Powerpoint Templates and Google slides for Terrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Threat Dashboard With KPI Metrics
Cyber Security Threat Dashboard With KPI MetricsThis slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Introducing our Cyber Security Threat Dashboard With KPI Metrics set of slides. The topics discussed in these slides are Cyber Security Threat, Dashboard, KPI Metrics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing
Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Time To Fix Security Threat With Manual Testing. Use it as a tool for discussion and navigation on Manual, Testing, Security Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness
KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security AwarenessThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Deliver an outstanding presentation on the topic using this KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based Role using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats
Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Time To Fix Security Threat With Manual Testing Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Firewall KPIs Dashboard for Threat Tracking in WAF
Application Firewall KPIs Dashboard for Threat Tracking in WAFThis slide depicts how threat risk will be monitored and threat detection will be done in the organization through web application firewall implementation. Present the topic in a bit more detail with this Application Firewall KPIs Dashboard for Threat Tracking in WAF. Use it as a tool for discussion and navigation on Monthly Threat Status, Current Risk Status, Threats Based On Role. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training
KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness TrainingThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Current Risk Status, Threats By Owners, Risk By Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
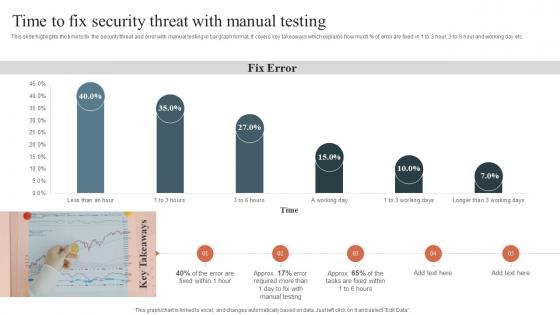 Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide
Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response GuideThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Present the topic in a bit more detail with this Time To Fix Security Threat With Manual Testing Security Orchestration Automation And Response Guide. Use it as a tool for discussion and navigation on Time To Fix, Security Threat, Manual Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat And Vulnerability Management Program Analysis Dashboard
Threat And Vulnerability Management Program Analysis DashboardThis slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Presenting our well structured Threat And Vulnerability Management Program Analysis Dashboard. The topics discussed in this slide are Exposure Score, Top Vulnerable Software, Severity Distribution. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Quarterly Comparison Of Cloud Security Threats
Quarterly Comparison Of Cloud Security ThreatsThis slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Presenting our well structured Quarterly Comparison Of Cloud Security Threats. The topics discussed in this slide are Quarterly, Comparison Of Cloud Security, Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity
Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat IntensityMentioned slide displays phase model that can be used by an organization to visualize corporate crisis threat intensity with respect to time. Increase audience engagement and knowledge by dispensing information using Effectively Handling Crisis To Restore Phase Model To Visualize Corporate Crisis Threat Intensity. This template helps you present information on four stages. You can also present information on Strategic Crisis, Threat To Viability, Liquidity Crisis, Insolvency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
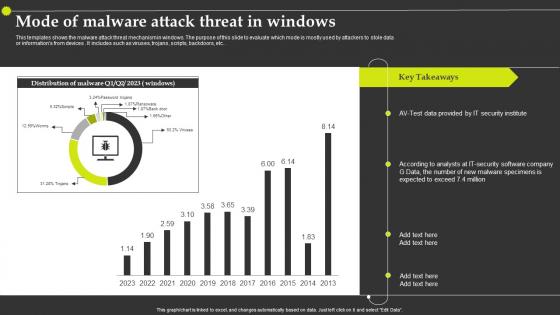 Mode Of Malware Attack Threat In Windows
Mode Of Malware Attack Threat In WindowsThis templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices . It includes such as viruses, trojans, scripts, backdoors, etc.Introducing our Mode Of Malware Attack Threat In Windows set of slides. The topics discussed in these slides are Security Institute, Malware Specimens, Security Software Company. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview
Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace OverviewThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Current Potential Implications Faced By Firm As Threats Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Employees, Financial, Records using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats Management Dashboard Managing It Threats At Workplace Overview
Cyber Threats Management Dashboard Managing It Threats At Workplace OverviewThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Present the topic in a bit more detail with this Cyber Threats Management Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Rating, Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview
Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Present the topic in a bit more detail with this Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Cybersecurity, Management, Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview
