Powerpoint Templates and Google slides for Security Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance Assessment
F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance AssessmentThis slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. Increase audience engagement and knowledge by dispensing information using F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance Assessment. This template helps you present information on four stages. You can also present information on Technology, Surveillance, Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Hacker 30 60 90 Days Plan For New Strategies Implementation Ppt Information
Security Hacker 30 60 90 Days Plan For New Strategies Implementation Ppt InformationThis slide represents the 30 60 90 days plan to implement new strategies in the company, including the tasks performed in each month interval. Increase audience engagement and knowledge by dispensing information using Security Hacker 30 60 90 Days Plan For New Strategies Implementation Ppt Information. This template helps you present information on three stages. You can also present information on 30 Days, 60 Days, 90 Days using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration
Security Hacker Roadmap To Implement New Security Strategies Ppt InspirationThis slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. Introducing Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Consultants, Tracking And Monitoring, Cyber Security Awareness Session, using this template. Grab it now to reap its full benefits.
-
 Strategies We Will Implement To Make Building A Security Awareness Program
Strategies We Will Implement To Make Building A Security Awareness ProgramThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Building A Security Awareness Program. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Strategy Roadmap Icon With Lock Symbol
Cyber Security Strategy Roadmap Icon With Lock SymbolPresenting our set of slides with name Cyber Security Strategy Roadmap Icon With Lock Symbol. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Strategy Roadmap Icon With Lock Symbol.
-
 Business Development Strategy Smart Security Systems Company Profile Ppt Show Example Topics
Business Development Strategy Smart Security Systems Company Profile Ppt Show Example TopicsThis slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings. Increase audience engagement and knowledge by dispensing information using Business Development Strategy Smart Security Systems Company Profile Ppt Show Example Topics. This template helps you present information on three stages. You can also present information on Multifamily, Professional Channels, Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Existing Channel Development Strategy Smart Security Systems Company Profile Ppt Show Graphics Pictures
Existing Channel Development Strategy Smart Security Systems Company Profile Ppt Show Graphics PicturesThis slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Present the topic in a bit more detail with this Existing Channel Development Strategy Smart Security Systems Company Profile Ppt Show Graphics Pictures. Use it as a tool for discussion and navigation on Development, Strategy, Sources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Company Strategic Partnerships Smart Security Systems Company Profile
Security Company Strategic Partnerships Smart Security Systems Company ProfileThis slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Present the topic in a bit more detail with this Security Company Strategic Partnerships Smart Security Systems Company Profile. Use it as a tool for discussion and navigation on Strategic, Partnerships, Installation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Overcome Cyber Security Manpower Shortage To Address Demand And Supply Gaps
Strategies To Overcome Cyber Security Manpower Shortage To Address Demand And Supply GapsThis slide covers different techniques to overcome cyber workforce shortage. It includes expanding talent pool, identifying existing talent, re-train staff and introduce innovations to reduce demand. Presenting our set of slides with Strategies To Overcome Cyber Security Manpower Shortage To Address Demand And Supply Gaps. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Expand Talent Pool, Identify Existing Talent, Introduce Innovations.
-
 Mobile Device Security Strategy In Powerpoint And Google Slides Cpb
Mobile Device Security Strategy In Powerpoint And Google Slides CpbPresenting Mobile Device Security Strategy In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Mobile Device Security Strategy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Business Development Strategy Security Alarm And Monitoring Systems Company Profile
Business Development Strategy Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings. Increase audience engagement and knowledge by dispensing information using Business Development Strategy Security Alarm And Monitoring Systems Company Profile. This template helps you present information on three stages. You can also present information on Business, Development, Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Existing Channel Development Strategy Security Alarm And Monitoring Systems Company Profile
Existing Channel Development Strategy Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Present the topic in a bit more detail with this Existing Channel Development Strategy Security Alarm And Monitoring Systems Company Profile. Use it as a tool for discussion and navigation on Development, Strategy, Marketing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Company Strategic Partnerships Security Alarm And Monitoring Systems Company Profile
Security Company Strategic Partnerships Security Alarm And Monitoring Systems Company ProfileThis slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Present the topic in a bit more detail with this Security Company Strategic Partnerships Security Alarm And Monitoring Systems Company Profile. Use it as a tool for discussion and navigation on Strategic, Partnerships, Installation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Data Analytics And Cyber Security Strategy Framework
Building Data Analytics And Cyber Security Strategy FrameworkThis slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Introducing our premium set of slides with Building Data Analytics And Cyber Security Strategy Framework. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Collection, Data Normalization, Expansion. So download instantly and tailor it with your information.
