Powerpoint Templates and Google slides for Security Rules
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Risk Assessment Process For Effective Cyber Monitoring
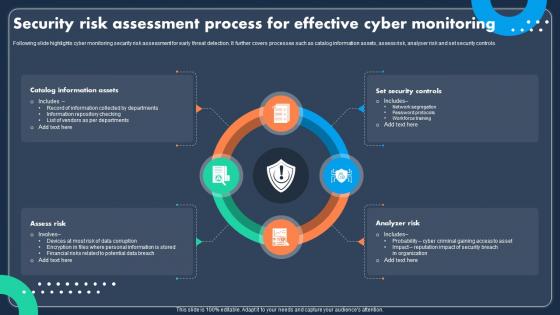
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Cloud Access Security Broker Working Process CASB Cloud Security
Cloud Access Security Broker Working Process CASB Cloud SecurityThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process CASB Cloud Security. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Critical Infrastructure Security Response Process
Critical Infrastructure Security Response ProcessThis slide represents the infrastructure security process for assessing preparedness. Its objective is to involve and study critical infrastructure and provide protection. This slide includes identification of infrastructure, assessment of vulnerabilities, prioritise, etc. Introducing our premium set of slides with Critical Infrastructure Security Response Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Infrastructure, Vulnerabilities, Prioritise. So download instantly and tailor it with your information.
-
 Data Security Management Process Icon For Companies
Data Security Management Process Icon For CompaniesPresenting our set of slides with Data Security Management Process Icon For Companies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Management Process, Icon.
-
 Process To Create Cyber Security Policy
Process To Create Cyber Security PolicyIntroducing our premium set of slides with Process To Create Cyber Security Policy Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Legal Compliance Review, Stakeholder Collaboration. So download instantly and tailor it with your information.
-
 ATP Cyber Security Attack Process
ATP Cyber Security Attack ProcessThis slide depicts the ATP cyber security attack process. Its aim is to monitor the cyber security attack and prevent them. This slide includes brute force attacker, unfamiliar location, lateral movement, sensitive data, etc. Presenting our set of slides with name ATP Cyber Security Attack Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Integrate Security, Measures In The System, Prevents Attack Automatically, Access Of Sensitive Data.
-
 ATP Cyber Security System Process
ATP Cyber Security System ProcessThis slide showcases the ATP cyber security process. Its aim is to help define the target and identify the anomalies. This slide includes researching target, acquiring tools, detection of virus, strengthening the system, remove virus, etc. Presenting our set of slides with name ATP Cyber Security System Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Plan, Intrusion, Getting Out, Sub Zero.
-
 Mobile Security Two Factor Authentication Process
Mobile Security Two Factor Authentication ProcessThis slide showcases roadmap for 2FA mobile security and includes assessment, select solutions, planning and integration, implementation, etc. Presenting our set of slides with name Mobile Security Two Factor Authentication Process. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment, Select Solution, Implementation, Testing And Optimization.
-
 Cyber Security Gap Analysis Process
Cyber Security Gap Analysis ProcessThis slide covers procedure for cyber security gap analysis such as establishing security goal, assembling skilled team, and gathering documentation to identify and address vulnerabilities and shortcomings in an organizations security measures to enhance overall resilience against cyber threats. Presenting our set of slides with name Cyber Security Gap Analysis Process. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Establish Security Goal, Assemble Skilled Team, Gather Necessary Documentation.
