Powerpoint Templates and Google slides for Security Vendors
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 A60 Email Security Best Practices And Email Security Vendor Market Share
A60 Email Security Best Practices And Email Security Vendor Market ShareThis slide represents the market of different email security service providers available in the market. The purpose of this slide is to depict the market share of each of the service providers, such as Symantec, Microsoft, Google, Mimecast, etc. Present the topic in a bit more detail with this A60 Email Security Best Practices And Email Security Vendor Market Share. Use it as a tool for discussion and navigation on Microsoft Accounts, Email Security Market. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb
Party Vendor Management Security Best Practices In Powerpoint And Google Slides CpbPresenting Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Party Vendor Management Security Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors
Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker VendorsThis slide outlines the popular Cloud Access Security Broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Mid To Large Enterprises, Robust Integration, Cisco Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Multiple Blockchain Security Vendors Hands On Blockchain Security Risk BCT SS V
Comparative Analysis Of Multiple Blockchain Security Vendors Hands On Blockchain Security Risk BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Multiple Blockchain Security Vendors Hands On Blockchain Security Risk BCT SS V. Dispense information and present a thorough explanation of Description, Parameters, Experience using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Deliver an outstanding presentation on the topic using this Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Popular Cloud Access Security Broker Vendors Next Generation CASB
Popular Cloud Access Security Broker Vendors Next Generation CASBThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Deliver an outstanding presentation on the topic using this Popular Cloud Access Security Broker Vendors Next Generation CASB Dispense information and present a thorough explanation of Forcepoint, Cisco Systems, Microsoft, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Popular Next Generation Firewall Vendors In Market
Firewall Network Security Popular Next Generation Firewall Vendors In MarketThis slide outlines the leading vendors for Next Generation Firewalls in the industry. The purpose of this slide is to showcase the different popular vendors of next-generation firewalls, such as Barracuda, Cisco, Fortinet, Palo Alto Networks, SonicWall, and Sophos. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Popular Next Generation Firewall Vendors In Market This template helps you present information on Four stages. You can also present information on Requested Data, NAT Firewall, Forwarding Table using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Top Firewall As A Service Vendors In Global Market
Firewall Network Security Top Firewall As A Service Vendors In Global MarketThis slide outlines the leading vendors for Firewall as a Service in the global market. The purpose of this slide is to showcase the best FaaS vendors, including CrowdStrike, Palo Alto Networks, Zscaler, Fortinet, Cisco, and GFI Software. Present the topic in a bit more detail with this Firewall Network Security Top Firewall As A Service Vendors In Global Market Use it as a tool for discussion and navigation on Unique Selling Point, Network Infrastructure This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS V
Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 or 7 availability, etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Popular Cloud Access Security Broker Vendors CASB Cloud Security
Popular Cloud Access Security Broker Vendors CASB Cloud SecurityThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Deliver an outstanding presentation on the topic using this Popular Cloud Access Security Broker Vendors CASB Cloud Security. Dispense information and present a thorough explanation of Cloud Access Security Broker Vendors, Multiple Leading Service, Software Or Appliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How To Strategically Engage Vendors To Secure Procurement Excellence
How To Strategically Engage Vendors To Secure Procurement ExcellenceThis slide showcases the ways engaging distributors for securing procurement excellence which helps an organization to manage and update approved suppliers lists effectively and quickly. It include details such as analyze vendor performance, provide self service portals, etc. Presenting our set of slides with How To Strategically Engage Vendors To Secure Procurement Excellence. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyze Vendor Performance, Service Portals, Vendor Dashboards.
-
 Security Checklist For Choosing A Kyc Vendor
Security Checklist For Choosing A Kyc VendorThe purpose of this slide is to provide a security checklist for choosing a KYC vendor, ensuring compliance, data security, and reliability. Elements in the checklist are security measures namely document detection, verification of MRZ digits, etc. Presenting our well structured Security Checklist For Choosing A Kyc Vendor. The topics discussed in this slide are Data Extraction From RFID Chip, Validation Of Dates, Hologram Detection Verification. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Four Step Approach To Select OT Cyber Security Vendor
Four Step Approach To Select OT Cyber Security VendorThis slide focuses on four-step approach that assists IT companies in selecting right vendor to enhance their OT cyber security according to NIST and ICS framework. It includes various steps such as access engineering involvement, framework pillar prioritization, etc. Introducing our premium set of slides with Four Step Approach To Select OT Cyber Security Vendor Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Engineering Involvement, Framework Pillar Prioritization So download instantly and tailor it with your information.