-
 Managed Security Service Strategies For Effective Content Management
Managed Security Service Strategies For Effective Content ManagementPresenting our set of slides with Managed Security Service Strategies For Effective Content Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Clean Up Plugins, Scan CMS Platform, Use Latest Version, Strategies.
-
 Various Cyber Security Threats And Strategies To Manage Network Service
Various Cyber Security Threats And Strategies To Manage Network ServiceThis slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Introducing our premium set of slides with Various Cyber Security Threats And Strategies To Manage Network Service. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategies Overcome Threats, IT Security Services, Provide Security Awareness. So download instantly and tailor it with your information.
-
 Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy
Implementation Add Roles And Enable Security Customer Relationship Management Deployment StrategyThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an outstanding presentation on the topic using this Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy Dispense information and present a thorough explanation of Restrictions Enabling, Double Authentication, Prevent Unauthorized using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With CRM Customer Relationship Management Deployment Strategy
Securing Our Data With CRM Customer Relationship Management Deployment StrategyThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.Increase audience engagement and knowledge by dispensing information using Securing Our Data With CRM Customer Relationship Management Deployment Strategy This template helps you present information on three stages. You can also present information on Factor Authentication, Storage And Failover, Communication Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through Iot
Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through IotThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an outstanding presentation on the topic using this Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through Iot. Dispense information and present a thorough explanation of Applications, Bandwidth Access Limitation, Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing Infrastructure
Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing InfrastructureMentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security. Introducing Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing Infrastructure to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Services, Internal Security, Security Design, using this template. Grab it now to reap its full benefits.
-
 Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides
Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google SlidesThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For CPS Cyber Physical Systems In Powerpoint And Google Slides. Dispense information and present a thorough explanation of Gap Analysis, Prioritization, Environmental Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google Slides
Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google SlidesThis slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Present the topic in a bit more detail with this Steps For CPS Security Strategy Plan Cyber Physical Systems In Powerpoint And Google Slides. Use it as a tool for discussion and navigation on Continuous Monitoring, Gap Analysis, Communicate Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threat Mitigation Strategies
Cyber Security Threat Mitigation StrategiesThe following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting our set of slides with name Cyber Security Threat Mitigation Strategies. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Assessment, Patch Management, Traffic Monitoring.
-
 Cyber Security Transformation Strategy With Implementation
Cyber Security Transformation Strategy With ImplementationThe following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Introducing our premium set of slides with name Cyber Security Transformation Strategy With Implementation. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implementation, Mobilization, Vision, Analysis. So download instantly and tailor it with your information.
-
 Business Development Strategy Wireless Home Security Systems Company Profile
Business Development Strategy Wireless Home Security Systems Company ProfileThis slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings. Increase audience engagement and knowledge by dispensing information using Business Development Strategy Wireless Home Security Systems Company Profile. This template helps you present information on three stages. You can also present information on Retail, Multifamily, Professional Channels using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Existing Channel Development Strategy Wireless Home Security Systems Company Profile
Existing Channel Development Strategy Wireless Home Security Systems Company ProfileThis slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Introducing Existing Channel Development Strategy Wireless Home Security Systems Company Profile to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispense information on Direct To Home Strategy, Inside Sales Strategy, using this template. Grab it now to reap its full benefits.
-
 Security Company Strategic Partnerships Wireless Home Security Systems Company Profile
Security Company Strategic Partnerships Wireless Home Security Systems Company ProfileThis slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Increase audience engagement and knowledge by dispensing information using Security Company Strategic Partnerships Wireless Home Security Systems Company Profile. This template helps you present information on four stages. You can also present information on Services, Company, Partnership using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Security Strategic Planning Process For Cps Intelligent System
Security Strategic Planning Process For Cps Intelligent SystemThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an outstanding presentation on the topic using this Security Strategic Planning Process For Cps Intelligent System. Dispense information and present a thorough explanation of Strategic, Planning, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For Cps Security Strategy Plan Intelligent System
Steps For Cps Security Strategy Plan Intelligent SystemThis slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver an outstanding presentation on the topic using this Steps For Cps Security Strategy Plan Intelligent System. Dispense information and present a thorough explanation of Analysis, Communicate, Implementation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business
Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping BusinessThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business. Use it as a tool for discussion and navigation on Strategy, Authentication, Appropriate Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 5 Steps To Develop Workplace Security Strategy
5 Steps To Develop Workplace Security StrategyThis slide shows multi steps process to draft security strategy for office premises. These stages are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Presenting our set of slides with 5 Steps To Develop Workplace Security Strategy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assess Vulnerabilities, Adopt Safety Measures, Alert Authorities.