-
 Crypto Tokens Unlocking Process To Launch Security Token Offering BCT SS
Crypto Tokens Unlocking Process To Launch Security Token Offering BCT SSThis slide covers the procedure to launch security token offerings. It includes major steps such as preparation, pre-STO, STO for accredited investors, and post-STO. Present the topic in a bit more detail with this Crypto Tokens Unlocking Process To Launch Security Token Offering BCT SS Use it as a tool for discussion and navigation on Preparation, Accredited Investors, Sto For Investors This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment
Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E PaymentMentioned slide illustrates comparative analysis of various ACH Automated Clearing House payment processors which can be leveraged by businesses to making bank transfer. It includes key attributes such as ACH processors, best attribute, features, rating, price, and company size. Deliver an outstanding presentation on the topic using this Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of ACH Payment Processors, Best Attribute, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization Working Process For Data Security Implementing Effective Tokenization
Tokenization Working Process For Data Security Implementing Effective TokenizationThis slide represents the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization Working Process For Data Security Implementing Effective Tokenization. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Log Management Process In Application Security
Log Management Process In Application SecurityThis slide showcases the introduction of log management in application security for decreasing the security threats. Increase audience engagement and knowledge by dispensing information using Log Management Process In Application Security. This template helps you present information on five stages. You can also present information on Handling Security Logs, Non Compliance Risks Attacks, Ensure Data Security, Log Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process Phases Of Penetration Testing In Application Security
Process Phases Of Penetration Testing In Application SecurityThis slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc. Introducing Process Phases Of Penetration Testing In Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Planning And Reconnaissance, Gaining Access, Maintaining Access, Analysis And WAF Configuration, using this template. Grab it now to reap its full benefits.
-
 DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps
DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOpsThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build or test, deploy, and monitor. Present the topic in a bit more detail with this DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps. Use it as a tool for discussion and navigation on Integrate Security, Encourage Developer Ownership, Static Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Security Issue IAM Process For Effective Access
Identity And Access Management Security Issue IAM Process For Effective AccessThis slide discusses the security issue of the Identity and Access Management process. The purpose of this slide is to explain the security challenges of IAM these include impractical security policies, inconsistent security policies, slow de-provision, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Security Issue IAM Process For Effective Access. Dispense information and present a thorough explanation of Impractical Security Policies, Inconsistent Security Policies, Inconsistent Identity Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Audit Procedure Icon To Verify Company Data Protection
Security Audit Procedure Icon To Verify Company Data ProtectionPresenting our set of slides with Security Audit Procedure Icon To Verify Company Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Audit Procedure, Verify Company, Data Protection.
-
 Process To Determine Adequate Cyber Security Control
Process To Determine Adequate Cyber Security ControlThis slide represents the process to identifying adequate cyber security control for business to prevent online threats and implement necessary steps. It includes various steps such as evaluate size of the company, identify scope of IT infrastructure, etc. Presenting our set of slides with Process To Determine Adequate Cyber Security Control This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Scope Of It Infrastructure, Evaluate Size Of Company, Investment In Cyber Security
-
 Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS
Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of cryptographic network protocols for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about secure connectivity, updates, etc. Increase audience engagement and knowledge by dispensing information using Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Secure Connectivity, Network Protocols Usage, Continuous Updates, Cryptographic Network Protocols using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Email Authentication And Security Working Process
Email Authentication And Security Working ProcessThis slide highlights the email authentication and security working process which includes sender establishes authentication rules, and sender configuration. Presenting our set of slides with Email Authentication And Security Working Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Infrastructure, Authentication Rules, Authentication Results.
-
 Email Security Gateway Workflow Process
Email Security Gateway Workflow ProcessThis slide outlines the workflow process of email gateway which involves incoming emails, validate sender, validate content, advanced threat detection, etc. Presenting our well structured Email Security Gateway Workflow Process. The topics discussed in this slide are Email Gateway, Protection Against, Validate Sender. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Primary Protocols Used In Email Security
Primary Protocols Used In Email SecurityThis slide is an overview of different protocols used in email security which includes simple mail transfer protocol secure and sender policy framework. Introducing our premium set of slides with Primary Protocols Used In Email Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mail Transfer, Policy Framework, Layer Security. So download instantly and tailor it with your information.
