Powerpoint Templates and Google slides for Security Tools
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Revenue Streams Smart Farming Technology Pitch Deck For Food Security
Revenue Streams Smart Farming Technology Pitch Deck For Food SecurityThis slide represents major sources through which company generate revenue. It includes pointers such as profit sharing and commission. Increase audience engagement and knowledge by dispensing information using Revenue Streams Smart Farming Technology Pitch Deck For Food Security This template helps you present information on Two stages. You can also present information on Profit Sharing, Commission using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Smart Farming Technology Pitch Deck For Food Security
Table Of Contents For Smart Farming Technology Pitch Deck For Food SecurityIntroducing Table Of Contents For Smart Farming Technology Pitch Deck For Food Security to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Company Introduction, Esteemed Clientele using this template. Grab it now to reap its full benefits.
-
 Value Proposition Smart Farming Technology Pitch Deck For Food Security
Value Proposition Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases company value preposition that helps company to gain competitive edge and sustainability in market. It includes pointers such as insurance funding, environmental impact, food security etc. Increase audience engagement and knowledge by dispensing information using Value Proposition Smart Farming Technology Pitch Deck For Food Security This template helps you present information on Four stages. You can also present information on Food Security, Environmental Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why Invest With Us Smart Farming Technology Pitch Deck For Food Security
Why Invest With Us Smart Farming Technology Pitch Deck For Food SecurityFollowing slide highlights major reasons that helps to attract investors for fund raising. It includes pointers such as impact funding, farmer empowerment, environmental friendly etc. Introducing Why Invest With Us Smart Farming Technology Pitch Deck For Food Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Farmer Empowerment, Environmental Friendly using this template. Grab it now to reap its full benefits.
-
 Advantages Of Crypto Technology In Smartphone Security
Advantages Of Crypto Technology In Smartphone SecurityThis slide represents advantages of crypto technologies in smartphone security which offers enhanced security features and secure communication infrastructure. It includes advantages of crypto technology in smartphone security such as tracks privacy, hardware security, etc. Presenting our set of slides with name Advantages Of Crypto Technology In Smartphone Security. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Tracks Privacy, Hardware Security, User Anonymity, Hack Proof.
-
 Best Practices To Overcome Smartphone Technology Security Threats
Best Practices To Overcome Smartphone Technology Security ThreatsThis slide represents best practices to overcome smartphone technology security threats which enhances smartphone security and prevents from malware and spyware attacks. It includes security threats such as downloadable applications threats, physical threats, etc. Presenting our set of slides with name Best Practices To Overcome Smartphone Technology Security Threats. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Downloadable Applications Threats, Network And Wi-Fi Security Threats, General Cyber Security Threats, Physical Threats.
-
 Big Data Security Technology To Enhance Systems Efficiency
Big Data Security Technology To Enhance Systems EfficiencyThis slide represents big data security technology which enhances security of non relational databases and boosts endpoint security. It includes big data security technology to enhance systems efficiency such as encryption, user access control etc. Presenting our set of slides with name Big Data Security Technology To Enhance Systems Efficiency. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Centralized Key Management, Physical Security, User Access Control, Encryption.
-
 Checklist For Holistic Data Security And Privacy In Big Data Technology
Checklist For Holistic Data Security And Privacy In Big Data TechnologyThis slide represents checklist for data security and privacy in big data technology which assists to prevent unauthorized access and provides safeguard against cyber threat. It includes key steps such as secure and monitor, find and classify, etc. Introducing our Checklist For Holistic Data Security And Privacy In Big Data Technology set of slides. The topics discussed in these slides are Find And Classify, Secure And Monitor, Harden, Protect And Remain Vigilant. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Privacy And Security Issues Faced In Big Data Technology
Privacy And Security Issues Faced In Big Data TechnologyThis slide represents privacy and security issues faced in big data technology which provides greater insight into data and assists to make better business decisions. It includes privacy and security issues faced in big data technology such as secure computations, access control, etc. Presenting our set of slides with name Privacy And Security Issues Faced In Big Data Technology. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Computations, Access Control, Protecting Data And Transaction Logs, Real Time Security Monitoring.
