Powerpoint Templates and Google slides for Security Rules
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information Security Program Action Plan Process
Information Security Program Action Plan ProcessThis slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc Introducing our Information Security Program Action Plan Process set of slides. The topics discussed in these slides are Security, Program, Process. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Workplace Emergency Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Workplace Emergency Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon is a bright and vibrant illustration of a workplace emergency action plan. It is perfect for presentations on communication and safety in the workplace. It is a great visual aid for highlighting the importance of emergency preparedness.
-
 Workplace Emergency Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Workplace Emergency Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is perfect for illustrating a workplace emergency action plan. Its a simple, yet effective way to communicate the importance of emergency preparedness in the workplace.
-
 Seven staged circular process network security planning ppt slides
Seven staged circular process network security planning ppt slidesVisually stunning PowerPoint Presentation slides. Clearly describes the various security strategies which could be beneficial to cope up with the risks. Offers Wide screen view for more clarity and better vision. Compatible with Google Framework. Being spacious enough to Include Description of Security groups and other vital information. Easily amendable PPT patterns.The stages in this process are security.
-
 Security of iot operations powerpoint slide rules
Security of iot operations powerpoint slide rulesPresenting security of iot operations powerpoint slide rules. This is a security of iot operations powerpoint slide rules. This is a one stage process. The stages in this process are security program, security configuration management, vulnerability scanning, application scanning, threat management, cloud assessment, authentication and privacy.
-
 Billing customer security e source control circular process with icon in centre
Billing customer security e source control circular process with icon in centrePresenting billing customer security e source control circular process with icon in centre. This is a billing customer security e source control circular process with icon in centre. This is a seven stage process. The stages in this process are billing process, billing procedure, billing cycle.
-
 Cloud governance define roles security policies and processes
Cloud governance define roles security policies and processesPresenting this set of slides with name - Cloud Governance Define Roles Security Policies And Processes. This is a five stage process. The stages in this process are Cloud Governance, Cloud Computing, Cloud Management.
-
 Skill matrix table identifying technical security and transaction processing
Skill matrix table identifying technical security and transaction processingPresenting this set of slides with name - Skill Matrix Table Identifying Technical Security And Transaction Processing. This is a three stage process. The stages in this process are Skill Matrix, Skill Mapping, Intelligence.
-
 Management experience process control advanced training privacy security
Management experience process control advanced training privacy securityPresenting this set of slides with name - Management Experience Process Control Advanced Training Privacy Security. This is an editable four graphic that deals with topics like Management Experience, Process Control, Advanced Training, Privacy Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security management integration directory process composer lifecycle management
Security management integration directory process composer lifecycle managementPresenting this set of slides with name - Security Management Integration Directory Process Composer Lifecycle Management. This is an editable three stages graphic that deals with topics like Security Management, Integration Directory, Process Composer, Lifecycle Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Major internet security technologies internet protocol stack stateful inspection
Major internet security technologies internet protocol stack stateful inspectionPresenting this set of slides with name - Major Internet Security Technologies Internet Protocol Stack Stateful Inspection. This is an editable four graphic that deals with topics like Major Internet Security Technologies, Internet Protocol Stack, Stateful Inspection to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Insurance claim process cashless intimate submit documents security pay
Insurance claim process cashless intimate submit documents security payPresenting this set of slides with name - Insurance Claim Process Cashless Intimate Submit Documents Security Pay. This is a five stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Insurance claim process intimate submit document security pay
Insurance claim process intimate submit document security payPresenting this set of slides with name - Insurance Claim Process Intimate Submit Document Security Pay. This is a four stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Insurance claim process intimate submit documents security pay
Insurance claim process intimate submit documents security payPresenting this set of slides with name - Insurance Claim Process Intimate Submit Documents Security Pay. This is a four stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Hotel safety and security emergency process with 5 boxes
Hotel safety and security emergency process with 5 boxesPresenting hotel safety and security emergency process with 5 boxes. This is a hotel safety and security emergency process with 5 boxes. This is a five stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Hotel safety and security procedures with converging arrows and boxes
Hotel safety and security procedures with converging arrows and boxesPresenting hotel safety and security procedures with converging arrows and boxes. This is a hotel safety and security procedures with converging arrows and boxes. This is a six stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Operating system memory process management security
Operating system memory process management securityPresenting this Operating System Memory Process Management Security PowerPoint presentation. Add charts and graphs for a wonderful representation of information. The PPT also supports the standard (4:3) and widescreen (16:9) aspect ratios. It is compatible with Google Slides. Convert this into popular images or document formats such as JPEG, PNG or PDF. High-quality graphics ensure that graphics quality is maintained at every stage of presentation.
