Powerpoint Templates and Google slides for Security Rules
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Firewall Migration Proposal Our Process For Migrating Firewall Network Security
Firewall Migration Proposal Our Process For Migrating Firewall Network SecurityThis slide outlines the process of a firewall service provider company to replace a legacy firewall solution with a new one in an organization. The process steps include assessment and requirements gathering, solution design and planning, pre-migration preparation, etc. Present the topic in a bit more detail with this Firewall Migration Proposal Our Process For Migrating Firewall Network Security. Use it as a tool for discussion and navigation on Assessment And Requirements Gathering, Solution Design And Planning, Migration Execution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Inherited Ira Withdrawal Rules Secure Act In Powerpoint And Google Slides Cpb
Inherited Ira Withdrawal Rules Secure Act In Powerpoint And Google Slides CpbPresenting Inherited Ira Withdrawal Rules Secure Act In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Inherited Ira Withdrawal Rules Secure Act This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Establish Effective Internet Security Protocols In Network Layer
Establish Effective Internet Security Protocols In Network LayerThis slide exhibits network layer security architecture for providing virtual private network between two locations. It includes protocols such as encapsulating security payload, authentication header and internet key exchange. Presenting our set of slides with Establish Effective Internet Security Protocols In Network Layer. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Header, Authentication Methods, Encapsulating Security Payload.
-
 Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V
Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Audit Process For Digital Ecosystem
Cyber Security Audit Process For Digital EcosystemThis slide elaborates on cybersecurity audit process and provides details about how to implement protection in a digital ecosystem. It includes elements such as build blueprint, audit frequently, etc. Presenting our set of slides with Cyber Security Audit Process For Digital Ecosystem. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Audit Purpose, Build Blueprint, Identify Evaluate Risk Management.
-
 NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V
NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V. Dispense information and present a thorough explanation of Authentication Process Flow, Enhanced Security, Verify Biometrics, Authentication Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Deposit Rules In Powerpoint And Google Slides Cpb
Security Deposit Rules In Powerpoint And Google Slides CpbPresenting our Security Deposit Rules In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Deposit Rules. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Content Automation Protocol Specifications
Security Content Automation Protocol SpecificationsThis slide represents the protocol specifications of security content automation which enables organisations to automate software management and provide option for policy compliance based on industry requirement. It includes protocol such as OVAL, OCIL, TMSAD, etc. Presenting our set of slides with Security Content Automation Protocol Specifications. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Common Platform Enumeration, Common Configuration Enumeration, Software Identification.
-
 Security Incident Management Process Icon
Security Incident Management Process IconPresenting our well structured Security Incident Management Process Icon. The topics discussed in this slide are Incident, Management, Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V
Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V Use it as a tool for discussion and navigation on Parameters, Description, Verify Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 HR Offboarding Process Mapping To Mitigate Security Risks
HR Offboarding Process Mapping To Mitigate Security RisksThis slide represents HR offboarding process mapping to mitigate security risks. It further includes manager request, replacement, job vacancy, preparation of resignation letter and health check, etc. Presenting our well structured HR Offboarding Process Mapping To Mitigate Security Risks. The topics discussed in this slide are Resignation, Documentation, Termination. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
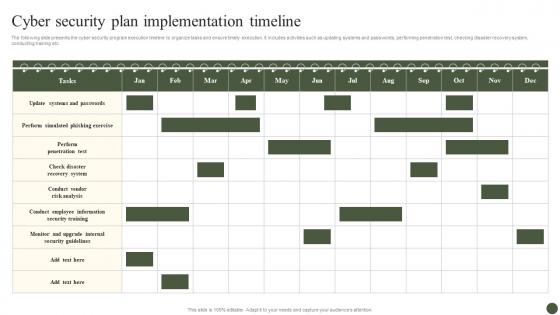 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Procedure Of Software Firewall In Network
Firewall Network Security Working Procedure Of Software Firewall In NetworkThis slide illustrates the working of a software firewall, including its architecture. The purpose of this slide is to showcase the working steps of a software firewall and its architecture. The architecture components include managed firewall as a service, a virtual firewall, and a containerized firewall. Present the topic in a bit more detail with this Firewall Network Security Working Procedure Of Software Firewall In Network Use it as a tool for discussion and navigation on Virtual Machine, Container, Private Cloud This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Working Process Of Proxy Firewall System