Financial Performance Tracking Dashboard Managing It Threats At Workplace OverviewThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Present the topic in a bit more detail with this Financial Performance Tracking Dashboard Managing It Threats At Workplace Overview. Use it as a tool for discussion and navigation on Receivables, Revenue, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Reporting Dashboard Managing IT Threats At Workplace Overview
Incident Reporting Dashboard Managing IT Threats At Workplace OverviewThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Incident Reporting Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Assignee, Resolved, Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview
Statistics Associated To Workplace Threats Managing IT Threats At Workplace OverviewThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Statistics, Workplace, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Reasons Of Cyber Bullying Among Young People
Major Reasons Of Cyber Bullying Among Young PeopleThis slide showcases statistical data depicting the harmful impact of cyberbullying on individuals. It also includes proportion depicting various impacts such as social anxiety, suicidal thoughts, eating disorder, etc. Introducing our Major Reasons Of Cyber Bullying Among Young People set of slides. The topics discussed in these slides are Percent, Online, Target. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cases Of Cyber Bullying In Schools Due To Mobile Use
Cases Of Cyber Bullying In Schools Due To Mobile UseThis slide showcases the proportion of principal reported cyberbullying in schools where mobile phones are permitted or prohibited. It also includes rate of cell phones allowed and not allowed in school .Introducing our Cases Of Cyber Bullying In Schools Due To Mobile Use set of slides. The topics discussed in these slides are Apparent, Difference, Cyberbullying. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Bullying Cases Occurred In Various Areas
Cyber Bullying Cases Occurred In Various AreasPresenting our well structured Cyber Bullying Cases Occurred In Various Areas. The topics discussed in this slide are Respondents, Social, Media. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Bullying Of Children In Different Regions
Cyber Bullying Of Children In Different RegionsThis slide showcases statistical data from different countries experiencing online bullying. It also includes percentage of different countries such as brazil, Egypt, china, Italy, etc. Introducing our Cyber Bullying Of Children In Different Regions set of slides. The topics discussed in these slides are Adolescents, Between, Bullying. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Depicting Effects Of Cyber Bullying On Children
Data Depicting Effects Of Cyber Bullying On ChildrenThis slide showcases statistical data regarding childrens problems caused by cyberbullying to understand its effect and apply effective measures. It also includes the frequency of issues such as drug abuse, self harm, etc. Introducing our Data Depicting Effects Of Cyber Bullying On Children set of slides. The topics discussed in these slides are Experienced, Cyberbullying, Spreading. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Forms Of Various Cyber Bullying In The Society
Forms Of Various Cyber Bullying In The SocietyThis slide showcases various forms of online harassment that take place. It also includes proportion regarding forms of bullying such as sending screenshot, trolling , etc. Introducing our Forms Of Various Cyber Bullying In The Society set of slides. The topics discussed in these slides are Bullies, Communications, Response. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
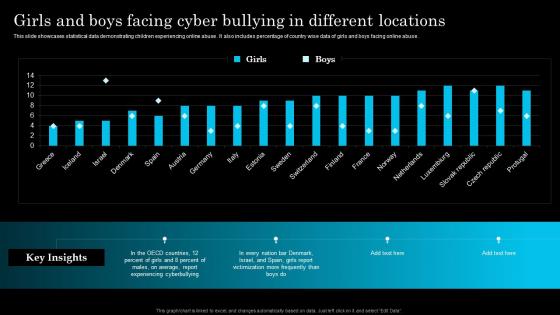 Girls And Boys Facing Cyber Bullying In Different Locations
Girls And Boys Facing Cyber Bullying In Different LocationsThis slide showcases statistical data demonstrating children experiencing online abuse . It also includes percentage of country wise data of girls and boys facing online abuse . Presenting our well structured Girls And Boys Facing Cyber Bullying In Different Locations. The topics discussed in this slide are OECD, Percent, Denmark. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Harmful Impacts Of Cyber Bullying On Individuals
Harmful Impacts Of Cyber Bullying On IndividualsThis slide showcases statistical data depicting the harmful impact of cyberbullying on individuals. It also includes proportion depicting various impacts such as social anxiety, suicidal thoughts, eating disorder, etc. Introducing our Harmful Impacts Of Cyber Bullying On Individuals set of slides. The topics discussed in these slides are According, Cyber, Esteem. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber bullying cases on various social media platforms
Cyber bullying cases on various social media platformsThis slide showcases statistical data depicting the reasons for cyberbullying among young generation. It also includes percentage of reasons such as internet and hobbies, household income, academic performances, etc. Presenting our well structured Cyber bullying cases on various social media platforms. The topics discussed in this slide are Cyberbullies, Commit, Disgrace. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Most Common Types Of Cyber Bullying At School
Most Common Types Of Cyber Bullying At SchoolThis slide showcases the most prevalent sort of bullying in schools. It also includes percentages regarding verbal harassment, Social harassment, physical bullying, cyberbullying, etc. Introducing our Most Common Types Of Cyber Bullying At School set of slides. The topics discussed in these slides are According, Frequent, Harassment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Negative Effects Of Cyber Bullying On Victims
