Powerpoint Templates and Google slides for Security Strategies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Build Strategic STO Team Beginners Guide To Successfully Launch Security Token BCT SS V
Build Strategic STO Team Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts tactical structure of STO team and advisory board to ensure clear communication. It includes elements such as blockchain developer, marketing manager, legal advisor, finance, operation manager, PR experts, etc. Introducing Build Strategic STO Team Beginners Guide To Successfully Launch Security Token BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Build Strategic, STO Team, Advisory Structure, using this template. Grab it now to reap its full benefits.
-
 Strategic Content Marketing Beginners Guide To Successfully Launch Security Token BCT SS V
Strategic Content Marketing Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide illustrates content marketing action plan for security token offerings STO to maximize reach. It includes elements such as objectives, target audience, content strategy, create blogs, determine areas of improvement, etc. Introducing Strategic Content Marketing Beginners Guide To Successfully Launch Security Token BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Target Audience, Content Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategic Influencer Beginners Guide To Successfully Launch Security Token BCT SS V
Strategic Influencer Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Increase audience engagement and knowledge by dispensing information using Strategic Influencer Beginners Guide To Successfully Launch Security Token BCT SS V. This template helps you present information on five stages. You can also present information on Objectives, Budget, Giveaways using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Fortify Cyber Security By Using Big Data Strategies
Fortify Cyber Security By Using Big Data StrategiesThis slide contains strategies to fortify cyber security using big data. Its aim is to predict future anomalies and detect frauds in cyber security. This slide includes automated monitoring, real time protection. Presenting our set of slides with Fortify Cyber Security By Using Big Data Strategies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Predict, Detection, Monitoring.
-
 Infrastructure Security Management Optimisation Strategies
Infrastructure Security Management Optimisation StrategiesThis slide represents the infrastructure security management utilisation methods. Its aim is to run security tools in a secure, documented with virtual team. This slide includes firewall system, remote access, cloud management and workflow system. Introducing our premium set of slides with Infrastructure Security Management Optimisation Strategies. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Generation, Remote, Management. So download instantly and tailor it with your information.
-
 Strategies To Mitigate Saas Cyber Security Risks
Strategies To Mitigate Saas Cyber Security RisksThis slide represents tips to boost SaaS cyber security by reducing risks. It aims to implement effective measures collectively to reduce cyber security risks for SaaS platform. It includes various approaches such as continuous SaaS discovery, consistent SaaS risk management, etc. Introducing our premium set of slides with Strategies To Mitigate Saas Cyber Security Risks Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Continuous Saas Discovery, Risk Management, Mitigate Vulnerabilities. So download instantly and tailor it with your information.
-
 Strategies And Tools To Enhance Big Data Security Management
Strategies And Tools To Enhance Big Data Security ManagementThis slide showcases the strategies and tools helping companies to effectively manage and monitor big data security from cyber threats. It includes strategies such as cloud security monitoring, centralized key management, incident investigation, etc. Introducing our Strategies And Tools To Enhance Big Data Security Management set of slides. The topics discussed in these slides are Cloud Security Monitoring, Centralized Key Management, Network Traffic Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among
Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness AmongThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Email Attachments, Systems, Employees using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence
Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk OccurrenceThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence Use it as a tool for discussion and navigation on Parameters, Impact, Probability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence Checklist
Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence ChecklistThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Deliver an outstanding presentation on the topic using this Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence Checklist Dispense information and present a thorough explanation of Parameters, Tasks, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration
Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud MigrationThe following slide showcases a case study on data security and compliance in cloud migration. It includes various elements such as company details, challenges, and solutions. Increase audience engagement and knowledge by dispensing information using Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration. This template helps you present information on three stages. You can also present information on Data Security, Cloud Migration, Security And Confidentiality, Customer Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data Migration
Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data MigrationThe purpose of this slide is to showcase a checklist for ensuring safe migration of data from one source to another. It includes various tactics such as data protection impact assessment, data security and encryption, data retention and deletion, etc. Deliver an outstanding presentation on the topic using this Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data Migration. Dispense information and present a thorough explanation of Legal Limitations, Compliance Requirements, Legacy Database Schema, Intrusion Detection Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By Companies
Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By CompaniesThe purpose of this slide is to assess security and privacy challenges, and their impact on data migration process. It includes challenges and need for ensuring data privacy. Introducing Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By Companies to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Data Security And Privacy Challenges, Loss Of Customers, Sensitive Data, Poses Security And Privacy Concerns, using this template. Grab it now to reap its full benefits.
