Powerpoint Templates and Google slides for Security Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
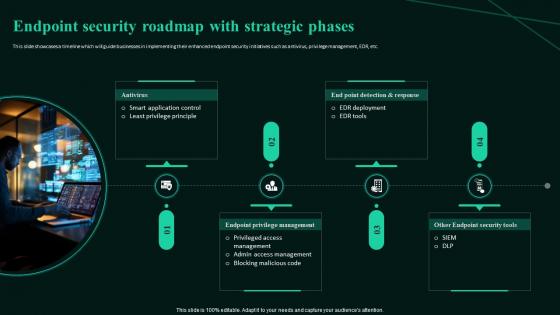 Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases a timeline which will guide businesses in implementing their enhanced endpoint security initiatives such as antivirus, privilege management, EDR, etc.Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on one stages. You can also present information on Other Endpoint Security Tools, Endpoint Privilege Management, Antivirus, End Point Detection And Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security
Web Security Upgradation Risks And Mitigation Strategies While Deploying Web SecurityThe purpose of this slide is to discuss the challenges faced while implementing web security such as alert overload, skill gap, etc. Present the topic in a bit more detail with this Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security. Use it as a tool for discussion and navigation on Risk, Impact, Mitigation Strategies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies For Chatbot Security Risks
Mitigation Strategies For Chatbot Security RisksThis slide shows information regarding various types of security risks associated with chatbots which are threats and vulnerabilities such as ransomware, malware, unencrypted communications, back-door access by hackers, etc. It also includes mitigation strategies to overcome these issues. Introducing our premium set of slides with Mitigation Strategies For Chatbot Security Risks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mitigation Strategies, Biometric Authentication, Two Factor Authentication. So download instantly and tailor it with your information.
-
 Strategies For Successful IOT Device Security
Strategies For Successful IOT Device SecurityThis slide showcases techniques followed for securing IoT devices. It includes use of virtual private network, regular checking and securing networks. Introducing our premium set of slides with name Strategies For Successful IOT Device Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Use VPN, Regular Checking, Secure Network. So download instantly and tailor it with your information.
-
 Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social
Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For SocialThe slide illustrates various strategies to secure the right grant option as per the fiscal needs of the social enterprise. Various strategies included are align project with funding requirements, review fiscal needs and improve funding information.Introducing Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Funding Information, Review Fiscal Needs, Funding Requirements, using this template. Grab it now to reap its full benefits.
-
 Web Security Solution Defense Strategies To Protect Web Applications
Web Security Solution Defense Strategies To Protect Web ApplicationsThis slide outlines the strategies for safeguarding web applications from threats which include resource allocation and web scanning solutions. Introducing Web Security Solution Defense Strategies To Protect Web Applications to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Protect Against A Wide, Range Of Breaches, Web Scanning Solutions, Resource Allocation, using this template. Grab it now to reap its full benefits.
-
 Strategies To Ensure Event Safety And Security
Strategies To Ensure Event Safety And SecurityThe slide represents event safety and security strategies that organizers can adopt to create a memorable and secure experience. It include tips such as access control, safety procedures and contingency planning. Introducing our premium set of slides with Strategies To Ensure Event Safety And Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Communicate Safety Procedures, Contingency Planning. So download instantly and tailor it with your information.
-
 Major Types Of Application Security Strategies
Major Types Of Application Security StrategiesThis slide showcases the different techniques of application security which include authentication, authorization, encryption, logging, and security testing. Presenting our set of slides with Major Types Of Application Security Strategies This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Spot Potential, Recognize Valuable Data, Vulnerable Areas
-
 IT Modernization Strategy Icon For Data Security
IT Modernization Strategy Icon For Data SecurityIntroducing our premium set of slides with IT Modernization Strategy Icon For Data Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Modernization Strategy, Data Security So download instantly and tailor it with your information.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS
Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SSThis slide showcases the Wi-Fi security to protect network and connected devices. It includes strategies such as strong passwords, encryption, firewall and intrusion detection systems IDS and two-factor authentication 2FA.Introducing Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two Factor Authentication, Intrusion Detection Systems, Encryption, Strong Passwords, using this template. Grab it now to reap its full benefits.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
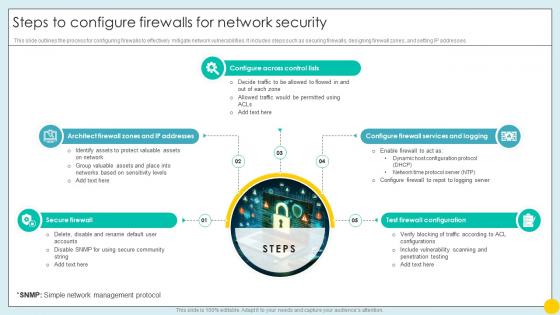 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Deepfake Threat Prevention Strategies To Improve Corporate Security
Deepfake Threat Prevention Strategies To Improve Corporate SecurityThe purpose of this slide is to help organizations improve security levels by implementing strong deepfake threat prevention strategies such as establishing strong cyber security culture, improving risk intelligence and investing in detection technology. Presenting our set of slides with name Deepfake Threat Prevention Strategies To Improve Corporate Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Improve Risk Intelligence, Establish Strong Cyber Security Culture, Invest Detection Technology.
