Powerpoint Templates and Google slides for Security Timeline
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Firewall Network Security Timeline For Firewall Network Security Evolution
Firewall Network Security Timeline For Firewall Network Security EvolutionThis slide gives an overview of the firewall evolution timeline. The purpose of this slide is to showcase the different stages and enhancements in firewall security over time. It also includes the launch of firewall technology and a list of improvements in the technology from 1989 to 2019. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Timeline For Firewall Network Security Evolution This template helps you present information on Seven stages. You can also present information on Firewall Born, Mainstream Growth, Ngfw Introduction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline for security guard services proposal ppt slides examples
Timeline for security guard services proposal ppt slides examplesIntroducing Timeline For Security Guard Services Proposal Ppt Slides Examples to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Security Guard Services, 2016 To 2020, using this template. Grab it now to reap its full benefits.
-
 Data security it timeline for the implementation of data security
Data security it timeline for the implementation of data securityThis slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Data Security IT Timeline For The Implementation Of Data Security. Use it as a tool for discussion and navigation on Phishing Exercise, Risk Assessments, Security Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security timeline ppt powerpoint presentation slides visuals
Computer system security timeline ppt powerpoint presentation slides visualsIntroducing Computer System Security Timeline Ppt Powerpoint Presentation Slides Visuals to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, 2016 To 2021, using this template. Grab it now to reap its full benefits.
-
 Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SS
Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SSThe following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Present the topic in a bit more detail with this Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Brief Evolution Timeline, Security Token Offerings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
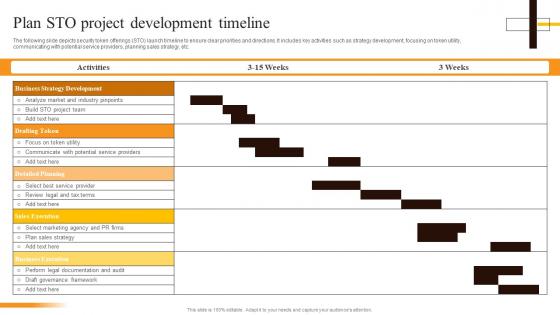 Plan STO Project Development Timeline Security Token Offerings BCT SS
Plan STO Project Development Timeline Security Token Offerings BCT SSThe following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. Present the topic in a bit more detail with this Plan STO Project Development Timeline Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Business Strategy Development, Drafting Token, Detailed Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
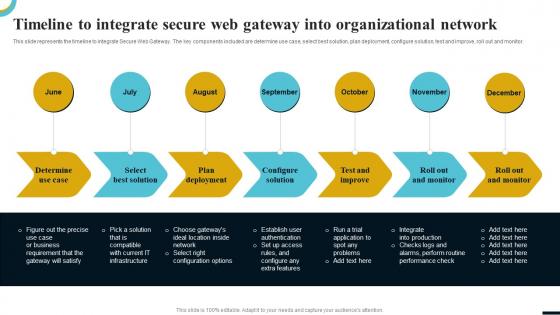
 Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web Gateway
Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Increase audience engagement and knowledge by dispensing information using Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web Gateway. This template helps you present information on seven stages. You can also present information on Organizational, Configure Solution, Determine Use Case using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Awareness Communication Plan Timeline Used By Organization
Security Awareness Communication Plan Timeline Used By OrganizationThis light showcases timeline that assist to evaluate time taken in completing tasks of security awareness communication plan. It contains phases such as assessment, planning etc. along with objective, activities to be conducted and days taken. Presenting our well structured Security Awareness Communication Plan Timeline Used By Organization. The topics discussed in this slide are Security, Communication, Organization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
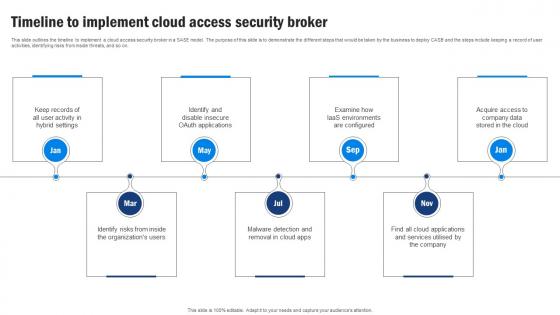
 Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a Cloud Access Security Broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Cloud Applications, Malware Detection And Removal, using this template. Grab it now to reap its full benefits.
