Powerpoint Templates and Google slides for Security Roadmap
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Roadmap Powerpoint Ppt Template Bundles
Cyber Security Roadmap Powerpoint Ppt Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cyber Security Roadmap Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
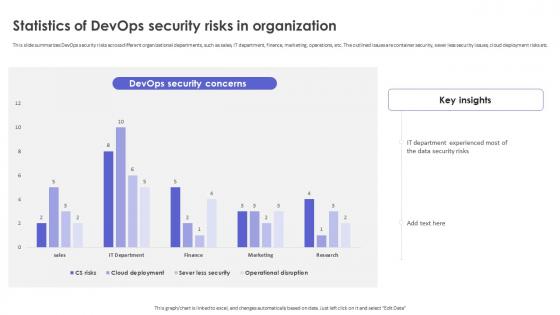 Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In Organization
Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In OrganizationThis slide summarizes DevOps security risks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined issues are container security, sever less security issues, cloud deployment risks etc. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In Organization. Dispense information and present a thorough explanation of Devops Security Risks Across, Organizational Departments, Finance, Marketing, Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roadmap for security guard services proposal ppt slides introduction
Roadmap for security guard services proposal ppt slides introductionIncrease audience engagement and knowledge by dispensing information using Roadmap For Security Guard Services Proposal Ppt Slides Introduction. This template helps you present information on six stages. You can also present information on Roadmap, Security Guard Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
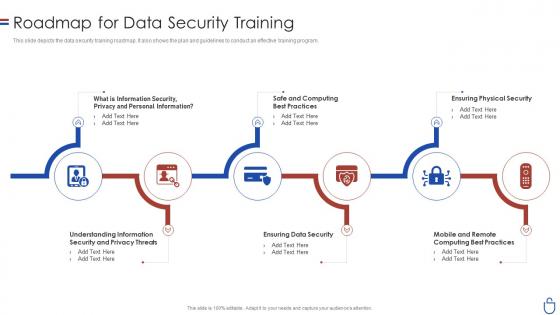 Data security it roadmap for data security training ppt slides grid
Data security it roadmap for data security training ppt slides gridThis slide depicts the data security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Data Security IT Roadmap For Data Security Training Ppt Slides Grid to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Information Security, Understanding Information, Security And Privacy Threats, Ensuring Data Security, Ensuring Physical Security, Safe And Computing Best Practices, using this template. Grab it now to reap its full benefits.
-
 Computer system security roadmap for computer security training
Computer system security roadmap for computer security trainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Computer System Security Roadmap For Computer Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ensuring Physical Security, Ensuring, Data Security, Mobile And Remote Computing, Safe And Computing, Security And Privacy Threats, using this template. Grab it now to reap its full benefits.
-
 Computer system security roadmap ppt powerpoint presentation slides visuals
Computer system security roadmap ppt powerpoint presentation slides visualsIncrease audience engagement and knowledge by dispensing information using Computer System Security Roadmap Ppt Powerpoint Presentation Slides Visuals. This template helps you present information on four stages. You can also present information on Roadmap, 2018 To 2020 using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web Gateway
Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Organizational, Requirements, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Establishing Effective Business Security Management Plan
Roadmap For Establishing Effective Business Security Management PlanThis slide showcases the roadmap for executing an effective business security management plan. This slide aims to help the business ensure sufficient security measures are put in place to avoid cyber attacks and data thefts. It includes steps such as risk assessment, framework development, plan reviews, etc.Presenting our set of slides with Roadmap For Establishing Effective Business Security Management Plan. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Security Assessment, Conduct Technology Evaluation, Implement Security Plan.
-
 Roadmap For Robust Information Security Plan
Roadmap For Robust Information Security PlanThis slide highlights roadmap for strategic information plan to manage threat and to avoid misuse of critical information of business. It involves building recovery plan, developing compliance plan, managing data, assessing risk and creating security team. Presenting our set of slides with Roadmap For Robust Information Security Plan. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Build Strong Recovery Plan, Assess Risk, Create Security Team.
-
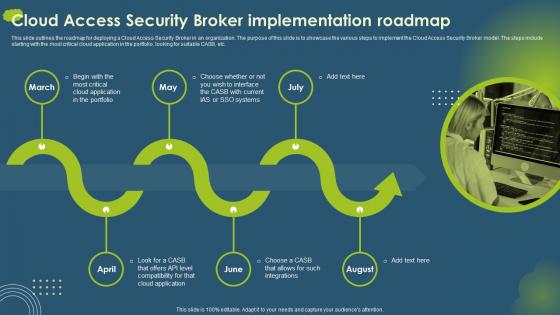 Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait
Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery PortraitThis slide outlines the roadmap for deploying a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to implement the Cloud Access Security Broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Critical Cloud Application, Compatibility, using this template. Grab it now to reap its full benefits.