-
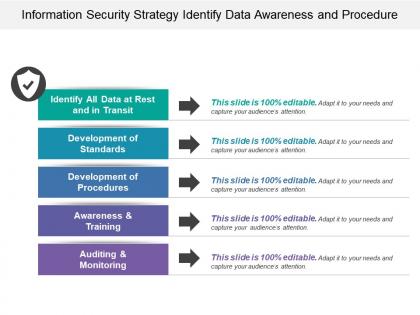 Information security strategy identify data awareness and procedure
Information security strategy identify data awareness and procedurePresenting this set of slides with name - Information Security Strategy Identify Data Awareness And Procedure. This is a five stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Business process automation standardise security collaboration consistency
Business process automation standardise security collaboration consistencyPresenting this set of slides with name - Business Process Automation Standardise Security Collaboration Consistency. This is a eight stage process. The stages in this process are Business Process Automation, Robotic Process Automation, Software Development.
-
 Infrastructure management defining application security and process
Infrastructure management defining application security and processPresenting this set of slides with name - Infrastructure Management Defining Application Security And Process. This is a seven stage process. The stages in this process are Infrastructure Management, Operation Management, Network Management.
-
 Process integration oversight security policy management corporate strategic plan
Process integration oversight security policy management corporate strategic planPresenting this set of slides with name - Process Integration Oversight Security Policy Management Corporate Strategic Plan. This is an editable three stages graphic that deals with topics like Process Integration Oversight, Security Policy Management, Corporate Strategic Plan to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Release roadmap swimlane include flow of process such as environment setup and security improvements
Release roadmap swimlane include flow of process such as environment setup and security improvementsPresenting this set of slides with name - Release Roadmap Swimlane Include Flow Of Process Such As Environment Setup And Security Improvements. This is a three stage process. The stages in this process are Release Swimlane, Launch Swimlane, Deliver Swimlane.
-
 Digital media management network security business process transformation cpb
Digital media management network security business process transformation cpbPresenting this set of slides with name - Digital Media Management Network Security Business Process Transformation Cpb. This is an editable five stages graphic that deals with topics like Digital Media Management, Network Security, Business Process Transformation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Intelligent process automation framework security a136 ppt powerpoint presentation layouts
Intelligent process automation framework security a136 ppt powerpoint presentation layoutsPresenting this set of slides with name Intelligent Process Automation Framework Security A136 Ppt Powerpoint Presentation Layouts. This is a five stage process. The stages in this process are Technology, Cognitive Agents, Planning, Strategy, Marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Intelligent process automation framework icons slide security ppt powerpoint presentation file
Intelligent process automation framework icons slide security ppt powerpoint presentation filePresenting this set of slides with name Intelligent Process Automation Framework Icons Slide Security Ppt Powerpoint Presentation File. The topics discussed in these slides are Technology, Communication, Knowledge, Planning, Marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Latest cyber security technology ppt powerpoint presentation gallery rules cpb
Latest cyber security technology ppt powerpoint presentation gallery rules cpbPresenting this set of slides with name Latest Cyber Security Technology Ppt Powerpoint Presentation Gallery Rules Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Latest Cyber Security Technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Leverage securities calculation ppt powerpoint presentation rules
Leverage securities calculation ppt powerpoint presentation rulesPresenting this set of slides with name Leverage Securities Calculation Ppt Powerpoint Presentation Rules. The topics discussed in these slides are Leverage, Securities, Calculation, Operating, Financial. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Contents securities categorization l344 ppt powerpoint presentation rules