-
 Strategic Approach For Effective Data Migration Steps For A Secure Data Migration Process
Strategic Approach For Effective Data Migration Steps For A Secure Data Migration ProcessThe purpose of this slide is to represent the process of secure and safe data migration from one platform to another. It includes various stages such as assessing data sources, choosing method, designing architecture, etc. Introducing Strategic Approach For Effective Data Migration Steps For A Secure Data Migration Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Design Architecture, Validate And Verify Results, Assess Data Sources, Data Migration Process, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Strategies For Data Management
Cyber Security Strategies For Data ManagementThe mentioned slide underscores critical strategies, including updated software, firewall protection, awareness of phishing scams, safeguarding sensitive information, and securing mobile devices. These cybersecurity measures collectively contribute to effective data management and protection against potential threats. Introducing our premium set of slides with Cyber Security Strategies For Data Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Keep Software Up To Date, Reduced Data Breach Risk, Empowered User Vigilance. So download instantly and tailor it with your information.
-
 How To Strategically Engage Vendors To Secure Procurement Excellence
How To Strategically Engage Vendors To Secure Procurement ExcellenceThis slide showcases the ways engaging distributors for securing procurement excellence which helps an organization to manage and update approved suppliers lists effectively and quickly. It include details such as analyze vendor performance, provide self service portals, etc. Presenting our set of slides with How To Strategically Engage Vendors To Secure Procurement Excellence. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyze Vendor Performance, Service Portals, Vendor Dashboards.
-
 Strategic Training Planning For Cyber Security Awareness
Strategic Training Planning For Cyber Security AwarenessThis slide represents training program for cyber security awareness which includes key topics such as phishing detection, password security, etc Presenting our well structured Strategic Training Planning For Cyber Security Awareness The topics discussed in this slide are Communication Skills, Personality, Problem Solving. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implement ATP Cyber Security Strategies In Organisation
Implement ATP Cyber Security Strategies In OrganisationThis slide depicts the strategies for cyber security ATP. Its objective is to help formulate advanced strategies for threat protection. This slide includes broad test repository, benign software behaviour, analysis of data, etc. Presenting our set of slides with name Implement ATP Cyber Security Strategies In Organisation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Broad Test Repository, Benign Software Behaviour, Analysis Of Data.
-
 Strategies For Identifying Security Gap In Network
Strategies For Identifying Security Gap In NetworkThe following slide represents identifying tactics of gaps in security network for improving data structure. It further covers run network audit, analyse system log data and audit IT supply chain. Introducing our Strategies For Identifying Security Gap In Network set of slides. The topics discussed in these slides are Run Network Audit, Analyse System Log Data, Audit IT Supply Chain. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment
Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E PaymentMentioned slide provides information about strategies which can be implemented by businesses before going cashless. It includes strategies such as determine customer preferences, select payment processor, offer payment options, implement CRM software. Present the topic in a bit more detail with this Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Determine Customer Preference, Select Payment Processor, Implement CRM Tool This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security And Compliance Strategies Of Event Driven Automation
Security And Compliance Strategies Of Event Driven AutomationThis slide represents event-based automation security and compliance strategies. It aims to assist in harden IT systems such that when security-related incidents occur. It includes various constituents such as applying security patches, unauthorized access detection and response, etc. Presenting our set of slides with Security And Compliance Strategies Of Event Driven Automation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enhance Success Of Events, Attendee Satisfaction, Meet Event Goals
-
 Implementing Effective Tokenization Steps To Implement Security Tokenization Strategy
Implementing Effective Tokenization Steps To Implement Security Tokenization StrategyThis slide represents the different phases of deploying security tokenization which include identifying sensitive data, implementing tokenization, etc. Increase audience engagement and knowledge by dispensing information using Implementing Effective Tokenization Steps To Implement Security Tokenization Strategy. This template helps you present information on seven stages. You can also present information on Implement Security Tokenization, Identify Sensitive Data, Secure Storage Of Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps
DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOpsThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build or test, deploy, and monitor. Present the topic in a bit more detail with this DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps. Use it as a tool for discussion and navigation on Integrate Security, Encourage Developer Ownership, Static Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
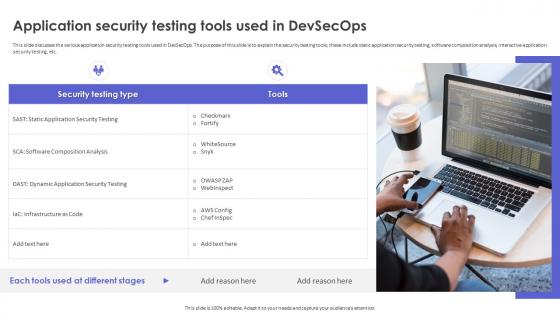 Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps
Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOpsThis slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Increase audience engagement and knowledge by dispensing information using Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps. This template helps you present information on one stages. You can also present information on Application Security Testing, Software Composition Analysis, Interactive Application Security Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model
Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model. Dispense information and present a thorough explanation of Boost Workflow Efficiency, Performance Metrics, Pipeline Security Working using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Ensure Information Security From Ransomware Attacks
Strategies To Ensure Information Security From Ransomware AttacksThis slide highlights techniques for securing information against ransomware attacks. The purpose of this slide is to assist professionals in ensuring business continuity and minimizing downtime. It includes elements such as email security, patch updates, network segmentation, etc. Introducing our premium set of slides with Strategies To Ensure Information Security From Ransomware Attacks. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Awareness. So download instantly and tailor it with your information.
