Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data security it types of threats in data security ppt slides graphic tips
Data security it types of threats in data security ppt slides graphic tipsThis slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Data Security IT Types Of Threats In Data Security Ppt Slides Graphic Tips. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack, Cause Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data security it what are the benefits of data security
Data security it what are the benefits of data securityThis slide depicts the different benefits of deploying a data security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Increase audience engagement and knowledge by dispensing information using Data Security IT What Are The Benefits Of Data Security. This template helps you present information on five stages. You can also present information on Legitimate Traffic, Hardware Security Devices, Threats And Risks, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data security it what is data security and how does it work
Data security it what is data security and how does it workThis slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Introducing Data Security IT What Is Data Security And How Does IT Work to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Collective Methods, Protect Data, Computer Systems, Networks, Servers And Mobile Devices, using this template. Grab it now to reap its full benefits.
-
 Computer system security elements of computer security disaster recovery planning
Computer system security elements of computer security disaster recovery planningThis slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Introducing Computer System Security Elements Of Computer Security Disaster Recovery Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Business, Technology, Administration, Budget, Resources, Financial, using this template. Grab it now to reap its full benefits.
-
 Computer system security main principle of information security
Computer system security main principle of information securityThis slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Present the topic in a bit more detail with this Computer System Security Main Principle Of Information Security. Use it as a tool for discussion and navigation on Confidentiality, Integrity, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security managing computer security 90 days plan
Computer system security managing computer security 90 days planThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Computer System Security Managing Computer Security 90 Days Plan. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security security framework in cloud computing
Computer system security security framework in cloud computingThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Increase audience engagement and knowledge by dispensing information using Computer System Security Security Framework In Cloud Computing. This template helps you present information on five stages. You can also present information on Identify, Protect, Detect, Respond, Recover using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
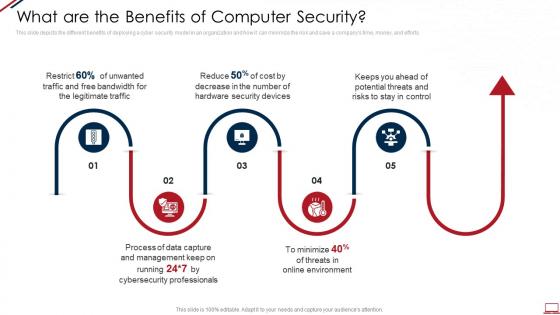 Computer system security what are the benefits of computer security
Computer system security what are the benefits of computer securityThis slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Increase audience engagement and knowledge by dispensing information using Computer System Security What Are The Benefits Of Computer Security. This template helps you present information on five stages. You can also present information on Management, Process, Security Devices, Potential Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Elements of computer security end user education computer system security
Elements of computer security end user education computer system securityThis slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Introducing Elements Of Computer Security End User Education Computer System Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Social Media, Protection Measures, Security Threat, Cyber Security, using this template. Grab it now to reap its full benefits.
-
 Elements of computer security information security computer system security
Elements of computer security information security computer system securityThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Increase audience engagement and knowledge by dispensing information using Elements Of Computer Security Information Security Computer System Security. This template helps you present information on three stages. You can also present information on Confidentiality, Integrity, Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Elements of computer security network security computer system security
Elements of computer security network security computer system securityThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Introducing Elements Of Computer Security Network Security Computer System Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Firewalls, Web Security, Email Security, Virtual Private Network, End Point Security, using this template. Grab it now to reap its full benefits.