Contents securities categorization l344 ppt powerpoint presentation rulesPresenting this set of slides with name Contents Securities Categorization L344 Ppt Powerpoint Presentation Rules. This is a five stage process. The stages in this process are Business, Management, Planning, Strategy, Marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Bi fold hipaa law checklist including security and privacy rule document report pdf ppt template one pager
Bi fold hipaa law checklist including security and privacy rule document report pdf ppt template one pagerInduced with graphics that captivate the mind, this Bi Fold HIPAA Law Checklist Including Security And Privacy Rule Document Report PDF PPT Template One Pager is a remarkable visual communication and promotion tool to bring attention to your business and its prospects. Use it to devise a successful business project that speaks volumes of your companys identity and enhances the viewers interest in your services. With plenty of industry-specific customizable shapes, visuals, graphics, and many more, this A4 size bi-fold design is the perfect fit for your creative and professional needs. Improve your customer engagement by editing the default text, fonts, or images to create a completely-customized layout for comprehensive reporting. Click below and download right now.
-
 Cluster checklist security process engine ppt icons graphics
Cluster checklist security process engine ppt icons graphicsRuns effortlessly with all compatible software. Downloads rapidly in matter of moments. Trouble free process to add company logo, name or trademark. No pixilation when slide is viewed on widescreen. Compatible with google slides. Mention titles and subtitles without feeling constrained. High resolution PPT slides. Convert to JPG and PDF formats easily. Useful for businesses, artists, NGO’s, students, teachers etc.
-
 Business strategy innovation laptop with pair of keys security process ppt slide powerpoint
Business strategy innovation laptop with pair of keys security process ppt slide powerpointAccess to resize the shape and size of the slide icons. Flexible to be used with the Google Slides. Provided instructions to modify the slide designs. Replace the image icons with your own images. Useful for the Marketing and Sales professionals or business managers.
-
 Business strategy development powerpoint templates mind key security ppt process
Business strategy development powerpoint templates mind key security ppt processWe are proud to present our business strategy development powerpoint templates mind key security ppt process. This template with keys in mind on it will be the great choice for presentations on security, symbol, shapes, and business.
-
 External network security ppt powerpoint presentation slides rules cpb
External network security ppt powerpoint presentation slides rules cpbPresenting this set of slides with name External Network Security Ppt Powerpoint Presentation Slides Rules Cpb. This is an editable Powerpoint four stages graphic that deals with topics like External Network Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Network security fundamentals ppt powerpoint presentation show rules cpb
Network security fundamentals ppt powerpoint presentation show rules cpbPresenting this set of slides with name Network Security Fundamentals Ppt Powerpoint Presentation Show Rules Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Network Security Fundamentals to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security essentials ppt powerpoint presentation model rules cpb
Cyber security essentials ppt powerpoint presentation model rules cpbPresenting this set of slides with name Cyber Security Essentials Ppt Powerpoint Presentation Model Rules Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cyber Security Essentials to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security risk assessment process ppt powerpoint presentation shapes cpb
Information security risk assessment process ppt powerpoint presentation shapes cpbPresenting this set of slides with name Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Information Security Risk Assessment Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Physical security management protocol ppt powerpoint presentation infographic cpb
Physical security management protocol ppt powerpoint presentation infographic cpbPresenting this set of slides with name Physical Security Management Protocol Ppt Powerpoint Presentation Infographic Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Physical Security Management Protocol to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Encryption security ppt powerpoint presentation icon rules cpb
