Powerpoint Templates and Google slides for Security Requirements
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data security it requirement of data security in different sectors
Data security it requirement of data security in different sectorsThis slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Present the topic in a bit more detail with this Data Security IT Requirement Of Data Security In Different Sectors. Use it as a tool for discussion and navigation on Medical, Military, Govt, Corporate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
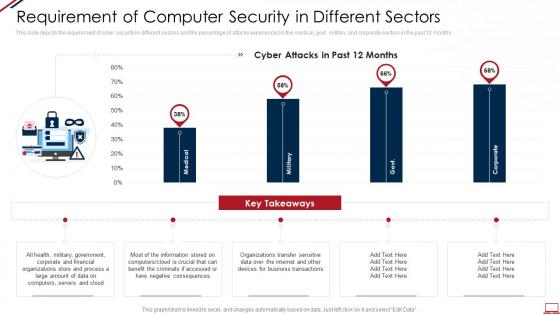 Computer system security requirement of computer security in different sectors
Computer system security requirement of computer security in different sectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Present the topic in a bit more detail with this Computer System Security Requirement Of Computer Security In Different Sectors. Use it as a tool for discussion and navigation on Organizations, Process, Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors
Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different SectorsThis slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Present the topic in a bit more detail with this Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors. Use it as a tool for discussion and navigation on Requirement Of Ethical Hackers, Military, Government Sector, Corporate Sectors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker
Ethical Hacking And Network Security Skills And Certifications Required For Ethical HackerThis slide describes the skills and certifications required for ethical hacker, such as computer networking skills, computer skills, Linux skills, and so on. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker. Dispense information and present a thorough explanation of Skills And Certifications, Ethical Hacker, Computer Networking Skills, Computer Skills, Linux Skills using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security requirements web applications ppt powerpoint presentation inspiration tips cpb
Security requirements web applications ppt powerpoint presentation inspiration tips cpbPresenting Security Requirements Web Applications Ppt Powerpoint Presentation Inspiration Tips Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Requirements Web Applications. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Bank Credit Card Requirements In Powerpoint And Google Slides Cpb
Security Bank Credit Card Requirements In Powerpoint And Google Slides CpbPresenting Security Bank Credit Card Requirements In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Bank Credit Card Requirements. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model
Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security ModelThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Threat Detection, Continuous Compliance, Data Encryption, Strong Authentication, using this template. Grab it now to reap its full benefits.
-
 Social Security Age Requirements Benefits In Powerpoint And Google Slides Cpb
Social Security Age Requirements Benefits In Powerpoint And Google Slides CpbPresenting Social Security Age Requirements Benefits In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Security Age Requirements Benefits This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secops V2 Skills Required For Security Operations Teams Ppt Infographics Tips
Secops V2 Skills Required For Security Operations Teams Ppt Infographics TipsThis slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Present the topic in a bit more detail with this Secops V2 Skills Required For Security Operations Teams Ppt Infographics Tips. Use it as a tool for discussion and navigation on Security Operations Teams, Peer Influence, Communicating Business Value, Organizational Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Security Protocols Required According To Type Of Network
Encryption Implementation Strategies Security Protocols Required According To Type Of NetworkThe purpose of this slide is to outline different security protocols used in various types of networks, and their specific applications. These network types are wired, wireless networks, Local Area Networks LANs, Wide Area Networks WANs, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Security Protocols Required According To Type Of Network. Use it as a tool for discussion and navigation on Local Area Networks, Wide Area Networks, Wired Networks, Wireless Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Network Security Management Requirements
It Network Security Management RequirementsThis slide showcases the information technology network security management requirements which helps an organization to address ever expanding matrix of users and locations. It include details such as network deployment, configuration, security, etc. Presenting our well structured It Network Security Management Requirements. The topics discussed in this slide are Network Deployment, Feature Configuration, Network Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Requirements For Appropriate Cloud Security Model Next Generation CASB
Requirements For Appropriate Cloud Security Model Next Generation CASBThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Increase audience engagement and knowledge by dispensing information using Requirements For Appropriate Cloud Security Model Next Generation CASB This template helps you present information on five stages. You can also present information on Continuous Compliance, Data Encryption, Strong Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Requirements For Appropriate Cloud Security Model CASB Cloud Security
Requirements For Appropriate Cloud Security Model CASB Cloud SecurityThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Requirements For Appropriate Cloud Security Model CASB Cloud Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Strong Authentication, Integrated Security, Data Encryption, Continuous Compliance, Visibility And Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Requirement For Effective Cyber Security Policy
Requirement For Effective Cyber Security PolicyThis slide covers the imperative reasons for the need of cybersecurity policies. The purpose of this template is to articulate the significance of policies in ensuring legal compliance, data protection, effective risk management, employee training, and incident response. Presenting our set of slides with Requirement For Effective Cyber Security Policy This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Legal Compliance, Data Protection, Risk Management
-
 Security And Privacy Requirements For Blockchain Comprehensive Approach To Privacy BCT SS
Security And Privacy Requirements For Blockchain Comprehensive Approach To Privacy BCT SSThis slide covers prerequisites to maintain privacy and security for seamless transactions such as integrity, preventing double spending, data confidentiality, anonymity of users identity, etc. Increase audience engagement and knowledge by dispensing information using Security And Privacy Requirements For Blockchain Comprehensive Approach To Privacy BCT SS. This template helps you present information on four stages. You can also present information on Prevention Of Double-Spending, Confidentiality Of Transactions, Anonymity Of Users Identity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Key Requirements Checklist For Chatbot Security
