Powerpoint Templates and Google slides for Security Risk Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
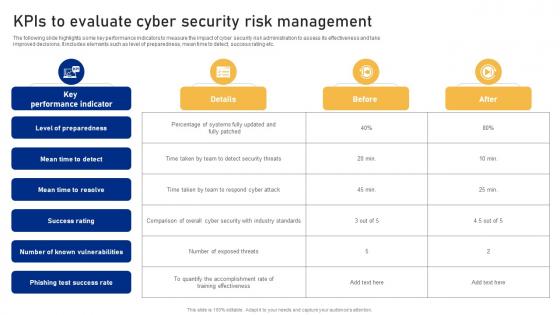
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Risk Management Training Program
Information Security And Risk Management Training ProgramThis slide showcases the successful information security and risk management training outline. It include details such as threats and vulnerabilities, etc. Presenting our well structured Information Security And Risk Management Training Program. The topics discussed in this slide are Training, Vulnerabilities, Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Organizational Security Risk Analysis And Management
Organizational Security Risk Analysis And ManagementThis slide shows organizational risk analysis by reviewing security threats and audit findings. The purpose of this slide is to help businesses in strengthening their security management system. Analysis is conducting by reviewing security threats, risk factors and management techniques. Presenting our well structured Organizational Security Risk Analysis And Management. The topics discussed in this slide are Security, Factors, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V
Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS VIntroducing Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cyber Security, Risk Management Process, using this template. Grab it now to reap its full benefits.
-
 KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment
KPIS To Evaluate Cyber Security Risk Management Cyber Risk AssessmentThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment Use it as a tool for discussion and navigation on Performance Indicator, Success Rating, Risk Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness
Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security AwarenessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Minimizes Malware Infection, Security Requirements, Internal Risks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
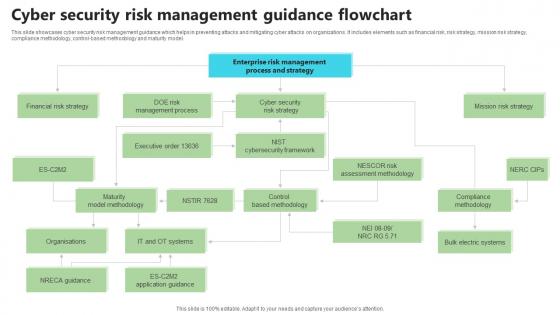 Cyber Security Risk Management Guidance Flowchart
Cyber Security Risk Management Guidance FlowchartThis slide showcases cyber security risk management guidance which helps in preventing attacks and mitigating cyber attacks on organizations. It includes elements such as financial risk, risk strategy, mission risk strategy, compliance methodology, control-based methodology and maturity model. Introducing our Cyber Security Risk Management Guidance Flowchart set of slides. The topics discussed in these slides are Financial Risk Strategy, Compliance Methodology, Mission Risk Strategy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices Of SaaS Security Risk Management
Best Practices Of SaaS Security Risk ManagementThis slide showcases the practices of SaaS security risk management. Its purpose is to protect critical workloads to ensure compliance. This slide includes vulnerability identification, analysis, risk assessment and remediation. Introducing Best Practices Of SaaS Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Identification, Remediation, Risk Assessment, Analysis, using this template. Grab it now to reap its full benefits.
-
 Cloud Cyber Security SaaS Risk Management
Cloud Cyber Security SaaS Risk ManagementThis slide showcases the cloud cyber security SaaS risk management. Its aim is to control profile and manage the risk involved. This slide includes authorization, monitor, cloud based, continuously monitor, etc. Introducing Cloud Cyber Security SaaS Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Control Profiles, Cloud Security Risk Management, Security Categorization, using this template. Grab it now to reap its full benefits.