-
 Strategies To Improve Business Security Operations
Strategies To Improve Business Security OperationsThis slide shows various strategies which can be used by organizations to enhance business operations security. These strategies are detect endpoint threats, leverage advanced analytics and automate incident response. Presenting our set of slides with Strategies To Improve Business Security Operations. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response.
-
 IT Security Risk Mitigation Strategies Icon
IT Security Risk Mitigation Strategies IconPresenting our well-structured IT Security Risk Mitigation Strategies Icon. The topics discussed in this slide are IT Security, Risk Mitigation Strategies, Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Security Threat Mitigation Strategies
IT Security Threat Mitigation StrategiesThe slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring Introducing our premium set of slides with IT Security Threat Mitigation Strategies. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Network Access Controls, Incident Response Plan, Regular Network Traffic Monitoring. So download instantly and tailor it with your information.
-
 6 Step Action Plan To Develop Effective Cyber Security Strategy
6 Step Action Plan To Develop Effective Cyber Security StrategyThis slide signifies the six stage implementation plan to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor. Presenting our set of slides with name 6 Step Action Plan To Develop Effective Cyber Security Strategy. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Monitor, Evaluate, Priorities, Treat.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Financial Burden To Company From It Security Breaches
IT Risk Management Strategies Financial Burden To Company From It Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present the topic in a bit more detail with this IT Risk Management Strategies Financial Burden To Company From It Security Breaches. Use it as a tool for discussion and navigation on Professional Services, Lost Business Opportunities, Total Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions
IT Risk Management Strategies IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions. Dispense information and present a thorough explanation of Control Topic, Evaluation Question, Response Action, Threat using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
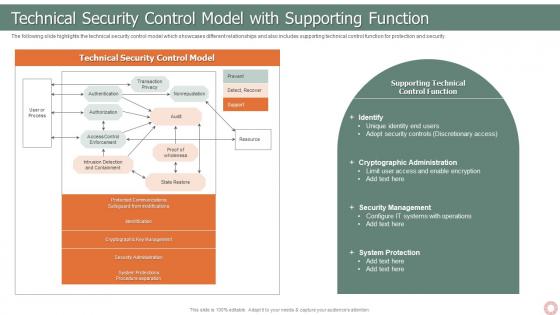 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Security Risk Mitigation Plan With Strategies
Security Risk Mitigation Plan With StrategiesThis slide focuses on the security risk mitigation plan which covers security components, vulnerabilities and mitigation strategies such as administrative, physical, technical and organizational safeguards with conducting workforce training, installing alarm systems, etc. Deliver an outstanding presentation on the topic using this Security Risk Mitigation Plan With Strategies. Dispense information and present a thorough explanation of Security Component, Examples Of Vulnerabilities, Security Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Role Of Management In Security Governance Across Firm Revamping Corporate Strategy
Role Of Management In Security Governance Across Firm Revamping Corporate StrategyThis slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Deliver an outstanding presentation on the topic using this Role Of Management In Security Governance Across Firm Revamping Corporate Strategy. Dispense information and present a thorough explanation of Risk Management, Value Delivery, Integration, Managing Resource using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security Awareness
Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security AwarenessThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Introducing Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, Variety, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Avoid Information Breach Information Security Risk Management
Mitigation Strategies To Avoid Information Breach Information Security Risk ManagementThis slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Introducing Mitigation Strategies To Avoid Information Breach Information Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Implement Antivirus Software, Monitor Network Traffic, Incident Response Plan, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management
Mitigation Strategies To Tackle Information Security Threats Information Security Risk ManagementThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management. This template helps you present information on five stages. You can also present information on Mitigation Strategies, Tackle Information, Security Threats using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Essential Strategies For Security Incident Management
Essential Strategies For Security Incident ManagementPresenting our set of slides with Essential Strategies For Security Incident Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employ Centralized Monitoring, Deploying Right Tools, Upgrading Monitoring Systems.
-
 Key Strategies For Data Security And Privacy
Key Strategies For Data Security And PrivacyThe following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Introducing our premium set of slides with name Key Strategies For Data Security And Privacy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Network Security, Data Encryption, Access Controls. So download instantly and tailor it with your information.
