Powerpoint Templates and Google slides for Security Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Suitable It Infrastructure Monitoring Tool Selection Strategic Plan To Secure It Infrastructure Strategy SS V
Suitable It Infrastructure Monitoring Tool Selection Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding selection of suitable IT infrastructure monitoring tool by comparative assessment based on various features such as real time visibility, capacity planning, network infrastructure monitoring, etc. along with costs. Present the topic in a bit more detail with this Suitable It Infrastructure Monitoring Tool Selection Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Comparative, Assessment, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Three Step Approach To Attain It Cost Leadership Strategic Plan To Secure It Infrastructure Strategy SS V
Three Step Approach To Attain It Cost Leadership Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding three step approach for strategic cost management in terms of enabling organization and IT alignment, detecting opportunities, and benefits realization. Present the topic in a bit more detail with this Three Step Approach To Attain It Cost Leadership Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Approach, Leadership, Optimization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Understanding Role Of It Steering Committee Strategic Plan To Secure It Infrastructure Strategy SS V
Understanding Role Of It Steering Committee Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding highlighting the role of IT steering committee, which perform advocating initiatives across the firm, track project progress, enable conflict resolution among parties, etc. Deliver an outstanding presentation on the topic using this Understanding Role Of It Steering Committee Strategic Plan To Secure It Infrastructure Strategy SS V. Dispense information and present a thorough explanation of Associated, Governance Process, Initiatives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS V
Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS V. Use it as a tool for discussion and navigation on Information, Governance, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Risk Management Framework To Manage Security Threats Cios Guide For It Strategy Strategy SS V
It Risk Management Framework To Manage Security Threats Cios Guide For It Strategy Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Threats Cios Guide For It Strategy Strategy SS V. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Action Plan For Cloud Security Threats
Strategic Action Plan For Cloud Security ThreatsThis slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments Presenting our well structured Strategic Action Plan For Cloud Security Threats. The topics discussed in this slide are Cloud, Security, Strategic. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Public Relations Strategy For Product Promotion Budget Securing Tips For Public MKT SS V
Public Relations Strategy For Product Promotion Budget Securing Tips For Public MKT SS VThis slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Increase audience engagement and knowledge by dispensing information using Public Relations Strategy For Product Promotion Budget Securing Tips For Public MKT SS V. This template helps you present information on three stages. You can also present information on Strategic Insights, Highlight Impacts, Company Goals using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Exit Strategy Awake Security Investor Funding Elevator Pitch Deck
Exit Strategy Awake Security Investor Funding Elevator Pitch DeckThe slide provides most profitable feasible ways for investors to exit from their investment in the company. It includes IPO, merger, private offerings, acquisition by venture capital firm etc. Introducing Exit Strategy Awake Security Investor Funding Elevator Pitch Deck to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Initial Public Offering, Private Offering, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS V
Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Find And Track Devices, Installation And Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS V
Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Deliver an outstanding presentation on the topic using this Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS V. Dispense information and present a thorough explanation of Encrypted Data, Backup Repository, Tape Media, Secret Key using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Access Security Control Models ICT Strategic Framework Strategy SS V
Key Access Security Control Models ICT Strategic Framework Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Key Access Security Control Models ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access, Role Based Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS V
Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Most Commonly Types Of ICT Securities Used By Businesses ICT Strategic Framework Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, End Point Security, Access Security, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Network Security Model To Effective Communication ICT Strategic Framework Strategy SS V
Network Security Model To Effective Communication ICT Strategic Framework Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Network Security Model To Effective Communication ICT Strategic Framework Strategy SS V. Dispense information and present a thorough explanation of Information Channel, Secure Message, Message Transformation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V
Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Present the topic in a bit more detail with this Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Network Security, Access Security, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 30 60 90 Days Plan To Secure Organizations Phishing Attacks And Strategies
30 60 90 Days Plan To Secure Organizations Phishing Attacks And StrategiesThis slide represents 30 60 90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Introducing 30 60 90 Days Plan To Secure Organizations Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Phishing, Deploy Anti Phishing, Implement Multi Factor, using this template. Grab it now to reap its full benefits.
