Powerpoint Templates and Google slides for Security Technology
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber security technology skills gap priorities
Cyber security technology skills gap prioritiesThis slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Introducing our Cyber Security Technology Skills Gap Priorities set of slides. The topics discussed in these slides are Cyber Security Technology Skills Gap Priorities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Technology assessment scorecard with device security ppt slides deck
Technology assessment scorecard with device security ppt slides deckThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an outstanding presentation on the topic using this Technology Assessment Scorecard With Device Security Ppt Slides Deck. Dispense information and present a thorough explanation of Compromised, Not Encrypted, Mention Security Feature, Last Seen Overview, Ownership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technology assessment scorecard with security incidents ppt slides graphics
Technology assessment scorecard with security incidents ppt slides graphicsThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Present the topic in a bit more detail with this Technology Assessment Scorecard With Security Incidents Ppt Slides Graphics. Use it as a tool for discussion and navigation on Criminal Activity, Investigation, Denial Service, Data Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
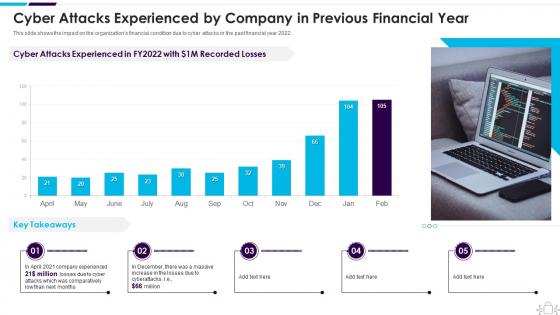 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Compliance Dashboard Snapshot For Information Technology Security
Information Technology Security Compliance Dashboard Snapshot For Information Technology SecurityThis slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Present the topic in a bit more detail with this Information Technology Security Compliance Dashboard Snapshot For Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Dashboard Snapshot Threat Tracking Information Technology Security
Information Technology Security Dashboard Snapshot Threat Tracking Information Technology SecurityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Information Technology Security Dashboard Threat Tracking Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Detail Impact Information Technology Reduce Organization
Information Technology Security Detail Impact Information Technology Reduce OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Present the topic in a bit more detail with this Information Technology Security Detail Impact Information Technology Reduce Organization. Use it as a tool for discussion and navigation on Information, Technology, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Highest Number Of Malware Attacks In Departments
Information Technology Security Highest Number Of Malware Attacks In DepartmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Present the topic in a bit more detail with this Information Technology Security Highest Number Of Malware Attacks In Departments. Use it as a tool for discussion and navigation on Department, Experienced, Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Problems Faced By The Organization
Information Technology Security Problems Faced By The OrganizationThis slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Present the topic in a bit more detail with this Information Technology Security Problems Faced By The Organization. Use it as a tool for discussion and navigation on Problems Faced By The Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Requirement Of Information Technology Security In Different Sectors
Information Technology Security Requirement Of Information Technology Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Technology Security Requirement Of Information Technology Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Update And Installation Of Antivirus Software
Information Technology Security Update And Installation Of Antivirus SoftwareThis slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an outstanding presentation on the topic using this Information Technology Security Update And Installation Of Antivirus Software. Dispense information and present a thorough explanation of Update And Installation Of Antivirus Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quarterly Comparison Of Information Technology Security Threats
Quarterly Comparison Of Information Technology Security ThreatsThis slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Introducing our Quarterly Comparison Of Information Technology Security Threats set of slides. The topics discussed in these slides are Quarterly Comparison, Information Technology, Security Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing
F652 Security Automation In Information Technology Security Automation Dashboard Highlighting PhishingThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing. Use it as a tool for discussion and navigation on Automation, Dashboard, Phishing Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology
Security Automation Dashboard Highlighting Resolved Events Security Automation In Information TechnologyThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an outstanding presentation on the topic using this Security Automation Dashboard Highlighting Resolved Events Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Dashboard, Workload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Current State Of Security Automation With Projected Development
Security Automation In Information Technology Current State Of Security Automation With Projected DevelopmentThis slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Current State Of Security Automation With Projected Development. Dispense information and present a thorough explanation of Projected Development, Security Automation, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Security Technology User Market
IT Security Technology User MarketThe following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Introducing our IT Security Technology User Market set of slides. The topics discussed in these slides are IT Security Technology, User Market. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Technology Generating Security Awareness Among Employees To Reduce
Information Technology Generating Security Awareness Among Employees To ReduceThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Present the topic in a bit more detail with this Information Technology Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Cyber Security, Budget Spent This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security processing technologies ppt powerpoint presentation model graphics download cpb
Security processing technologies ppt powerpoint presentation model graphics download cpbPresenting this set of slides with name - Security Processing Technologies Ppt Powerpoint Presentation Model Graphics Download Cpb. This is an editable three stages graphic that deals with topics like Security Processing Technologies to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Tools network security ppt powerpoint presentation icon background designs cpb
Tools network security ppt powerpoint presentation icon background designs cpbPresenting our Tools Network Security Ppt Powerpoint Presentation Icon Background Designs Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Tools Network Security . This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Electronic information security of employees devices
Electronic information security of employees devicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Introducing Electronic Information Security Of Employees Devices to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Peripheral Devices, Supervision And Prevent, Project, Data, using this template. Grab it now to reap its full benefits.