Key Requirements Checklist For Chatbot SecurityThis slide shows a detailed checklist that can be used to highlight various requirements for chatbot security. These requirements are categorized into three sections, which are environment, hosting, and security features. Further, these categories include securing code, communications, etc. Presenting our set of slides with Key Requirements Checklist For Chatbot Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Environment, Hosting, Security Features.
-
 Key Requirements For IOT Security Solution Selection
Key Requirements For IOT Security Solution SelectionThis slide showcases major requirements for choosing IoT solution along with description. It includes real-time visibility, device classification, augmented segmentation and scalability. Presenting our set of slides with name Key Requirements For IOT Security Solution Selection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Requirements, Device Classification, Scalability, Augmented Segmentation.
-
 Key Components Required For Building Security System
Key Components Required For Building Security SystemThis slide showcases the key elements required for developing effective security system which helps an organization to tackle issues in most efficient manner by providing quick response time. It include details such as surveillance,deterrence and response. Presenting our set of slides with Key Components Required For Building Security System. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Surveillance,Deterrence,Environmental Designs.
-
 Requirement of electronic information security in different sectors
Requirement of electronic information security in different sectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Requirement Of Electronic Information Security In Different Sectors. Dispense information and present a thorough explanation of Cyber Attacks, Past 12 Months, Devices Business Transactions, Organizations Transfer, Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Requirement Of Information Security In Different Sectors
Information Security Requirement Of Information Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Security Requirement Of Information Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Determining The Priority Requirements For Buying Iot Products
Information Security Program Determining The Priority Requirements For Buying Iot ProductsThis slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Present the topic in a bit more detail with this Information Security Program Determining The Priority Requirements For Buying Iot Products. Use it as a tool for discussion and navigation on Requirements, Products, Determining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Requirement Of Network Security In Different Sectors
Network Security Requirement Of Network Security In Different SectorsThis slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Network Security Requirement Of Network Security In Different Sectors. Dispense information and present a thorough explanation of Requirement Of Network Security In Different Sectors using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Requirement Of Information Technology Security In Different Sectors
Information Technology Security Requirement Of Information Technology Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Technology Security Requirement Of Information Technology Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security requirements website ppt powerpoint presentation summary introduction cpb
Security requirements website ppt powerpoint presentation summary introduction cpbPresenting Security Requirements Website Ppt Powerpoint Presentation Summary Introduction Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Requirements Website. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Lenders require collateral secured loan ppt powerpoint presentation professional cpb
Lenders require collateral secured loan ppt powerpoint presentation professional cpbPresenting Lender Credit Closing Costs Ppt Powerpoint Presentation Slides Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Lenders Require Collateral Secured Loan. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification
Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 CertificationFollowing slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Present the topic in a bit more detail with this Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification. Use it as a tool for discussion and navigation on Mandatory, Documents, Required. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Understanding The Requirement Of Interested Parties
Information Security And Iso 27001 Understanding The Requirement Of Interested Partiesdirectors and employee. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Understanding The Requirement Of Interested Parties. Dispense information and present a thorough explanation of Organization, Assessment, Procedure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Agreement Requirements Ppt Powerpoint Presentation Infographics Good Cpb
Security Agreement Requirements Ppt Powerpoint Presentation Infographics Good CpbPresenting Security Agreement Requirements Ppt Powerpoint Presentation Infographics Good Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Agreement Requirements. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Requirements Healthcare In Powerpoint And Google Slides Cpb
Cyber Security Requirements Healthcare In Powerpoint And Google Slides CpbPresenting Cyber Security Requirements Healthcare In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Requirements Healthcare. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud Environment
Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud EnvironmentThis slide covers the following requirements which explains the importance or need of Centralized policy management in multi cloud environment. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud Environment. This template helps you present information on four stages. You can also present information on Requirement, Policy Management, Multi Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Skillset Management Multi Cloud Skill Requirements
Cloud Architecture And Security Review Skillset Management Multi Cloud Skill RequirementsThis slide covers several roles found within multi cloud teams cloud architects and engineers, DevOps, site reliability engineers SREs. Thus these skills are required for multi cloud teams. Introducing Cloud Architecture And Security Review Skillset Management Multi Cloud Skill Requirements to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Knowledge, Experience, Execution, Vision, using this template. Grab it now to reap its full benefits.