-
 Checklist To Secure Organizations From Phishing Attacks And Strategies
Checklist To Secure Organizations From Phishing Attacks And StrategiesThis slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real time monitoring and develop an incident plan.Present the topic in a bit more detail with this Checklist To Secure Organizations From Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Key Approaches, Provide Staff Training, Alerting Impacted. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roadmap To Secure Organizations From Phishing Attacks And Strategies
Roadmap To Secure Organizations From Phishing Attacks And StrategiesThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.Increase audience engagement and knowledge by dispensing information using Roadmap To Secure Organizations From Phishing Attacks And Strategies. This template helps you present information on five stages. You can also present information on Security Assessment, Technical Controls, Employee Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Secure Organizations From Phishing Attacks And Strategies
Timeline To Secure Organizations From Phishing Attacks And StrategiesThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.Increase audience engagement and knowledge by dispensing information using Timeline To Secure Organizations From Phishing Attacks And Strategies. This template helps you present information on five stages. You can also present information on Security Assessment, Technical Controls, Educate Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security strategy powerpoint slide background designs
Cyber security strategy powerpoint slide background designsPresenting cyber security strategy powerpoint slide background designs. This is a cyber security strategy powerpoint slide background designs. This is a one stage process. The stages in this process are firewall, antivirus, passwords, email scans.
-
 Data security strategies powerpoint ideas
Data security strategies powerpoint ideasIntroducing data security strategies PPT design. Fully regulated PowerPoint template quite reasonable for the management professionals and business specialists. Extensive scope for reviving the dummy data and can add company logo, trademark etc. Reconvert able background PPT images, subject matter, designs, context etc. according to need. Versant with all Google Slides and other system applications. Can be easily projected over wide screen with exceptional picture quality.
-
 Cost strategies web acceleration security software shopping carts
Cost strategies web acceleration security software shopping cartsPresenting this set of slides with name - Cost Strategies Web Acceleration Security Software Shopping Carts. This is an editable one stages graphic that deals with topics like Cost Strategies, Web Acceleration, Security Software, Shopping Carts to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Integrated resources entity death national food security strategies
Integrated resources entity death national food security strategiesPresenting this set of slides with name - Integrated Resources Entity Death National Food Security Strategies. This is an editable eight stages graphic that deals with topics like Integrated Resources, Entity Death, National Food Security Strategies to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Service desk security management release management security strategy
Service desk security management release management security strategyPresenting this set of slides with name - Service Desk Security Management Release Management Security Strategy. This is an editable two stages graphic that deals with topics like Service Desk, Security Management, Release Management, Security Strategy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Performance outcome job security commitment organization strategy focus
Performance outcome job security commitment organization strategy focusPresenting this set of slides with name - Performance Outcome Job Security Commitment Organization Strategy Focus. This is an editable four stages graphic that deals with topics like Performance outcome, Job security, Commitment organization, Strategy focus to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Decision making secure advantage removing speeding marketing strategy
Decision making secure advantage removing speeding marketing strategyPresenting this set of slides with name - Decision Making Secure Advantage Removing Speeding Marketing Strategy. This is an editable four stages graphic that deals with topics like Decision Making, Secure Advantage, Removing Speeding, Marketing Strategy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Enterprise security strategy roadmap data architecture business analytics
Enterprise security strategy roadmap data architecture business analyticsPresenting this set of slides with name - Enterprise Security Strategy Roadmap Data Architecture Business Analytics. This is an editable four stages graphic that deals with topics like Enterprise Security, Strategy Roadmap, Data Architecture, Business Analytics to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security strategy activities controls monitor measure
Information security strategy activities controls monitor measurePresenting this set of slides with name - Information Security Strategy Activities Controls Monitor Measure. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy assessment ethical hacking
Information security strategy assessment ethical hackingPresenting this set of slides with name - Information Security Strategy Assessment Ethical Hacking. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
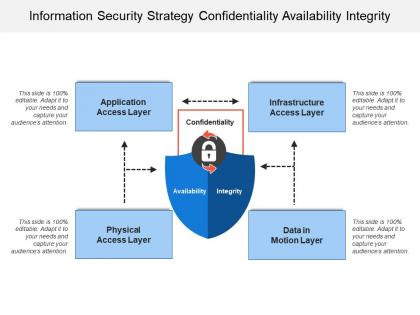 Information security strategy confidentiality availability integrity
Information security strategy confidentiality availability integrityPresenting this set of slides with name - Information Security Strategy Confidentiality Availability Integrity. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
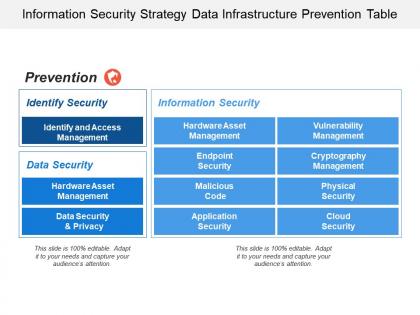 Information security strategy data infrastructure prevention table
