Powerpoint Templates and Google slides for Security Software
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Real time analysis of security alerts next evolution of siem software
Real time analysis of security alerts next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Real Time Analysis Of Security Alerts Next Evolution Of Siem Software. This template helps you present information on six stages. You can also present information on Endpoint Monitoring, Network Traffic Analysis, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Real time analysis of security alerts software challenges with solutions
Real time analysis of security alerts software challenges with solutionsThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Present the topic in a bit more detail with this Real Time Analysis Of Security Alerts Software Challenges With Solutions. Use it as a tool for discussion and navigation on Limitations, Responsiveness, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Hardware And Software Update In Company
Information Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Introducing Information Security Hardware And Software Update In Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Introduce, Hardware, Software using this template. Grab it now to reap its full benefits.
-
 Development operations skills software security skills
Development operations skills software security skillsThis slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Introducing Development Operations Skills Software Security Skills to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Training, Code Analysis, Change Management, using this template. Grab it now to reap its full benefits.
-
 Threat management for organization critical selecting secured threat management software
Threat management for organization critical selecting secured threat management softwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Threat Management For Organization Critical Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Security Incident, Automated Workflows, Customize Ownership. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management selecting secured threat management software
Cyber security risk management selecting secured threat management softwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Cyber Security Risk Management Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Centralized Platform, Security Incident Forms, Access Rights, API Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management software challenges with solutions
Improve it security with vulnerability management software challenges with solutionsThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Software Challenges With Solutions. Use it as a tool for discussion and navigation on Workforce Limitations, Responsiveness, Limitations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability management key features of siem software
Improve it security with vulnerability management key features of siem softwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Key Features Of Siem Software. This template helps you present information on seven stages. You can also present information on Comprehensive, Compliance, Classification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability management need for siem software company
Improve it security with vulnerability management need for siem software companyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Introducing Improve It Security With Vulnerability Management Need For Siem Software Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Detecting Incidents, Compliance With Regulations, Efficient Incident Management, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management next evolution of siem software
Improve it security with vulnerability management next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Next Evolution Of Siem Software. This template helps you present information on six stages. You can also present information on Foundation, Threat Intelligence, Analytics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Hardware And Software Update In Company
Information Technology Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Increase audience engagement and knowledge by dispensing information using Information Technology Security Hardware And Software Update In Company. This template helps you present information on three stages. You can also present information on Hardware And Software Update In Company using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advantages And Working Of Secure Sdlc Software Development Life Cycle It
Advantages And Working Of Secure Sdlc Software Development Life Cycle ItThis slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Present the topic in a bit more detail with this Advantages And Working Of Secure Sdlc Software Development Life Cycle It. Use it as a tool for discussion and navigation on Organizations, Commercial, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Importance Of Secure Sdlc Software Development Life Cycle It
Overview And Importance Of Secure Sdlc Software Development Life Cycle ItThis slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost. Deliver an outstanding presentation on the topic using this Overview And Importance Of Secure Sdlc Software Development Life Cycle It. Dispense information and present a thorough explanation of Secure, Development, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem For Security Analysis Key Features Of Siem Software
Siem For Security Analysis Key Features Of Siem SoftwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Introducing Siem For Security Analysis Key Features Of Siem Software to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Enrichment, Classification, Software, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Need For Siem Software In Your Company
Siem For Security Analysis Need For Siem Software In Your CompanyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Increase audience engagement and knowledge by dispensing information using Siem For Security Analysis Need For Siem Software In Your Company. This template helps you present information on three stages. You can also present information on Detecting Incidents, Compliance, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem For Security Analysis Next Evolution Of Siem Software
