Powerpoint Templates and Google slides for Security Rules
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Multistep process for continuous system security
Multistep process for continuous system securityPresenting this set of slides with name Multistep Process For Continuous System Security. This is a four stage process. The stages in this process are Predict, Prevent, Detect, Respond. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Organization security assessment process with monitor and mitigate
Organization security assessment process with monitor and mitigatePresenting this set of slides with name Organization Security Assessment Process With Monitor And Mitigate. This is a six stage process. The stages in this process are Monitor, Assessment, Analysis, Identify, Mitigate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security implementation process with strategize and plan
Security implementation process with strategize and planPresenting this set of slides with name Security Implementation Process With Strategize And Plan. This is a three stage process. The stages in this process are Assess And Learn, Strategize And Plan, Implement And Support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 One page hipaa law checklist including security and privacy rule presentation report infographic ppt pdf document
One page hipaa law checklist including security and privacy rule presentation report infographic ppt pdf documentHere we present One Page HIPAA Law Checklist Including Security And Privacy Rule Presentation Report Infographic PPT PDF Document one pager PowerPoint template. This is a HIPAA law one pager that highlights the most common health insurance portability and accountability. Utilize this readily available PowerPoint one pager to showcase the national standards that have been created to protect the information of patient that he doesnt want to disclose. This pre designed HIPAA law one pager PowerPoint slide includes various measures to avoid HIPAA violations. The main purpose of this law is to reduce healthcare fraud and abuse and to enforce standards for health information. Also, it guarantees security and privacy of health information. This creatively designed health insurance PowerPoint one pager includes high grade icons that makes it easy for your audience to understand the same. Protect the health information by taking the assistance of this amazing one pager PowerPoint slide show. Make your audience aware with the penalty that can be imposed on the violation of the HIPAA law. Grab this One Page HIPAA Law Checklist Including Security And Privacy Rule Presentation Report Infographic PPT PDF Document one pager template now.
-
 Process flow for enterprise cyber safety and security services ppt gallery
Process flow for enterprise cyber safety and security services ppt galleryPresenting this set of slides with name Process Flow For Enterprise Cyber Safety And Security Services Ppt Gallery. This is a four stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security management process standard ppt powerpoint presentation summary cpb
Security management process standard ppt powerpoint presentation summary cpbPresenting this set of slides with name Security Management Process Standard Ppt Powerpoint Presentation Summary Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Security Management Process Standard to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application security testing process ppt powerpoint presentation model picture cpb
Application security testing process ppt powerpoint presentation model picture cpbPresenting this set of slides with name Application Security Testing Process Ppt Powerpoint Presentation Model Picture Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Application Security Testing Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Incident management process cyber security ppt powerpoint presentation infographics show cpb
Incident management process cyber security ppt powerpoint presentation infographics show cpbPresenting this set of slides with name Incident Management Process Cyber Security Ppt Powerpoint Presentation Infographics Show Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Incident Management Process Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
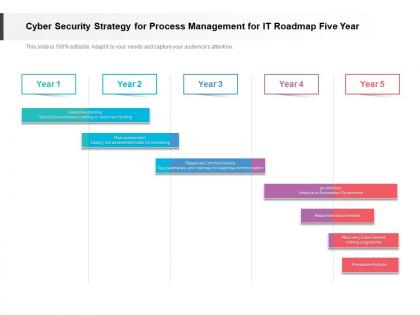 Cyber security strategy for process management for it roadmap five year
Cyber security strategy for process management for it roadmap five yearPresenting Cyber Security Strategy For Process Management For IT Roadmap Five Year PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap four quarter
Cyber security strategy for process management for it roadmap four quarterPresenting Cyber Security Strategy For Process Management For IT Roadmap Four Quarter PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Cyber security strategy for process management for it roadmap half yearly
Cyber security strategy for process management for it roadmap half yearlyPresenting Cyber Security Strategy For Process Management For IT Roadmap Half Yearly PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
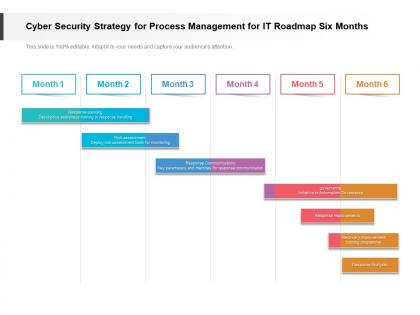 Cyber security strategy for process management for it roadmap six months
Cyber security strategy for process management for it roadmap six monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Six Months PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap three months
Cyber security strategy for process management for it roadmap three monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Three Months PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Process flow for company online database security ppt gallery
Process flow for company online database security ppt galleryPresenting this set of slides with name Process Flow For Company Online Database Security Ppt Gallery. This is a four stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Application security management process ppt powerpoint graphics tutorials cpb