-
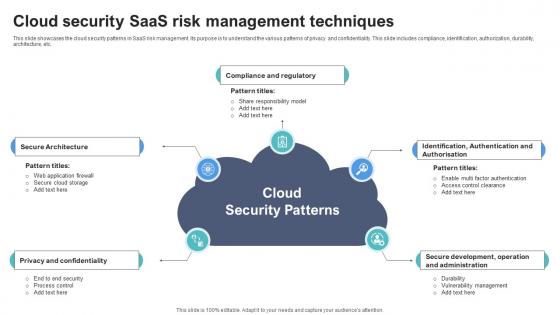 Cloud Security SaaS Risk Management Techniques
Cloud Security SaaS Risk Management TechniquesThis slide showcases the cloud security patterns in SaaS risk management. Its purpose is to understand the various patterns of privacy and confidentiality. This slide includes compliance, identification, authorization, durability, architecture, etc. Introducing Cloud Security SaaS Risk Management Techniques to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Architecture, Privacy And Confidentiality, Cloud Security Patterns, Compliance And Regulatory, using this template. Grab it now to reap its full benefits.
-
 Principles Of SaaS Security Risk Management
Principles Of SaaS Security Risk ManagementThis slide showcases the principles of SaaS risk based security management. Its aim is to secure infrastructure for assessing risk. This slide includes network control, VM management, data protection, incident, reliability, access management, etc. Present the topic in a bit more detail with this Principles Of SaaS Security Risk Management. Use it as a tool for discussion and navigation on Access Management, Network Control, Perimeter Network Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
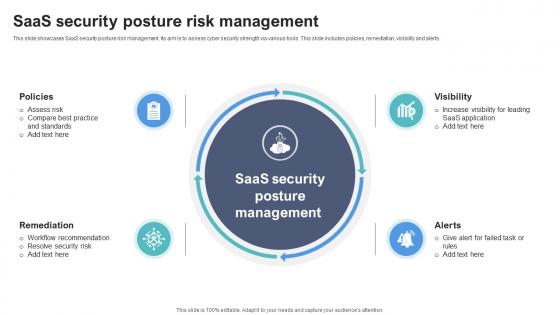 SaaS Security Posture Risk Management
SaaS Security Posture Risk ManagementThis slide showcases SaaS security posture risk management. Its aim is to assess cyber security strength via various tools. This slide includes policies, remediation, visibility and alerts. Increase audience engagement and knowledge by dispensing information using SaaS Security Posture Risk Management. This template helps you present information on four stages. You can also present information on Visibility, Policies, Remediation, Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
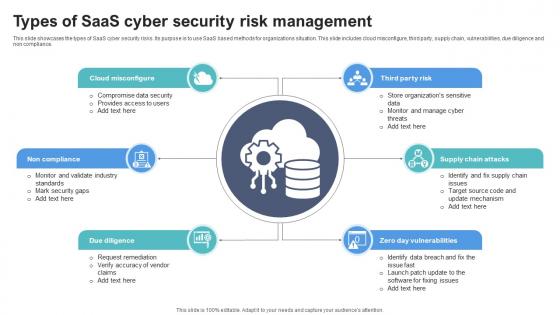 Types Of SaaS Cyber Security Risk Management
Types Of SaaS Cyber Security Risk ManagementThis slide showcases the types of SaaS cyber security risks. Its purpose is to use SaaS based methods for organizations situation. This slide includes cloud misconfigure, third party, supply chain, vulnerabilities, due diligence and non compliance. Increase audience engagement and knowledge by dispensing information using Types Of SaaS Cyber Security Risk Management. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Zero Day Vulnerabilities, Due Diligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Containerization Technology Container Security Essentials To Manage Risks
Containerization Technology Container Security Essentials To Manage RisksThis slide represents the various important factors of container security to manage environmental risks. The purpose of this slide is to outline the essentials of container security to manage risks, such as configuration, automation, container security solutions, and cloud and network security. Present the topic in a bit more detail with this Containerization Technology Container Security Essentials To Manage Risks. Use it as a tool for discussion and navigation on Dashboard To Retrieve Ongoing, Time Series Data Metrics, Containers Operating,Container Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Third Party Risk Management Methods In Information Security
Third Party Risk Management Methods In Information SecurityThis slide highlights strategies to control third-party risk in information security. The purpose of this slide is to aid organizations in identifying areas for improvement in their security practices. It includes elements such as vendor assessment, risk classification, etc. Presenting our set of slides with Third Party Risk Management Methods In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Assessment, Contractual Agreements, Maintain Records, Risk Classification
-
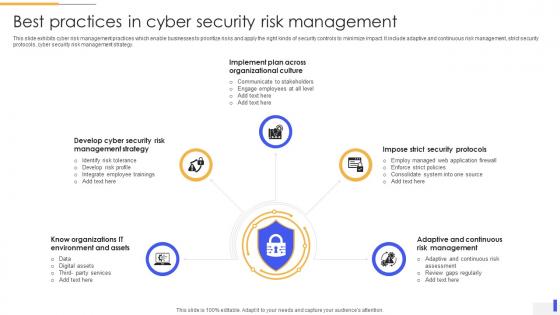 Best Practices In Cyber Security Risk Management
Best Practices In Cyber Security Risk ManagementThis slide exhibits cyber risk management practices which enable businesses to prioritize risks and apply the right kinds of security controls to minimize impact. It include adaptive and continuous risk management, strict security protocols, cyber security risk management strategy. Introducing our premium set of slides with Best Practices In Cyber Security Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Know Organizations IT Environment And Assets. Impose Strict Security Protocols, Adaptive And Continuous Risk Management . So download instantly and tailor it with your information.
