Powerpoint Templates and Google slides for Security Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence
Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk OccurrenceThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence Use it as a tool for discussion and navigation on Parameters, Impact, Probability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 Mobile Application Security Risk Assessment
Mobile Application Security Risk AssessmentThis slide demonstrates mobile application security to assess risks and includes improper platform usage, insecure data storage, and insecure communication. Presenting our set of slides with name Mobile Application Security Risk Assessment. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Improper Platform Usage, Insecure Data Storage, Insecure Communication.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Addressing Mobile Application Security Gap For Risk Protection
Addressing Mobile Application Security Gap For Risk ProtectionFollowing slide showcases application security vulnerabilities of mobiles for risk protection. It further includes factors such as poor server-side controls, accidental data leak, poor authorization alongside description, solution, etc. Introducing our Addressing Mobile Application Security Gap For Risk Protection set of slides. The topics discussed in these slides are Poor Server Side Controls, Accidental Data Leak, Poor Authorization, Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V
ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Introducing ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reporting After Attack, Cybersecurity Training, Developing Policies, using this template. Grab it now to reap its full benefits.
-
 ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS V
ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various ChatGPT use cases for streamlining and automating the cybersecurity operations of organization. Its key elements are establish security policies, automate repetitive tasks and identification of vulnerabilities. Increase audience engagement and knowledge by dispensing information using ChatGPT Use Cases For Streamlining Security Opportunities And Risks Of ChatGPT AI SS V. This template helps you present information on three stages. You can also present information on Establish Security Policies And Sops, Automate Repetitive Tasks, Identify Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS V
Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various disadvantages of leveraging ChatGPT for security operations. Its key elements are information inaccuracy, over-reliance on automation, input misinterpretation, output bias and confidentially concerns. Introducing Limitations Of Leveraging ChatGPT For Security Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality Concerns, Over-Reliance On Automation, Output Bias, using this template. Grab it now to reap its full benefits.
-
 Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SS
Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SSThe following slide showcases major security risks related to Bitcoin crypto wallets. It includes elements such as phishing attacks, malware, exchange hacks, user error, fake links, credential theft, infected attachments karma forgot passwords, private keys, etc. Introducing Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Malware, Exchange Hacks, using this template. Grab it now to reap its full benefits.
-
 Third Party Risk Management Methods In Information Security
Third Party Risk Management Methods In Information SecurityThis slide highlights strategies to control third-party risk in information security. The purpose of this slide is to aid organizations in identifying areas for improvement in their security practices. It includes elements such as vendor assessment, risk classification, etc. Presenting our set of slides with Third Party Risk Management Methods In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Assessment, Contractual Agreements, Maintain Records, Risk Classification
-
 Email Security Risks And Mitigation Plan
Email Security Risks And Mitigation PlanThis slide covers email security risks and its mitigation plan which includes risks such as phishing, evolving phishing, domain squatting and malware. Presenting our set of slides with Email Security Risks And Mitigation Plan. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Security, Risks, Mitigation Plan.
-
 Website Security Risks And Penetration Testing Report
Website Security Risks And Penetration Testing ReportThis template showcases advanced penetration testing report for organization website. It covers factors such as vulnerabilities, severity and risk level. Presenting our well structured Website Security Risks And Penetration Testing Report. The topics discussed in this slide are Website Security Risks, Penetration Testing Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Key Types Of Endpoint Security Risks
Endpoint Security Key Types Of Endpoint Security RisksThis slide highlights the various types of endpoint security risks such as phishing, device loss, outdated patches, malware ads, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Key Types Of Endpoint Security Risks. This template helps you present information on seven stages. You can also present information on Device Loss, Outdated Patches, Drive By Download, Ransomware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
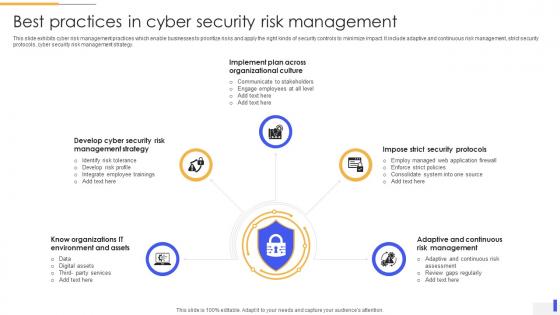 Best Practices In Cyber Security Risk Management
Best Practices In Cyber Security Risk ManagementThis slide exhibits cyber risk management practices which enable businesses to prioritize risks and apply the right kinds of security controls to minimize impact. It include adaptive and continuous risk management, strict security protocols, cyber security risk management strategy. Introducing our premium set of slides with Best Practices In Cyber Security Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Know Organizations IT Environment And Assets. Impose Strict Security Protocols, Adaptive And Continuous Risk Management . So download instantly and tailor it with your information.