-
 Cyber Security Tools For Saas Companies
Cyber Security Tools For Saas CompaniesThis slide represents SaaS cyber security tools and technologies. It aims to provide specialized capabilities for endpoint security of SaaS companies operating. It includes various tools such as authentication and access control, network and endpoint security, etc. Introducing our premium set of slides with Cyber Security Tools For Saas Companies Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication And Access Control, Secure Remote Access Technology, Network And Endpoint Security. So download instantly and tailor it with your information.
-
 Comparative Assessment For Data Security Management Tools
Comparative Assessment For Data Security Management ToolsThis slide represents the comparative analysis assisting businesses to choose correct tools to enhance data security management. It includes various tools such as oracle data safe, satori data security platform, etc. Introducing our Comparative Assessment For Data Security Management Tools set of slides. The topics discussed in these slides are Oracle Data Safe, Data Security Platform, Manager For Databases. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies And Tools To Enhance Big Data Security Management
Strategies And Tools To Enhance Big Data Security ManagementThis slide showcases the strategies and tools helping companies to effectively manage and monitor big data security from cyber threats. It includes strategies such as cloud security monitoring, centralized key management, incident investigation, etc. Introducing our Strategies And Tools To Enhance Big Data Security Management set of slides. The topics discussed in these slides are Cloud Security Monitoring, Centralized Key Management, Network Traffic Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Complete Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
Complete Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS VThis slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Increase audience engagement and knowledge by dispensing information using Complete Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V. This template helps you present information on four stages. You can also present information on Voice Recognition, Facial Recognition, Iris Recognition, Enhancing Online Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improving Security By Green Computing Technology Carbon Free Computing
Improving Security By Green Computing Technology Carbon Free ComputingThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Improving Security By Green Computing Technology Carbon Free Computing. Use it as a tool for discussion and navigation on Green Computing Technology, Computers And Networks, Security Concerns And Solution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ATP Cyber Technology Security Icon
ATP Cyber Technology Security IconPresenting our set of slides with name ATP Cyber Technology Security Icon. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on ATP Cyber Technology, Security Icon.
-
 Comparative Analysis Of ATP Cyber Security Tools
Comparative Analysis Of ATP Cyber Security ToolsThis slide depicts the comparative analysis of ATP cyber security tools. Its aim is to use the tools to protect the system from advanced threats. This slide include Microsoft defender, ESET endpoint, Palo Alto network, Fortinet sandbox. Presenting our set of slides with name Comparative Analysis Of ATP Cyber Security Tools. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Microsoft Defender, ESET Endpoint, Palo Alto Network, Fortinet Sandbox.
-
 Comparative Analysis Of Mobile Security Tools
Comparative Analysis Of Mobile Security ToolsThis slide showcases mobile security software applications comparison matrix and includes anti-theft protection, remote SMS control, call blocking, web protection, and wi-fi protection. Introducing our Comparative Analysis Of Mobile Security Tools set of slides. The topics discussed in these slides are Anti- Theft Protection, Remote Sms Control, Call Blocking, Web Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Gap Measurement Tools Comparative Analysis
Security Gap Measurement Tools Comparative AnalysisThis slide outlines represents security vulnerability performance by comparative analysis tools for choosing the best option. It further covers tools, free trials, prices, reviews, and features such as scanning global and local network ranges, custom extensions, etc. The following. Introducing our Security Gap Measurement Tools Comparative Analysis set of slides. The topics discussed in these slides are Scan Global, Local Network Ranges, Automate Vulnerabilities, Custom Extension. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Role Of 5g Technology In Retail Cyber Security
Icon For Role Of 5g Technology In Retail Cyber SecurityIntroducing our Icon For Role Of 5g Technology In Retail Cyber Security set of slides. The topics discussed in these slides are Icon For Role Of 5G Technology, Retail Cyber Security This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS V
Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS V. This template helps you present information on two stages. You can also present information on Surface Visibility, Internal Networking, Trust Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS V
Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Deliver an outstanding presentation on the topic using this Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS V. Dispense information and present a thorough explanation of Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Challenges In Blockchain Technology For Security Enhancement
Cybersecurity Challenges In Blockchain Technology For Security EnhancementThis slide highlights cybersecurity challenges for working together to enhance security posture of blockchain community by developers and users.It includes issues such as scalability challenges, lack of governance, blockchain literacy, and reliance on private keys. Presenting our set of slides with Cybersecurity Challenges In Blockchain Technology For Security Enhancement This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scalability Challenges, Blockchain Literacy, Lack Of Governance
-
 Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS V
Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS VThis slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Introducing Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Interworking Devices, Wireless Cameras, Protects Data, using this template. Grab it now to reap its full benefits.