-
 Web Security Vulnerabilities And Their Prevention Strategies
Web Security Vulnerabilities And Their Prevention StrategiesThis slide covers common web security pitfalls and their mitigation strategies. The purpose of this slide is to help businesses in minimizing web related IT security pitfalls. It covers various prevention strategies to address web security vulnerabilities such as injection flaws, broken authentication, cross site scripting and security misconfiguration. Introducing our premium set of slides with Web Security Vulnerabilities And Their Prevention Strategies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Injection Flaws, Broken Authentication, Cross Site Scripting So download instantly and tailor it with your information.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Existing IT Security Strategic Implementation Of Regression Testing
Existing IT Security Strategic Implementation Of Regression TestingThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. Deliver an outstanding presentation on the topic using this Existing IT Security Strategic Implementation Of Regression Testing. Dispense information and present a thorough explanation of Existing IT Security, Infrastructure Constituents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study 2 Internet Security Sales Enablement Strategy To Boost Productivity And Drive SA SS
Case Study 2 Internet Security Sales Enablement Strategy To Boost Productivity And Drive SA SSThis slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. Increase audience engagement and knowledge by dispensing information using Case Study 2 Internet Security Sales Enablement Strategy To Boost Productivity And Drive SA SS. This template helps you present information on two stages. You can also present information on Sales Tools, Product Knowledge, Single Platform using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Automation Strategies To Enhance Security And Compliance
Cloud Automation Strategies To Enhance Security And ComplianceThis slide represents cloud automation strategies to enhance security and compliance which assists organizations to streamline operations and minimizes manual intervention. It includes cloud automation strategies to enhance security and compliances such as utilize infrastructure as code, etc. Introducing our premium set of slides with name Cloud Automation Strategies To Enhance Security And Compliance. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Consulting Partner, Leverage Automation, Enhance Compliance, Utilize Policy As Tools. So download instantly and tailor it with your information.
-
 Cyber Security Management Strategies To Mitigate Threats
Cyber Security Management Strategies To Mitigate ThreatsThis slide highlights different strategies that can help businesses in reducing cyber security threats. It further covers attributes such as priority level, description, mitigating strategies, etc. Presenting our well structured Cyber Security Management Strategies To Mitigate Threats. The topics discussed in this slide are Information Disclosure, Service Denial, Tampering. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Plan With Prevention Strategies
Cyber Security Risk Management Plan With Prevention StrategiesFollowing slide includes cyber security plan to systematically assess and mitigation cyber risk within organisation. It further covers, description, risk level, responsible manager, threats and prevention strategies. Introducing our Cyber Security Risk Management Plan With Prevention Strategies set of slides. The topics discussed in these slides are Risk Level, Responsible Manager, Prevention Strategies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategic Cyber Security Management Objectives
Strategic Cyber Security Management ObjectivesFollowing slide showcases implementation of cyber security management in an organization for employee awareness. It further covers related measures, due date, strategies such as availability, threats, authority management and access control, etc. Introducing our Strategic Cyber Security Management Objectives set of slides. The topics discussed in these slides are Cyber Security Management Objectives, Authority Management, Access Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cyber Security Strategies In Automotive Sector
Effective Cyber Security Strategies In Automotive SectorThis slide highlights cyber security methods in automobile industry. The purpose of this slide is to help managers in safeguarding vehicles from threats by implementing robust security measures. It includes elements such as risk assessment, user education, etc. Introducing our premium set of slides with Effective Cyber Security Strategies In Automotive Sector Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Security By Design, Patch Management So download instantly and tailor it with your information.