-
 Weekly Timeline For Cyber Security Compliance Management
Weekly Timeline For Cyber Security Compliance ManagementThis slide shows framework for security compliance management weekly timeline that helps managing risk. It further includes details such as planning, readiness assessment, services agreement etc. Introducing our Weekly Timeline For Cyber Security Compliance Management set of slides. The topics discussed in these slides are Compliance Period, Remediation Period. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From PhishingThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing. This template helps you present information on five stages. You can also present information on Implement Technical Controls, Employee Training, Establish Policies And Procedures, Timely Evaluation And Updates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.
-
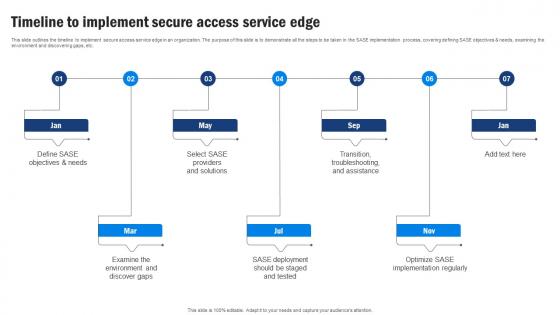
 Timeline To Implement Secure Access Service Edge Cloud Security Model
Timeline To Implement Secure Access Service Edge Cloud Security ModelThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Solutions, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Timeline To Implement Cloud Access Security Broker
Sase Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Security Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Timeline, Applications, Environments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Timeline To Implement Secure Access Service Edge
Sase Security Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Security Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Troubleshooting, using this template. Grab it now to reap its full benefits.
-
 Timeline To Cloud Access Security Broker Secure Access Service Edge Sase
Timeline To Cloud Access Security Broker Secure Access Service Edge SaseThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Cloud Access Security Broker Secure Access Service Edge Sase. This template helps you present information on seven stages. You can also present information on Timeline, Implement, Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase
Timeline To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Environment, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management
Cyber Security Plan Implementation Timeline Improving Cyber Security Risks ManagementThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Perform Simulated, Phishing Exercise, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge SASE Network Security
Timeline To Implement Secure Access Service Edge SASE Network SecurityThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge SASE Network Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Solutions, Regularly, using this template. Grab it now to reap its full benefits.
-
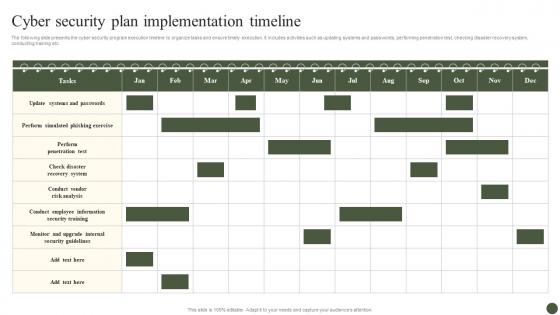 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
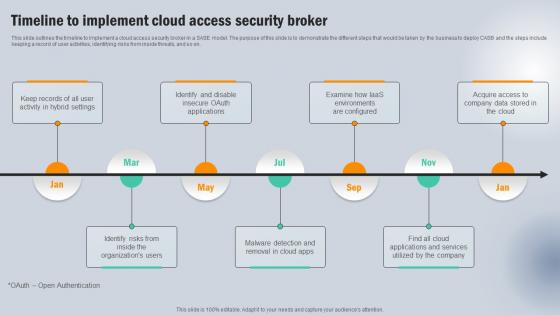 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
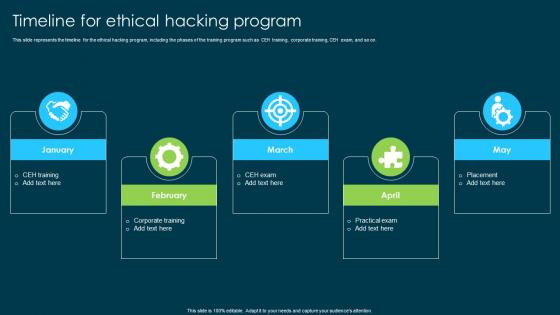 Ethical Hacking And Network Security Timeline For Ethical Hacking Program
Ethical Hacking And Network Security Timeline For Ethical Hacking ProgramThis slide represents the timeline for the ethical hacking program, including the phases of the training program such as CEH training, corporate training, CEH exam, and so on. Introducing Ethical Hacking And Network Security Timeline For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking Program, Training Program, Corporate Training, Placement, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization
Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In OrganizationThis slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization. This template helps you present information on five stages. You can also present information on Timeline To Implement Devsecops, Regularly Reviewing, Updating Security Tools, Sharing Basic Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Secure Access Service Edge
Sase Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Jan, Mar, May, Jul, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness
Cyber Security Plan Implementation Timeline Creating Cyber Security AwarenessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Malware Attacks, Breaches To Company, More Challenging This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Timeline To Integrate Secure Web Gateway
Internet Gateway Security IT Timeline To Integrate Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Timeline To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, using this template. Grab it now to reap its full benefits.