-
 Application Security Implementation Plan Process Of Implementing Cloud Native Application Security
Application Security Implementation Plan Process Of Implementing Cloud Native Application SecurityThis slide highlights the steps for deploying cloud-native application security which include understanding principles, risk assessment, etc. Introducing Application Security Implementation Plan Process Of Implementing Cloud Native Application Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Continuous Monitoring, Container Security, Implement Strong Access Controls, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Process Phases For Effective Authentication Implementation
Application Security Implementation Plan Process Phases For Effective Authentication ImplementationThis slide showcases the steps for deploying effective authentication which include defining requirements, selecting authentication method, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Process Phases For Effective Authentication Implementation. This template helps you present information on seven stages. You can also present information on Implement Login Mechanism, Choose Authentication Method, Secure Storage Of Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Working Process Of Effective Logging Implementation
Application Security Implementation Plan Working Process Of Effective Logging ImplementationThis slide outlines the steps for deploying effective logging which include assess requirements, select logging tool, defining logging standards, etc. Introducing Application Security Implementation Plan Working Process Of Effective Logging Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Security, Centralize Log Management, Define Logging Standards, Select Logging Tools, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Implementation Process Of Endpoint Security Solutions
Endpoint Security Implementation Process Of Endpoint Security SolutionsThis slide highlights the process stages of endpoint security which include information gathering, choosing security solutions, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Implementation Process Of Endpoint Security Solutions. This template helps you present information on three stages. You can also present information on Gather Information, Deploy Selected Solutions, Select Security Solutions, Endpoint Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IP Security For Cyber Protocol Icon
IP Security For Cyber Protocol IconPresenting our set of slides with name IP Security For Cyber Protocol Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IP Security, Cyber Protocol Icon.
-
 Effective Cyber Security Management Process
Effective Cyber Security Management ProcessFollowing slide showcases process that can help businesses in mitigating cyber security threats. It includes steps such as pinpoint cyber security risks, evaluate cybersecurity risks, mitigation measures, monitoring, etc. Presenting our well structured Effective Cyber Security Management Process. The topics discussed in this slide are Identify The Cybersecurity Risks, Identify Cybersecurity Risks, Mitigation Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security
Tokenization For Improved Data Security Overview And Process Of Tokenization In Data SecurityThis slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Introducing Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization In Data Security, While Ensuring Security, Small And Midsize Enterprises, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based System
Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based SystemThis slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Introducing Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based System to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization Process Activities, Cloud Based System, Retrieving Data, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Tokenization Working Process For Data Security
Tokenization For Improved Data Security Tokenization Working Process For Data SecurityThis slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Tokenization Working Process For Data Security. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SS
Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SSThe following slide depicts smart contract security checklist to minimize data breaches. It includes elements such as audit, token approval, interface, restrict potential risk, hardware wallets, etc. Deliver an outstanding presentation on the topic using this Smart Contracts Security Due Diligence Checklist Step By Step Process To Develop Blockchain BCT SS. Dispense information and present a thorough explanation of Token Approval, Restrict Potential Risk, Hardware Wallets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Financial Projection Security Protocols
Business Financial Projection Security ProtocolsThe purpose of this slide is to showcase safety measures of financial projection such as hire experts and understand market which help in ensuring risk mitigation and safeguards business. Introducing our premium set of slides with Business Financial Projection Security Protocols Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Benefit Existing Businesses, Understand Market, Hire Experts So download instantly and tailor it with your information.
-
 Process To Implement Gamified Cyber Security Training
Process To Implement Gamified Cyber Security TrainingThe purpose of this slide is to create a gamified cybersecurity training program that captures attention of users also achieves specific, measurable improvements in cybersecurity awareness and skills including steps such as identifying learning objectives, structuring activities and challenges, etc. Introducing our premium set of slides with name Process To Implement Gamified Cyber Security Training. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Learning Objectives, Structure Activities And Challenges, Cyber Security Training. So download instantly and tailor it with your information.
-
 Physical Security Process Flow Chart
Physical Security Process Flow ChartThis slide showcases flow chart of physical security that includes determining need, identifying threats, elements of protection system, verification, testing and handing over. Presenting our set of slides with Physical Security Process Flow Chart. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Security Need, Facility Characterization, Identify Potential Threats.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comanagement Of SIEM Cyber Security Process
Comanagement Of SIEM Cyber Security ProcessThis slide showcases the co management of SIEM cyber security process. Its aim is to list monitoring activities and manage services. This slide includes onboarding, build out, baseline, tune and monitor. Introducing our premium set of slides with name Comanagement Of SIEM Cyber Security Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Onboard, Build Out, Baseline. So download instantly and tailor it with your information.