-
 Strategies To Ensure Endpoint Cyber Security
Strategies To Ensure Endpoint Cyber SecurityThis slide covers common endpoint cyber security risks and various strategies to minimize threat effects. The purpose of this slide is to assist businesses in overcoming compliance vulnerabilities and security risks. It includes strategies such as outdated patches, phishing attacks, software vulnerabilities exploits, etc. Presenting our set of slides with Strategies To Ensure Endpoint Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Track Connected Devices, Strategies, Manage USB Port Access
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS
Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SSThis slide showcases password encryption policies which can help organizations achieve maximum data security. It provides details about salting, SHA-2, Bcrypt, passcode age, auto-lock, etc. Present the topic in a bit more detail with this Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS. Use it as a tool for discussion and navigation on Require Alphanumeric Value, Maximum Passcode Age, Grace Period For Device Lock. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies For RFID Security And Privacy Concerns
Mitigation Strategies For RFID Security And Privacy ConcernsThis slide represents mitigation strategies for RFID security and privacy concerns, such as encryption, monitoring and logging, shielding, etc.Increase audience engagement and knowledge by dispensing information using Mitigation Strategies For RFID Security And Privacy Concerns. This template helps you present information on seven stages. You can also present information on Physical Protection, Deploy Access Control, Use Shielding, Use Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies For Cyber Security Gamification To Engage Employees
Strategies For Cyber Security Gamification To Engage EmployeesThe purpose of this slide is to create comprehensive and engaging cybersecurity gamification program that enhances employee awareness also actively contributes to a more secure digital environment including strategies such as utilization of security badges, reliance on digital date, etc. Introducing our premium set of slides with name Strategies For Cyber Security Gamification To Engage Employees. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Utilization Of Security Badges, Rely On Digital Data, Cyber Security Gamification. So download instantly and tailor it with your information.
-
 Strategies For Identifying Security Vulnerability In Network
Strategies For Identifying Security Vulnerability In NetworkFollowing slide represents identifying tactics of vulnerabilities in security network for improving data structure. It further covers run network audit, analyse system log data and audit IT supply chain. Presenting our set of slides with Strategies For Identifying Security Vulnerability In Network This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Run Network Audit, Analyse System Log Data, Audit IT Supply Chain
-
 Website Design Security Management Strategic Plan Comprehensive E Commerce Website
Website Design Security Management Strategic Plan Comprehensive E Commerce WebsiteFollowing slide outlines website security action plan to assure safety from external threats and cybercrimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Deliver an outstanding presentation on the topic using this Website Design Security Management Strategic Plan Comprehensive E Commerce Website Dispense information and present a thorough explanation of Set Strong Passwords, Try New Configurations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Website Security Management Strategic Plan Comprehensive E Commerce Website
Website Security Management Strategic Plan Comprehensive E Commerce WebsiteFollowing slide outlines website security action plan to assure safety from external threats and cybercrimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Increase audience engagement and knowledge by dispensing information using Website Security Management Strategic Plan Comprehensive E Commerce Website This template helps you present information on Five stages. You can also present information on Strategy, Responsible Person, Priority Status using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Securing Food Safety In Online Adopting Insulated Food Packaging Strategy
Securing Food Safety In Online Adopting Insulated Food Packaging StrategyThis slide covers integrating insulated food packaging strategy to utilize its core functions such as temperature maintenance, extended delivery area and diverse menu options. Introducing Securing Food Safety In Online Adopting Insulated Food Packaging Strategy to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Temperature Maintenance, Leak Resistant Packaging, Proper Sizing, using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Strategies For Selecting The Right Food Packaging Material
Securing Food Safety In Online Strategies For Selecting The Right Food Packaging MaterialThis slide covers strategies for selecting right food material to enhance customer satisfaction which involves components such as sustainability, personalization and minimalistic. Present the topic in a bit more detail with this Securing Food Safety In Online Strategies For Selecting The Right Food Packaging Material. Use it as a tool for discussion and navigation on Sustainability, Personalized, Minimalistic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Strategies To Improve Food Delivery Process In Restaurants
Securing Food Safety In Online Strategies To Improve Food Delivery Process In RestaurantsThis slide covers implementing strategies to enhance delivery efficiency such as prioritizing orders, creating counter for drivers and leveraging feedback from team. Introducing Securing Food Safety In Online Strategies To Improve Food Delivery Process In Restaurants to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Prioritize Orders, Create Counter For Delivery Partners, Assess Feedback From Team, using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Strategies To Mitigate Food Delivery Challenges Faced
Securing Food Safety In Online Strategies To Mitigate Food Delivery Challenges FacedThis slide covers strategies to mitigate challenges faced by restaurant business such as third party integrations, innovative packaging, route optimization software and cyber security measures. Introducing Securing Food Safety In Online Strategies To Mitigate Food Delivery Challenges Faced to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Challenges, Innovative Packaging, Technology Integrations, using this template. Grab it now to reap its full benefits.