Siem For Security Analysis Next Evolution Of Siem SoftwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Introducing Siem For Security Analysis Next Evolution Of Siem Software to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Next Evolution Of SIEM Software, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Software Challenges With Solutions
Siem For Security Analysis Software Challenges With SolutionsThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Deliver an outstanding presentation on the topic using this Siem For Security Analysis Software Challenges With Solutions. Dispense information and present a thorough explanation of Workforce, Limitations, Responsiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Add Roles And Enable Security Planning And Implementation Crm Software
Implementation Add Roles And Enable Security Planning And Implementation Crm SoftwareThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Implementation Add Roles And Enable Security Planning And Implementation Crm Software. Use it as a tool for discussion and navigation on Implementation Add Roles And Enable Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Planning And Implementation Of Crm Software Securing Our Data With Crm
Planning And Implementation Of Crm Software Securing Our Data With CrmThis slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. Deliver an outstanding presentation on the topic using this Planning And Implementation Of Crm Software Securing Our Data With Crm. Dispense information and present a thorough explanation of User Role Based Security, Profile Based Security, Record Sharing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With Crm Planning And Implementation Of Crm Software
Securing Our Data With Crm Planning And Implementation Of Crm SoftwareThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Present the topic in a bit more detail with this Securing Our Data With Crm Planning And Implementation Of Crm Software. Use it as a tool for discussion and navigation on Securing Our Data With CRM. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Selecting Secured Threat Management Software
Vulnerability Administration At Workplace Selecting Secured Threat Management SoftwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Management, Software, Workflows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Home Operating System Integration Home Security Systems Company Profile
Smart Home Operating System Integration Home Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Home Security Systems Company Profile . Dispense information and present a thorough explanation of Smart Home Operating System Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
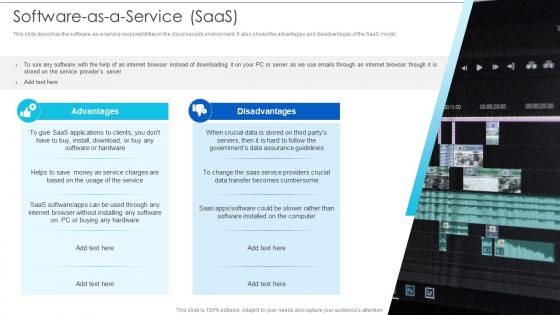 Software As A Service SaaS Cloud Information Security
Software As A Service SaaS Cloud Information SecurityThis slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model.Deliver an outstanding presentation on the topic using this Software As A Service SaaS Cloud Information Security Dispense information and present a thorough explanation of Security Is Important, Cloud Security, Security Different using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Steps Enable Data Security Crm Software Deployment Guide
Implementation Steps Enable Data Security Crm Software Deployment GuideThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm Software Deployment Guide. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Computing Security Software As A Service Saas Ppt Icons
Cloud Computing Security Software As A Service Saas Ppt IconsThis slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Deliver an outstanding presentation on the topic using this Cloud Computing Security Software As A Service Saas Ppt Icons. Dispense information and present a thorough explanation of Data Assurance, Service, Service Charges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Smart Security Systems Company Profile
Smart Home Operating System Integration Smart Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Smart Security Systems Company Profile. Dispense information and present a thorough explanation of Integration, Automation, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile
Smart Home Operating System Integration Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile. Dispense information and present a thorough explanation of Integration, Automation, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Advantages And Working Of Secure SDLC Software Development Process
Advantages And Working Of Secure SDLC Software Development ProcessThis slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Introducing Advantages And Working Of Secure SDLC Software Development Process to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security Planning, Existing Development, Design And Development, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Secure SDLC Software Development Process
Overview And Importance Of Secure SDLC Software Development ProcessThis slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Secure SDLC Software Development Process. This template helps you present information on two stages. You can also present information on Importance Of SDL, Overview Of SDL using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Add Roles And Enable Security Crm Software Implementation
Implementation Add Roles And Enable Security Crm Software ImplementationThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Implementation Add Roles And Enable Security Crm Software Implementation. Use it as a tool for discussion and navigation on Implementation, Generation, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Collaboration Software Ppt Powerpoint Presentation Slides Example Cpb
Secure Collaboration Software Ppt Powerpoint Presentation Slides Example CpbPresenting our Secure Collaboration Software Ppt Powerpoint Presentation Slides Example Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secure Collaboration Software. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Smart Home Operating System Integration Wireless Home Security Systems Company Profile
Smart Home Operating System Integration Wireless Home Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Introducing Smart Home Operating System Integration Wireless Home Security Systems Company Profile to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispense information on Smart Home Operating, System Integration, using this template. Grab it now to reap its full benefits.