-
 A vendor application security testing diagram example ppt presentation
A vendor application security testing diagram example ppt presentationPresenting a vendor application security testing diagram example ppt presentation. This is a vendor application security testing diagram example ppt presentation. This is a three stage process. The stages in this process are enterprise customer, vast program, 3rd party vendor.
-
 Comparison of cyber threat security vendors with pricing and use case
Comparison of cyber threat security vendors with pricing and use caseMentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Presenting our well structured Comparison Of Cyber Threat Security Vendors With Pricing And Use Case. The topics discussed in this slide are Financial Services, Cyber Security, Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist For Selecting Operational Technology Security Vendor
Checklist For Selecting Operational Technology Security VendorFollowing slide shows a comprehensive operational technology OT checklist which can be used by an organization for selecting the security vendor. organization can select the best security vendor for improving OT security system after considering points such as vendor understanding regard to OT and IT risk assessment etc. Deliver an outstanding presentation on the topic using this Checklist For Selecting Operational Technology Security Vendor. Dispense information and present a thorough explanation of Checklist, Vendor Understand OT, IT Risk Assessment, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Operational Technology Security Vendors
Comparative Assessment Of Operational Technology Security VendorsMentioned slide showcase various vendors who offers operational technology OT security solutions to business organizations. Organization can choose the best among security vendors by making comparison on the basis of features, deployment, operating systems, price and ratings. Present the topic in a bit more detail with this Comparative Assessment Of Operational Technology Security Vendors. Use it as a tool for discussion and navigation on Types Vendors, Key Features, Deployment, Operating Systems, Pricing In USD, Ratings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operational Technology Security Services Offered By Vendors
Operational Technology Security Services Offered By VendorsMentioned slide illustrates operational technology OT services offered by vendors to business organizations. Information covered in this slide is related to services such as network operations, fabric connections, multi-cloud security, application security etc. Increase audience engagement and knowledge by dispensing information using Operational Technology Security Services Offered By Vendors. This template helps you present information on eight stages. You can also present information on Network Operations, Multi Cloud Security, Application Security, Fabric Connections, Information Security, Secure Access, Endpoint Protection, Fabric API using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vendor Selection Steps For Cyber Security Risk
Vendor Selection Steps For Cyber Security RiskThe following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting our set of slides with name Vendor Selection Steps For Cyber Security Risk. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment Methodology, Tailor Assessment, Risk Threshold, Cyber Security Assessment.
-
 Cloud Architecture And Security Review Where Is The Complexity Too Many Cloud Vendors
Cloud Architecture And Security Review Where Is The Complexity Too Many Cloud VendorsThis slide covers the number of cloud providers are being used which are increasing complexity and their importance in managing companys cloud capabilities. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Where Is The Complexity Too Many Cloud Vendors. Dispense information and present a thorough explanation of Cloud Service Providers, Cyber Security Service Providers, Cloud Consulting Services, Managed Service Providers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS
Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SSThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS Dispense information and present a thorough explanation of Experience, Detect Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Vendor Management Policy Overview And Considerations
Cyber Security Policy Vendor Management Policy Overview And ConsiderationsThis slide represents the vendor management policy, and it also includes points to be considered when choosing a vendor. This policy is about the vendor with whom organizations share their critical information. Present the topic in a bit more detail with this Cyber Security Policy Vendor Management Policy Overview And Considerations. Use it as a tool for discussion and navigation on Management, Considerations, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
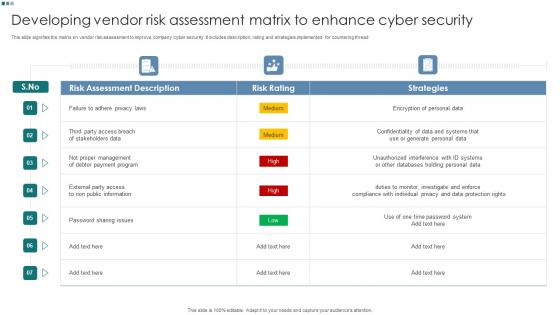 Developing Vendor Risk Assessment Matrix To Enhance Cyber Security
Developing Vendor Risk Assessment Matrix To Enhance Cyber SecurityThis slide signifies the matrix on vendor risk assessment to improve company cyber security. It includes description, rating and strategies implemented for countering thread. Introducing our Developing Vendor Risk Assessment Matrix To Enhance Cyber Security set of slides. The topics discussed in these slides are Strategies, Risk Assessment, Risk Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Popular Cloud Access Security Broker Vendors Ppt Slides Format Ideas
Popular Cloud Access Security Broker Vendors Ppt Slides Format IdeasThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Present the topic in a bit more detail with this Popular Cloud Access Security Broker Vendors Ppt Slides Format Ideas. Use it as a tool for discussion and navigation on Vendor, Suitable, Features. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V
Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Present the topic in a bit more detail with this Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Assessment, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vendor Data Security Checklist For Market Research Company