-
 Elements of computer security operational security computer system security
Elements of computer security operational security computer system securityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Elements Of Computer Security Operational Security Computer System Security. This template helps you present information on five stages. You can also present information on Change Management Processes, Deploy Automation, Plan For Disaster, Restrict Device Access, Implement Dual Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table of contents for computer system security cont computer system security
Table of contents for computer system security cont computer system securityPresent the topic in a bit more detail with this Table Of Contents For Computer System Security Cont Computer System Security. Use it as a tool for discussion and navigation on Computer Security, Implementation, Roadmap Or Timeline, Business, Budget. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security common methods used to threaten computer security
Computer system security common methods used to threaten computer securityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Increase audience engagement and knowledge by dispensing information using Computer System Security Common Methods Used To Threaten Computer Security. This template helps you present information on five stages. You can also present information on Malware, Daniel Of Service, Man In The Middle, SQL Injection, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
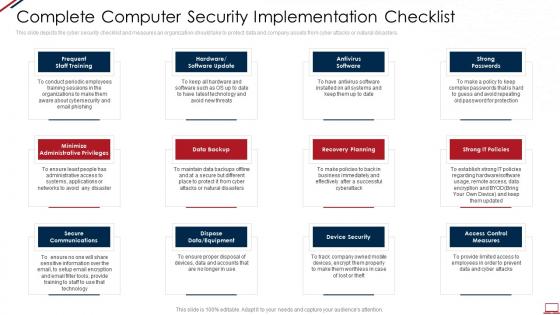 Computer system security complete computer security implementation checklist
Computer system security complete computer security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Computer System Security Complete Computer Security Implementation Checklist. This template helps you present information on twelve stages. You can also present information on Data Backup, Secure Communications, Recovery Planning, Strong Passwords, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security compliance dashboard Snapshot of computer security
Computer system security compliance dashboard Snapshot of computer securityThis slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Present the topic in a bit more detail with this Computer System Security Compliance Dashboard Snapshot Of Computer Security. Use it as a tool for discussion and navigation on Asset Type Control, Control Issues By Standard, Control Issues By Regulation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security computer security awareness training for staff
Computer system security computer security awareness training for staffThis slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an outstanding presentation on the topic using this Computer System Security Computer Security Awareness Training For Staff. Dispense information and present a thorough explanation of Senior Executives, Project Managers, IT Teams, Front Line Staff, Developers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
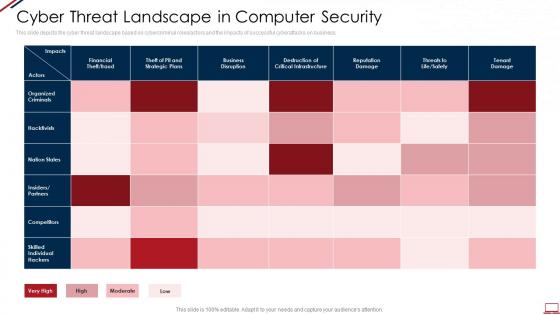 Computer system security cyber threat landscape in computer security
Computer system security cyber threat landscape in computer securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Computer System Security Cyber Threat Landscape In Computer Security. Use it as a tool for discussion and navigation on Financial, Business, Tenant Damage, Organized Criminals, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security elements of computer security cloud security
Computer system security elements of computer security cloud securityThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Introducing Computer System Security Elements Of Computer Security Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Insecure Apis, Account Hijacking, Malicious Insiders, Malware Injections, Data Breaches, using this template. Grab it now to reap its full benefits.
-
 Computer system security how is automation used in computer security
Computer system security how is automation used in computer securityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Computer System Security How Is Automation Used In Computer Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Computer system security impact on organization after implementing computer security strategy and training
Computer system security impact on organization after implementing computer security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Increase audience engagement and knowledge by dispensing information using Computer System Security Impact On Organization After Implementing Computer Security Strategy And Training. This template helps you present information on five stages. You can also present information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
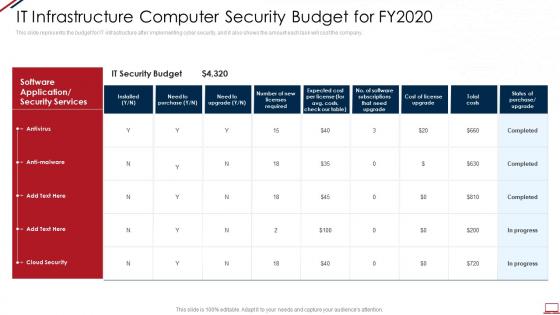 Computer system security it infrastructure computer security budget for fy2020
Computer system security it infrastructure computer security budget for fy2020This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Computer System Security It Infrastructure Computer Security Budget For Fy2020. Use it as a tool for discussion and navigation on Cost, IT Security Budget, Software Application Or Security Services, Antivirus, Anti Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
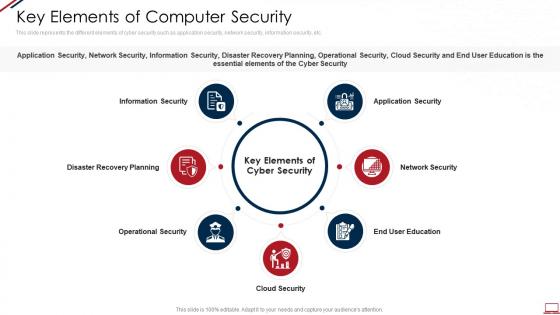 Computer system security key elements of computer security
Computer system security key elements of computer securityThis slide represents the different elements of cyber security such as application security, network security, information security, etc. Introducing Computer System Security Key Elements Of Computer Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Information Security, Disaster Recovery Planning, Operational Security, Cloud Security, Network Security, using this template. Grab it now to reap its full benefits.
-
 Computer system security latest threats in computer security
Computer system security latest threats in computer securityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Increase audience engagement and knowledge by dispensing information using Computer System Security Latest Threats In Computer Security. This template helps you present information on three stages. You can also present information on Dridex Malware, Romance Scams, Emotet Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security main steps of operational security
Computer system security main steps of operational securityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Introducing Computer System Security Main Steps Of Operational Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assessment Of Risks, Analyze Security Holes And Vulnerabilities, Potential Threats, Sensitive Information, Implementation Of Appropriate Countermeasures, using this template. Grab it now to reap its full benefits.