-
 Computer Security Icon For Cyber Risk Management
Computer Security Icon For Cyber Risk ManagementPresenting our set of slides with Computer Security Icon For Cyber Risk Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Security Icon, Cyber Risk Management.
-
 Cyber Security Risk Management Lifecycle
Cyber Security Risk Management LifecycleFollowing slide highlights risk management lifecycle of cyber security for maintaining customer trust. It further covers evaluate, analyse, implement and decision and further includes preparing cyber security policy, risk in data collection, etc. Introducing our premium set of slides with Cyber Security Risk Management Lifecycle. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement, Evaluate, Decision. So download instantly and tailor it with your information.
-
 Cyber Security Risk Management Plan With Prevention Strategies
Cyber Security Risk Management Plan With Prevention StrategiesFollowing slide includes cyber security plan to systematically assess and mitigation cyber risk within organisation. It further covers, description, risk level, responsible manager, threats and prevention strategies. Introducing our Cyber Security Risk Management Plan With Prevention Strategies set of slides. The topics discussed in these slides are Risk Level, Responsible Manager, Prevention Strategies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Cyber Security Risk Management Plan
Supply Chain Cyber Security Risk Management PlanThis slide includes cyber security management plan which can be used by supply chain managers to manage security threats. It includes various strategies such as upgrade minimum security baseline, assess process for further risks, and educate employees. Presenting our well structured Supply Chain Cyber Security Risk Management Plan. The topics discussed in this slide are Supervisor, Action Required, Mitigation Strategy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Mobile Application Security Vulnerabilities For Effective Risk Protection
Addressing Mobile Application Security Vulnerabilities For Effective Risk ProtectionFollowing slide showcases application security vulnerabilities of mobiles for risk protection. It further includes factors such as poor server side controls, accidental data leak, poor authorization along side description, solution, etc. Introducing our Addressing Mobile Application Security Vulnerabilities For Effective Risk Protection set of slides. The topics discussed in these slides are Accidental Data Leak, Poor Authorization, Poor Server Side ControlsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
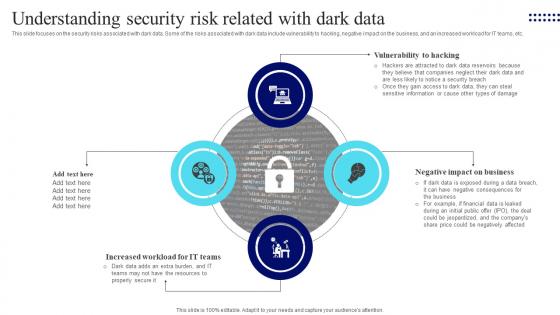 Management Of Redundant Data Understanding Security Risk Related With Dark Data
Management Of Redundant Data Understanding Security Risk Related With Dark DataThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Management Of Redundant Data Understanding Security Risk Related With Dark Data to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Workload For IT Teams, Negative Impact On Business, Vulnerability To Hacking, using this template. Grab it now to reap its full benefits.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Enhance OT Security From Cyber Risks
Checklist To Enhance OT Security From Cyber RisksThis slide represents checklist that assist companies to optimize their OT security against multiple cyber threats efficiently. It includes various steps such as separate IT and OT assets, Restrict industrial security, document all communication, etc. Introducing our Checklist To Enhance OT Security From Cyber Risks set of slides. The topics discussed in these slides are Checklist, Status, PhaseThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Cloud Data Migration Security Risks And Solutions
Cloud Data Migration Security Risks And SolutionsThe below slide highlights the multiple security risks associated with cloud data migration along with the potential solutions to eliminate them. The various risks mentioned are unauthorized access, data breaches, weak data encryption, etc. Introducing our Cloud Data Migration Security Risks And Solutions set of slides. The topics discussed in these slides are Unauthorized Access, Data Breaches, Weak Data Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 NFC Technology Risks Associated With Mobile Security Mobile Security
