Powerpoint Templates and Google slides for Security Tools
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
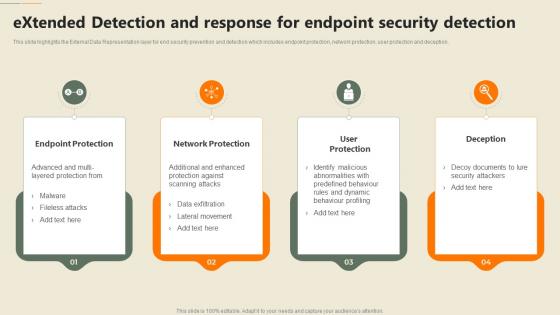 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Security Automation In Information Technology
Icons Slide Security Automation In Information TechnologyPresent the topic in a bit more detail with this Icons Slide Security Automation In Information Technology. Use it as a tool for discussion and navigation on Icons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
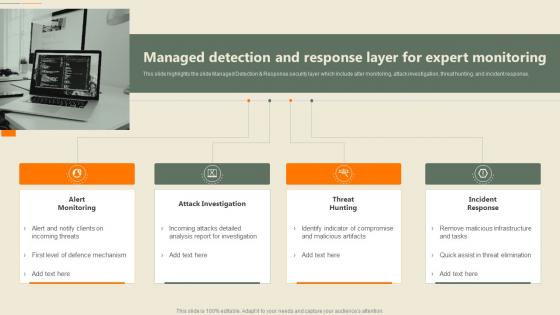 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation In Information Technology
Right Time To Add Automation In Security Security Automation In Information TechnologyThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Deliver an outstanding presentation on the topic using this Right Time To Add Automation In Security Security Automation In Information Technology. Dispense information and present a thorough explanation of Individual, Insights, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
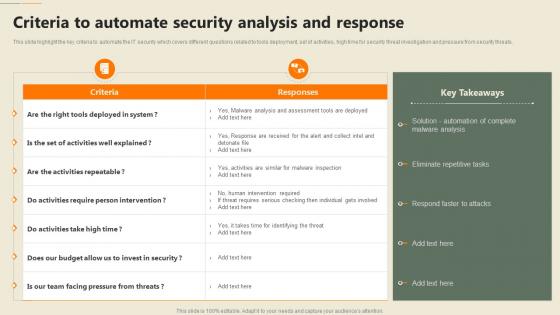 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Impacts Of Ineffective Information Technology Security
Security Automation In Information Technology Impacts Of Ineffective Information Technology SecurityThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Impacts Of Ineffective Information Technology Security. This template helps you present information on five stages. You can also present information on Information, Technology, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation In Information Technology Table Of Contents
Security Automation In Information Technology Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Automation In Information Technology Table Of Contents. This template helps you present information on one stages. You can also present information on Security Automation, Processes, Security Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Security Automation In Information Technology
Table Of Contents Security Automation In Information TechnologyPresent the topic in a bit more detail with this Table Of Contents Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Architecture And Importance, Automation Dashboards. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unified Platform Integration For Security Automation Security Automation In Information Technology
Unified Platform Integration For Security Automation Security Automation In Information TechnologyThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration For Security Automation Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Access Management, Security Automation, Firewalls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Risks Associated With EDI Technology
Security Risks Associated With EDI TechnologyThis slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc. Introducing our Security Risks Associated With EDI Technology set of slides. The topics discussed in these slides are Security Risks Associated, EDI Technology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Automation Tools With Functions And Cost
Security Automation Tools With Functions And CostThe following slide highlights various tools that can assist company to automate security process. The various tools could be Robotic process automation security orchestration, automation and response and extended detection Introducing our premium set of slides with Security Automation Tools With Functions And Cost. Elucidate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Expected Cost, Key Functions. So download instantly and tailor it with your information.
-
 Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology
Key Security Considerations For 5g For Threat Handling Developing 5g Transformative TechnologyThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology. Dispense information and present a thorough explanation of Considerations, Unauthorized Activities, Unauthorized Activities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Cyber Security Incident Response Tools
Comparative Assessment Of Cyber Security Incident Response ToolsThis slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Introducing our premium set of slides with name Comparative Assessment Of Cyber Security Incident Response Tools. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Comparative Assessment, Cyber Security, Incident Response Tools. So download instantly and tailor it with your information.