-
 Roadmap Journey Of Securing Cloud And Digital Transformation
Roadmap Journey Of Securing Cloud And Digital TransformationThis slide demonstrates cloud and digital transformation roadmap for improving scalability by ensuring data security and agility. It includes phases such as setting objectives, evaluate alternatives, discover inventory, etc. Presenting our set of slides with Roadmap Journey Of Securing Cloud And Digital Transformation. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Setting Objectives, Evaluate Alternatives.
-
 ERP Security Management Implementation Roadmap
ERP Security Management Implementation RoadmapThis slide showcases the ERP security management implementation roadmap in SMEs. Its objective is to make the management ready to reach predefined goals. This slide includes project team, assessment, technological selection, business blueprint, test, etc. Presenting our well structured ERP Security Management Implementation Roadmap. The topics discussed in this slide are Build Alignment, Define ERP, Plan Project. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementation Roadmap For ERP Security Management
Implementation Roadmap For ERP Security ManagementThis slide showcases the implementation of roadmap security management in ERP. Its objective is to formulate a team and figure out the configuration level. This slide includes training, hardware evaluation, scenario training, protocol, etc. Presenting our set of slides with Implementation Roadmap For ERP Security Management. This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resolution Protocol, Figure Out Configuration, Testing Scenario.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From PhishingThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Technical Controls, Establish Policies And Procedures, Employee Training, Baseline Security Assessment, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Secure Access Service Edge Cloud Security Model
Roadmap To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Discover, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Roadmap To Implement Secure Access Service Edge
Sase Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Sase Security Roadmap To Implement Secure Access Service Edge. This template helps you present information on seven stages. You can also present information on Roadmap, Service, Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap To Implement Secure Access Service Edge Secure Access Service Edge Sase
Roadmap To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Secure Access Service Edge Secure Access Service Edge Sase. This template helps you present information on six stages. You can also present information on Environment, Solutions, Troubleshooting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Roadmap To Implement Secure Access Service Edge
SASE Network Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE Network Security Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Providers, Deployment, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Information Security Management System In Organization
Roadmap To Implement Information Security Management System In OrganizationThis slide represents roadmap that helps organizations implement system for information security management systems to protect sensitive data. It includes steps such as defining scope and objectives, identifying assets, recognizing risk, etc. Introducing our premium set of slides with Roadmap To Implement Information Security Management System In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recognize Risk, Make Improvement, Identify Mitigation Measures. So download instantly and tailor it with your information.
-
 Implementing Virtual Infrastructure Security Integration Roadmap
Implementing Virtual Infrastructure Security Integration RoadmapThis slide showcases timeline that assist businesses to implement virtual infrastructure to enhance data security integration and management. It includes carious phases such as resource virtualization, application virtualization, internal cloud and hybrid cloud. Introducing our premium set of slides with Implementing Virtual Infrastructure Security Integration Roadmap. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trusted Platform Incorporation, Zero Data Loss, Trusted Security. So download instantly and tailor it with your information.