-
 Strategic Information Technology Security Plan
Strategic Information Technology Security PlanThis slide represents strategic plan for information technology security which includes security types such as network security, internet security, endpoint security, etc. Introducing our premium set of slides with name Strategic Information Technology Security Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Purpose, Person Responsible, Actions Required, Status. So download instantly and tailor it with your information.
-
 Securing strategy implementation ppt examples slides
Securing strategy implementation ppt examples slidesQuick and simple download without any hassles. Modify text anywhere as per the context. Insert your own company logo, tagline, trademark, brand name etc. Absolutely modifiable PPT infographics- change color and contrast as required. No change in resolution of PPT images after editing. Fully alterable size and orientation of presentation icons.The stages in this process are human resource management, strategy, structure, lateral links, rewards systems.
-
 National security strategy ppt images gallery
National security strategy ppt images galleryQuick and simple to download without any hassles. Unchanged original resolution of PPT images after editing. Modify text anywhere to complement the graphics. Absolutely modifiable PPT infographics- change color scheme and contrast. Fully modifiable size and orientation of PPT icons. Add this slide anywhere within your own presentation to maximize impact.The stages in this process are national security strategy, homeland security review, critical infrastructure and climate, execute order.
-
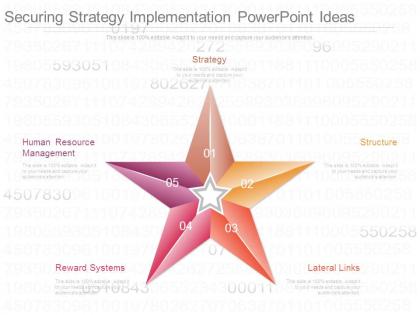 Securing strategy implementation powerpoint ideas
Securing strategy implementation powerpoint ideasPresenting securing strategy implementation powerpoint ideas. This is a securing strategy implementation powerpoint ideas. This is a five stage process. The stages in this process are strategy, structure, lateral links, reward systems, human resource management.
-
 Strategic security risk management ppt idea
Strategic security risk management ppt ideaPresenting strategic security risk management ppt idea. This is a strategic security risk management ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.
-
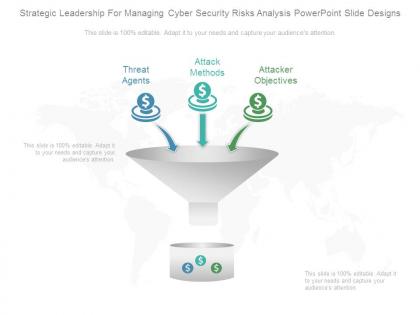 Strategic leadership for managing cyber security risks analysis powerpoint slide designs
Strategic leadership for managing cyber security risks analysis powerpoint slide designsPresenting strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
-
 Security information and event management successful siem strategies for audit compliance
Security information and event management successful siem strategies for audit complianceThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Present the topic in a bit more detail with this Security Information And Event Management Successful Siem Strategies For Audit Compliance. Use it as a tool for discussion and navigation on Information, Management, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Impact On Organization After Implementing Information Strategy Training
Information Security Impact On Organization After Implementing Information Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Security Impact On Organization After Implementing Information Strategy Training. Use it as a tool for discussion and navigation on Implementing, Information, Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan current potential challenges faced by firm
Building organizational security strategy plan current potential challenges faced by firmThis slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Current Potential Challenges Faced By Firm. Use it as a tool for discussion and navigation on Current Potential Challenges Faced By Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan ensuring effective intellectual property security
Building organizational security strategy plan ensuring effective intellectual property securityThis slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Ensuring Effective Intellectual Property Security. Use it as a tool for discussion and navigation on Information, Intellectual, Trademarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan impact of critical security concerns issues on overall
Building organizational security strategy plan impact of critical security concerns issues on overallThis slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace. Introducing Building Organizational Security Strategy Plan Impact Of Critical Security Concerns Issues On Overall to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Performance, Dissatisfaction, Reputation, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan security incidents tracking dashboard
Building organizational security strategy plan security incidents tracking dashboardThis slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Security Incidents Tracking Dashboard. Use it as a tool for discussion and navigation on Security Incidents Tracking Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And Governance
Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And GovernanceThis slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Cloud Capability Model For Strategy Architecture And Governance. This template helps you present information on four stages. You can also present information on Traditional Data Center, Orchestration And Integration, Service Request Brokering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response KPI Dashboard Incident Response Strategies Deployment
Cyber Security Incident Response KPI Dashboard Incident Response Strategies DeploymentThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response KPI Dashboard Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Monitoring, Operational, Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Systems Monitoring Report Incident Response Strategies Deployment