-
 Technology Replacement Model For Business Network Security
Technology Replacement Model For Business Network SecurityThis slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products. Introducing our premium set of slides with name Technology Replacement Model For Business Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Interoperable Solutions, Secured Business, Standalone Products. So download instantly and tailor it with your information.
-
 Blockchain Security Technology For Healthcare Industry
Blockchain Security Technology For Healthcare IndustryThis slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification. Presenting our set of slides with name Blockchain Security Technology For Healthcare Industry. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Blockchain Security, Technology, Healthcare Industry.
-
 Information Security Policy For Employees Information Technology Policy
Information Security Policy For Employees Information Technology PolicyThis slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Introducing Information Security Policy For Employees Information Technology Policy to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Company Infrastructure, IT Infrastructure, Data Processing Activities And Purposes, using this template. Grab it now to reap its full benefits.
-
 Overview Of Network Security Policy For Workers Information Technology Policy
Overview Of Network Security Policy For Workers Information Technology PolicyThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log in attempts, information starts up or shutdown, etc. Introducing Overview Of Network Security Policy For Workers Information Technology Policy to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organizations, Network Security, Information, using this template. Grab it now to reap its full benefits.
-
 Security Awareness And Training Policy Overview Information Technology Policy
Security Awareness And Training Policy Overview Information Technology PolicyThis slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Increase audience engagement and knowledge by dispensing information using Security Awareness And Training Policy Overview Information Technology Policy. This template helps you present information on six stages. You can also present information on Corporate Data, Security, Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Various Configuration Profiles Using MDM Technology Unified Endpoint Security
Determine Various Configuration Profiles Using MDM Technology Unified Endpoint SecurityThis slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Present the topic in a bit more detail with this Determine Various Configuration Profiles Using MDM Technology Unified Endpoint Security. Use it as a tool for discussion and navigation on Internet Settings, Processes Configuration, Profile Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impacts Of Ineffective Information Technology Security Security Orchestration Automation
Impacts Of Ineffective Information Technology Security Security Orchestration AutomationThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Introducing Impacts Of Ineffective Information Technology Security Security Orchestration Automation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Impacts Of Ineffective, Information Technology, Security, using this template. Grab it now to reap its full benefits.
-
 What Security Features Does 5g 5th Generation Technology Include Mobile Communication Standards 1g To 5g
What Security Features Does 5g 5th Generation Technology Include Mobile Communication Standards 1g To 5gThis slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Introducing What Security Features Does 5g 5th Generation Technology Include Mobile Communication Standards 1g To 5g to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on 5g Network, 5g Technology, using this template. Grab it now to reap its full benefits.
-
 Comparison Assessment Of Enterprise Security Operations Tools
Comparison Assessment Of Enterprise Security Operations ToolsThis slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Introducing our Comparison Assessment Of Enterprise Security Operations Tools set of slides. The topics discussed in these slides are Features, Cost Involved, User Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Orchestration Automation Security Automation Integrates Tools Systems And Processes
Security Orchestration Automation Security Automation Integrates Tools Systems And ProcessesThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver an outstanding presentation on the topic using this Security Orchestration Automation Security Automation Integrates Tools Systems And Processes. Dispense information and present a thorough explanation of Security Automation, Robotic Process, Security Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Orchestration Automation And Response Different Security Automation Tools With Pros And Cons
Security Orchestration Automation And Response Different Security Automation Tools With Pros And ConsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Introducing Security Orchestration Automation And Response Different Security Automation Tools With Pros And Cons to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Automation, Integrates Tools, Systems And Processes, using this template. Grab it now to reap its full benefits.
-
 Applications Of Confidential Computing Security Technology
Applications Of Confidential Computing Security TechnologyThe following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting our set of slides with name Applications Of Confidential Computing Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Guard Business Process, Collaboration, Customer Satisfaction.