-
 Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In Market
Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In MarketThis slide represents the roadmap for the development of cryptocurrency. The key steps include planning and research, design and development, testing and quality assurance, launch user acquisition, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Roadmap Of Development Of Cryptocurrency In Market. This template helps you present information on six stages. You can also present information on Post Launch Maintenance And Growth, Testing And Quality Assurance, Planning And Research, Design And Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Implementation Roadmap Next Generation CASB
Cloud Access Security Broker Implementation Roadmap Next Generation CASBThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Implementation Roadmap Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Portfolio, Cloud Application, Systems using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Roadmap For Firewall Security Integration In Business
Firewall Network Security Roadmap For Firewall Security Integration In BusinessThis slide showcases a roadmap to implement firewall security in an organization. This slide highlights the various steps businesses should take while implementing firewall security, such as assessing network requirements and risks, designing and deploying firewall architecture, and so on. Introducing Firewall Network Security Roadmap For Firewall Security Integration In Business to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use Antivirus Protection, Segmented Network, Avoid Outage using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Roadmap For Ethical Hacking Program
Ethical Hacking And Network Security Roadmap For Ethical Hacking ProgramThis slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master. Introducing Ethical Hacking And Network Security Roadmap For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap For Ethical Hacking, Ethical Hacking Training Program, Ethical Hacking Master, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Roadmap To Implement Secure Access Service Edge
SD WAN Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SD WAN Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Regularly, Transition, Troubleshooting And Assistance, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 Security Monitoring Event Monitoring Roadmap
Security Monitoring Event Monitoring RoadmapThis slide contains the roadmap for enhancing security event roadmap. Its objective is to control the amount of users and reduce attacks on the network. This slide includes transaction security, monitoring, limit event, data leakage, etc. Increase audience engagement and knowledge by dispensing information using Security Monitoring Event Monitoring Roadmap. This template helps you present information on Four stages. You can also present information on Digital Twin Construction, Network Construction, Monitoring Centres using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy
Devsecops Best Practices For Secure Roadmap For Devsecops Implementation StrategyThis slide highlights the project roadmap to implement the DevSecOps plan in an organization. The purpose of this slide is to showcase the different phases of the DevSecOps implementation plan, such as foundation and preparation, tool selection and integration, etc. Introducing Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Tool Selection And Integration, Compliance And Governance, Foundation And Preparation, Security As Code, using this template. Grab it now to reap its full benefits.
-
 Sase Model Roadmap To Implement Secure Access Service Edge
Sase Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing Sase Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Examine The Environment, Providers And Solutions, Implementation Regularly, using this template. Grab it now to reap its full benefits.
-
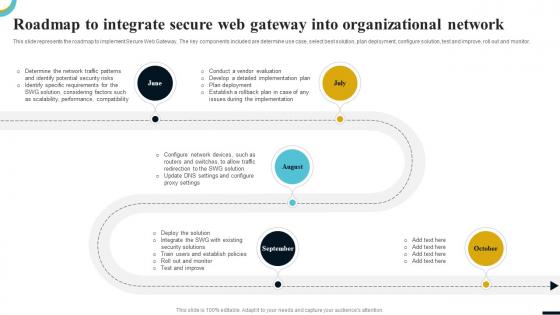 Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway
Internet Gateway Security IT Roadmap To Integrate Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Performance, Compatibility, Implementation, Plan Deployment, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Implementing Effective Web Security
Roadmap For Implementing Effective Web SecurityThis slide outlines the steps that an organization should take while conducting web security such as education, infrastructure security, etc. Presenting our set of slides with name Roadmap For Implementing Effective Web Security. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Application Security, Incident Response, Assessment And Planning.
-
 Cloud Access Security Broker Implementation Roadmap CASB Cloud Security
Cloud Access Security Broker Implementation Roadmap CASB Cloud SecurityThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Roadmap CASB Cloud Security. This template helps you present information on six stages. You can also present information on Cloud Access Security Broker, Cloud Application In The Portfolio, Implementation Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
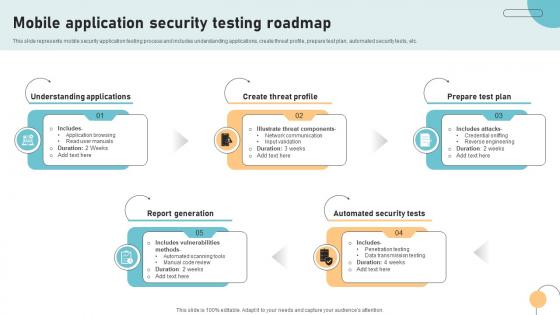 Mobile Application Security Testing Roadmap
Mobile Application Security Testing RoadmapThis slide represents mobile security application testing process and includes understanding applications, create threat profile, prepare test plan, automated security tests, etc. Presenting our set of slides with name Mobile Application Security Testing Roadmap. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understanding Applications, Report Generation, Create Threat Profile, Automated Security Tests, Prepare Test Plan.
-
 Five Step Roadmap To Implement Application Security
Five Step Roadmap To Implement Application SecurityThis slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. Introducing Five Step Roadmap To Implement Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Monitoring And Logging, Education And Planning, Five Step Roadmap, Application Security, using this template. Grab it now to reap its full benefits.