NFC Technology Risks Associated With Mobile Security Mobile SecurityThis slide discusses the NFC technology risks associated with mobile security which includes data tampering, data interception, smartphone malware, etc. Increase audience engagement and knowledge by dispensing information using NFC Technology Risks Associated With Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Installing Patches, Add Features, Systems Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unsecured Wi Fi Network Security Risks Mobile Security
Unsecured Wi Fi Network Security Risks Mobile SecurityThis slide highlights the risks associated with unsecured Wi-Fi network which include free wi-fi risks, security threats and data exposure. Introducing Unsecured Wi Fi Network Security Risks Mobile Security to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Apps And Websites, Phishing using this template. Grab it now to reap its full benefits.
-
 Pam Cyber Security Risk And Adoption Scorecard
Pam Cyber Security Risk And Adoption ScorecardThis slide represents scorecard that assist companies to measure adoption of PAM cybersecurity to enhance their data protection. It includes various components such as work stream type, preferred trends, target ETS , etc. Presenting our well structured Pam Cyber Security Risk And Adoption Scorecard. The topics discussed in this slide are Adoption Scorecard, Platform, Deployment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS
Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SSThis slide defines the process of conducting a comprehensive risk assessment to identify potential threats to the insurance organizations security, utilizing automated platforms for efficient risk identification. Present the topic in a bit more detail with this Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS. Use it as a tool for discussion and navigation on Underwriting Errors, Failure To Meet Regulatory Requirements, Poor Customer Service, Internal Operational Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Cyber Security In Banking To Reduce Risks
Checklist For Cyber Security In Banking To Reduce RisksThis slide represents banking cyber security checklist in minimizing risks. This slide aims to regularly reviewing and updating cyber security measures to stay ahead of evolving threats. It includes various elements such as activities, comments, threat type, etc. Introducing our Checklist For Cyber Security In Banking To Reduce Risks set of slides. The topics discussed in these slides are Activities, Daily, Weekly. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Risk Factors In Banking
Cyber Security Risk Factors In BankingThis slide represents emerging cyber security risks faced in banking industry. This slide aims to report bank network security risk related to growth of service providers incorporated into network. It includes various threats such as supply chain attacks, phishing, ransomware attacks, etc. Presenting our set of slides with Cyber Security Risk Factors In Banking. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Engineering Attacks, Phishing, Supply Chain Networks.
-
 Factors Contributing To Rising Cyber Security Risks In Finance And Banking
Factors Contributing To Rising Cyber Security Risks In Finance And BankingThis slide represents factors affecting cyber security concerns in finance and banking. It aims to continually invest in cyber security measures, employee training, and threat intelligence to protect from evolving landscape of cyber security risks. It includes various elements such as factors, description and strategies to reduce risks. Presenting our set of slides with Factors Contributing To Rising Cyber Security Risks In Finance And Banking. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Third Party Vendors, Onboarding New Technologies, Cloud Cybercrimes.
-
 Factors To Consider For Cyber Security Risks In Banking
Factors To Consider For Cyber Security Risks In BankingThis slide represents key considerations for cyber security concerns in banking. It aims to continually assess and adapt cyber security strategies to address evolving threats and ensure protection of sensitive financial and customer data. It includes various approaches such as cloud vulnerabilities, endpoint security, etc. Introducing our premium set of slides with Factors To Consider For Cyber Security Risks In Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Emerging Technology, Vulnerabilities Cloud, Endpoint Security. So download instantly and tailor it with your information.