-
 Comparison Of Various Cyber Security Software
Comparison Of Various Cyber Security SoftwareThis slide shows comparative analysis of various cyber security tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Presenting our well structured Comparison Of Various Cyber Security Software. The topics discussed in this slide are Software, Features, Compatibility, Price, Ratings. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparison Of Various Security Awareness Training Software Developing Cyber Security Awareness
Comparison Of Various Security Awareness Training Software Developing Cyber Security AwarenessThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Developing Cyber Security Awareness. Dispense information and present a thorough explanation of Comparison Of Various, Security Awareness, Training Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Selecting Suitable Software For Information Security Risk Management
Selecting Suitable Software For Information Security Risk ManagementThis slide showcases software that can help organization to monitor and manage the risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Deliver an outstanding presentation on the topic using this Selecting Suitable Software For Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Risk Quantification, Vulnerability Management, Selecting Suitable Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Architecture And Security Review Software Defined Perimeter Solution Infrastructure
Cloud Architecture And Security Review Software Defined Perimeter Solution InfrastructureThis slide covers Network that Prevention Cyber Attacks with a Software Defined Perimeter which reduces the attack surface area by hiding network resources from unauthorized or unauthenticated users. Present the topic in a bit more detail with this Cloud Architecture And Security Review Software Defined Perimeter Solution Infrastructure. Use it as a tool for discussion and navigation on Software, Defined Perimeter, Solution Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Spending On Security Software Against Web Attacks
Spending On Security Software Against Web AttacksThis slide defines the spending by different enterprises for security software against web attacks. It includes information related to the following security network, endpoint, messaging, web etc. Introducing our Spending On Security Software Against Web Attacks set of slides. The topics discussed in these slides are Network Security, Endpoint Security, Messaging Security, Web Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison Of Various Security Awareness Training Software Conducting Security Awareness
Comparison Of Various Security Awareness Training Software Conducting Security AwarenessThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Conducting Security Awareness. Dispense information and present a thorough explanation of Key Features, Phishing Simulations, Security Reporting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Software Security Skills Devops Skills Ppt Styles Slide Download
Software Security Skills Devops Skills Ppt Styles Slide DownloadThis slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Introducing Software Security Skills Devops Skills Ppt Styles Slide Download to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Management, Threat Investigation, Compliance Monitoring , using this template. Grab it now to reap its full benefits.
-
 C15 Selecting Suitable Software For Information Security Risk Management Ppt Styles Background Image
C15 Selecting Suitable Software For Information Security Risk Management Ppt Styles Background ImageThis slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Present the topic in a bit more detail with this C15 Selecting Suitable Software For Information Security Risk Management Ppt Styles Background Image. Use it as a tool for discussion and navigation on Cyber Risk Quantification, Vulnerability Management, Centralized Repository For Assets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt Graphics
Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt GraphicsThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Introducing Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt Graphics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comparative Analysis, Cyber Security, Mitigation Software, using this template. Grab it now to reap its full benefits.
-
 Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management Plan
Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Present the topic in a bit more detail with this Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Software, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Security Reporting, Phishing Simulations, Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Software Defined Networking And Security Software Defined Networking IT
Software Defined Networking And Security Software Defined Networking ITThis slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Present the topic in a bit more detail with this Software Defined Networking And Security Software Defined Networking IT. Use it as a tool for discussion and navigation on Infrastructure Security, Controller Security, Software Defined Networking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 What Role Does SDN Play In Customer Security Software Defined Networking IT
What Role Does SDN Play In Customer Security Software Defined Networking ITThis slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Introducing What Role Does SDN Play In Customer Security Software Defined Networking IT to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Provides Several, Cybersecurity Advantages, Customer Security, using this template. Grab it now to reap its full benefits.