-
 Cloud Architecture And Security Review Performance Challenges In Multi Cloud Architectures And Strategies
Cloud Architecture And Security Review Performance Challenges In Multi Cloud Architectures And StrategiesThis slide covers the performance challenges in multi cloud architecture and solutions to overcome the challenges such as networking between clouds and scaling limitations. Present the topic in a bit more detail with this Cloud Architecture And Security Review Performance Challenges In Multi Cloud Architectures And Strategies. Use it as a tool for discussion and navigation on Networking Between Clouds, Monitoring Multiple Clouds, Scaling Limitations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Review Strategies For Every Phase Of The Cloud Journey To Remove
Cloud Architecture And Security Review Strategies For Every Phase Of The Cloud Journey To RemoveThis slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Strategies For Every Phase Of The Cloud Journey To Remove. Dispense information and present a thorough explanation of Strategies Every Phase, Cloud Journey, Remove Network Complexity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Management Strategy Cloud Architecture And Security Review
Cloud Management Strategy Cloud Architecture And Security ReviewThis slide covers the strategies for cloud management such as cloud environment audits, cloud strategy, CIOs in charge, automating clod management, multi capability solutions, rationalizing suppliers and reducing excess spend on cloud. Introducing Cloud Management Strategy Cloud Architecture And Security Review to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Environment Audit, Rationalizing Suppliers, Automating Cloud Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Architecture And Security Review Strategies To Avoid Lock In With Multi Cloud
Cloud Architecture And Security Review Strategies To Avoid Lock In With Multi CloudThis slide covers the strategies to avoid lock ins with multi cloud such as using devops culture, keeping application managed, using opensource protocols, using opensource technologies and many more. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Strategies To Avoid Lock In With Multi Cloud. This template helps you present information on six stages. You can also present information on Ensuring Proprietary, Technology Is Ubiquitous, Isolate Proprietary Services, Infrastructure From Code using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Strategy To Scale Up Application Performance When The Business
Cloud Architecture And Security Review Strategy To Scale Up Application Performance When The BusinessThis slide covers the strategies to scale up the application performance when business will grow significantly and all applications would need a highly scalable platform. Introducing Cloud Architecture And Security Review Strategy To Scale Up Application Performance When The Business to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategy To Scale, Application Performance, Grows Significantly, using this template. Grab it now to reap its full benefits.
-
 Conducting Security Awareness Strategies We Will Implement To Make Security Awareness
Conducting Security Awareness Strategies We Will Implement To Make Security AwarenessThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Introducing Conducting Security Awareness Strategies We Will Implement To Make Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Strategy In Powerpoint And Google Slides Cpb
Cloud Security Strategy In Powerpoint And Google Slides CpbPresenting our Cloud Security Strategy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cloud Security Strategy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi System
F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi SystemThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface Increase audience engagement and knowledge by dispensing information using F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi System. This template helps you present information on four stages. You can also present information on Resources, Requirements, Heterogeneous using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
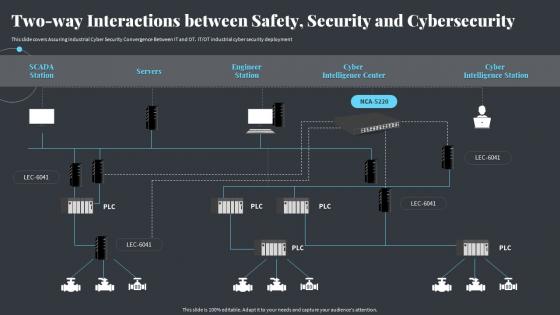 Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System
Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi SystemThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Deliver an outstanding presentation on the topic using this Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System. Dispense information and present a thorough explanation of Cybersecurity, Interactions, Intelligence Station using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations
Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient OperationsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an outstanding presentation on the topic using this Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations. Dispense information and present a thorough explanation of Strategy, Information, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics
Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better LogisticsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics. Use it as a tool for discussion and navigation on Profile Authentication, Allocation Appropriate, Particular Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ecommerce Security Strategy Framework To Prevent Fraudulent Transactions Icon
Ecommerce Security Strategy Framework To Prevent Fraudulent Transactions IconIntroducing our premium set of slides with Ecommerce Security Strategy Framework To Prevent Fraudulent Transactions Icon. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ecommerce, Security Strategy Framework, Prevent Fraudulent, Transactions Icon. So download instantly and tailor it with your information.