-
 Wealth Management Strategies Secure Retirement Planning With Key Fin SS V
Wealth Management Strategies Secure Retirement Planning With Key Fin SS VThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Introducing Wealth Management Strategies Secure Retirement Planning With Key Fin SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Lifestyle Assessment, Retirement Income Projection, Savings Strategies, Pension Optimization, using this template. Grab it now to reap its full benefits.
-
 Comprehensive Blockchain Security Strategy Plan
Comprehensive Blockchain Security Strategy PlanIntroducing our premium set of slides with Comprehensive Blockchain Security Strategy Plan. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Goals, Streamline Operations, Assess Hardware. So download instantly and tailor it with your information.
-
 Strategies To Train Employees On Cyber Security Ethics
Strategies To Train Employees On Cyber Security EthicsThis slide represents various strategies that assists corporate companies to provide training on ethical cyber security for enhancing data protection. It includes strategies such as assessment and planning, establishing ethical guidelines, etc. Introducing our Strategies To Train Employees On Cyber Security Ethics set of slides. The topics discussed in these slides are Strategies, Assessment And Planning, Establish Ethical Guidelines. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Optimize OT Cyber Security
Strategies To Optimize OT Cyber SecurityThis slide represents various strategies that assist companies to enhance their OT cyber security with ICS products effectively. It includes various strategies such as host security, security monitoring, physical security, etc. Introducing our premium set of slides with Strategies To Optimize OT Cyber Security Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Host Security, Physical Security, Security Monitoring So download instantly and tailor it with your information.
-
 Strategies To Secure Digital Banking Channels
Strategies To Secure Digital Banking ChannelsThe purpose of this slide is to help banking professionals secure digital channels for prevention of potential threats. It covers security solutions for various threats such as phishing, ransomware, advanced persistent threats, etc. Introducing our premium set of slides with Strategies To Secure Digital Banking Channels. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threats,Phishing,Ransomware.So download instantly and tailor it with your information.
-
 Best Strategies For Creating Security Awareness Mobile Security
Best Strategies For Creating Security Awareness Mobile SecurityThis slide represents the best strategies for creating culture of mobile security awareness which includes educate workforce on mobile security, etc. Increase audience engagement and knowledge by dispensing information using Best Strategies For Creating Security Awareness Mobile Security This template helps you present information on Five stages. You can also present information on Enable Authentication In App, Device Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Technology Strategies For Fintech Cyber Security
Best Technology Strategies For Fintech Cyber SecurityThis slide showcases the best technologies to choose for fintech security management. Its aim is to prioritise the resources and execute the best strategy. This slide includes governance, risk, crisis, service, threat, access, privacy, etc. Presenting our set of slides with name Best Technology Strategies For Fintech Cyber Security. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance Strategy, Emerging Trends, Risk Compliance, Crisis Management .
-
 Strategies To Mitigate Cyber Security Risks In Banking Sector
Strategies To Mitigate Cyber Security Risks In Banking SectorThis slide represents approaches to reduce risk of cyber security in banking sector. This template aims to cyber security risks in banking sector to protect sensitive financial data and maintain customer trust. It includes various strategies such as risk determination, mitigating identity theft and fraud, etc. Introducing our premium set of slides with Strategies To Mitigate Cyber Security Risks In Banking Sector. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Privacy Protection, Application Control, Risk Determination. So download instantly and tailor it with your information.
-
 Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS
Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SSThis slide represents training plan for verifying identity of user accessing a digital system. It includes details related to password authentication methods, training sessions etc. Deliver an outstanding presentation on the topic using this Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Token Authentication, Biometric Authentication, Strategic Password, Authentication Training Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





