Powerpoint Templates and Google slides for Security Programs
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Key security controls to be addressed in the program managing cyber risk in a digital age
Key security controls to be addressed in the program managing cyber risk in a digital agePurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Key Security Controls To Be Addressed In The Program Managing Cyber Risk In A Digital Age. This template helps you present information on three stages. You can also present information on Framework, Elaborates, Security, Controls, Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing cyber risk in a digital age information security program values to business
Managing cyber risk in a digital age information security program values to businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Introducing Managing Cyber Risk In A Digital Age Information Security Program Values To Business to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Framework For Building Security Transformation Program
Framework For Building Security Transformation ProgramThis slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc. Presenting our set of slides with name Framework For Building Security Transformation Program. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Architecture, Training And Awareness, Cyber Threat Management.
-
 Framework Of Information Security Action Program
Framework Of Information Security Action ProgramThis slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc. Introducing our Framework Of Information Security Action Program set of slides. The topics discussed in these slides are Stakeholder Engagement, Identity Management, Operational Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon Of Computer Security Program For Protection
Icon Of Computer Security Program For ProtectionIntroducing our premium set of slides with Icon Of Computer Security Program For Protection. Elucidate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Computer Security Program For Protection. So download instantly and tailor it with your information.
-
 IT Security Program To Measure Likelihood Of Impact
IT Security Program To Measure Likelihood Of ImpactThis slide represents the information security program to measure likelihood of impact which includes effects, system operationality that will help company to categorize risk level and develop risk mitigation strategies. Presenting our well-structured IT Security Program To Measure Likelihood Of Impact. The topics discussed in this slide are System Operationality, Availability, Integrity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Program Icon For Protecting Client Data
Security Program Icon For Protecting Client DataPresenting our set of slides with name Security Program Icon For Protecting Client Data. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Program Icon For Protecting Client Data.
-
 Six Practices For Security Management Program
Six Practices For Security Management ProgramThis slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency. Introducing our premium set of slides with Six Practices For Security Management Program. Elucidate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Analysis And Prioritization, Strategic Initiatives Roadmap, Business Analyst. So download instantly and tailor it with your information.
-
 Stages Involved In Data Security Management Program
Stages Involved In Data Security Management ProgramThis slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically. Introducing our Stages Involved In Data Security Management Program set of slides. The topics discussed in these slides are Develop Data Security, Communicate, Communication Method. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Develop Strategic Security Program
Steps To Develop Strategic Security ProgramThis slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc. Introducing our premium set of slides with Steps To Develop Strategic Security Program. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organizational Culture, Measuring Goals, Program Assessment. So download instantly and tailor it with your information.
-
 Strategic Model For Information Security Program
Strategic Model For Information Security ProgramThis slide focuses on strategic model for information security program which includes governance and management such as security risk analysis, audit and assessment, supplier management, backup and recovery, etc. Presenting our well-structured Strategic Model For Information Security Program. The topics discussed in this slide are Evaluation And Direction, Leadership, Human Resource Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Three Pillars Of Information Security Program With Availability
Three Pillars Of Information Security Program With AvailabilityThis slide shows the three pillars of information security program which includes confidentiality, availability and integrity that will allow business to prevent from losses, regulatory fines and loss of reputation. Presenting our set of slides with name Three Pillars Of Information Security Program With Availability. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Confidentiality, Availability, Integrity.
-
 Risk Based Methodology To Cyber Information Security Program Framework Key Components
Risk Based Methodology To Cyber Information Security Program Framework Key ComponentsMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Risk Based Methodology To Cyber Information Security Program Framework Key Components to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy, using this template. Grab it now to reap its full benefits.
-
 Security Awareness Program Maturity Model
Security Awareness Program Maturity ModelThe following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Introducing our premium set of slides with Security Awareness Program Maturity Model. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Awareness, Sustainment, Metrics Framework. So download instantly and tailor it with your information.
-
 Cybersecurity Criticality Assessment Of Identified Assets Information Security Program
Cybersecurity Criticality Assessment Of Identified Assets Information Security ProgramFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Present the topic in a bit more detail with this Cybersecurity Criticality Assessment Of Identified Assets Information Security Program. Use it as a tool for discussion and navigation on Criticality Assessment Of Identified Assets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Program Effective Cybersecurity Risk Management Table Of Contents
Security Program Effective Cybersecurity Risk Management Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Program Effective Cybersecurity Risk Management Table Of Contents. This template helps you present information on seven stages. You can also present information on Risk Governance, Enterprise Risk Ecosystem, Program Effectiveness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Information Security Program For Effective Cybersecurity Risk Management
Icons Slide Information Security Program For Effective Cybersecurity Risk ManagementIntroducing our well researched set of slides titled Icons Slide Information Security Program For Effective Cybersecurity Risk Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Agenda Security Program For Effective Cybersecurity Risk Management
Agenda Security Program For Effective Cybersecurity Risk ManagementIntroducing Agenda Security Program For Effective Cybersecurity Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digitalization, Cybersecurity, Business, using this template. Grab it now to reap its full benefits.