-
 Applications Of Data Masking Security Technology
Applications Of Data Masking Security TechnologyThis slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Introducing our premium set of slides with Applications Of Data Masking Security Technology. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Date Aging, Encryption, Scrambling, Nulling Out, Substitution. So download instantly and tailor it with your information.
-
 Automobile Industry Transformation With Security Technology
Automobile Industry Transformation With Security TechnologyThe following slide highlights the use of automobile security technology to prevent theft related issues which results in improved customer loyalty and brand building. Key elements are smart apps and sensor alarms. Introducing our Automobile Industry Transformation With Security Technology set of slides. The topics discussed in these slides are Smart Apps, Sensor Alarms. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Blockchain Security Technology Working Flowchart
Blockchain Security Technology Working FlowchartThis slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Introducing our premium set of slides with Blockchain Security Technology Working Flowchart. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Blockchain Security, Technology, Working Flowchart. So download instantly and tailor it with your information.
-
 Business Data Encryption Security Technology
Business Data Encryption Security TechnologyThis slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting our set of slides with name Business Data Encryption Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy, Authentication, Regulatory Compliance, Security.
-
 Cloud Computing Security Technology Framework
Cloud Computing Security Technology FrameworkThis slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Introducing our premium set of slides with Cloud Computing Security Technology Framework. Elucidate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Network Security, Others, Monitoring, Governance. So download instantly and tailor it with your information.
-
 Cloud Deployment Security Technology Icon
Cloud Deployment Security Technology IconPresenting our set of slides with name Cloud Deployment Security Technology Icon. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Deployment Security, Technology, Icon.
-
 Cyber Security Management Technology Framework
Cyber Security Management Technology FrameworkThis slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Introducing our premium set of slides with Cyber Security Management Technology Framework. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protect, Identify, Detect, Respond, Recover. So download instantly and tailor it with your information.
-
 Digital Banking Security Technology Trends
Digital Banking Security Technology TrendsThe following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting our set of slides with name Digital Banking Security Technology Trends. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Login Protection, Cloud Computing, AI.
-
 Firewall Data Network Security Technology
Firewall Data Network Security TechnologyThe below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Introducing our premium set of slides with Firewall Data Network Security Technology. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Packet Filtering, Proxy Service, UTM, Stateful Inspection, Next Gen Firewall. So download instantly and tailor it with your information.
-
 Information Technology Operations Security Icon
Information Technology Operations Security IconPresenting our set of slides with name Information Technology Operations Security Icon. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Technology, Operations Security, Icon.
-
 IOT Smart Home Security Technology
IOT Smart Home Security TechnologyThis slide provides the use of smart security technology to get real time monitoring of home and obtain authenticity. Key features mentioned are smart cameras, biometric locks, smart cameras, connected switches and fire sensor. Introducing our premium set of slides with IOT Smart Home Security Technology. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Biometric Locks, Smart Cameras, Connected Switches, Fire Sensor. So download instantly and tailor it with your information.
-
 Mobile Application Security Technology Icon
Mobile Application Security Technology IconIntroducing our premium set of slides with Mobile Application Security Technology Icon. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mobile Application, Security, Technology, Icon. So download instantly and tailor it with your information.
-
 User Authentication And Authorization Security Technology
User Authentication And Authorization Security TechnologyThis slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Presenting our set of slides with name User Authentication And Authorization Security Technology. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Password Based, Multi Factor, Certificate Based, Biometrics, Token Based.
-
 Cyber Security Tools Technologies In Powerpoint And Google Slides Cpb
Cyber Security Tools Technologies In Powerpoint And Google Slides CpbPresenting our Cyber Security Tools Technologies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Tools Technologies. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Icon For Payment Security Technology In Investor Transactions
Icon For Payment Security Technology In Investor TransactionsPresenting our set of slides with Icon For Payment Security Technology In Investor Transactions. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Payment Security Technology, Investor Transactions.
-
 Data Security Governance Tool Assessment Matrix
Data Security Governance Tool Assessment MatrixThis slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Introducing our premium set of slides with Data Security Governance Tool Assessment Matrix. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Intelligence, Advanced Data Governance. So download instantly and tailor it with your information.