-
 Computer system security managing computer security 60 days plan
Computer system security managing computer security 60 days planThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Computer System Security Managing Computer Security 60 Days Plan. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security roadmap for computer security training
Computer system security roadmap for computer security trainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Computer System Security Roadmap For Computer Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ensuring Physical Security, Ensuring, Data Security, Mobile And Remote Computing, Safe And Computing, Security And Privacy Threats, using this template. Grab it now to reap its full benefits.
-
 Computer system security security of employees devices
Computer system security security of employees devicesThis slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Introducing Computer System Security Security Of Employees Devices to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security Of Employees Devices, using this template. Grab it now to reap its full benefits.
-
 Computer system security set measures for secure communication
Computer system security set measures for secure communicationThis slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Increase audience engagement and knowledge by dispensing information using Computer System Security Set Measures For Secure Communication. This template helps you present information on six stages. You can also present information on Technology, Training, Organization, Data Transfer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security types of threats in computer security
Computer system security types of threats in computer securityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Computer System Security Types Of Threats In Computer Security. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security what is computer security and how does it work
Computer system security what is computer security and how does it workThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Computer System Security What Is Computer Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Techniques, Collective, Networks, Computer Systems, using this template. Grab it now to reap its full benefits.
-
 Elements of computer security application security computer system security
Elements of computer security application security computer system securityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Introducing Elements Of Computer Security Application Security Computer System Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Developers, Weaknesses, Cyber Security, Management, Input Validation, using this template. Grab it now to reap its full benefits.
-
 Managing computer security 30 days plan computer system security
Managing computer security 30 days plan computer system securityPresent the topic in a bit more detail with this Managing Computer Security 30 Days Plan Computer System Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Threats Cyber Security In Powerpoint And Google Slides Cpb
Security Threats Cyber Security In Powerpoint And Google Slides CpbPresenting Security Threats Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Threats Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
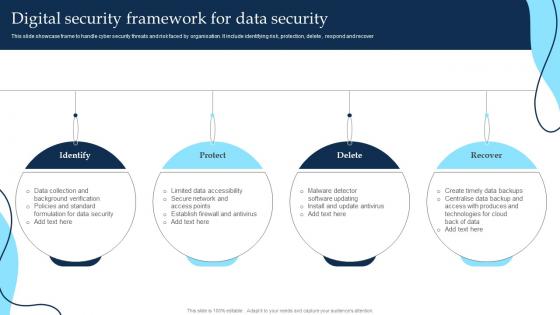 Digital Security Framework For Data Security
Digital Security Framework For Data SecurityThis slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete, respond and recover Presenting our set of slides with Digital Security Framework For Data Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Protect, Recover.
-
 Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security Model
Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security ModelThis slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Deliver an outstanding presentation on the topic using this Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security Model. Dispense information and present a thorough explanation of Comparison, Architecture, Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Features Of Zero Trust Network Access Security Model Zero Trust Security Model
Features Of Zero Trust Network Access Security Model Zero Trust Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Organizations, Applications, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model
Role Of ZTNA To Improve Business Operations And Security Zero Trust Security ModelThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Deliver an outstanding presentation on the topic using this Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced User Experience, Remote Workforce Protection, Improve Data Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model
Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security ModelThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Deliver an outstanding presentation on the topic using this Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model. Dispense information and present a thorough explanation of Traditional, Overview, Limitations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model
Traditional Security Models Vs Zero Trust Network Access Zero Trust Security ModelThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Present the topic in a bit more detail with this Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Dependence, Foundation, Attack Surface. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SS
Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SSThe following slide depicts timeline showcasing innovations in security token offerings to gain insights key improvements and evolution. It includes elements such as blockchain capital, spice VC, open finance network, aspen coin, tZERO, etc. Present the topic in a bit more detail with this Brief Evolution Timeline Of Security Token Offerings Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Brief Evolution Timeline, Security Token Offerings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Define Security Token Project Business Model Security Token Offerings BCT SS
Define Security Token Project Business Model Security Token Offerings BCT SSThe following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. Present the topic in a bit more detail with this Define Security Token Project Business Model Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Project, Overview, Tokenization Model, Revenue Streams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Develop Security Token Offering Plan Security Token Offerings BCT SS
Develop Security Token Offering Plan Security Token Offerings BCT SSThe following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Introducing Develop Security Token Offering Plan Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Completion Of Tokenization Process, Offering Plan, using this template. Grab it now to reap its full benefits.