-
 DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps
DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOpsThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build or test, deploy, and monitor. Present the topic in a bit more detail with this DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps. Use it as a tool for discussion and navigation on Integrate Security, Encourage Developer Ownership, Static Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
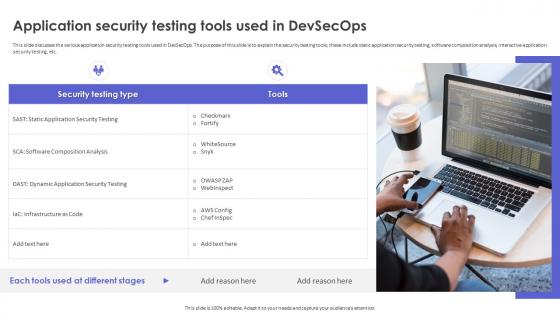 Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps
Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOpsThis slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Increase audience engagement and knowledge by dispensing information using Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps. This template helps you present information on one stages. You can also present information on Application Security Testing, Software Composition Analysis, Interactive Application Security Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model
Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model. Dispense information and present a thorough explanation of Boost Workflow Efficiency, Performance Metrics, Pipeline Security Working using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roadmap For Implementing Security Testing In Organization
Roadmap For Implementing Security Testing In OrganizationThis slide showcases the schedule for putting wireless LAN controllers into practice. The purpose of this slide is to highlight the installation plan for wireless LAN controllers such as need assessment and goal defining, infrastructure planning, etc. Introducing Roadmap For Implementing Security Testing In Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Testing, Infrastructure Planning, Installation Plan For Wireless, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Robust Information Security System Plan
Roadmap For Robust Information Security System PlanThis slide highlights roadmap for a strategic information system plan to manage threats and to avoid misuse of critical information of business. Presenting our set of slides with Roadmap For Robust Information Security System Plan. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Build Strong Recovery Plan, Manage Data, Assess Risk.
-
 Application Security Implementation Plan Five Step Roadmap To Implement Application Security
Application Security Implementation Plan Five Step Roadmap To Implement Application SecurityThis slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. Introducing Application Security Implementation Plan Five Step Roadmap To Implement Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Monitoring And Logging, Incident Response, Education And Planning, Application Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Roadmap To Implement Effective Endpoint Security
Endpoint Security Roadmap To Implement Effective Endpoint SecurityThis slide outlines the steps to deploy endpoint security which include recognizing known malware, reduce end user access, utilizing application control, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap To Implement Effective Endpoint Security. This template helps you present information on six stages. You can also present information on Utilize Sensible Application Control, Recognize And Avoid Known Malware, Block Dangerous Activity, Effective Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security
Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data SecurityThis slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security. This template helps you present information on five stages. You can also present information on Identify Sensitive Data, Implement Access Controls, Configure The Tokenization System, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat
Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about business cyber security attack recovery plan. It includes key steps such as setting time based recovery goals, impact and risk assessment, build recovery team, communication plan, recovery strategies implementation, etc. Introducing Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Communication Plan, Recovery Strategies Implementation, using this template. Grab it now to reap its full benefits.
-
 Blockchain Security Roadmap For Enterprise Setting
Blockchain Security Roadmap For Enterprise SettingPresenting our set of slides with Blockchain Security Roadmap For Enterprise Setting. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Access Control Methods, Distributed Transactional Responsibilities, Planning For Contingencies.
-
 Roadmap To Implement Robust OT Cyber Security
Roadmap To Implement Robust OT Cyber SecurityThis slide represents roadmap that guides companies to implement strong operational technology cybersecurity model for enhancing information protection. It includes various steps such as conducting OT threat assessment, know network and assets, etc. Presenting our set of slides with Roadmap To Implement Robust OT Cyber Security This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct OT Threat Assessment, Know Network And Assets, Publish OT Security Policy
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap For Mobile Security Implementation In Organization Mobile Security
Roadmap For Mobile Security Implementation In Organization Mobile SecurityThis slide highlights the different phases of the mobile security implementation plan, such as plan and research, update security policies, conduct training, etc. Introducing Roadmap For Mobile Security Implementation In Organization Mobile Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Malware Detection And Prevention, Authentication And Encryption using this template. Grab it now to reap its full benefits.