Firewall Network Security Working Process Of Proxy Firewall SystemThis slide represents a proxy firewall systems working process and user query flow. The purpose of this slide is to showcase how a proxy firewall works to safeguard network data from unethical activities. The components include a proxy server, proxy client, internet, and real server. Present the topic in a bit more detail with this Firewall Network Security Working Process Of Proxy Firewall System Use it as a tool for discussion and navigation on Working, Technologies Used, Firewall Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Working Process Of Stateful Inspection Firewalls
Firewall Network Security Working Process Of Stateful Inspection FirewallsThis slide describes how stateful inspection firewalls work. The purpose of this slide is to showcase the working process of a stateful inspection firewall, and the components include active sessions, authorized users, security policy, state recording, and a secure internal network. Present the topic in a bit more detail with this Firewall Network Security Working Process Of Stateful Inspection Firewalls Use it as a tool for discussion and navigation on Filtering Framework, Inspection Process, Valid Response This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security IP Internet Protocol Reputation Function In NGFW
Firewall Network Security IP Internet Protocol Reputation Function In NGFWThis slide outlines the overview of the IP Reputation function used in Next Generation Firewalls. The purpose of this slide is to introduce the Internet Protocol IP reputation, including its features and limitations. This function blocks network traffic based on the reputation score of Ips. Introducing Firewall Network Security IP Internet Protocol Reputation Function In NGFW to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Network Visibility, Streamlined Adaptability using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
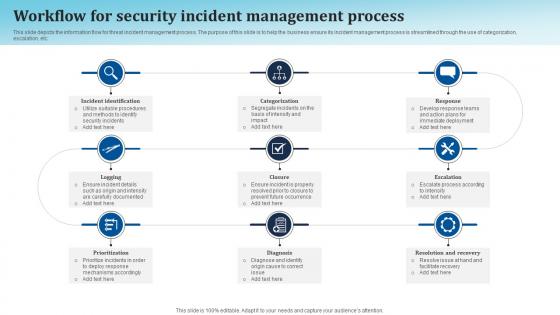 Workflow For Security Incident Management Process
Workflow For Security Incident Management ProcessThis slide depicts the information flow for threat incident management process. The purpose of this slide is to help the business ensure its incident management process is streamlined through the use of categorization, escalation, etc. Presenting our set of slides with Workflow For Security Incident Management Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Categorization, Escalation.
-
 Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V
Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Network Security, Node Security, Consensus Mechanism This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Environment And Data Security For Devsecops Process
Devsecops Best Practices For Secure Environment And Data Security For Devsecops ProcessThis slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Environment And Data Security For Devsecops Process. Use it as a tool for discussion and navigation on Standardize And Automate Environment, Isolate Containers For Security, Encrypt Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security
Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP SecurityThis slide represents the important attributes to contemplate DSP security. The purpose of this slide is to highlight the factors of DSPO security such as data encryption, Access control, secure communication, etc. Increase audience engagement and knowledge by dispensing information using Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security. This template helps you present information on twelve stages. You can also present information on Firmware Security, Physical Security, Secure Communication, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing Solve
Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing SolveThis slide showcases the solution to major security aspects of Digital Signal Processing in modern communication systems. The purpose of this slide is to highlight the security aspects such as encryption and data security, audio and speech authentication, biometric security, etc. Introducing Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing Solve to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Audio And Speech Authentication, Biometric Security, Encryption And Data Security, Network Security And Intrusion Detection, using this template. Grab it now to reap its full benefits.
-
 About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It
About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role and functionality of IPsec Internet Protocol Security in securing connections between devices. This slide also outlines the uses of IPsec such as protecting data during transmission over open networks, use in building VPNs, etc. Deliver an outstanding presentation on the topic using this About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Overview, Protocol Security, Destination using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Internet protocol Security IPsec technology. The various benefits explained in this slide are strong security, broad compatibility, flexibility, scalability and efficient network performance. Deliver an outstanding presentation on the topic using this Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Key Management, Performance Impact, Compatibility Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It
Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various features of Internet Protocol Security IPsec mechanism. The properties of IPsec include authentication, privacy, integrity, key management, tunnelling, flexibility and interoperability. Introducing Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Interoperability, using this template. Grab it now to reap its full benefits.