Application security management process ppt powerpoint graphics tutorials cpbPresenting this set of slides with name Application Security Management Process Ppt Powerpoint Graphics Tutorials Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Application Security Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security auditing process ppt powerpoint presentation outline inspiration cpb
Information security auditing process ppt powerpoint presentation outline inspiration cpbPresenting this set of slides with name Information Security Auditing Process Ppt Powerpoint Presentation Outline Inspiration Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Information Security Auditing Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Industrial security risk management process
Industrial security risk management processPresenting this set of slides with name Industrial Security Risk Management Process. The topics discussed in these slides are External Situation, Internal Situation, Informs Analysis, Analyze Risk, Informs Analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Weakness icon for business process security
Weakness icon for business process securityPresenting this set of slides with name Weakness Icon For Business Process Security. This is a one stage process. The stages in this process are Weakness Icon For Business Process Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Analysts discussing cyber security protocols against crime
Analysts discussing cyber security protocols against crimePresenting this set of slides with name Analysts Discussing Cyber Security Protocols Against Crime. This is a three stage process. The stages in this process are Analysts Discussing Cyber Security Protocols Against Crime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Firewall rule base security practice ppt powerpoint presentation infographic template sample cpb
Firewall rule base security practice ppt powerpoint presentation infographic template sample cpbPresenting this set of slides with name Firewall Rule Base Security Practice Ppt Powerpoint Presentation Infographic Template Sample Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Firewall Rule Base Security Practice to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Financial security rules and regulation document
Financial security rules and regulation documentPresenting this set of slides with name Financial Security Rules And Regulation Document. This is a one stage process. The stages in this process are Financial Security Rules And Regulation Document. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Step 1 2 3 of network security process
Step 1 2 3 of network security processPresenting our set of slides with name Step 1 2 3 Of Network Security Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Step 1 2 3 Network, Security, Process.
-
 Computer security cyber security quotes ppt powerpoint presentation show rules cpb
Computer security cyber security quotes ppt powerpoint presentation show rules cpbPresenting our Computer Security Cyber Security Quotes Ppt Powerpoint Presentation Show Rules Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computer Security Cyber Security Quotes This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk migration process for enterprise information security management
Risk migration process for enterprise information security managementIntroducing our premium set of slides with Risk Migration Process For Enterprise Information Security Management. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Migration, Process Enterprise, Information Security, Management. So download instantly and tailor it with your information.
-
 Security incident management process ppt powerpoint presentation visual aids styles cpb
Security incident management process ppt powerpoint presentation visual aids styles cpbPresenting our Security Incident Management Process Ppt Powerpoint Presentation Visual Aids Styles Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Incident Management Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Requirement for security planning and risk management procedure
Requirement for security planning and risk management procedurePresenting our well structured Requirement For Security Planning And Risk Management Procedure. The topics discussed in this slide are Requirement Security, Planning Risk, Management Procedure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Wifi security protocols ppt powerpoint presentation ideas background image cpb
Wifi security protocols ppt powerpoint presentation ideas background image cpbPresenting WIFI Security Protocols Ppt Powerpoint Presentation Ideas Background Image Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase ten stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Wifi Security Protocols. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security content automation protocol ppt powerpoint presentation ideas model cpb
Security content automation protocol ppt powerpoint presentation ideas model cpbPresenting our Security Content Automation Protocol Ppt Powerpoint Presentation Ideas Model Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Security Content Automation Protocol This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Wireless security protocols ppt powerpoint presentation infographic template sample cpb
Wireless security protocols ppt powerpoint presentation infographic template sample cpbPresenting our Wireless Security Protocols Ppt Powerpoint Presentation Infographic Template Sample Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Wireless Security Protocols This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Business information security governance process
Business information security governance processPresenting our set of slides with name Business Information Security Governance Process. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification And Definition, Continuous Implementation, Business Impact, Acceptable Loss, Timeliness Of Security Delivery, Process Implementation.