Negative Effects Of Cyber Bullying On VictimsThis slide showcases the frequency of several detrimental repercussions of cyberbullying on victims to make inquiry easier. It also includes percentage of effects such as skipping classes, social anxiety, etc. Presenting our well structured Negative Effects Of Cyber Bullying On Victims. The topics discussed in this slide are According, Encounter, Attempt. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Psychological Impact Due To Cyber Bullying On Females
Psychological Impact Due To Cyber Bullying On FemalesThis slide showcases graphical data regarding the psychological impact on the women facing online bullying and harassment. It also includes the percentage of impacts such as insomnia, less focus, etc. Introducing our Psychological Impact Due To Cyber Bullying On Females set of slides. The topics discussed in these slides are Loss, Confidence, Consequence. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Reasons Of Cyber Bullying Cases Among Teens
Reasons Of Cyber Bullying Cases Among TeensThis slide showcases statistics depicting major reasons why cyberbullying happens, that demonstrate the magnitude of this growing problem and the necessity for an effective response. It also includes frequency of reasons such as appearance, race ,etc. Presenting our well structured Reasons Of Cyber Bullying Cases Among Teens. The topics discussed in this slide are Cyberbullying, Approximately, Members. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ways That Works For Dealing Cyber Bullying
Ways That Works For Dealing Cyber BullyingThis slide showcases statistical data regarding different ways that work the best to deal with online bullying activities. It also includes frequency of various methods such as blocking, ignoring, police complaint, etc. Introducing our Ways That Works For Dealing Cyber Bullying set of slides. The topics discussed in these slides are Almost, Blocking, Frequently. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Analysis Of Hospitalization Length Of Stay With Drug Abuse Comorbidity
Analysis Of Hospitalization Length Of Stay With Drug Abuse ComorbidityThis slide showcases hospitalization length of stay analysis with drug abuse comorbidity to ensure efficient proper utilization of the hospital. It also includes four years statistical data of different age group . Introducing our Analysis Of Hospitalization Length Of Stay With Drug Abuse Comorbidity set of slides. The topics discussed in these slides are Medicaid, Comorbidity, Insurance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat Management Action Plan Handling Pivotal Assets Associated With Firm
Threat Management Action Plan Handling Pivotal Assets Associated With FirmThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Handling Pivotal Assets Associated With Firm. Use it as a tool for discussion and navigation on Management, Resources, Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Initiatives To Safeguard Threats Handling Activities Tracking Dashboard
Essential Initiatives To Safeguard Threats Handling Activities Tracking DashboardThis slide provides details regarding various threats management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Deliver an outstanding presentation on the topic using this Essential Initiatives To Safeguard Threats Handling Activities Tracking Dashboard. Dispense information and present a thorough explanation of Breach Risk Trend, Threats Handling Activities, Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security
Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. Present the topic in a bit more detail with this Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Periodic Risk Assessment, Individuals, Implement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security
Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard Communicating Project Threat Status
Dashboard Communicating Project Threat StatusThe following slide showcases a dashboard providing insights about project risks status for managing and mitigating key issues. It highlights components such as inherent riks by period, control rate by period, risk category by total risk rating, residual risks by period, etc. Introducing our Dashboard Communicating Project Threat Status set of slides. The topics discussed in these slides are Communicating, Dashboard, Project. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Virtual Terrorism Attack Trends On Usa
Virtual Terrorism Attack Trends On UsaThis slide shows cyber terrorism attack trends on USA organizations for decade to highlight importance of cyber security systems. It includes valuation of losses, categories of cyber attacks and victim companies etc.Presenting our well structured Virtual Terrorism Attack Trends On Usa. The topics discussed in this slide are Internet Bureau, Ransom Malware, Software Companies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Virtual Terrorism Attack Trends Post Russia Ukraine War
Virtual Terrorism Attack Trends Post Russia Ukraine WarThis slides shows cyber attack trends on different countries post Russia-Ukraine War. It include countries such as Russia, Ukraine, United States etc.Introducing our Virtual Terrorism Attack Trends Post Russia Ukraine War set of slides. The topics discussed in these slides are Government Authorities, Russia Witnessed, Decrease Percentage. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Virtual Terrorism International Statistical Trends