-
 Server Security Maintenance Timeline For Preventing Unauthorized Access
Server Security Maintenance Timeline For Preventing Unauthorized AccessFollowing slide highlights timeline for server security maintenance by preventing unauthorized access, also including tasks such as installation of new package, updates of other applications, review server accessibility, etc. Presenting our well structured Server Security Maintenance Timeline For Preventing Unauthorized Access. The topics discussed in this slide are Review Server Accessibility, Firewall Rules, User Password Change. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats
Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Update Systems And Passwords, Perform Simulated Phishing Exercise, Perform Penetration Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Cloud Access Security Broker CASB Cloud Security
Timeline To Implement Cloud Access Security Broker CASB Cloud SecurityThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker CASB Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Malware Detection, Identify Risks, using this template. Grab it now to reap its full benefits.
-
 Timeline Representing Strategic Retirement Planning To Build Secure Future Fin SS
Timeline Representing Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows roadmap which contains detailed information about history and evolution of retirement planning over time. It includes details such as first private pension plan introduction, establishment of social security system, etc. Increase audience engagement and knowledge by dispensing information using Timeline Representing Strategic Retirement Planning To Build Secure Future Fin SS. This template helps you present information on nine stages. You can also present information on Pension Plan, Contribution Plans, Older Workers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Brief Evolution Timeline Beginners Guide To Successfully Launch Security Token BCT SS V
Brief Evolution Timeline Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Increase audience engagement and knowledge by dispensing information using Brief Evolution Timeline Beginners Guide To Successfully Launch Security Token BCT SS V. This template helps you present information on three stages. You can also present information on Brief Evolution Timeline, Security Token Offerings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline For Implementing Efficient Application Security
Timeline For Implementing Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Introducing Timeline For Implementing Efficient Application Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Patch Management, Incident Response Planning, Planning Phase, Education And Training, using this template. Grab it now to reap its full benefits.
-
 IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SS
IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SSThis slide showcases software development lifecycle SDLC in IoT security , referable for developers in software programming of connected devices. It provides details about training, requirements, implementation, verification, etc. Present the topic in a bit more detail with this IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Training, Requirements And Design, Verification, Release And Respond. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Timeline For Deploying Efficient Application Security
Application Security Implementation Plan Timeline For Deploying Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Timeline For Deploying Efficient Application Security. This template helps you present information on six stages. You can also present information on Education And Training, Patch Management, Incident Response Planning, Establish Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Timeline For Implementing Efficient Endpoint Security
Endpoint Security Timeline For Implementing Efficient Endpoint SecurityThis slide outlines the different steps performed while deploying endpoint security, including planning phase, solution selection, etc. Introducing Endpoint Security Timeline For Implementing Efficient Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Testing And Optimization, Solution Selection, Deployment, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security
Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data SecurityThis slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security. This template helps you present information on six stages. You can also present information on Tokenization Key Management, Monitoring And Auditing, Tokenization Methods, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
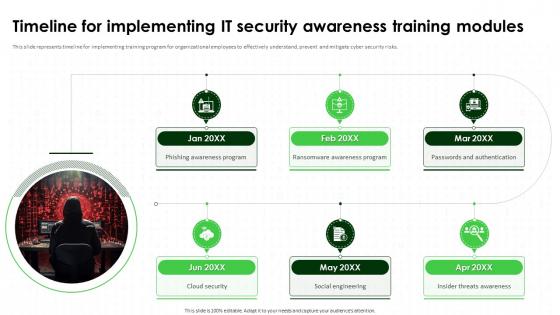 Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS
Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SSThis slide represents timeline for implementing training program for organizational employees to effectively understand, prevent and mitigate cyber security risks. Increase audience engagement and knowledge by dispensing information using Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS. This template helps you present information on six stages. You can also present information on Ransomware Awareness Program, Passwords And Authentication, Social Engineering, Insider Threats Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Security Upgradation Timeline For Web Security Deployment In Business
Web Security Upgradation Timeline For Web Security Deployment In BusinessThis slide outlines the timeline for implementing web security in an organization which include assessment, planning, etc. Introducing Web Security Upgradation Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Timeline For Email Security Measures Implementation
Email Security Best Practices Timeline For Email Security Measures ImplementationThis slide shows the timeline for applying email security policies in organization. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Timeline For Email Security Measures Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Crisis Management Timeline
Cyber Security Crisis Management TimelineThe purpose of this slide is to highlight how a cybersecurity crisis management timeline aids in orchestrating swift and sequential responses, mitigating cyber threats effectively, and minimizing potential damages to the organization. Presenting our set of slides with name Cyber Security Crisis Management Timeline. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Communication, Recover Learn.