Cyber Security Systems Monitoring Report Incident Response Strategies DeploymentThis slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Success, Resolve, Intrusion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Analyze Cyber Security Incidents Response Strategies Deployment
Strategies To Analyze Cyber Security Incidents Response Strategies DeploymentThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Strategies To Analyze Cyber Security Incidents Response Strategies Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Details, Strategies, Correlation, using this template. Grab it now to reap its full benefits.
-
 Addressing Different Security Priorities At Organization Strategic Organizational Security Plan
Addressing Different Security Priorities At Organization Strategic Organizational Security PlanThis slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Increase audience engagement and knowledge by dispensing information using Addressing Different Security Priorities At Organization Strategic Organizational Security Plan. This template helps you present information on six stages. You can also present information on Information Security, Brand Protection, Crisis Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Performance Indicators To Determine Security Strategic Organizational Security Plan
Addressing Performance Indicators To Determine Security Strategic Organizational Security PlanThis slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an outstanding presentation on the topic using this Addressing Performance Indicators To Determine Security Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Incidents, Offender Management, Risk Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Potential Challenges Faced By Firm Strategic Organizational Security Plan
Current Potential Challenges Faced By Firm Strategic Organizational Security PlanThis slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Present the topic in a bit more detail with this Current Potential Challenges Faced By Firm Strategic Organizational Security Plan. Use it as a tool for discussion and navigation on Financial, Data, Data Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Critical Security Concerns Issues On Overall Firms Strategic Organizational Security Plan
Impact Of Critical Security Concerns Issues On Overall Firms Strategic Organizational Security PlanThis slide provides information about the several situations that will result in increase of potential security threats in the organization and addressing various major security concerns at workplace.Deliver an outstanding presentation on the topic using this Impact Of Critical Security Concerns Issues On Overall Firms Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Tarnished Reputation, Customer Dissatisfaction, Increase In Expenses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Incidents Tracking Dashboard Strategic Organizational Security Plan
Security Incidents Tracking Dashboard Strategic Organizational Security PlanThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Present the topic in a bit more detail with this Security Incidents Tracking Dashboard Strategic Organizational Security Plan. Use it as a tool for discussion and navigation on Security, Application Hardening, Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS
ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SSThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc.Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Risk Categories, Control Review, Control Review Effectiveness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Analysis Of Major How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Competitive Analysis Of Major How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding comparative analysis of potential players existing across marketplace. The points of differentiation include financial parameters, critical success factors such as product variety, customer services, email marketing, etc. Present the topic in a bit more detail with this Competitive Analysis Of Major How Amazon Is Securing Competitive Edge Across Globe Strategy SS. Use it as a tool for discussion and navigation on Ecommerce Market Share, Ecommerce Ecosystem, Dynamics. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Acquisitions Initiated How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Major Acquisitions Initiated How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding potential businesses acquired by Amazon in past years. Firm considered acquisitions in order to strengthen its core e commerce operations and technology in order to attract target audience. Present the topic in a bit more detail with this Major Acquisitions Initiated How Amazon Is Securing Competitive Edge Across Globe Strategy SS. Use it as a tool for discussion and navigation on E Commerce Operations, Technology, Cybersecurity Player. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Performance Report To Assess How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Performance Report To Assess How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding Amazon platform growth performance analysis report. The progress is determined by products sold on platform, increase in ad spend, active sellers, advertising growth, etc. Deliver an outstanding presentation on the topic using this Performance Report To Assess How Amazon Is Securing Competitive Edge Across Globe Strategy SS. Dispense information and present a thorough explanation of Revenue Growth, Amazon Advertising, Market Share using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding potential business and research collaboration initiated by Amazon. The focus of Amazon is to cooperate with credible, knowledgeable, innovative industry partners who share similar vision such as microsoft, ford, etc. Introducing Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implemented, Security Systems, Capability, using this template. Grab it now to reap its full benefits.