Information security strategy data infrastructure prevention tablePresenting this set of slides with name - Information Security Strategy Data Infrastructure Prevention Table. This is a two stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy icons
Information security strategy iconsPresenting this set of slides with name - Information Security Strategy Icons. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
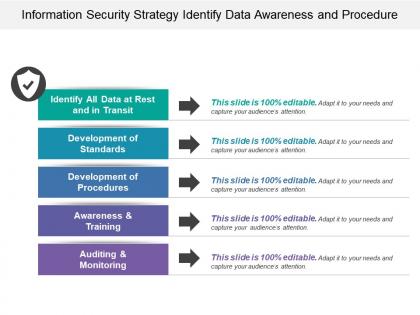 Information security strategy identify data awareness and procedure
Information security strategy identify data awareness and procedurePresenting this set of slides with name - Information Security Strategy Identify Data Awareness And Procedure. This is a five stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy mobile computer antivirus
Information security strategy mobile computer antivirusPresenting this set of slides with name - Information Security Strategy Mobile Computer Antivirus. This is a eight stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy prevention and detection
Information security strategy prevention and detectionPresenting this set of slides with name - Information Security Strategy Prevention And Detection. This is a six stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy prevention detection response
Information security strategy prevention detection responsePresenting this set of slides with name - Information Security Strategy Prevention Detection Response. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy security partner solutions
Information security strategy security partner solutionsPresenting this set of slides with name - Information Security Strategy Security Partner Solutions. This is a five stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Execution plan showing strategic plan and securing value delivery
Execution plan showing strategic plan and securing value deliveryPresenting this set of slides with name - Execution Plan Showing Strategic Plan And Securing Value Delivery. This is a seven stage process. The stages in this process are Execution Plan, Execution Strategy, Execution Approach.
-
 Technical strategy with service security value and agility
Technical strategy with service security value and agilityPresenting this set of slides with name - Technical Strategy With Service Security Value And Agility. This is a two stage process. The stages in this process are Technical Strategy, Technical Plan, Technical Approaches.
-
 Process integration oversight security policy management corporate strategic plan
Process integration oversight security policy management corporate strategic planPresenting this set of slides with name - Process Integration Oversight Security Policy Management Corporate Strategic Plan. This is an editable three stages graphic that deals with topics like Process Integration Oversight, Security Policy Management, Corporate Strategic Plan to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Sales trends business investment cases secure finding portfolio strategic
Sales trends business investment cases secure finding portfolio strategicPresenting this set of slides with name - Sales Trends Business Investment Cases Secure Finding Portfolio Strategic. This is an editable five stages graphic that deals with topics like Sales Trends, Business Investment Cases, Secure Finding, Portfolio Strategic to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Valuation companies secure date exchange strategic planning investment
Valuation companies secure date exchange strategic planning investmentPresenting this set of slides with name - Valuation Companies Secure Date Exchange Strategic Planning Investment. This is an editable four stages graphic that deals with topics like Valuation Companies, Secure Date Exchange, Strategic Planning Investment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application security effective web application environment strategic planning
Application security effective web application environment strategic planningPresenting this set of slides with name - Application Security Effective Web Application Environment Strategic Planning. This is an editable five stages graphic that deals with topics like Application Security Effective, Web Application Environment, Strategic Planning to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Hr strategic business risk management enterprise security intelligence cpb
Hr strategic business risk management enterprise security intelligence cpbPresenting this set of slides with name - Hr Strategic Business Risk Management Enterprise Security Intelligence Cpb. This is an editable four stages graphic that deals with topics like Hr Strategic Business, Risk Management, Enterprise Security Intelligence to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Half yearly data strategy govern integrate store security swim lane
Half yearly data strategy govern integrate store security swim lanePresenting this set of slides with name - Half Yearly Data Strategy Govern Integrate Store Security Swim Lane. This is a two stage process. The stages in this process are Data Management For Data Strategy Swim Lane, Data Management For Data Plan Swim Lane, Data Management For Data Approach Swim Lane.
-
 Quarterly data strategy govern integrate store security swim lane
Quarterly data strategy govern integrate store security swim lanePresenting this set of slides with name - Quarterly Data Strategy Govern Integrate Store Security Swim Lane. This is a four stage process. The stages in this process are Data Management For Data Strategy Swim Lane, Data Management For Data Plan Swim Lane, Data Management For Data Approach Swim Lane.
-
 Six months data strategy govern integrate store security swim lane
Six months data strategy govern integrate store security swim lanePresenting this set of slides with name - Six Months Data Strategy Govern Integrate Store Security Swim Lane. This is a six stage process. The stages in this process are Data Management For Data Strategy Swim Lane, Data Management For Data Plan Swim Lane, Data Management For Data Approach Swim Lane.