-
 Application Security Testing Tool Pyramid Ppt File Background Image
Application Security Testing Tool Pyramid Ppt File Background ImageThis slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Introducing Application Security Testing Tool Pyramid Ppt File Background Image to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Application Security, Testing Tool Pyramid, Test Coverage Analysis, Correlation Tools, using this template. Grab it now to reap its full benefits.
-
 Application Security Testing Tools Reference Model Ppt File Infographics
Application Security Testing Tools Reference Model Ppt File InfographicsThis slide showcases the application security testing tools reference model along with the workflow. Deliver an outstanding presentation on the topic using this Application Security Testing Tools Reference Model Ppt File Infographics. Dispense information and present a thorough explanation of Software Composition Analysis, Static Application Security Testing, Dynamic Application Security Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Tools For Vulnerability Scanning In Security Testing
Application Security Tools For Vulnerability Scanning In Security TestingThis slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Present the topic in a bit more detail with this Application Security Tools For Vulnerability Scanning In Security Testing. Use it as a tool for discussion and navigation on Tools For Vulnerability, Scanning In Security Testing, Application Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
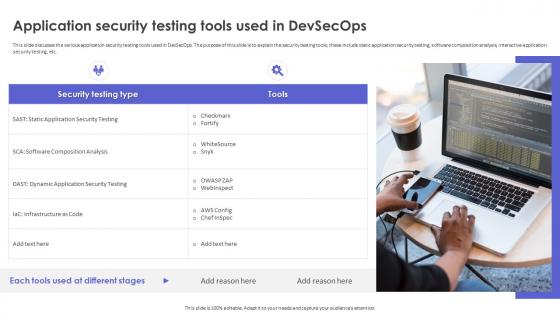 Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps
Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOpsThis slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Increase audience engagement and knowledge by dispensing information using Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps. This template helps you present information on one stages. You can also present information on Application Security Testing, Software Composition Analysis, Interactive Application Security Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Open Source Tools Among Security Testers
Top Open Source Tools Among Security TestersThis slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc. Increase audience engagement and knowledge by dispensing information using Top Open Source Tools Among Security Testers. This template helps you present information on four stages. You can also present information on Proof Based Scanning Technology, AI Enabled Penetration Testing, Flexible And Scalable Scanning using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Icon For Ensuring Security By Containerization Technology
Icon For Ensuring Security By Containerization TechnologyPresenting our well structured Icon For Ensuring Security By Containerization Technology. The topics discussed in this slide are Icon, Ensuring Security, Containerization Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
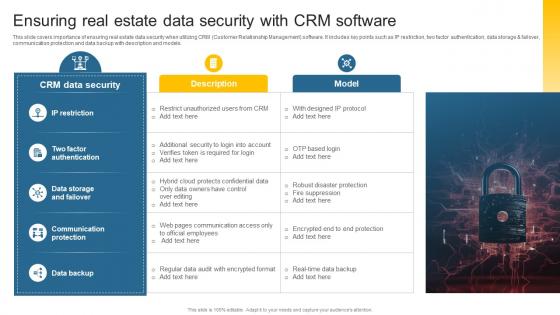 Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company
Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers importance of ensuring real estate data security when utilizing CRM Customer Relationship Management software. It includes key points such as IP restriction, two factor authentication, data storage and failover, communication protection and data backup with description and models. Introducing Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage And Failover, Communication Protection, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Application Security Implementation Plan Comparative Analysis Of Application Security Tools
Application Security Implementation Plan Comparative Analysis Of Application Security ToolsThis slide highlights the comparison of different application security tools and optimal selection of the tool along with the reason of selection. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Comparative Analysis Of Application Security Tools. Dispense information and present a thorough explanation of Comparative Analysis, Application Security Tools, Commercial, License using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Top Endpoint Security Tools And Cost
Endpoint Security Top Endpoint Security Tools And CostThis slide highlights the tools used for endpoint security such as Sophos, Vipre, and CrowdStrike along with their cost and features. Deliver an outstanding presentation on the topic using this Endpoint Security Top Endpoint Security Tools And Cost. Dispense information and present a thorough explanation of Prevents Ransomware, Security Tools And Cost, Crowdstrike using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Analysis Of Data Masking Tools For Information Security