-
 Computer Security Icon For Cyber Risk Management
Computer Security Icon For Cyber Risk ManagementPresenting our set of slides with Computer Security Icon For Cyber Risk Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Security Icon, Cyber Risk Management.
-
 Cyber Security Risk Management Lifecycle
Cyber Security Risk Management LifecycleFollowing slide highlights risk management lifecycle of cyber security for maintaining customer trust. It further covers evaluate, analyse, implement and decision and further includes preparing cyber security policy, risk in data collection, etc. Introducing our premium set of slides with Cyber Security Risk Management Lifecycle. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement, Evaluate, Decision. So download instantly and tailor it with your information.
-
 Cyber Security Risk Management Plan With Prevention Strategies
Cyber Security Risk Management Plan With Prevention StrategiesFollowing slide includes cyber security plan to systematically assess and mitigation cyber risk within organisation. It further covers, description, risk level, responsible manager, threats and prevention strategies. Introducing our Cyber Security Risk Management Plan With Prevention Strategies set of slides. The topics discussed in these slides are Risk Level, Responsible Manager, Prevention Strategies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Cyber Security Risk Management Plan
Supply Chain Cyber Security Risk Management PlanThis slide includes cyber security management plan which can be used by supply chain managers to manage security threats. It includes various strategies such as upgrade minimum security baseline, assess process for further risks, and educate employees. Presenting our well structured Supply Chain Cyber Security Risk Management Plan. The topics discussed in this slide are Supervisor, Action Required, Mitigation Strategy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
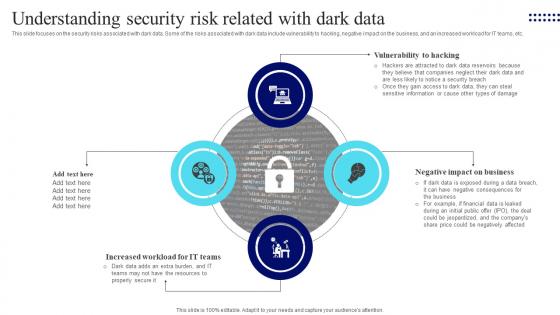 Management Of Redundant Data Understanding Security Risk Related With Dark Data
Management Of Redundant Data Understanding Security Risk Related With Dark DataThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Management Of Redundant Data Understanding Security Risk Related With Dark Data to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Workload For IT Teams, Negative Impact On Business, Vulnerability To Hacking, using this template. Grab it now to reap its full benefits.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS
Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SSThis slide defines the process of conducting a comprehensive risk assessment to identify potential threats to the insurance organizations security, utilizing automated platforms for efficient risk identification. Present the topic in a bit more detail with this Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS. Use it as a tool for discussion and navigation on Underwriting Errors, Failure To Meet Regulatory Requirements, Poor Customer Service, Internal Operational Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots
Construction Risk Management Software For Security Of Workers Revolutionizing Construction With RobotsThis slide showcases various softwares to easily conduct inspections and proactively identify risks. It includes of tools such as Raken, Zepth, etc.Present the topic in a bit more detail with this Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots. Use it as a tool for discussion and navigation on Key Features, Pros, Cons, Free Trial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic security risk management ppt idea
Strategic security risk management ppt ideaPresenting strategic security risk management ppt idea. This is a strategic security risk management ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.