-
 Cyber Security Process In Industry 4 0 Icon
Cyber Security Process In Industry 4 0 IconPresenting our set of slides with Cyber Security Process In Industry 4 0 Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Process, Industry 4 0, Icon.
-
 Step By Step Process Of E Commerce Security
Step By Step Process Of E Commerce SecurityThis slide shows e-commerce transactions and data integrity through comprehensive multi-layer security measures. The steps are regular back of database, set up strong passwords, use malware softwwares,etc. Presenting our set of slides with Step By Step Process Of E Commerce Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Process, Ecommerce Security, Security Measures.
-
 Working Process Of Security Operations Center
Working Process Of Security Operations CenterThe below slide highlights the various steps involved in the working of security operations center that helps to safeguard sensitive data from cyber attacks. The major steps are asset discovery, behavioral monitoring, etc. Presenting our set of slides with name Working Process Of Security Operations Center. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Compliance Management, Incident Response, Alert Ranking.
-
 Mobile Application Security Testing Process Mobile Security
Mobile Application Security Testing Process Mobile SecurityThis slide explains the mobile application security testing process which includes interaction and data handling and static analysis for weaknesses. Introducing Mobile Application Security Testing Process Mobile Security to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Enable User Authentication, Cloud Backups using this template. Grab it now to reap its full benefits.
-
 Mobile Platform Security Communication Process Mobile Security
Mobile Platform Security Communication Process Mobile SecurityThis slide depicts the mobile platform security communication process which include application registration and back-end credentials. Present the topic in a bit more detail with this Mobile Platform Security Communication Process Mobile Security Use it as a tool for discussion and navigation on Agenda, Mode This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Patch Management Process Lifecycle Mobile Security
Security Patch Management Process Lifecycle Mobile SecurityThis slide represents the patch management process lifecycle which include steps like standardize software versions, categorize assets and patches, etc. Introducing Security Patch Management Process Lifecycle Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Information Gathering, Exploitation using this template. Grab it now to reap its full benefits.
-
 Working Process Of Phishing Attacks In Devices Mobile Security
Working Process Of Phishing Attacks In Devices Mobile SecurityThis slide depicts about the working of phishing attacks in mobile devices which include attacker, victim, phishing website and legitimate website. Deliver an outstanding presentation on the topic using this Working Process Of Phishing Attacks In Devices Mobile Security Dispense information and present a thorough explanation of Sends Email To Victim, Legitimate Website using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Fintech Cyber Security KYC Process
Fintech Cyber Security KYC ProcessThis slide showcases the fintech cyber security KYC process. Its aim is to identify the problems and verify the right customer to protect the data. This slide includes document verification, customer authentication, assess risk, enrolment facilitation, etc. Presenting our set of slides with name Fintech Cyber Security KYC Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enrolment, Risk Assessment, Identity Verification Report.
-
 Ssl Certificate Process To Secure Payment Gateway Implementing E Commerce Security Measures
Ssl Certificate Process To Secure Payment Gateway Implementing E Commerce Security MeasuresThe slide depicts secure sockets layer SSL process to encrypt sensitive information between a webs browser and server. It include client web browser, websiteserver, SSL certificate etc. Introducing Ssl Certificate Process To Secure Payment Gateway Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Client Check Certificate, Impact, Delivers Encrypted Content, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Gather Information, Choose Security Solutions, Implement Chosen Solutions, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Process Of Performing White Box Testing
Web Security Upgradation Process Of Performing White Box TestingThis slide highlights the steps for executing manual testing in software development such as document review, requirement analysis, etc. Introducing Web Security Upgradation Process Of Performing White Box Testing to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Process Of Performing White Box Testing, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Process Stages Of Implementing Vulnerability Scanning
Web Security Upgradation Process Stages Of Implementing Vulnerability ScanningThis slide gives an overview of the phases in the process of web security such as requirement analysis, test planning, test case development, etc. Present the topic in a bit more detail with this Web Security Upgradation Process Stages Of Implementing Vulnerability Scanning. Use it as a tool for discussion and navigation on Asset Inventory, Surface Scanning, Detection And Classification, Remediation Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Process Stages Of Web Application Firewall Waf
Web Security Upgradation Process Stages Of Web Application Firewall WafThis slide represents the different phases of Web Application Firewall WAF which include set up, creating web ACL, etc. Introducing Web Security Upgradation Process Stages Of Web Application Firewall Waf to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Initiate WAF, Select Resources, Include Specific Rules, Create A Web ACL, using this template. Grab it now to reap its full benefits.