Comparison Analysis Of Data Masking Tools For Information SecurityThis slide represents comparison analysis of data masking tools that assist companies to enhance their sensitive information security. It includes various tools such as K2View data masking, DATPROF data masking tool, Oracle data masking and subsetting, etc. Presenting our well structured Comparison Analysis Of Data Masking Tools For Information Security. The topics discussed in this slide are Virtualization, Synthetic Data Generation, Tokenization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Assessment Of Cyber Security Tools In Automotive Industry
Comparative Assessment Of Cyber Security Tools In Automotive IndustryThis slide highlights comparison of digital security tools in automobile sector. The purpose of this slide is to aid businesses in utilizing reliable software for managing automotive cybersecurity. It includes elements such as intrusion detection, secure boot, etc. Introducing our Comparative Assessment Of Cyber Security Tools In Automotive Industry set of slides. The topics discussed in these slides are Intrusion Detection, Access Control, Network Monitoring This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Role Of 5g Technology In Automotive Cyber Security
Icon For Role Of 5g Technology In Automotive Cyber SecurityIntroducing our premium set of slides with Icon For Role Of 5g Technology In Automotive Cyber Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Role, 5G Technology In Automotive, Cyber Security So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities
Tokenization For Improved Data Security Data Tokenization Tools Key CapabilitiesPresent the topic in a bit more detail with this Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities. Use it as a tool for discussion and navigation on Data Tokenization Tools, Key Capabilities, Operational And Analytical Purposes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology
Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain TechnologyThis slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A plus, S regulations, etc. Introducing Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Regulations Of Security Tokens, Blockchain Technology, Data Security, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Tools To Measure Security Vulnerability Performance
Comparative Analysis Of Tools To Measure Security Vulnerability PerformanceFollowing slide represents security vulnerability performance by comparative analysis tools for choosing best option. It further covers tools, free trials, price, reviews and features such as scan global and local network ranges, custom extension, etc. Introducing our Comparative Analysis Of Tools To Measure Security Vulnerability Performance set of slides. The topics discussed in these slides are Features, Free TrialThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of SIEM Cyber Security Monitoring Tools
Comparative Analysis Of SIEM Cyber Security Monitoring ToolsThis slide showcases the comparative analysis of SIEM cyber security tools. Its objective is to detect threats and log analysis. This slide includes log analysis, LogPoint, ExaBeam infusion, ManageEngine and DataDog security. Presenting our well structured Comparative Analysis Of SIEM Cyber Security Monitoring Tools. The topics discussed in this slide are Datadog Security, Logpoint, Manageengine Log. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Common Blockchain Security Testing Tools
Common Blockchain Security Testing ToolsThis slide gives an overview of commonly used testing tools in blockchain security which include Oyente, Manticore, SmartCheck, Securify 2.0, etc. Introducing our Common Blockchain Security Testing Tools set of slides. The topics discussed in these slides are Static Analysis, Symbolic Execution, Security Scanner. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Common Security Types In Blockchain Technology
Common Security Types In Blockchain TechnologyPresenting our set of slides with Common Security Types In Blockchain Technology. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Public Blockchain, Hybrid Blockchain, Restricted Access.
-
 Cyber Security Attacks In Blockchain Technology
Cyber Security Attacks In Blockchain TechnologyPresenting our set of slides with Cyber Security Attacks In Blockchain Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Interception, Floods Networks, False Identities.