-
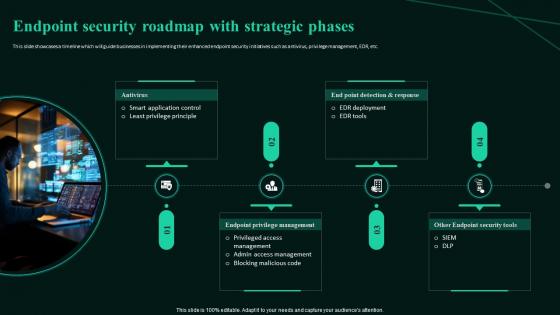 Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases a timeline which will guide businesses in implementing their enhanced endpoint security initiatives such as antivirus, privilege management, EDR, etc.Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on one stages. You can also present information on Other Endpoint Security Tools, Endpoint Privilege Management, Antivirus, End Point Detection And Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Security Upgradation Roadmap For Implementing Web Security In Organization
Web Security Upgradation Roadmap For Implementing Web Security In OrganizationThis slide outlines the steps that an organization should take while conducting web security which include education, infrastructure security, etc. Introducing Web Security Upgradation Roadmap For Implementing Web Security In Organization to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Education And Planning, Infrastructure Security, Incident Response, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Roadmap For Implementing Email Security Policies
Email Security Best Practices Roadmap For Implementing Email Security PoliciesThis slide represents the roadmap to implement email security policies. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Roadmap For Implementing Email Security Policies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Trustworthy Email Provider, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Implementing Web Security In Organization
Roadmap For Implementing Web Security In OrganizationThis slide outlines the steps that an organization should take while conducting web security such as education, infrastructure security, etc. Introducing Roadmap For Implementing Web Security In Organization to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Education And Planning, Infrastructure Security, Application Security, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS
Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SSThis slide showcases roadmap that can help to implement mobile security solutions. Its key elements are estimated budget, duration of different phases etc. Present the topic in a bit more detail with this Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Device Security Budget, Device Security Solutions, Techniques Effectiveness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roadmap for electronic information security training
Roadmap for electronic information security trainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Roadmap For Electronic Information Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Information Security, Privacy And Personal Information, Understanding Information Security And Privacy Threats, Safe And Computing Best Practices, Ensuring Physical Security, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorism
Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorismThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism. This template helps you present information on four stages. You can also present information on Creating Personal Accounts, Awareness Training Employees, Keep Hardware And Software Updated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
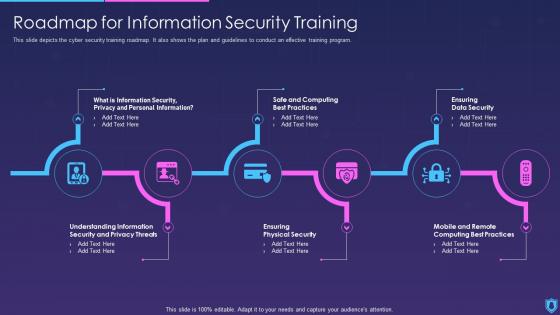 Information Security Roadmap For Information Security Training
Information Security Roadmap For Information Security TrainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Increase audience engagement and knowledge by dispensing information using Information Security Roadmap For Information Security Training. This template helps you present information on six stages. You can also present information on Information Security, Computing, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
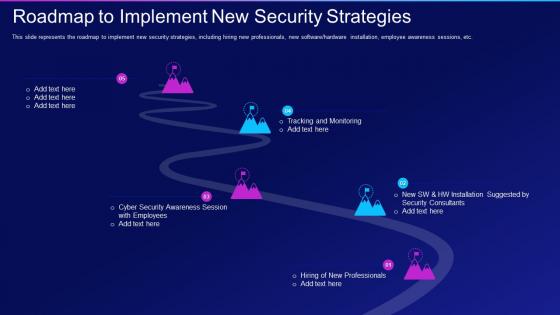 Hacking it roadmap to implement new security strategies
Hacking it roadmap to implement new security strategiesThis slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. Increase audience engagement and knowledge by dispensing information using Hacking It Roadmap To Implement New Security Strategies. This template helps you present information on five stages. You can also present information on Roadmap To Implement New Security Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Roadmap For Network Security Training
Network Security Roadmap For Network Security TrainingThis slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Increase audience engagement and knowledge by dispensing information using Network Security Roadmap For Network Security Training. This template helps you present information on six stages. You can also present information on Information, Physical Security, Data Security, Practices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Roadmap For Information Technology Security Training
Information Technology Security Roadmap For Information Technology Security TrainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Information Technology Security Roadmap For Information Technology Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
 Implementing Mobile Device Security Framework Roadmap Android Device Security Management
Implementing Mobile Device Security Framework Roadmap Android Device Security ManagementThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Framework Roadmap Android Device Security Management. Use it as a tool for discussion and navigation on Implement Enterprise, Security Program, Implement Security Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration
Security Hacker Roadmap To Implement New Security Strategies Ppt InspirationThis slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. Introducing Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Consultants, Tracking And Monitoring, Cyber Security Awareness Session, using this template. Grab it now to reap its full benefits.