-
 Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It
Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Internet Protocol Security. The main components of IPsec architecture are ESP protocol, AH protocol, encryption algorithm, authentication algorithm, key management, etc. Present the topic in a bit more detail with this Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protocol Security, Architecture, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss the main components of Internet Protocol Security IPsec architecture. These three components are Encapsulating Security Payload ESP, Authentication Header AH, and Internet Key Exchange IKE. Deliver an outstanding presentation on the topic using this Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Authentication Header, Internet Key Exchange, Encapsulating Security Payload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It
Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the working steps of Internet Protocol Security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Deliver an outstanding presentation on the topic using this Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Connections, Protocol Security, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide talks about the distinction between the two methods of protecting information transmission. The purpose of this slide is to explain the concepts of transport mode and tunnel mode in the context of securing data during communication. Present the topic in a bit more detail with this Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Transport Mode, Protocol Security, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Ensuring Data Security In Onboarding Procedure
Icon For Ensuring Data Security In Onboarding ProcedureIntroducing our premium set of slides with Icon For Ensuring Data Security In Onboarding Procedure. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Data Onboarding, Digital Transformation. So download instantly and tailor it with your information.
-
 Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS
Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SSThis slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. Deliver an outstanding presentation on the topic using this Data Processing And Storage System Security Measures IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Data Tampering, Strong Authentications, Regular Hardware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SS
IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SSThis slide outlines key communication protocols that facilitate data exchange within IoT devices. It covers communication protocols such as wireless frequencies, Bluetooth, Zigbee, and LPWAN. Present the topic in a bit more detail with this IoT Communication Protocol Security Concerns IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Wearables Devices, Personal Devices, Jamming Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS
IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SSThis slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Introducing IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Robust Authentication, Registering Devices, Device Management, using this template. Grab it now to reap its full benefits.
-
 IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SS
IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SSThis slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re testing. Present the topic in a bit more detail with this IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Disconnect Infected, Mitigate Malicious, Infected Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SS
Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SSThis slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Present the topic in a bit more detail with this Security Attacks At Various Stages Of IoT Process IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Intelligent Processing, Data Transmission, Transmission Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS
Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SSThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS. Use it as a tool for discussion and navigation on Enable Security, Lead Generation, Emails For Contact Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Authentication Process For Web Security
Password Authentication Process For Web SecurityThis slide highlights the working process of authentication for web security approaches which includes password verification. Introducing our Password Authentication Process For Web Security set of slides. The topics discussed in these slides are Create Mobile Agent, Password Authentication Process, Web Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Web Application Security Testing Process Phases
Web Application Security Testing Process PhasesThis slide showcases the process phases of implementing web application security which include information gathering, planning analysis, etc. Introducing our premium set of slides with name Web Application Security Testing Process Phases. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Gathering, Vulnerability Detection, Reporting, Planning Analysis. So download instantly and tailor it with your information.
-
 Steps For Effective Triage Cyber Security Process
Steps For Effective Triage Cyber Security ProcessThis slide represents steps for effective triage process which assists security teams to focus on critical threats and allocate resources effectively., It includes steps for effective triage cyber security process such as identify, map and eradicate Introducing our premium set of slides with name Steps For Effective Triage Cyber Security Process Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Artifacts, Draw Event Timelines, System From Backup. So download instantly and tailor it with your information.
-
 Triage Process For Cyber Security Icon
Triage Process For Cyber Security IconPresenting our set of slides with name Triage Process For Cyber Security Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Process, Cyber Security Icon
-
 Utilization Of Triage Cyber Security Process In It
Utilization Of Triage Cyber Security Process In ItThis slide represents utilization of triage cyber security process in IT which assists to handle large number of tickets and increases help desk efficiency. It includes utilization of triage cyber security process in IT such as IT operations, email, etc Presenting our set of slides with name Utilization Of Triage Cyber Security Process In It This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Testing, Agile Software Development, IT Operations
-
 EDR Security Tools Matrix For Process Efficiency
EDR Security Tools Matrix For Process EfficiencyThis slide depicts EDR security tools and includes anomaly detection, real-time data visibility, threat processing, logs collection from network, and detecting vulnerabilities. Presenting our well structured EDR Security Tools Matrix For Process Efficiency. The topics discussed in this slide are Anomaly Detection, Real Time Data Visibility, Threat Processing, Detecting Vulnerabilities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