-
 Website security testing tools online ppt powerpoint presentation model diagrams cpb
Website security testing tools online ppt powerpoint presentation model diagrams cpbPresenting Website Security Testing Tools Online Ppt Powerpoint Presentation Model Diagrams Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Website Security Testing Tools Online. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Endpoint security tools ppt powerpoint presentation gallery maker cpb
Endpoint security tools ppt powerpoint presentation gallery maker cpbPresenting Endpoint Security Tools Ppt Powerpoint Presentation Gallery Maker Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Endpoint Security Tools. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 Technological assessment of managing critical threat vulnerabilities and security threats
Technological assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Technological Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Industry Standard, Firms Standard, Customer Satisfaction Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technological assessment of firm current management corporate security management
Technological assessment of firm current management corporate security managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Management Corporate Security Management. Dispense information and present a thorough explanation of Incidents Handling Rate, Client Onboarding, Service Failure Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security
Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security.Increase audience engagement and knowledge by dispensing information using Risk Based Methodology To Cyber Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security security This template helps you present information on one stage. You can also present information on Artificial Intelligence, Human Machine Interface, Internet Of Things using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile security apps ppt powerpoint presentation layouts microsoft cpb
Mobile security apps ppt powerpoint presentation layouts microsoft cpbPresenting Mobile Security Apps Ppt Powerpoint Presentation Layouts Microsoft Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Mobile Security Apps. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Service network security tools ppt powerpoint presentation ideas cpb
Service network security tools ppt powerpoint presentation ideas cpbPresenting Service Network Security Tools Ppt Powerpoint Presentation Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Service Network Security Tools. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 F58 Reverse Proxy It Reverse Proxy Server Side Technology Security
F58 Reverse Proxy It Reverse Proxy Server Side Technology SecurityThis slide explains the reverse proxy server side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. Deliver an outstanding presentation on the topic using this F58 Reverse Proxy It Reverse Proxy Server Side Technology Security. Dispense information and present a thorough explanation of Security Proxy, Technology, Transmitted Securely using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Drivers And Emerging Technologies Impact On Cyber Security
Threat Drivers And Emerging Technologies Impact On Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Increase audience engagement and knowledge by dispensing information using Threat Drivers And Emerging Technologies Impact On Cyber Security. This template helps you present information on four stages. You can also present information on Infrastructure, Artificial Intelligence, Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
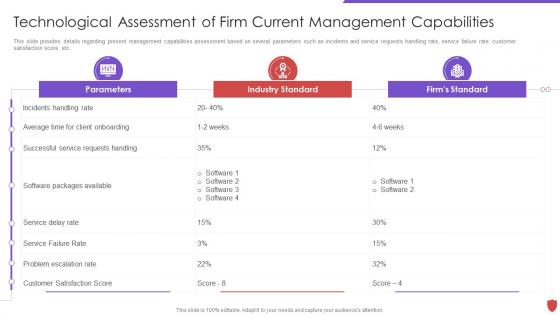 Technological assessment of firm current capabilities cyber security risk management
Technological assessment of firm current capabilities cyber security risk managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Capabilities Cyber Security Risk Management. Dispense information and present a thorough explanation of Parameters, Industry Standard, Firms Standard, Service Delay Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5 Operational Technology Security Controls To Improve It Security
5 Operational Technology Security Controls To Improve It SecurityFollowing slide depict operational technology OT security controls ways that can be used by an organization. Organization can enhance the security of IT infrastructure by using security controls such as update asset inventory, training, managing portable media, backup and restore and implementing secure configuration. Present the topic in a bit more detail with this 5 Operational Technology Security Controls To Improve IT Security. Use it as a tool for discussion and navigation on Update Asset Inventory, Training Manage, Portable Media, Backup And Restore, Secure Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Selecting Operational Technology Security Vendor
Checklist For Selecting Operational Technology Security VendorFollowing slide shows a comprehensive operational technology OT checklist which can be used by an organization for selecting the security vendor. organization can select the best security vendor for improving OT security system after considering points such as vendor understanding regard to OT and IT risk assessment etc. Deliver an outstanding presentation on the topic using this Checklist For Selecting Operational Technology Security Vendor. Dispense information and present a thorough explanation of Checklist, Vendor Understand OT, IT Risk Assessment, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Operational Technology Security Vendors
Comparative Assessment Of Operational Technology Security VendorsMentioned slide showcase various vendors who offers operational technology OT security solutions to business organizations. Organization can choose the best among security vendors by making comparison on the basis of features, deployment, operating systems, price and ratings. Present the topic in a bit more detail with this Comparative Assessment Of Operational Technology Security Vendors. Use it as a tool for discussion and navigation on Types Vendors, Key Features, Deployment, Operating Systems, Pricing In USD, Ratings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Operational Technology Security