-
 Icon For Blockchain Technology In Cyber Security
Icon For Blockchain Technology In Cyber SecurityPresenting our well structured Icon For Blockchain Technology In Cyber Security. The topics discussed in this slide are Icon, Blockchain Technology, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Structural Design Of Blockchain Technology On Security Threats
Structural Design Of Blockchain Technology On Security ThreatsIntroducing our Structural Design Of Blockchain Technology On Security Threats set of slides. The topics discussed in these slides are Application Layer, Contract Layer, Incentive Layer. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Network Security Open Source Tools
Ai Network Security Open Source ToolsThis slide depicts the top trending open-source artificial interline network security tools KeePass, Open VAS, Zed attack proxy, and VeraCrypt. Introducing our Ai Network Security Open Source Tools set of slides. The topics discussed in these slides are Identifies Security Weaknesses, Proxy Interception, Unique Passwords. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Technology Implementation Icon For Robust OT Cyber Security
Ai Technology Implementation Icon For Robust OT Cyber SecurityPresenting our set of slides with Ai Technology Implementation Icon For Robust OT Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Technology Implementation Icon, Robust OT Cyber Security
-
 A224 Mobile Banking Application Security Testing Tools Fin SS V
A224 Mobile Banking Application Security Testing Tools Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Present the topic in a bit more detail with this A224 Mobile Banking Application Security Testing Tools Fin SS V. Use it as a tool for discussion and navigation on Micro Focus, Global Customer, Codifiedsecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SS
Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SSThis slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non identification of security vulnerabilities, delay response to security threats, etc. Increase audience engagement and knowledge by dispensing information using Ineffective Utilization Of Security Tools By Employees Software Development Training Program DTE SS This template helps you present information on three stages. You can also present information on Security Threats, Security Vulnerabilities, Security Team using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Ecommerce Security Tools
Comparative Analysis Of Ecommerce Security ToolsThis slide shows the software tools matrix in monitoring ecommerce threats in advanced to draft a strategic measures plan to prevent form these attacks. The tools are uptime, ketch, Keep cart, Lubneda,etc Introducing our Comparative Analysis Of Ecommerce Security Tools set of slides. The topics discussed in these slides are Comparative, Analysis, Security Tools. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technology Integration For Security Operations Center
Technology Integration For Security Operations CenterThe below slide provides a technological integration architecture for security operation center that helps to understand the various technology used for threat identification and mitigation. The various technologies are cloud, network sensors, etc. Introducing our premium set of slides with name Technology Integration For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Analysis, SIEM, Intrusion Activity. So download instantly and tailor it with your information.
-
 Technology Trends And Impact Of Security Operations Center
Technology Trends And Impact Of Security Operations CenterThe following slide represents the technological trends of security operations center along with their impact on security. The various trends are rise in adoption of cloud deployment, increased use of AI and ML, etc. Presenting our set of slides with name Technology Trends And Impact Of Security Operations Center. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Impact, MDR Security Assessment.
-
 Tool And Technologies For Security Operations Center
Tool And Technologies For Security Operations CenterThe following slide showcases the various tools that are used in functioning of security operations center for effective monitoring and prevention of threats. The different tools are log collection and management, endpoint detection, etc. Introducing our premium set of slides with name Tool And Technologies For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Log Collection And Management, Endpoint Detection And Response. So download instantly and tailor it with your information.
-
 NIDS Tools Comparison To Ensure Cyber Security
NIDS Tools Comparison To Ensure Cyber SecurityThis Slide Represents NIDS Software Comparative Assessment To Establish Cyber Security. It Aims To Select Right NIDS Tool Depending On Specific Requirements Of Organization. Presenting Our Well Structured NIDS Tools Comparison To Ensure Cyber Security. The Topics Discussed In This Slide Are Cyber Security, Comparison, Organization. This Is An Instantly Available Powerpoint Presentation That Can Be Edited Conveniently. Download It Right Away And Captivate Your Audience.
-
 NFC Technology Risks Associated With Mobile Security Mobile Security
NFC Technology Risks Associated With Mobile Security Mobile SecurityThis slide discusses the NFC technology risks associated with mobile security which includes data tampering, data interception, smartphone malware, etc. Increase audience engagement and knowledge by dispensing information using NFC Technology Risks Associated With Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Installing Patches, Add Features, Systems Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