-
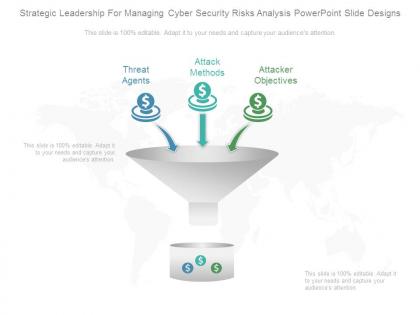 Strategic leadership for managing cyber security risks analysis powerpoint slide designs
Strategic leadership for managing cyber security risks analysis powerpoint slide designsPresenting strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
-
 Current security infrastructure effective information security risk management process
Current security infrastructure effective information security risk management processMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Current Security Infrastructure Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset Management, Incident Mitigation Plan, Incident Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security dashboard effective information security risk management process
Information security dashboard effective information security risk management processFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Present the topic in a bit more detail with this Information Security Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Analysis Progress Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security information security risk management dashboard
Effective information security information security risk management dashboardFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Effective Information Security Information Security Risk Management Dashboard. Dispense information and present a thorough explanation of Risk Threshold, Risk Analysis, Progress Response, Progress Risks Threshold using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact of information security risk management on company
Impact of information security risk management on companyMentioned slide graphically depicts before and after impact of information security risk management on a company. The various points covered in the slide are increased costs, operational disruption, reputational damage, improved company credentials, faster recovery time etc. Introducing our Impact Of Information Security Risk Management On Company set of slides. The topics discussed in these slides are Network, Security, Risk. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk management challenges and solutions
Information security risk management challenges and solutionsMentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber adversaries, tracking sensitive data flows. Introducing our Information Security Risk Management Challenges And Solutions set of slides. The topics discussed in these slides are Measuring, Service, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
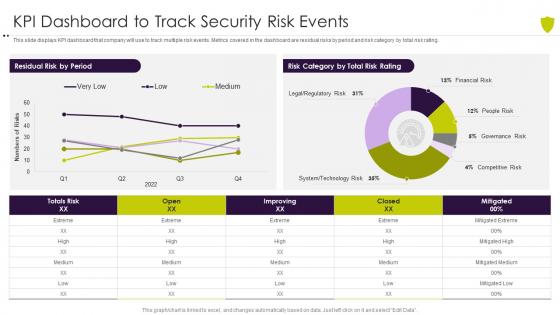 Kpi dashboard to track security risk events managing cyber risk in a digital age
Kpi dashboard to track security risk events managing cyber risk in a digital ageThis slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Track Security Risk Events Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of KPI Dashboard To Track Security Risk Events using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions
Information Security Program Risk Management Kpi Dashboard With Loss Events And ActionsFollowing slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an outstanding presentation on the topic using this Information Security Program Risk Management Kpi Dashboard With Loss Events And Actions. Dispense information and present a thorough explanation of Management, Dashboard, Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Current Security Infrastructure
Risk Management Framework For Information Security Current Security InfrastructureMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Risk Management Framework For Information Security Current Security Infrastructure. Use it as a tool for discussion and navigation on Actual Target Met, Performance, Target To Be Met, Asset Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Impact On Security Infrastructure
Risk Management Framework For Information Security Impact On Security InfrastructureMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Impact On Security Infrastructure. Dispense information and present a thorough explanation of Actual Target Met, Performance, Target to Be Met, Target Met after Introducing, Risk Assessment Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Management Framework Current Security Infrastructure Performance
Cybersecurity Risk Management Framework Current Security Infrastructure PerformanceMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Current Security Infrastructure Performance. Dispense information and present a thorough explanation of Performance, Asset Management, Protect Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework Impact On Security Infrastructure Performance
