshot for threat tracking in computer securityThis slide depicts the dashboard snapshot for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Computer System Security Dashboard For Threat Tracking In Computer Security. Dispense information and present a thorough explanation of Monthly Threat Status, Threats By Owners, Risk By Threats, Current Risk Status, Threats Based On Role using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics Interpreting Threat On Network Security
Statistics Interpreting Threat On Network SecurityThis slide showcases weightage of threat to network security. The main purpose of this slide is to show different channels that cause threats to business security. This includes channels such as malware, phishing, bots, etc. Presenting our well structured Statistics Interpreting Threat On Network Security. The topics discussed in this slide are Steals Information, Credit Card Number.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 E Commerce Release Management Dashboard Showcasing Threats
E Commerce Release Management Dashboard Showcasing ThreatsThis slide showcases the r commerce release management dashboard showcasing threats which helps an organization to standardized strategy and increases rate of interest. It include details such as under review, done, in progress, selected for development, etc. Presenting our well structured E Commerce Release Management Dashboard Showcasing Threats. The topics discussed in this slide are Release, Management, Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Managed Detection And Response Dashboard For Tracking Threats
Managed Detection And Response Dashboard For Tracking ThreatsThis slide showcases MDR dashboard for remediation threats. The main purpose of this template is risk-level threats and threat performance. This includes threats, performance of threat, asset group of threats, etc. Presenting our well structured Managed Detection And Response Dashboard For Tracking Threats. The topics discussed in this slide are Managed, Response, Tracking. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Graph Showing Cyber Security Threats In Various Industries
Graph Showing Cyber Security Threats In Various IndustriesThis slide demonstrates cybersecurity threats for deploying AUP to leverage techniques and determine safety of personal identifiable information. It includes various sectors such as financial institutions, healthcare, manufacturing, public administration, retail trade, etc. Introducing our Graph Showing Cyber Security Threats In Various Industries set of slides. The topics discussed in these slides are Business Services, Financial Institutions, Software Service This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V
Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS VThe following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V Use it as a tool for discussion and navigation on Rise In Demand, Web3 Market This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V
Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS VThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as Ronin, poly network, wormhole, BITMART, Venus, cream finance, along with key insights, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V Use it as a tool for discussion and navigation on Top Cryptocurrency Threat, Loss Amount This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS V
Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS V Dispense information and present a thorough explanation of Major Instances, Contracts Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS V
Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS V This template helps you present information on Two stages. You can also present information on Client Honey Spot, Malware Honeypots using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS V
Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS V Dispense information and present a thorough explanation of Major Reasons, Hacked Computer, Blockchain Cybersecurity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Dashboard For Threat Tracking By Firewall System
Firewall Network Security Dashboard For Threat Tracking By Firewall SystemThis slide represents the dashboard for threat tracking in a firewall-protected network. The purpose of this slide is to showcase the various threats based on categories such as threats by owners, risk by threats, threat report, monthly threat status, current risk status, and threats based on user role. Present the topic in a bit more detail with this Firewall Network Security Dashboard For Threat Tracking By Firewall System Use it as a tool for discussion and navigation on Threats By Owners, Current Risk Status, Threats Based On Role This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SS
Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SSThis slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats. Present the topic in a bit more detail with this Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Scanning Network Connected, Attacks Exploit, Device Weaknesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Triage Cyber Security Dashboard To Response Phishing Threats
Triage Cyber Security Dashboard To Response Phishing ThreatsThis slide represents triage cyber security dashboard to response phishing threats which assists to analyse and response to phishing attacks. It includes key components such as active clusters, processed reports, etc Presenting our well structured Triage Cyber Security Dashboard To Response Phishing Threats The topics discussed in this slide are Active Clusters, Categorized Reports. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Prevented Attacks, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Current And Future Goal Analysis, Breach Risk Trend This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats
Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Security Threat Assessment Dashboard
Mobile Security Threat Assessment DashboardThis slide illustrates KPI or Dashboard of mobile security threat assessment and includes security incidents log, security compromised users or devices, and highly targeted networks. Introducing our Mobile Security Threat Assessment Dashboard set of slides. The topics discussed in these slides are Security Compromised Users Devices, Highly Targeted Networks, Security Incidents Log. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistics Associated With Retail Cybersecurity Threats