-
 Overview Of Key KPMG Cyber Security Comprehensive Guide To KPMG Strategy SS
Overview Of Key KPMG Cyber Security Comprehensive Guide To KPMG Strategy SSThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less data centric future, etc. with description and insights.Present the topic in a bit more detail with this Overview Of Key KPMG Cyber Security Comprehensive Guide To KPMG Strategy SS. Use it as a tool for discussion and navigation on Security Considerations, Warranted Commensurate, Automating Mundane. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V
Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding effective IT cost optimization strategies for IT executives such as revamping technology procurement, DevOps deployment, enabling business process reengineering, etc. Increase audience engagement and knowledge by dispensing information using Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V. This template helps you present information on four stages. You can also present information on Revamping Technology Procurement, Enabling Business Process Reengineering, Optimization Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS V
F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding dashboard to monitor critical activities related to IT in terms of incident tracker, outage report, IT spend per employee, application trends, etc. Present the topic in a bit more detail with this F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Dashboard, Associated, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS V
It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding the dashboard to monitor overall IT performance. The dashboard tracks occupancy rate, net promoter score, avg. first contact resolution rate, etc. Present the topic in a bit more detail with this It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Performance, Dashboard, Satisfaction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS V
Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding responsibilities managed by CIOs across firm in terms of task delegation to improve productivity, management of IT dept., Administer network and system deployment, etc. Present the topic in a bit more detail with this Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Responsibilities, Management, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS V
Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding the key steps required to develop an application rationalization framework and their feasibility. The steps include determining business value, measuring application TCO, etc. Present the topic in a bit more detail with this Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Application, Rationalization, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V
Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information various steps required to develop target marketing initiatives for IT department. The initiatives include detect target market, conduct market research, develop objectives and goals, etc. Introducing Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Marketing, Initiatives, Department, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS V
Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS VPresent the topic in a bit more detail with this Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Strategic Business Alignment, Workforce And Cost Management, Deploy Application Rationalization . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Information Security Strategy On Company
Impact Of Information Security Strategy On CompanyThe slide showcases impact initiated by information security strategy and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Presenting our well structured Impact Of Information Security Strategy On Company. The topics discussed in this slide are Impact Of Information, Security, Strategy On Company. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS V
ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Standard Control Issues, Control Issues By Regulation, Risk Categories. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS V
Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Responsible Person, Number Of Respondents, Businesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
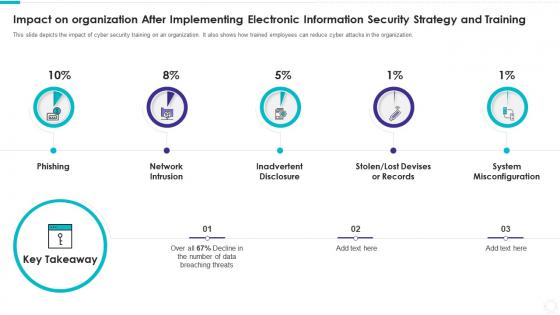 Impact on organization after implementing electronic information security strategy
Impact on organization after implementing electronic information security strategyThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Introducing Impact On Organization After Implementing Electronic Information Security Strategy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen, Lost Devises Or Records, System Misconfiguration, using this template. Grab it now to reap its full benefits.
-
 Electronic information security strategies to manage cyber risks
Electronic information security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Prioritize Cyber Risk Strategic Issue, Build Policies And Structures, Invest Worthy Implementation, Conduct Awareness Sessions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber threat strategies for security protection
Cyber threat strategies for security protectionThis slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Presenting our set of slides with Cyber Threat Strategies For Security Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Program, Software Protocols, End Point Protection.
-
 Steps To Develop Strategic Security Program
Steps To Develop Strategic Security ProgramThis slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc. Introducing our premium set of slides with Steps To Develop Strategic Security Program. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organizational Culture, Measuring Goals, Program Assessment. So download instantly and tailor it with your information.