Encryption security ppt powerpoint presentation icon rules cpbPresenting this set of slides with name Encryption Security Ppt Powerpoint Presentation Icon Rules Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Encryption Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security log management process ppt powerpoint presentation professional graphics cpb
Security log management process ppt powerpoint presentation professional graphics cpbPresenting this set of slides with name Security Log Management Process Ppt Powerpoint Presentation Professional Graphics Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Security Log Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Investment process security analysis ppt powerpoint presentation icon background images cpb
Investment process security analysis ppt powerpoint presentation icon background images cpbPresenting this set of slides with name Investment Process Security Analysis Ppt Powerpoint Presentation Icon Background Images Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Investment Process Security Analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Process of security risk assessment and audit
Process of security risk assessment and auditPresenting this set of slides with name Process Of Security Risk Assessment And Audit. The topics discussed in these slides are Process Security, Risk Assessment, Audit. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber security audit procedures ppt powerpoint presentation infographics slides cpb
Cyber security audit procedures ppt powerpoint presentation infographics slides cpbPresenting this set of slides with name Cyber Security Audit Procedures Ppt Powerpoint Presentation Infographics Slides Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Audit Procedures to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Itil security management process ppt powerpoint presentation visual aids slides cpb
Itil security management process ppt powerpoint presentation visual aids slides cpbPresenting this set of slides with name ITIL Security Management Process Ppt Powerpoint Presentation Visual Aids Slides Cpb. This is an editable Powerpoint three stages graphic that deals with topics like ITIL Security Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Standard security management process ppt powerpoint presentation pictures graphic images cpb
Standard security management process ppt powerpoint presentation pictures graphic images cpbPresenting this set of slides with name Standard Security Management Process Ppt Powerpoint Presentation Pictures Graphic Images Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Standard Security Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security vulnerability scanning ppt powerpoint presentation inspiration rules cpb
Security vulnerability scanning ppt powerpoint presentation inspiration rules cpbPresenting this set of slides with name Security Vulnerability Scanning Ppt Powerpoint Presentation Inspiration Rules Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Security Vulnerability Scanning to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security people process technology ppt powerpoint presentation file graphics template cpb
Cyber security people process technology ppt powerpoint presentation file graphics template cpbPresenting this set of slides with name Cyber Security People Process Technology Ppt Powerpoint Presentation File Graphics Template Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Cyber Security People Process Technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security people process technology framework
Cyber security people process technology frameworkPresenting this set of slides with name Cyber Security People Process Technology Framework. This is a six stage process. The stages in this process are Information Risk Management, Incident Response And Forensic Investigation, Architecture, Applications And Network Security, Threat And Vulnerability Assessment, Compliance And Awareness, Security Management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security trends information security ppt powerpoint presentation icon rules cpb