Icon For Operational Technology SecurityIntroducing Icon For Operational Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Icon For Operational Technology Security, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Icon For Security Threat Detection
Operational Technology Icon For Security Threat DetectionIntroducing Operational Technology Icon For Security Threat Detection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Operational Technology Icon For Security Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Security Challenges And Solutions To Overcome
Operational Technology Security Challenges And Solutions To OvercomeMentioned slide illustrates various operational technology OT security challenges. It also cover information about the multiple solutions which will assist organization to overcome challenges and build a strong security IT system. Introducing Operational Technology Security Challenges And Solutions To Overcome to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Challenges, Solutions, Employees, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Security Services Offered By Vendors
Operational Technology Security Services Offered By VendorsMentioned slide illustrates operational technology OT services offered by vendors to business organizations. Information covered in this slide is related to services such as network operations, fabric connections, multi-cloud security, application security etc. Increase audience engagement and knowledge by dispensing information using Operational Technology Security Services Offered By Vendors. This template helps you present information on eight stages. You can also present information on Network Operations, Multi Cloud Security, Application Security, Fabric Connections, Information Security, Secure Access, Endpoint Protection, Fabric API using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Information Technology Security
Agenda For Information Technology SecurityIntroducing Agenda For Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 Elements Of Information Technology Security Application Security Information Technology Security
Elements Of Information Technology Security Application Security Information Technology SecurityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Increase audience engagement and knowledge by dispensing information using Elements Of Information Technology Security Application Security Information Technology Security. This template helps you present information on five stages. You can also present information on Session Management, Parameter Tampering, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Information Technology Security
Icons Slide For Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementation Of Strong Password Policy Information Technology Security
Implementation Of Strong Password Policy Information Technology SecurityThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Implementation Of Strong Password Policy Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Americans, Implementation, Passwords, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security 60 Days Plan
Information Technology Security 60 Days PlanThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Information Technology Security 60 Days Plan. Use it as a tool for discussion and navigation on Managing, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Awareness Training Budget For Fy2022
Information Technology Security Awareness Training Budget For Fy2022This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Present the topic in a bit more detail with this Information Technology Security Awareness Training Budget For Fy2022. Use it as a tool for discussion and navigation on Employee Awareness Training Budget For FY2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
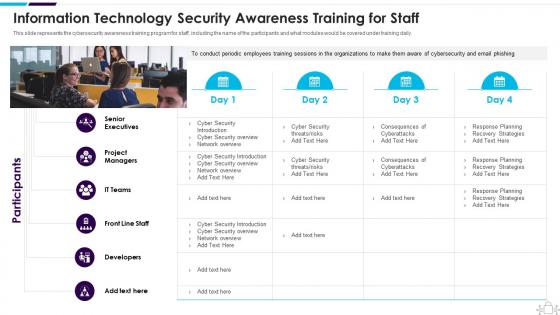 Information Technology Security Awareness Training For Staff
Information Technology Security Awareness Training For StaffThis slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an outstanding presentation on the topic using this Information Technology Security Awareness Training For Staff. Dispense information and present a thorough explanation of Senior Executives, Project Managers, Developers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Best Practices For Cloud Security
Information Technology Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Technology Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Operations, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Common Methods Used Threaten Information Security
Information Technology Security Common Methods Used Threaten Information SecurityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Introducing Information Technology Security Common Methods Used Threaten Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Daniel Of Service, Man In The Middle, SQL Injection , using this template. Grab it now to reap its full benefits.
-
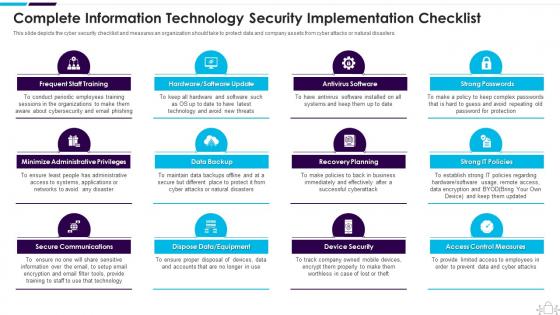 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Data Backup For Sensitive Information
Information Technology Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Information Technology Security Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Dispose Data And Equipment Properly
Information Technology Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Information Technology Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Elements Information Technology Security Cloud Security
Information Technology Security Elements Information Technology Security Cloud SecurityThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Introducing Information Technology Security Elements Information Technology Security Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Employees Devices
Information Technology Security Employees DevicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Increase audience engagement and knowledge by dispensing information using Information Technology Security Employees Devices. This template helps you present information on four stages. You can also present information on Security Of Employees Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