Statistics Associated With Retail Cybersecurity ThreatsThis slide highlights stats data for vulnerabilities affecting retail cybersecurity. The purpose of this template is to provide businesses with quantitative for fostering strategic defences and risk management. It includes elements such as credential phishing, ransomware, etc. Introducing our Statistics Associated With Retail Cybersecurity Threats set of slides. The topics discussed in these slides are Statistics Associated, Retail Cybersecurity Threats This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 How To Handle Emergency Situation Of Bomb Threat At The Hotel Training Ppt
How To Handle Emergency Situation Of Bomb Threat At The Hotel Training PptPresenting How to Handle Emergency Situation of Bomb Threat at the Hotel. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizablealter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Checklist For Bomb Threat At A Hotel Training Ppt
Checklist For Bomb Threat At A Hotel Training PptPresenting Checklist for Bomb Threat at a Hotel. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS
Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SSThis slide showcases common internet of things IoT threats in the company, referable for related businesses. It provides details about network scan, command injection, SQL, zero-day, etc. Present the topic in a bit more detail with this Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Security Awareness, Quality Threat Modeling Tools, Weak Passwords, Authentication Practices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry Outlook
Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry OutlookThe slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Increase audience engagement and knowledge by dispensing information using Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry Outlook. This template helps you present information on three stages. You can also present information on Automotive Hacking, Attacks Against Cloud Services, Social Engineering Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Hids Cyber Security Dashboard To Identify Network Threats
Hids Cyber Security Dashboard To Identify Network ThreatsThis slide represents HIDS cyber security dashboard to identify network issues and monitor malicious activity in host devices which could lead to serious breaches. It includes key components such as number of alerts, summary of alerts, etc Introducing our Hids Cyber Security Dashboard To Identify Network Threats set of slides. The topics discussed in these slides are Security, Dashboard, Network Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threat Intelligence Statistical Dashboard
Cyber Threat Intelligence Statistical DashboardThis slide depicts cyber threat intelligence dashboard which helps to use data on current cyber threat actors and boost cognitive content. It includes elements such as dashboard, SEM, threats, list, asset profile, penetration text, vulnerability, cyber essentials, training and threat remediation. Introducing our Cyber Threat Intelligence Statistical Dashboard set of slides. The topics discussed in these slides are Active Threats, Threat Remediations, Threats By Risk Level . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Physical Security System Dashboard To Track Potential Threat
Physical Security System Dashboard To Track Potential ThreatThis slide showcases the dashboard of physical security system to ensure real-time monitoring and tracking of potential threats. The dashboard includes cyber and physical threats. Introducing our Physical Security System Dashboard To Track Potential Threat set of slides. The topics discussed in these slides are Vulnerabilities Select Threat, Insider Threats, Cyber Attack. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber response plan impact on business finances over the years. It includes key reasons of reduced cyber-attack costing such as Deliver an outstanding presentation on the topic using this Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Business, Finances, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat
Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates cyber incident tracking dashboard. It showcase number of open cases, resolved incidents, open tickets, resolved tickets, number of incidents per incident type and incidents by cyber attack type. Deliver an outstanding presentation on the topic using this Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Monitoring, Dashboard, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the incident assessment checklist. It includes key assessment areas such as incident documentation, communication, incident response team activation, containment of threats, etc. Present the topic in a bit more detail with this Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Response Team, Contain Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat
Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides a graphical presentation of cyber attacks and costs per incident. It includes key elements such as cost per incident, attack rate by month, cost of incident by assets, and time taken to detect and resolve the attack. Deliver an outstanding presentation on the topic using this Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Dashboard, Reported Incidents, Graphical Presentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat
Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about key roles, responsibilities, and accountability across the different team in the recovery plan. It includes key team such as executive, crisis management, business continuity experts, etc. Deliver an outstanding presentation on the topic using this Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Executive Team, Crisis Management, Business Continuity Expert using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
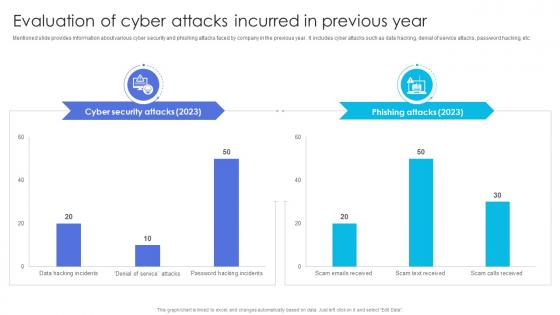 Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat
Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various cyber security and phishing attacks faced by company in the previous year. It includes cyber attacks such as data hacking, denial of service attacks, password hacking, etc. Deliver an outstanding presentation on the topic using this Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Information, Service, Evaluation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about incident status page leverage to communicate with internal stakeholders. It includes key elements such as target audience, incident page sample, and best practices. Present the topic in a bit more detail with this Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Stakeholders, Resolution Adopted. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat
Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various strategies adopted by company for preventing cyber attacks. It includes key threats such as ransomware, malware, phishing, and denial of service. Deliver an outstanding presentation on the topic using this Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Strategies, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS
Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint detection and response EDR dashboard which can help analyze malicious operations Malops and provide information about scans, investigations, activities, etc.Deliver an outstanding presentation on the topic using this Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Affected, Affected Users, Recent Activity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major IOT Security Threats And Its Negative Effects
Major IOT Security Threats And Its Negative EffectsThis slide showcases major security threats that disrupt the operations. Threats covered are buffer overflow, SQL injection, worm, botnet, ransomware, password, phishing, crypto jacking, etc. Presenting our well structured Major IOT Security Threats And Its Negative Effects. The topics discussed in this slide are Negative Effective, Lack Visibility, Poor Testing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Standard Cyber Threat Hunting Activities
Standard Cyber Threat Hunting ActivitiesThis slide highlights common cyber threat-hunting activities, such as clustering, grouping, stack counting, and so on. Deliver an outstanding presentation on the topic using this Standard Cyber Threat Hunting Activities. Dispense information and present a thorough explanation of Clustering, Grouping, Stack Counting, Standard Cyber Threat using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Hunting Performance Monitoring Dashboard
Threat Hunting Performance Monitoring DashboardThis slide outlines the cyber threat hunting performance monitoring dashboard, including total number of rare threats found, threat purpose, threat severity, etc. Deliver an outstanding presentation on the topic using this Threat Hunting Performance Monitoring Dashboard. Dispense information and present a thorough explanation of Threat Hunting Performance, Monitoring Dashboard, Rare Threats Found, Threat Purpose, Threat Severity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Hunting Services Market Analysis
Threat Hunting Services Market AnalysisThis slide represents the global market analysis summary for threat-hunting services, including market segmentation, top key players, market size, and regional analysis. Present the topic in a bit more detail with this Threat Hunting Services Market Analysis. Use it as a tool for discussion and navigation on Threat Hunting Services, Market Analysis, Market Segmentation, Regional Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS
Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SSThis slides showcases dashboard that can help to track number of cyber threats in organization. Its key elements are hacker attacks, spyware, viruses and zero day attacks Present the topic in a bit more detail with this Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Track Cyber Threats, Attacks Types This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS
Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Support And Maintenance, Device Troubleshooting, Access Control This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS
Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Before Mobile Security, Management Plan This template is free to edit as deemed fit for your organization. Therefore download it now.
-
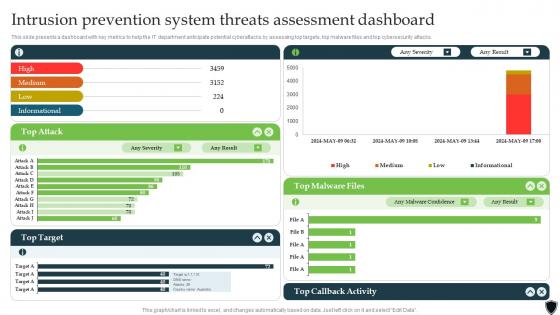 Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS
Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SSThis slide presents a dashboard with key metrics to help the IT department anticipate potential cyberattacks by assessing top targets, top malware files and top cybersecurity attacks. Present the topic in a bit more detail with this Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS. Use it as a tool for discussion and navigation on Callback Activity, Malware Files, Target. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Dashboard For Threat Detection And Response
Network Security Dashboard For Threat Detection And ResponseThis slide illustrates KPI Dashboard of network security including attack type, authentication, firewall events, and attack rates. Introducing our Network Security Dashboard For Threat Detection And Response set of slides. The topics discussed in these slides are Attack Type, Authentication, Firewall Events. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Threats For E Commerce Websites
Network Security Threats For E Commerce WebsitesThis slide demonstrates threats affecting e commerce websites including factors driving threats. Presenting our well structured Network Security Threats For E Commerce Websites. The topics discussed in this slide are Factors Driving Threats, Increased Online Transactions, Ransomware Trends. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service Challenges
Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service ChallengesThis slide showcases current vulnerabilities in b2b ecommerce platforms, referable for businesses in recognizing major issues. It provides details about the lack of proper security testing, inadequate encryption protocols, etc.Present the topic in a bit more detail with this Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service Challenges. Use it as a tool for discussion and navigation on Inadequate Encryption Protocols, Proper Security Testing, Software And Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.