-
 Security assessment process ppt powerpoint presentation portfolio portrait cpb
Security assessment process ppt powerpoint presentation portfolio portrait cpbPresenting our Security Assessment Process Ppt Powerpoint Presentation Portfolio Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Assessment Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Response plan process to handle security incidents
Response plan process to handle security incidentsIntroducing our Response Plan Process To Handle Security Incidents set of slides. The topics discussed in these slides are Strategy, Analysis, Remediation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multiple steps of blockchain security process architecture
Multiple steps of blockchain security process architecturePresenting our set of slides with name Multiple Steps Of Blockchain Security Process Architecture. This exhibits information on seven stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Distributed Network, Secure Transaction, Block Chain.
-
 Design development plan highlighting key features and security protocols
Design development plan highlighting key features and security protocolsThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Presenting our well-structured Design Development Plan Highlighting Key Features And Security Protocols. The topics discussed in this slide are Security, Organization, Resource. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Process With Data Sharing
Cyber Security Risk Management Process With Data SharingIntroducing our Cyber Security Risk Management Process With Data Sharing set of slides. The topics discussed in these slides are Assess Data Sources, Cyber Intelligence, Continuous Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security risk management process ppt powerpoint presentation file vector cpb
Security risk management process ppt powerpoint presentation file vector cpbPresenting our Security Risk Management Process Ppt Powerpoint Presentation File Vector Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Online Security Issues This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Machine learning web application security ppt powerpoint presentation gallery rules cpb
Machine learning web application security ppt powerpoint presentation gallery rules cpbPresenting Machine Learning Web Application Security Ppt Powerpoint Presentation Gallery Rules Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Machine Learning Web Application Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Video analytics security ppt powerpoint presentation layouts rules cpb
Video analytics security ppt powerpoint presentation layouts rules cpbPresenting Video Analytics Security Ppt Powerpoint Presentation Layouts Rules Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Video Analytics Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Circle process slide of hybrid cloud security system requirements infographic template
Circle process slide of hybrid cloud security system requirements infographic templateThis is our Circle Process Slide Of Hybrid Cloud Security System Requirements Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully editable visual content.
-
 Application security review process ppt powerpoint presentation icon ideas cpb
Application security review process ppt powerpoint presentation icon ideas cpbPresenting our Application Security Review Process Ppt Powerpoint Presentation Icon Ideas Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Application Security Review Process This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data and security breach process
Data and security breach processThis slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as- link forwarding by emails, data sharing and attacking and so on. Introducing our Data And Security Breach Process set of slides. The topics discussed in these slides are Research, Stage Attack, Exfiltrate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Process for responding to security data breach
Process for responding to security data breachThis slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Introducing our Process For Responding To Security Data Breach set of slides. The topics discussed in these slides are Survey, Limit, Learn, Engage, Record. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security data breach process by backdoor
Security data breach process by backdoorFollowing slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as- code integration with company software, so on. Introducing our Security Data Breach Process By Backdoor set of slides. The topics discussed in these slides are Execution Persistence, Defense Evasion, Supply Chain Attack, Exfiltration, Backdoor Activates. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Payroll security procedures ppt powerpoint presentation infographics slide portrait cpb
Payroll security procedures ppt powerpoint presentation infographics slide portrait cpbPresenting our Payroll Security Procedures Ppt Powerpoint Presentation Infographics Slide Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Payroll Security Procedures This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Process of disaster recovery planning cyber security it ppt powerpoint presentation styles
Process of disaster recovery planning cyber security it ppt powerpoint presentation stylesThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Process Of Disaster Recovery Planning Cyber Security IT Ppt Powerpoint Presentation Styles to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Plan Testing, Data Collection, Recovery Plans, Perform Risk Analysis, using this template. Grab it now to reap its full benefits.
-
 Costs incurred to process faulty cybersecurity transactions overcome the it security
Costs incurred to process faulty cybersecurity transactions overcome the it securityThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Faulty Cybersecurity Transactions Overcome The It Security. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline process overcome the it security
Timeline process overcome the it securityIncrease audience engagement and knowledge by dispensing information using Timeline Process Overcome The It Security. This template helps you present information on five stages. You can also present information on Timeline Process 2017 To 2021 using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud database sync process with firewall and security
Cloud database sync process with firewall and securityPresenting our set of slides with Cloud Database Sync Process With Firewall And Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Synergy Cloud Database, Firewall And Security, Synergy Database Server.