-
 Strategies To Mitigate Cyber Security Risks In Banking Sector
Strategies To Mitigate Cyber Security Risks In Banking SectorThis slide represents approaches to reduce risk of cyber security in banking sector. This template aims to cyber security risks in banking sector to protect sensitive financial data and maintain customer trust. It includes various strategies such as risk determination, mitigating identity theft and fraud, etc. Introducing our premium set of slides with Strategies To Mitigate Cyber Security Risks In Banking Sector. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Privacy Protection, Application Control, Risk Determination. So download instantly and tailor it with your information.
-
 Third Party Cyber Security Risk Icon
Third Party Cyber Security Risk IconIntroducing our premium set of slides with Third Party Cyber Security Risk Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party, Cyber Security, Risk Icon. So download instantly and tailor it with your information.
-
 Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS
Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SSThis slide represents best practices for mitigating threats that originate from within the targeted organization. It includes best practices such as perform enterprise-wide risk assessment etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enforce Policies And Controls, Establish Physical Security, Harden Network Perimeter Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security
Web Security Upgradation Risks And Mitigation Strategies While Deploying Web SecurityThe purpose of this slide is to discuss the challenges faced while implementing web security such as alert overload, skill gap, etc. Present the topic in a bit more detail with this Web Security Upgradation Risks And Mitigation Strategies While Deploying Web Security. Use it as a tool for discussion and navigation on Risk, Impact, Mitigation Strategies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies For Chatbot Security Risks
Mitigation Strategies For Chatbot Security RisksThis slide shows information regarding various types of security risks associated with chatbots which are threats and vulnerabilities such as ransomware, malware, unencrypted communications, back-door access by hackers, etc. It also includes mitigation strategies to overcome these issues. Introducing our premium set of slides with Mitigation Strategies For Chatbot Security Risks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mitigation Strategies, Biometric Authentication, Two Factor Authentication. So download instantly and tailor it with your information.
-
 Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots
Construction Risk Management Software For Security Of Workers Revolutionizing Construction With RobotsThis slide showcases various softwares to easily conduct inspections and proactively identify risks. It includes of tools such as Raken, Zepth, etc.Present the topic in a bit more detail with this Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots. Use it as a tool for discussion and navigation on Key Features, Pros, Cons, Free Trial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organization Security Risk Assessment Matrix
Organization Security Risk Assessment MatrixThis slide provide a risk assessment matrix for organizations to assess the threat vulnerability. The various outcomes mentioned are insignificant, minor, moderate, major, and severe. Introducing our Organization Security Risk Assessment Matrix set of slides. The topics discussed in these slides are Insignificant, Minor, Moderate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPP
Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPPPresenting our Security Concern Of Bioprinting Risks In Powerpoint And Google Slides CPP PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Concern Of Bioprinting Risks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPP
Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPPPresenting Ambient Intelligent Cyber Security Risk In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Ambient Intelligent Cyber Security Risk. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Income securities risk and return level ppt background graphics
Income securities risk and return level ppt background graphicsPresenting income securities risk and return level ppt background graphics. This is a income securities risk and return level ppt background graphics. This is a four stage process. The stages in this process are risk, cash, fixed interest, property, shares.
-
 Strategic security risk management ppt idea
Strategic security risk management ppt ideaPresenting strategic security risk management ppt idea. This is a strategic security risk management ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.
-
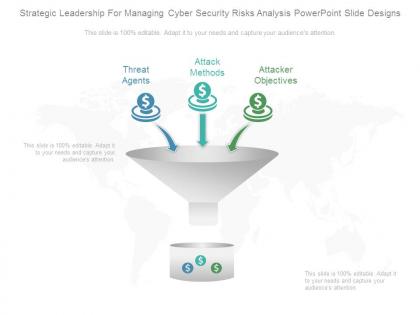 Strategic leadership for managing cyber security risks analysis powerpoint slide designs
Strategic leadership for managing cyber security risks analysis powerpoint slide designsPresenting strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
-
 Security risk assessment methodology analysis ppt powerpoint image
Security risk assessment methodology analysis ppt powerpoint imagePresenting security risk assessment methodology analysis ppt powerpoint image. This is a security risk assessment methodology analysis ppt powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.