Virtual Terrorism International Statistical TrendsThis slide shows International Statistical Trends of cyber terrorism at global level for building cyber security systems. It include statistics such as Global business attacks, International BYOD registrations etc.Presenting our well structured Virtual Terrorism International Statistical Trends. The topics discussed in this slide are Business Operations, Statistical Trends, International Businesses. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Kpi Dashboard For Tracking Cyber Security Threats Of Healthcare Organization
Kpi Dashboard For Tracking Cyber Security Threats Of Healthcare OrganizationThis slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Introducing our Kpi Dashboard For Tracking Cyber Security Threats Of Healthcare Organization set of slides. The topics discussed in these slides are Breakdown Of Threat, Business Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Drug Abuse Testing Market Sales
Drug Abuse Testing Market SalesThe mentioned slide showcases trends in the market of drug testing across globe and the reasons for expansion and slow down. It includes growth phase , maturity phase, decline phase and sales trends. Introducing our Drug Abuse Testing Market Sales set of slides. The topics discussed in these slides are Testing, Drug, Market. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Risk Management Dashboard For Tracking Threats And Attacks
Digital Risk Management Dashboard For Tracking Threats And AttacksThe purpose of this slide is to represent dashboard to monitor risks and cyber threats for efficient risk management. It includes various types of key performance indicators such as types of risks, severities, sources and risk meter. Introducing our Digital Risk Management Dashboard For Tracking Threats And Attacks set of slides. The topics discussed in these slides are Severities, Types Of Risk This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Cybersecurity Technology Threat Management
IoT Cybersecurity Technology Threat ManagementThe below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Presenting our well structured IoT Cybersecurity Technology Threat Management. The topics discussed in this slide are Cybersecurity, Technology, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Social assistance kpi for substance abuse recidivism rate ppt slide
Social assistance kpi for substance abuse recidivism rate ppt slidePresenting social assistance kpi for substance abuse recidivism rate ppt slide. This presentation slide shows one Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Substance Abuse Recidivism Rate. These KPI Powerpoint graphics are all data driven, and the shape automatically adjusts according to your data. Just right click on the KPI graphic, enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Boy crying child abuse template
Boy crying child abuse templatePresenting this set of slides with name - Boy Crying Child Abuse Template. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template boy head down image
Child abuse template boy head down imagePresenting this set of slides with name - Child Abuse Template Boy Head Down Image. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template finger pointing image
Child abuse template finger pointing imagePresenting this set of slides with name - Child Abuse Template Finger Pointing Image. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template girl covering her ears with hands
Child abuse template girl covering her ears with handsPresenting this set of slides with name - Child Abuse Template Girl Covering Her Ears With Hands. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template with kid hiding in box
Child abuse template with kid hiding in boxPresenting this set of slides with name - Child Abuse Template With Kid Hiding In Box. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template with kid sitting on bench
Child abuse template with kid sitting on benchPresenting this set of slides with name - Child Abuse Template With Kid Sitting On Bench. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template with man giving bad words to kid
Child abuse template with man giving bad words to kidPresenting this set of slides with name - Child Abuse Template With Man Giving Bad Words To Kid. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template with man hitting child
Child abuse template with man hitting childPresenting this set of slides with name - Child Abuse Template With Man Hitting Child. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child abuse template with man scaring kid
Child abuse template with man scaring kidPresenting this set of slides with name - Child Abuse Template With Man Scaring Kid. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Child crying abuse template asking for help image
Child crying abuse template asking for help imagePresenting this set of slides with name - Child Crying Abuse Template Asking For Help Image. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.
-
 Girl child crying abuse template
Girl child crying abuse templatePresenting this set of slides with name - Girl Child Crying Abuse Template. This is a one stage process. The stages in this process are Child Abuse, Sexual Harm, Child Maltreatment.