Computer security trends information security ppt powerpoint presentation icon rules cpbPresenting this set of slides with name Computer Security Trends Information Security Ppt Powerpoint Presentation Icon Rules Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Computer Security Trends Information Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security management process ppt powerpoint presentation model cpb
Information security management process ppt powerpoint presentation model cpbPresenting this set of slides with name Information Security Management Process Ppt Powerpoint Presentation Model Cpb. This is an editable Powerpoint eight stages graphic that deals with topics like Information Security Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Process transformation compliance security risk management ppt powerpoint presentation file format ideas cpb
Process transformation compliance security risk management ppt powerpoint presentation file format ideas cpbPresenting this set of slides with name Process Transformation Compliance Security Risk Management Ppt Powerpoint Presentation File Format Ideas Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Process Transformation Compliance Security Risk Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security problems cloud computing ppt powerpoint presentation gallery rules cpb
Security problems cloud computing ppt powerpoint presentation gallery rules cpbPresenting this set of slides with name Security Problems Cloud Computing Ppt Powerpoint Presentation Gallery Rules Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Security Problems Cloud Computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
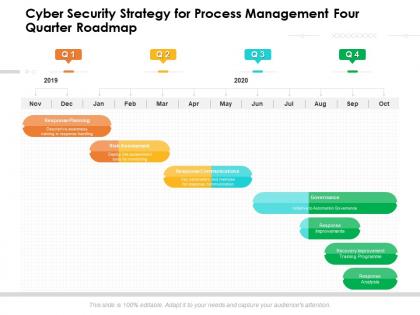 Cyber security strategy for process management four quarter roadmap
Cyber security strategy for process management four quarter roadmapPresenting Cyber Security Strategy For Process Management Four Quarter Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
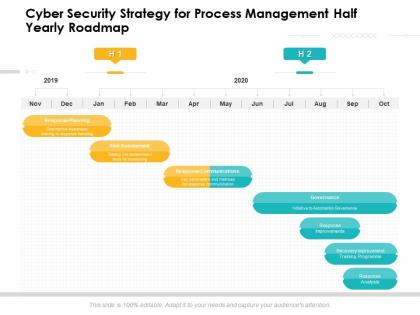 Cyber security strategy for process management half yearly roadmap
Cyber security strategy for process management half yearly roadmapPresenting Cyber Security Strategy For Process Management Half Yearly Roadmap PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
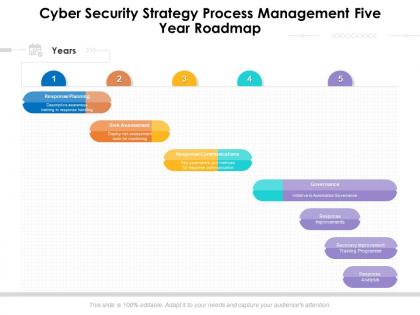 Cyber security strategy process management five year roadmap
Cyber security strategy process management five year roadmapPresenting Cyber Security Strategy Process Management Five Year Roadmap PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
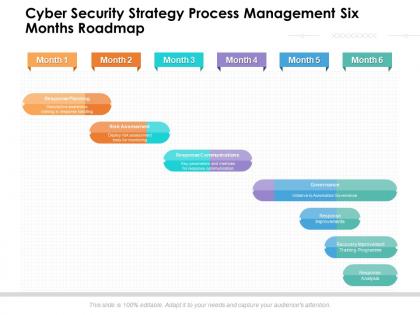 Cyber security strategy process management six months roadmap
Cyber security strategy process management six months roadmapPresenting Cyber Security Strategy Process Management Six Months Roadmap PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
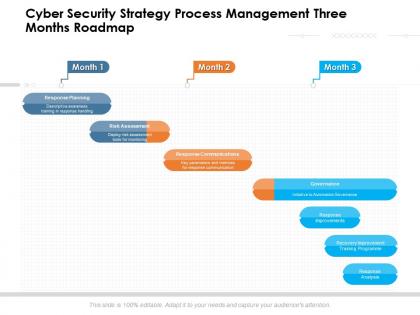 Cyber security strategy process management three months roadmap
Cyber security strategy process management three months roadmapPresenting Cyber Security Strategy Process Management Three Months Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Application security management process ppt powerpoint presentation guide cpb
Application security management process ppt powerpoint presentation guide cpbPresenting this set of slides with name Application Security Management Process Ppt Powerpoint Presentation Guide Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Application Security Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Process flow for cyber security service ppt powerpoint presentation files
Process flow for cyber security service ppt powerpoint presentation filesPresenting this set of slides with name Process Flow For Cyber Security Service Ppt Powerpoint Presentation Files. This is a three stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security processing ppt powerpoint presentation file design ideas cpb
Security processing ppt powerpoint presentation file design ideas cpbPresenting this set of slides with name Security Processing Ppt Powerpoint Presentation File Design Ideas Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Security Processing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security process with identify and react
Cyber security process with identify and reactPresenting this set of slides with name Cyber Security Process With Identify And React. This is a four stage process. The stages in this process are Identify, Protect, Detect, React. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.