Vendor Data Security Checklist For Market Research CompanyThe purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Introducing our Vendor Data Security Checklist For Market Research Company set of slides. The topics discussed in these slides are Supplier Has Invested, Protection Information This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Vendors In Powerpoint And Google Slides Cpb
Security Vendors In Powerpoint And Google Slides CpbPresenting our Security Vendors In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Vendors. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Corporate security vendor ppt powerpoint presentation summary cpb
Corporate security vendor ppt powerpoint presentation summary cpbPresenting this set of slides with name Corporate Security Vendor Ppt Powerpoint Presentation Summary Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Corporate Security Vendor to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Automate vendor security ppt powerpoint presentation inspiration outfit cpb
Automate vendor security ppt powerpoint presentation inspiration outfit cpbPresenting this set of slides with name Automate Vendor Security Ppt Powerpoint Presentation Inspiration Outfit Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Automate Vendor Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security checklist vendors ppt powerpoint presentation gallery cpb
Information security checklist vendors ppt powerpoint presentation gallery cpbPresenting this set of slides with name Information Security Checklist Vendors Ppt Powerpoint Presentation Gallery Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Information Security Checklist Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Industrial cyber security vendor landscape with application enablement
Industrial cyber security vendor landscape with application enablementPresenting this set of slides with name Internet Of Things Ecosystem Vendor Landscape With Data Ingestion. The topics discussed in these slides are Application Enablement, Edge And Cloud, Advanced Industrial Analytics, Connectivity, Integrated Development Environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Web app security testing vendors ppt powerpoint presentation professional summary cpb
Web app security testing vendors ppt powerpoint presentation professional summary cpbPresenting this set of slides with name Web App Security Testing Vendors Ppt Powerpoint Presentation Professional Summary Cpb. This is a seven stage process. The stages in this process are Web App Security Testing Vendors. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Web application security vendors ppt presentation pictures themes cpb
Web application security vendors ppt presentation pictures themes cpbPresenting this set of slides with name Web Application Security Vendors Ppt Presentation Pictures Themes Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Web Application Security Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application security testing vendors ppt powerpoint presentation outline show cpb
Application security testing vendors ppt powerpoint presentation outline show cpbPresenting this set of slides with name Application Security Testing Vendors Ppt Powerpoint Presentation Outline Show Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Application Security Testing Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Web application security scanning vendors ppt powerpoint presentation layouts cpb
Web application security scanning vendors ppt powerpoint presentation layouts cpbPresenting this set of slides with name Web Application Security Scanning Vendors Ppt Powerpoint Presentation Layouts Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Web Application Security Scanning Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Web app security scanning vendors ppt powerpoint presentation ideas shapes cpb
Web app security scanning vendors ppt powerpoint presentation ideas shapes cpbPresenting this set of slides with name Web App Security Scanning Vendors Ppt Powerpoint Presentation Ideas Shapes Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Web App Security Scanning Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Web app security testing vendors ppt powerpoint presentation outline maker cpb
Web app security testing vendors ppt powerpoint presentation outline maker cpbPresenting this set of slides with name Web App Security Testing Vendors Ppt Powerpoint Presentation Outline Maker Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Web App Security Testing Vendors to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Secure vendor access ppt powerpoint presentation summary clipart images cpb
Secure vendor access ppt powerpoint presentation summary clipart images cpbPresenting Secure Vendor Access Ppt Powerpoint Presentation Summary Clipart Images Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase seven stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Vendor Access. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Vendor security risk management process ppt powerpoint presentation file cpb
Vendor security risk management process ppt powerpoint presentation file cpbPresenting this set of slides with name Vendor Security Risk Management Process Ppt Powerpoint Presentation File Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Vendor Security Risk Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Firewall Implementation For Cyber Security Next Generation Firewall Vendor Comparison Chart Sheet
Firewall Implementation For Cyber Security Next Generation Firewall Vendor Comparison Chart SheetThis slide outlines the comparative analysis of different firewall vendors. The purpose of this slide is to highlight the key differences between different firewall vendors in terms of firewall products, key features, unique selling points, and cost. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Next Generation Firewall Vendor Comparison Chart Sheet. Use it as a tool for discussion and navigation on Comparative Analysis, Firewall Vendors, Firewall Products, Unique Selling Points, Vendor Comparison Chart. This template is free to edit as deemed fit for your organization. Therefore download it now.