Cybersecurity Risk Management Framework Impact On Security Infrastructure PerformanceMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Impact On Security Infrastructure Performance. Dispense information and present a thorough explanation of Target To Be Met, Actual Target Met, Target Met After Introducing, Risk Assessment Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
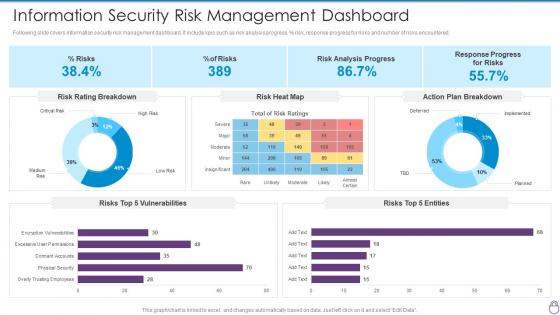 Cybersecurity Risk Management Framework Information Security Risk Management Dashboard
Cybersecurity Risk Management Framework Information Security Risk Management DashboardFollowing slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Information Security Risk Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks Top 5 Vulnerabilities, Risks Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management current potential implications faced by firm threats
Cyber security risk management current potential implications faced by firm threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Security Risk Management Current Potential Implications Faced By Firm Threats. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management cyber threats management dashboard
Cyber security risk management cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks, Threshold Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management financial performance tracking dashboard
Cyber security risk management financial performance tracking dashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Receivables Analysis, Revenue And Expense Trends, Central County Deal using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
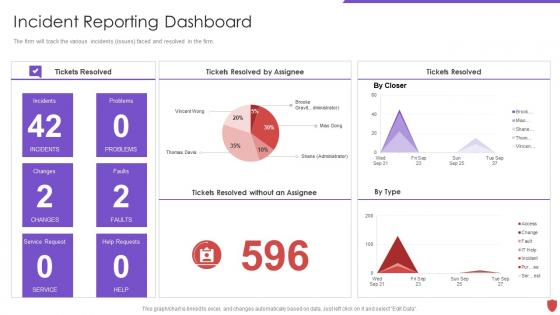 Cyber security risk management incident reporting dashboard
Cyber security risk management incident reporting dashboardThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Cyber Security Risk Management Incident Reporting Dashboard. Use it as a tool for discussion and navigation on Tickets Resolved, Tickets Resolved By Assignee, Tickets Resolved, Tickets Resolved Assignee. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iso 27001 dashboard for information security risk management ppt sample
Iso 27001 dashboard for information security risk management ppt sampleThis slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parsent risk, response progress for risks and number of risks encountered. Present the topic in a bit more detail with this ISO 27001 Dashboard For Information Security Risk Management Ppt Sample. Use it as a tool for discussion and navigation on Dashboard For Information Security Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Information Security Risk Management Information Security And Iso 27001
Dashboard For Information Security Risk Management Information Security And Iso 27001This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Present the topic in a bit more detail with this Dashboard For Information Security Risk Management Information Security And Iso 27001. Use it as a tool for discussion and navigation on Dashboard, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
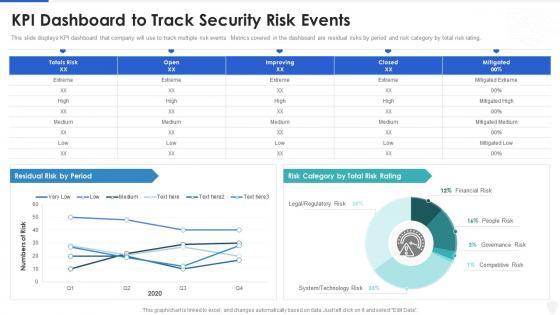 Cybersecurity and digital business risk management kpi dashboard to track security risk events
Cybersecurity and digital business risk management kpi dashboard to track security risk eventsPresent the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Kpi Dashboard To Track Security Risk Events. Use it as a tool for discussion and navigation on KPI Dashboard To Track Security Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iso 27001certification Process Dashboard For Information Security Risk Management
Iso 27001certification Process Dashboard For Information Security Risk ManagementThis slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Iso 27001certification Process Dashboard For Information Security Risk Management. Dispense information and present a thorough explanation of Dashboard, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security
Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information SecurityPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Information, Sources, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Data Security Risk Assessment And Management Plan For Information Security
Dashboard For Data Security Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Deliver an outstanding presentation on the topic using this Dashboard For Data Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Dashboard, Management, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