-
 Why Enterprise Security Operation Center Is Required
Why Enterprise Security Operation Center Is RequiredThis slide covers need of enterprise security operation center. It involves reasons such as continuous monitoring, centralized visibility, reduced cybersecurity costs and ensures better collaboration. Introducing our premium set of slides with Why Enterprise Security Operation Center Is Required. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Continuous Monitoring, Centralized Visibility, Reduced Cybersecurity Costs. So download instantly and tailor it with your information.
-
 Threat Mitigation Strategies Required Network Security In Powerpoint And Google Slides Cpb
Threat Mitigation Strategies Required Network Security In Powerpoint And Google Slides CpbPresenting our Threat Mitigation Strategies Required Network Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Threat Mitigation Strategies Required Network Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Transit Security Requirements In Powerpoint And Google Slides Cpb
Transit Security Requirements In Powerpoint And Google Slides CpbPresenting Transit Security Requirements In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Transit Security Requirements. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Jobs Require Social Security Number In Powerpoint And Google Slides Cpb
Jobs Require Social Security Number In Powerpoint And Google Slides CpbPresenting Jobs Require Social Security Number In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Jobs Require Social Security Number. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 SecOps Skills Required For Security Operations Ppt Powerpoint Presentation Portfolio Slides
SecOps Skills Required For Security Operations Ppt Powerpoint Presentation Portfolio SlidesThis slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no code automation, communicating modern threats from first principles, peer influence, and so on. Deliver an outstanding presentation on the topic using this SecOps Skills Required For Security Operations Ppt Powerpoint Presentation Portfolio Slides. Dispense information and present a thorough explanation of Communicating Business, Value Through Writing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Requirements For Appropriate Cloud Security Model Ppt Infographic
Requirements For Appropriate Cloud Security Model Ppt InfographicThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Increase audience engagement and knowledge by dispensing information using Requirements For Appropriate Cloud Security Model Ppt Infographic. This template helps you present information on five stages. You can also present information on Visibility And Threat Detection, Continuous Compliance, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Requirement In Credit Card Processing
Security Requirement In Credit Card ProcessingThis slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Introducing our Security Requirement In Credit Card Processing set of slides. The topics discussed in these slides are Payment Card Industry, Security Standard Requirements. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Requirement analysis sales analysis code security difference verification
Requirement analysis sales analysis code security difference verificationPresenting this set of slides with name - Requirement Analysis Sales Analysis Code Security Difference Verification. This is an editable nine stages graphic that deals with topics like Requirement Analysis, Sales Analysis, Code Security Difference Verification to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Requirements definition land policies food security consultation participation
Requirements definition land policies food security consultation participationPresenting this set of slides with name - Requirements Definition Land Policies Food Security Consultation Participation. This is an editable seven stages graphic that deals with topics like Requirements Definition, Land Policies, Food Security, Consultation Participation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security requirement abuse cases risk analysis code review
Security requirement abuse cases risk analysis code reviewPresenting this set of slides with name - Security Requirement Abuse Cases Risk Analysis Code Review. This is an editable ten stages graphic that deals with topics like Security Requirement, Abuse Cases, Risk Analysis, Code Review to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Acquisition retention strategy customer segmentation requirements security analyst cpb
Acquisition retention strategy customer segmentation requirements security analyst cpbPresenting this set of slides with name - Acquisition Retention Strategy Customer Segmentation Requirements Security Analyst Cpb. This is an editable nine stages graphic that deals with topics like Acquisition Retention Strategy, Customer Segmentation Requirements, Security Analyst to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Management auditing structure project security requirements business tactics cpb
Management auditing structure project security requirements business tactics cpbPresenting this set of slides with name - Management Auditing Structure Project Security Requirements Business Tactics Cpb. This is an editable three stages graphic that deals with topics like Management Auditing, Structure Project, Security Requirements, Business Tactics to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security strategy requirements ppt powerpoint presentation sample cpb
Cyber security strategy requirements ppt powerpoint presentation sample cpbPresenting this set of slides with name Cyber Security Strategy Requirements Ppt Powerpoint Presentation Sample Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cyber Security Strategy Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security requirements ppt powerpoint presentation slides elements cpb