-
 Five Steps Process To Address Chatbot Security
Five Steps Process To Address Chatbot SecurityThis slide shows the processes organizations can use to improve or enhance the security of their chatbots. It includes stages such as assessment, minimizing data exposure, implementation, testing, and training. Introducing our premium set of slides with Five Steps Process To Address Chatbot Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement, Minimize Data Exposure, Test. So download instantly and tailor it with your information.
-
 Email Security Best Practices Components Of Email Account Security Process
Email Security Best Practices Components Of Email Account Security ProcessThis slide highlights the process of incorporating email security policies in an organization. The purpose of this slide is to illustrate the flow of email security implementation. The components are isolate, prevent, prepare, integrate, etc. Introducing Email Security Best Practices Components Of Email Account Security Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prevent, Isolate, Respond, Prepare, Integrate, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Understanding The Concept Of Email Security Process
Email Security Best Practices Understanding The Concept Of Email Security ProcessThis slide demonstrates the email account security process. The purpose of this slide is to highlight the main components of securing email communication, such as email gateway, update, action, continuously reprocess, email provider, etc. Introducing Email Security Best Practices Understanding The Concept Of Email Security Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Email Gateway, Email Sent For Security Check, Directs Email To Email Provider, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Wireless Lan Security Protocols
Comparative Assessment Of Wireless Lan Security ProtocolsThis slide represents comparative assessment of various WLAN security protocols that assist companies in selecting relevant protocol suitable for specific use cases. It includes various protocols such as WEP, WPA, WPA2, and WPA3 Presenting our well structured Comparative Assessment Of Wireless Lan Security Protocols The topics discussed in this slide are Year Release, Cryptographic Technique, Session Key SizeThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Hypertext Transfer Protocol Authentication In Web Security Solution
Hypertext Transfer Protocol Authentication In Web Security SolutionThis slide showcases the HTTP authentication in web security which include HTTP Basic Authentication, HTTP Digest Authentication, etc. Introducing Hypertext Transfer Protocol Authentication In Web Security Solution to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Http Basic Authentication, Http Digest Authentication, Https Client Authentication, Form Based Authentication, using this template. Grab it now to reap its full benefits.
-
 Process Phases Of Web Security In CS
Process Phases Of Web Security In CSIntroducing Process Phases Of Web Security In CS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Process Phases, Web Security In Cs, using this template. Grab it now to reap its full benefits.
-
 Web Security Solution Working Process Of Web Application Firewall WAF
Web Security Solution Working Process Of Web Application Firewall WAFThie slide represents the process of WAF in web security with its various components such as origin server, web application firewalls, etc. Present the topic in a bit more detail with this Web Security Solution Working Process Of Web Application Firewall WAF. Use it as a tool for discussion and navigation on Working Process, Web Application Firewall Waf. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Patch Management Process For IOT Device Security
Patch Management Process For IOT Device SecurityThe purpose of this slide is to ensure cybersecurity through compliance management and regular audits of network device patch management. It covers steps such as defining goals, conducting vulnerability scanning, managing patch compliance, etc. Presenting our set of slides with name Patch Management Process For IOT Device Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Device Inventory, Embrace Automation, Test Patches.
-
 Security Patch Management Process Icon
Security Patch Management Process IconIntroducing our premium set of slides with name Security Patch Management Process Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Patch Management, Process. So download instantly and tailor it with your information.