-
 Competitive Matrix Analysis Of Security Software
Competitive Matrix Analysis Of Security SoftwareThis slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Introducing our Competitive Matrix Analysis Of Security Software set of slides. The topics discussed in these slides are Antivirus, Firewall. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security And Compliance Software Layers Architecture
Security And Compliance Software Layers ArchitectureThe following slide displays security management software layers architecture for organization. It includes elements such as cloud manager, virtual in restructure, physical, business continuity, etc. Introducing our Security And Compliance Software Layers Architecture set of slides. The topics discussed in these slides are Service Management, Portfolio Management, Operations Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Software Implementation Project Planning Icon
Security Software Implementation Project Planning IconIntroducing our premium set of slides with Security Software Implementation Project Planning Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Software Implementation, Project Planning Icon. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Software Implementation
Cyber Security Incident Response Software ImplementationThis slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost.Introducing our Cyber Security Incident Response Software Implementation set of slides. The topics discussed in these slides are Identification Management, Risk Management, Containment Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Software Checklist To Respond Cyber Security Incidents
Software Checklist To Respond Cyber Security IncidentsThis slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc.Presenting our well structured Software Checklist To Respond Cyber Security Incidents. The topics discussed in this slide are Confidential Information, Misleading Advertising, Hacker Changed. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Public WIFI Security Software In Powerpoint And Google Slides Cpb
Public WIFI Security Software In Powerpoint And Google Slides CpbPresenting Public WIFI Security Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Public WIFI Security Software. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Software Programs In Powerpoint And Google Slides Cpb
Security Software Programs In Powerpoint And Google Slides CpbPresenting Security Software Programs In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Software Programs. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Software Supply Chain Security Comparative Analysis
Software Supply Chain Security Comparative AnalysisThe following slide highlights comparative analysis of software supply chain security to track vulnerabilities, risk prevention etc. It includes elements such as software, capabilities, budget, free trial and rating. Presenting our well structured Software Supply Chain Security Comparative Analysis The topics discussed in this slide are Vulnerability Mitigation, Security Strategy Assessment This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Software Supply Chain Security Icon
Software Supply Chain Security IconPresenting our set of slides with Software Supply Chain Security Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Supply, Chain Security Icon
-
 Best Home Computer Security Software In Powerpoint And Google Slides Cpb
Best Home Computer Security Software In Powerpoint And Google Slides CpbPresenting Best Home Computer Security Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Home Computer Security Software. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview
Selecting Secured Threat Management Software Managing IT Threats At Workplace OverviewThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Secured, Management, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And Innovation
Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And InnovationThis slide covers the current situation of cloud computing and software covering new opportunities and innovation for those willing to implement the change. Introducing Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And Innovation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Computing, Software Opportunities, Innovation, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy Software Usage Policy Objective And General Guidelines
Cyber Security Policy Software Usage Policy Objective And General GuidelinesThis slide depicts the software usage policy, including its objective, general guidelines, and compliance. This policy covers the instructions regarding both paid and free software. Deliver an outstanding presentation on the topic using this Cyber Security Policy Software Usage Policy Objective And General Guidelines. Dispense information and present a thorough explanation of Software, Organizational Computers, Corporate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Team Communication Plan Software For Large Events
Security Team Communication Plan Software For Large EventsThis slide presents major communication software which can be used by security teams to manage communication in large events. The elements covered are software name, features, integrations and pricing.Presenting our well structured Security Team Communication Plan Software For Large Events. The topics discussed in this slide are Troop Messenger, Integrations, Community Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.