Security requirements ppt powerpoint presentation slides elements cpbPresenting this set of slides with name Security Requirements Ppt Powerpoint Presentation Slides Elements Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security requirements ppt powerpoint presentation layouts inspiration cpb
Security requirements ppt powerpoint presentation layouts inspiration cpbPresenting this set of slides with name Security Requirements Ppt Powerpoint Presentation Layouts Inspiration Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Non functional requirements security ppt powerpoint presentation model layout ideas cpb
Non functional requirements security ppt powerpoint presentation model layout ideas cpbPresenting this set of slides with name Non Functional Requirements Security Ppt Powerpoint Presentation Model Layout Ideas Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Non Functional Requirements Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Gdpr data security requirements ppt powerpoint presentation inspiration guidelines cpb
Gdpr data security requirements ppt powerpoint presentation inspiration guidelines cpbPresenting this set of slides with name GDPR Data Security Requirements Ppt Powerpoint Presentation Inspiration Guidelines Cpb. This is an editable Powerpoint four stages graphic that deals with topics like GDPR Data Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security requirements ppt powerpoint presentation gallery infographics cpb
Security requirements ppt powerpoint presentation gallery infographics cpbPresenting this set of slides with name Security Requirements Ppt Powerpoint Presentation Gallery Infographics Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security job requirements ppt powerpoint presentation ideas visuals cpb
Cyber security job requirements ppt powerpoint presentation ideas visuals cpbPresenting this set of slides with name Cyber Security Job Requirements Ppt Powerpoint Presentation Ideas Visuals Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Job Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cloud security requirements ppt powerpoint presentation infographics gridlines cpb
Cloud security requirements ppt powerpoint presentation infographics gridlines cpbPresenting this set of slides with name Cloud Security Requirements Ppt Powerpoint Presentation Infographics Gridlines Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cloud Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security systems compliance requirements ppt presentation summary themes cpb
Information security systems compliance requirements ppt presentation summary themes cpbPresenting this set of slides with name Information Security Systems Compliance Requirements Ppt Presentation Summary Themes Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Information Security Systems Compliance Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Product security requirements ppt powerpoint presentation professional grid cpb
Product security requirements ppt powerpoint presentation professional grid cpbPresenting this set of slides with name Product Security Requirements Ppt Powerpoint Presentation Professional Grid Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Product Security Requirements to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Impact analysis effective security management security requirement ppt presentation slides
Impact analysis effective security management security requirement ppt presentation slidesThis slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events. Presenting this set of slides with name Impact Analysis Effective Security Management Security Requirement Ppt Presentation Slides. The topics discussed in these slides are Impact Analysis, Effective Security, Management Security, Requirement. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Asset management security requirements ppt powerpoint presentation layouts format ideas cpb
Asset management security requirements ppt powerpoint presentation layouts format ideas cpbPresenting our Asset Management Security Requirements Ppt Powerpoint Presentation Layouts Format Ideas Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Asset Management Security Requirements This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Requirement security ppt powerpoint presentation styles aids cpb
Requirement security ppt powerpoint presentation styles aids cpbPresenting our Requirement Security Ppt Powerpoint Presentation Styles Aids Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Requirement Security This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Requirement for security planning and risk management procedure
Requirement for security planning and risk management procedurePresenting our well structured Requirement For Security Planning And Risk Management Procedure. The topics discussed in this slide are Requirement Security, Planning Risk, Management Procedure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Circle process slide of hybrid cloud security system requirements infographic template
Circle process slide of hybrid cloud security system requirements infographic templateThis is our Circle Process Slide Of Hybrid Cloud Security System Requirements Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully editable visual content.
-
 Data breach security requirements and goals
Data breach security requirements and goalsThis slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like securing cardholder data, manage vulnerability program and so on. Introducing our Data Breach Security Requirements And Goals set of slides. The topics discussed in these slides are Goals, Measures, Management, Secure Network, Product. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.