-
 Devops tools selection process it addressing different categories of devops tools security ppt slide
Devops tools selection process it addressing different categories of devops tools security ppt slideThis slide provides information regarding different categories of DevOps tools such as DevOps ready, DevOps enabled and DevOps capable. Introducing Devops Tools Selection Process It Addressing Different Categories Of Devops Tools Security Ppt Slide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on DevOps Ready, DevOps Enabled, DevOps Capable, Assessment Process, configuration automation, using this template. Grab it now to reap its full benefits.
-
 Enhanced security event management insider attacker method and behaviour assessment ppt rules
Enhanced security event management insider attacker method and behaviour assessment ppt rulesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this Enhanced Security Event Management Insider Attacker Method And Behaviour Assessment Ppt Rules. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhanced security event management various technologies for effective secops process ppt gallery
Enhanced security event management various technologies for effective secops process ppt galleryThis slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Introducing Enhanced Security Event Management Various Technologies For Effective Secops Process Ppt Gallery to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Basic Tools, Advanced Tools, using this template. Grab it now to reap its full benefits.
-
 Information security risk scorecard circular process ppt file background images
Information security risk scorecard circular process ppt file background imagesIncrease audience engagement and knowledge by dispensing information using Information Security Risk Scorecard Circular Process Ppt File Background Images. This template helps you present information on six stages. You can also present information on Circular Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security risk scorecard linear process ppt powerpoint presentation file gallery
Information security risk scorecard linear process ppt powerpoint presentation file galleryIntroducing Information Security Risk Scorecard Linear Process Ppt Powerpoint Presentation File Gallery to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Linear Process, using this template. Grab it now to reap its full benefits.
-
 Pitchbook for security underwriting deal share allocation process ppt file gallery
Pitchbook for security underwriting deal share allocation process ppt file galleryThe slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Introducing Pitchbook For Security Underwriting Deal Share Allocation Process Ppt File Gallery to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on In Case Undersubscription, In Case Of Oversubscription, using this template. Grab it now to reap its full benefits.
-
 Introducing information security risk assessment process workflow ppt portfolio
Introducing information security risk assessment process workflow ppt portfolioFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. Deliver an outstanding presentation on the topic using this Introducing Information Security Risk Assessment Process Workflow Ppt Portfolio. Dispense information and present a thorough explanation of Categorization, Prioritized Risks, System Characterization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Loss security performance ppt powerpoint presentation layouts rules cpb
Loss security performance ppt powerpoint presentation layouts rules cpbPresenting our Loss Security Performance Ppt Powerpoint Presentation Layouts Rules Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Low Investment Business Ideas. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Costs incurred to process overcome challenge cyber security healthcare ppt grid
Costs incurred to process overcome challenge cyber security healthcare ppt gridThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Overcome Challenge Cyber Security Healthcare Ppt Grid. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security process to manage firms sensitive data contd management to improve project safety it
Information security process to manage firms sensitive data contd management to improve project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Introducing Information Security Process To Manage Firms Sensitive Data Contd Management To Improve Project Safety IT to increase your presentation threshold. Encompassed with Firewall Audit Checklist, VPN Configuration, Penetrating Testing stages, this template is a great option to educate and entice your audience. Dispence information on Firewall Audit Checklist,VPN Configuration,Penetrating Testing, using this template. Grab it now to reap its full benefits.
-
 Information security process to manage firms sensitive data management to improve project safety it
Information security process to manage firms sensitive data management to improve project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Increase audience engagement and knowledge by dispensing information using Information Security Process To Manage Firms Sensitive Data Management To Improve Project Safety IT. This template helps you present information on three stages. You can also present information on Privileged Password Management, Daily Tasks Performed By Network Administrator, Network Security Audit Checklist using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise security operations various technologies for effective secops process ppt brochure
Enterprise security operations various technologies for effective secops process ppt brochureThis slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Introducing Enterprise Security Operations Various Technologies For Effective Secops Process Ppt Brochure to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Basic Tools, Advanced Tools, using this template. Grab it now to reap its full benefits.