-
 Key Opportunities Driving Growth Of Security Token Offerings Security Token Offerings BCT SS
Key Opportunities Driving Growth Of Security Token Offerings Security Token Offerings BCT SSThe following slide showcases various success factors driving growth of security token offerings STO adoption to insure success of. It includes elements such as ecosystem, credibility, regulation, investors literacy, etc. Increase audience engagement and knowledge by dispensing information using Key Opportunities Driving Growth Of Security Token Offerings Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Regulation, Credibility, Investor Literacy, Sto Ecosystem using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SS
Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SSThe following slide showcases the major issues in future development of security tokens to boost early stage adoption. It includes elements such as no uniformity, legal protection, regulations, manual processes, valuation, anti-money laundering, etc. Introducing Major Challenges In Future Development Of Security Token Offerings Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Legal Protection, Manual Process, Valuation, Anti Money Laundering, using this template. Grab it now to reap its full benefits.
-
 Major Cons Of Security Token Offerings Security Token Offerings BCT SS
Major Cons Of Security Token Offerings Security Token Offerings BCT SSThe following slide illustrates major challenges faced by users of security token offerings STOs to minimize the burden and optimize efficiency. It includes elements such as uncertainties, market adoption, security issues, valuation, etc. Increase audience engagement and knowledge by dispensing information using Major Cons Of Security Token Offerings Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Uncertainties, Market Adoption, Security Issues, Valuation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Pros Of Security Token Offerings Security Token Offerings BCT SS
Major Pros Of Security Token Offerings Security Token Offerings BCT SSThe following slide highlights the various advantages of security token offerings STOs to ensure easy security transfer and fund raising. It includes elements such as transparency, instant settlement, availability, divisibility, etc. Introducing Major Pros Of Security Token Offerings Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transparency, Instant Settlement, Availability, Divisibility, using this template. Grab it now to reap its full benefits.
-
 Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SS
Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SSThe following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc. Introducing Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Showcases Ownership, Security Regulations, Overview, using this template. Grab it now to reap its full benefits.
-
 Successful Security Token Offering Project Case Study Blockchain Security Token Offerings BCT SS
Successful Security Token Offering Project Case Study Blockchain Security Token Offerings BCT SSThe following slide focusses on blockchain capital security token offerings STO project to encourage more digital assets. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Increase audience engagement and knowledge by dispensing information using Successful Security Token Offering Project Case Study Blockchain Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Launched, Amount Raised, Features, Generated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Successful Security Token Offering Project Case Study Lottery Com Security Token Offerings BCT SS
Successful Security Token Offering Project Case Study Lottery Com Security Token Offerings BCT SSThe following slide depicts some key insights about lottery.com security token offerings STO to foster new trading of securities. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Introducing Successful Security Token Offering Project Case Study Lottery Com Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Launched, Amount Raised, Features, Generated, using this template. Grab it now to reap its full benefits.
-
 Successful Security Token Offering Project Case Study Polymath Security Token Offerings BCT SS
Successful Security Token Offering Project Case Study Polymath Security Token Offerings BCT SSThe following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Increase audience engagement and knowledge by dispensing information using Successful Security Token Offering Project Case Study Polymath Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Launched, Amount Raised, Features, Generated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Successful Security Token Offering Project Case Study Spice VC Security Token Offerings BCT SS
Successful Security Token Offering Project Case Study Spice VC Security Token Offerings BCT SSThe following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Introducing Successful Security Token Offering Project Case Study Spice VC Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Launched, Amount Raised, Features, Generated, using this template. Grab it now to reap its full benefits.
-
 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway
30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web GatewayThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Compatible, Performance, Production, using this template. Grab it now to reap its full benefits.
-
 Agenda Network Security Using Secure Web Gateway
Agenda Network Security Using Secure Web GatewayIncrease audience engagement and knowledge by dispensing information using Agenda Network Security Using Secure Web Gateway. This template helps you present information on seven stages. You can also present information on Protection, Businesses, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Applications Of Secure Web Gateway In Various Industries Network Security Using Secure Web Gateway
Applications Of Secure Web Gateway In Various Industries Network Security Using Secure Web GatewayThis slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Present the topic in a bit more detail with this Applications Of Secure Web Gateway In Various Industries Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Applications, Financial Services, Education. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web Gateway
Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Deliver an outstanding presentation on the topic using this Architecture Of Citrix Secure Web Gateway Proxy Solution Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Architecture, Company Complaint Internal, Malware Restricted Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway
Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web GatewayThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Productivity, Enforcement, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway
Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Deliver an outstanding presentation on the topic using this Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Assessment, Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Citrix Solutions To Safeguard Network Security Using Secure Web Gateway
Case Study Citrix Solutions To Safeguard Network Security Using Secure Web GatewayThis slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Present the topic in a bit more detail with this Case Study Citrix Solutions To Safeguard Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Organizational, Solutions, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.