-
 Timeline For Web Security Deployment In Business
Timeline For Web Security Deployment In BusinessThis slide outlines the different steps performed while deploying web security, including assessment, planning, and so on. Introducing Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Timeline For Endpoint Security Upgradation Proposal
Timeline For Endpoint Security Upgradation ProposalThis slide shows the time framework for upgrading the endpoint security proposal the steps include identifying requirements, developing architecture design, etc. Introducing Timeline For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Requirements Analysis, Developing Architecture Design, Creating Budget, Deployment, using this template. Grab it now to reap its full benefits.
-
 Brief Evolution Timeline Of Security Token Offerings Ultimate Guide Smart BCT SS V
Brief Evolution Timeline Of Security Token Offerings Ultimate Guide Smart BCT SS VThe following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Introducing Brief Evolution Timeline Of Security Token Offerings Ultimate Guide Smart BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Second Tokenized, REIT Sale, Advent New Security, using this template. Grab it now to reap its full benefits.
-
 Timeline for the implementation of electronic information security
Timeline for the implementation of electronic information securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Electronic Information Security. Dispense information and present a thorough explanation of Conduct Simulated Phishing Exercise, Change System, Network Passwords, Perform Third Party Vendor Risk Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it timeline for implementation of cyber security in the company
Cyberterrorism it timeline for implementation of cyber security in the companyThis slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Present the topic in a bit more detail with this Cyberterrorism IT Timeline For Implementation Of Cyber Security In The Company. Use it as a tool for discussion and navigation on Changes System, Network Passwords, Penetration Test. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Timeline For The Implementation Of Information Security
Information Security Timeline For The Implementation Of Information SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Information Security Timeline For The Implementation Of Information Security. Dispense information and present a thorough explanation of Timeline, Implementation, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Timeline For The Implementation Of Network Security
Network Security Timeline For The Implementation Of Network SecurityThis slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Network Security Timeline For The Implementation Of Network Security. Use it as a tool for discussion and navigation on Timeline For The Implementation Of Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For The Implementation Of Information Technology Security
Timeline For The Implementation Of Information Technology SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Information Technology Security. Dispense information and present a thorough explanation of Implementation, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Company Timeline From 1992 To 2022 Manpower Security Services Company Profile
Company Timeline From 1992 To 2022 Manpower Security Services Company ProfileThis slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Increase audience engagement and knowledge by dispensing information using Company Timeline From 1992 To 2022 Manpower Security Services Company Profile. This template helps you present information on eight stages. You can also present information on Timeline, Services, Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Company Timeline From 1992 To 2022 Security Guard Service Company Profile
Company Timeline From 1992 To 2022 Security Guard Service Company ProfileThis slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Increase audience engagement and knowledge by dispensing information using Company Timeline From 1992 To 2022 Security Guard Service Company Profile. This template helps you present information on nine stages. You can also present information on 1992 To 2022, Expand Services, Security Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Company Timeline From 1992 To 2022 Security Services Business Profile Ppt Formats
Company Timeline From 1992 To 2022 Security Services Business Profile Ppt FormatsThis slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Introducing Company Timeline From 1992 To 2022 Security Services Business Profile Ppt Formats to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Company Timeline, Security Services, using this template. Grab it now to reap its full benefits.