-
 Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics
Security Architecture In 5G Technology Working Of 5G Technology IT Ppt TopicsThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Present the topic in a bit more detail with this Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics. Use it as a tool for discussion and navigation on Security Architecture, Technology, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas
Security In 5G Technology Architecture Working Of 5G Technology IT Ppt IdeasThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas. This template helps you present information on five stages. You can also present information on Mobile Technologys, Service, Delivery Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 1G To 5G Technology What Security Features Does 5G 5th Generation Technology Include
1G To 5G Technology What Security Features Does 5G 5th Generation Technology IncludeThis slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Introducing 1G To 5G Technology What Security Features Does 5G 5th Generation Technology Include Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Features, Technology Include, Authentication Confirmation, using this template. Grab it now to reap its full benefits.
-
 Security Technology In Use Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Technology In Use Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security technology in use colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security Technology In Use Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Technology In Use Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security technology in use monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security Architecture In 5G Technology Ppt Powerpoint Presentation Infographic
Security Architecture In 5G Technology Ppt Powerpoint Presentation InfographicThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Deliver an outstanding presentation on the topic using this Security Architecture In 5G Technology Ppt Powerpoint Presentation Infographic. Dispense information and present a thorough explanation of Security Functions, Security Management, Global Wireless Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides Template
Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides TemplateThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides Template. This template helps you present information on four stages. You can also present information on Security Procedures, Mobile Technology, Service Delivery Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Members Of Financial Security Department Kyc Transaction Monitoring Tools For Business Safety
Key Members Of Financial Security Department Kyc Transaction Monitoring Tools For Business SafetyThe following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Present the topic in a bit more detail with this Key Members Of Financial Security Department Kyc Transaction Monitoring Tools For Business Safety. Use it as a tool for discussion and navigation on Financial, Department, Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Roles And Responsibilities Financial Security Kyc Transaction Monitoring Tools For Business Safety
Major Roles And Responsibilities Financial Security Kyc Transaction Monitoring Tools For Business SafetyThe following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Present the topic in a bit more detail with this Major Roles And Responsibilities Financial Security Kyc Transaction Monitoring Tools For Business Safety. Use it as a tool for discussion and navigation on Responsibilities, Financial, Compliance Auditor . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Various Cloud Security Tools
Comparative Analysis Of Various Cloud Security ToolsThis slide shows comparison amongst various cloud security tools which can be used by the organization to select the best suitable tool. it also includes details about features, price and ratings. Introducing our Comparative Analysis Of Various Cloud Security Tools set of slides. The topics discussed in these slides are Comparative Analysis, Various, Cloud Security Tools. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Edge Computing Security Technology Icon
IoT Edge Computing Security Technology IconPresenting our well structured IoT Edge Computing Security Technology Icon. The topics discussed in this slide are Iot Edge Computing, Security Technology Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IoT Edge Computing Security Technology Image
IoT Edge Computing Security Technology ImagePresenting our set of slides with IoT Edge Computing Security Technology Image. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iot Edge Computing, Security Technology Image.
-
 Comparative Analysis Of Tools To Overcome Iot Security Challenges
Comparative Analysis Of Tools To Overcome Iot Security ChallengesThis slide highlights tools that help to solve security challenges in IoT devices and help to provide better customer services. Some of the elements of comparative analysis include tools, features, pricing, and additional comments. Presenting our well structured Comparative Analysis Of Tools To Overcome Iot Security Challenges. The topics discussed in this slide are Features, Sternum Iot.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 5G Network Technology Architecture Security Architecture In 5G Technology
5G Network Technology Architecture Security Architecture In 5G TechnologyThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Present the topic in a bit more detail with this 5G Network Technology Architecture Security Architecture In 5G Technology. Use it as a tool for discussion and navigation on System Wide Security, Security Functions, Trust Anchoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 5G Network Technology Architecture Security In 5G Technology Architecture
5G Network Technology Architecture Security In 5G Technology ArchitectureThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Introducing 5G Network Technology Architecture Security In 5G Technology Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Technologys Security, Service Delivery Process, 5G Security Features, using this template. Grab it now to reap its full benefits.