-
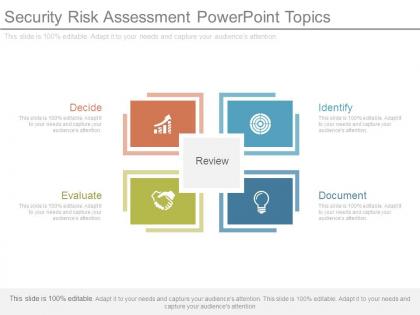 Security risk assessment powerpoint topics
Security risk assessment powerpoint topicsPresenting security risk assessment powerpoint topics. This is a security risk assessment powerpoint topics. This is a four stage process. The stages in this process are identify, document, evaluate, decide, review.
-
 Current security infrastructure effective information security risk management process
Current security infrastructure effective information security risk management processMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Current Security Infrastructure Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset Management, Incident Mitigation Plan, Incident Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security dashboard effective information security risk management process
Information security dashboard effective information security risk management processFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Present the topic in a bit more detail with this Information Security Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Analysis Progress Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security information security risk management dashboard
Effective information security information security risk management dashboardFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Effective Information Security Information Security Risk Management Dashboard. Dispense information and present a thorough explanation of Risk Threshold, Risk Analysis, Progress Response, Progress Risks Threshold using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact of information security risk management on company
Impact of information security risk management on companyMentioned slide graphically depicts before and after impact of information security risk management on a company. The various points covered in the slide are increased costs, operational disruption, reputational damage, improved company credentials, faster recovery time etc. Introducing our Impact Of Information Security Risk Management On Company set of slides. The topics discussed in these slides are Network, Security, Risk. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk management challenges and solutions
Information security risk management challenges and solutionsMentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber adversaries, tracking sensitive data flows. Introducing our Information Security Risk Management Challenges And Solutions set of slides. The topics discussed in these slides are Measuring, Service, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
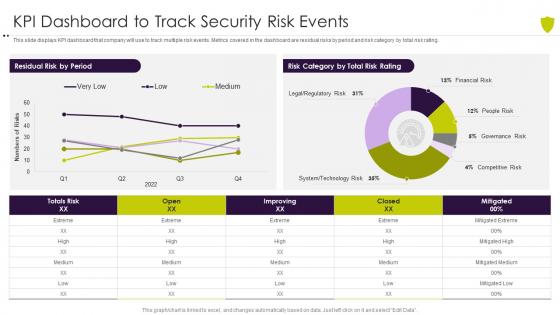 Kpi dashboard to track security risk events managing cyber risk in a digital age
Kpi dashboard to track security risk events managing cyber risk in a digital ageThis slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Track Security Risk Events Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of KPI Dashboard To Track Security Risk Events using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat dashboard with current risks and security service
Cyber threat dashboard with current risks and security serviceThe following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Presenting our well structured Cyber Threat Dashboard With Current Risks And Security Service. The topics discussed in this slide are Current Risks, Current Threats, Security Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization
Information Security Detail Impact Information Security Can Reduce Risk Data Breach OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization. Dispense information and present a thorough explanation of Organization, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Kpi Dashboard To Track Security Risk Events
Information Security Program Cybersecurity Kpi Dashboard To Track Security Risk EventsThis slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Kpi Dashboard To Track Security Risk Events. Dispense information and present a thorough explanation of KPI Dashboard To Track Security Risk Events using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions
Information Security Program Risk Management Kpi Dashboard With Loss Events And ActionsFollowing slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an outstanding presentation on the topic using this Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions. Dispense information and present a thorough explanation of Management, Dashboard, Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Current Security Infrastructure
Risk Management Framework For Information Security Current Security InfrastructureMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Risk Management Framework For Information Security Current Security Infrastructure. Use it as a tool for discussion and navigation on Actual Target Met, Performance, Target To Be Met, Asset Management. This template is free to edit as deemed fit for your organization. Therefore download it now.