-
 Three months data strategy govern integrate store security swim lane
Three months data strategy govern integrate store security swim lanePresenting this set of slides with name - Three Months Data Strategy Govern Integrate Store Security Swim Lane. This is a three stage process. The stages in this process are Data Management For Data Strategy Swim Lane, Data Management For Data Plan Swim Lane, Data Management For Data Approach Swim Lane.
-
 Yearly data strategy govern integrate store security swim lane
Yearly data strategy govern integrate store security swim lanePresenting this set of slides with name - Yearly Data Strategy Govern Integrate Store Security Swim Lane. This is a five stage process. The stages in this process are Data Management For Data Strategy Swim Lane, Data Management For Data Plan Swim Lane, Data Management For Data Approach Swim Lane.
-
 Mobile applications security new strategic selling stress management cpb
Mobile applications security new strategic selling stress management cpbPresenting this set of slides with name - Mobile Applications Security New Strategic Selling Stress Management Cpb. This is an editable six stages graphic that deals with topics like Mobile Applications Security, New Strategic Selling, Stress Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security analysis strategy strategic planning life cycle diagram cpb
Security analysis strategy strategic planning life cycle diagram cpbPresenting this set of slides with name - Security Analysis Strategy Strategic Planning Life Cycle Diagram Cpb. This is an editable four stages graphic that deals with topics like Security Analysis, Strategy Strategic Planning, Life Cycle Diagram to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Acquisition retention strategy customer segmentation requirements security analyst cpb
Acquisition retention strategy customer segmentation requirements security analyst cpbPresenting this set of slides with name - Acquisition Retention Strategy Customer Segmentation Requirements Security Analyst Cpb. This is an editable nine stages graphic that deals with topics like Acquisition Retention Strategy, Customer Segmentation Requirements, Security Analyst to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Pricing strategies retail strategy network security network management cpb
Pricing strategies retail strategy network security network management cpbPresenting this set of slides with name - Pricing Strategies Retail Strategy Network Security Network Management Cpb. This is an editable five stages graphic that deals with topics like Pricing Strategies, Retail Strategy, Network Security, Network Management to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategy financial retail services migration work cpb
Cyber security strategy financial retail services migration work cpbPresenting this set of slides with name - Cyber Security Strategy Financial Retail Services Migration Work Cpb. This is an editable four graphic that deals with topics like Cyber Security Strategy, Financial Retail Services, Migration Work to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Finance business collaboration corporate business data security business strategy cpb
Finance business collaboration corporate business data security business strategy cpbPresenting this set of slides with name - Finance Business Collaboration Corporate Business Data Security Business Strategy Cpb. This is an editable three stages graphic that deals with topics like Finance, Business, Collaboration, Corporate, Business, Data, Security, Business, Strategy to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Champagne littoral e currency list safety regulations security strategy cpb
Champagne littoral e currency list safety regulations security strategy cpbPresenting this set of slides with name - Champagne Littoral E Currency List Safety Regulations Security Strategy Cpb. This is an editable three stages graphic that deals with topics like Champagne, Littoral, E Currency, List, Safety Regulations, Security Strategy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Business strategy continuity management network security product development cpb
Business strategy continuity management network security product development cpbPresenting this set of slides with name - Business Strategy Continuity Management Network Security Product Development Cpb. This is an editable four stages graphic that deals with topics like Business, Strategy, Continuity, Management, Network, Security, Product, Development to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Insider threats information security strategic thinking entrepreneurial action cpb
Insider threats information security strategic thinking entrepreneurial action cpbPresenting this set of slides with name - Insider Threats Information Security Strategic Thinking Entrepreneurial Action Cpb. This is an editable four stages graphic that deals with topics like Insider Threats Information Security, Strategic Thinking Entrepreneurial Action to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategies small business ppt powerpoint presentation demonstration cpb
Cyber security strategies small business ppt powerpoint presentation demonstration cpbPresenting this set of slides with name Cyber Security Strategies Small Business Ppt Powerpoint Presentation Demonstration Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Strategies Small Business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security strategy framework ppt powerpoint presentation outline pictures cpb
Information security strategy framework ppt powerpoint presentation outline pictures cpbPresenting this set of slides with name Information Security Strategy Framework Ppt Powerpoint Presentation Outline Pictures Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Information Security Strategy Framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Post it strategy security ppt powerpoint presentation pictures portrait
Post it strategy security ppt powerpoint presentation pictures portraitPresenting this set of slides with name Post It Strategy Security Ppt Powerpoint Presentation Pictures Portrait. This is a four stage process. The stages in this process are Marketing, Business, Management, Planning, Strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.