-
 Information Program Cybersecurity Summary Existing Security Management Capabilities
Information Program Cybersecurity Summary Existing Security Management CapabilitiesFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Present the topic in a bit more detail with this Information Program Cybersecurity Summary Existing Security Management Capabilities. Use it as a tool for discussion and navigation on Management, Capabilities, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Addressing The Companies Digitization Levels By Sectors
Information Security Program Addressing The Companies Digitization Levels By SectorsMentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an outstanding presentation on the topic using this Information Security Program Addressing The Companies Digitization Levels By Sectors. Dispense information and present a thorough explanation of Companies, Digitization, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Categorization Worksheet For Assets Owned Organization
Information Security Program Categorization Worksheet For Assets Owned OrganizationThis slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Information Security Program Categorization Worksheet For Assets Owned Organization. Use it as a tool for discussion and navigation on Categorization, Worksheet, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Action Plan In Case Of Breaches
Information Security Program Cybersecurity Action Plan In Case Of BreachesMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Action Plan In Case Of Breaches. Dispense information and present a thorough explanation of Action Plan In Case Of Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Communication Plan For Cyber Breaches
Information Security Program Cybersecurity Communication Plan For Cyber BreachesMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Communication Plan For Cyber Breaches. Dispense information and present a thorough explanation of Communication Plan For Cyber Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Defining Risk Events Based On Impact Size
Information Security Program Cybersecurity Defining Risk Events Based On Impact SizeThis slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Defining Risk Events Based On Impact Size. Dispense information and present a thorough explanation of Occurrence, Likelihood, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Employee Upskilling Training Program
Information Security Program Cybersecurity Employee Upskilling Training ProgramMentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Present the topic in a bit more detail with this Information Security Program Cybersecurity Employee Upskilling Training Program. Use it as a tool for discussion and navigation on Introduction, Obligations, Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Flow Diagram Of Incident Response Process
Information Security Program Cybersecurity Flow Diagram Of Incident Response ProcessMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Flow Diagram Of Incident Response Process. Dispense information and present a thorough explanation of Flow Diagram Of Incident Response Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Information Security Program Values To Business
Information Security Program Cybersecurity Information Security Program Values To BusinessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Information Security Program Values To Business. Dispense information and present a thorough explanation of Information, Business, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Introducing New Incidents Logging Process
Information Security Program Cybersecurity Introducing New Incidents Logging ProcessThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Present the topic in a bit more detail with this Information Security Program Cybersecurity Introducing New Incidents Logging Process. Use it as a tool for discussion and navigation on Introducing New Incidents Logging Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Risk Governance Structure
Information Security Program Cybersecurity Management Risk Governance StructureMentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Present the topic in a bit more detail with this Information Security Program Cybersecurity Management Risk Governance Structure. Use it as a tool for discussion and navigation on Risk Governance Structure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Security Lifecycle
Information Security Program Cybersecurity Management Security LifecycleIncrease audience engagement and knowledge by dispensing information using Information Security Program Cybersecurity Management Security Lifecycle. This template helps you present information on six stages. You can also present information on Categorize, Implement, Authorize using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Overview Of New It Policy Framework
Information Security Program Cybersecurity Overview Of New It Policy FrameworkThis slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Present the topic in a bit more detail with this Information Security Program Cybersecurity Overview Of New It Policy Framework. Use it as a tool for discussion and navigation on Information, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control
Information Security Program Cybersecurity Setting Scenario For Cybersecurity ControlFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control. Dispense information and present a thorough explanation of Technical Controls, Management Controls, Operational Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Defining Business Priorities To Ensure Information Security
Information Security Program Defining Business Priorities To Ensure Information SecurityThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Increase audience engagement and knowledge by dispensing information using Information Security Program Defining Business Priorities To Ensure Information Security. This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Embedding Risk Based Approach Product Development Process
Information Security Program Embedding Risk Based Approach Product Development ProcessPurpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Present the topic in a bit more detail with this Information Security Program Embedding Risk Based Approach Product Development Process. Use it as a tool for discussion and navigation on Product, Development, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Encountered Risks Summary And Their Impact Assessment
Information Security Program Encountered Risks Summary And Their Impact AssessmentMentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver an outstanding presentation on the topic using this Information Security Program Encountered Risks Summary And Their Impact Assessment. Dispense information and present a thorough explanation of Assessment, Encountered, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
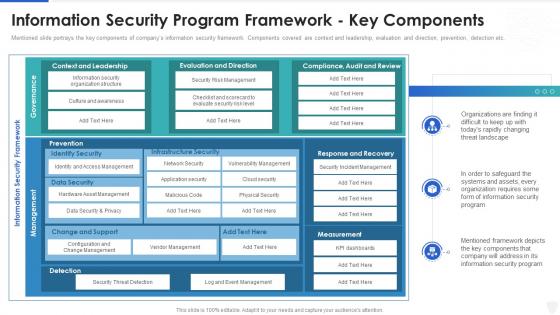
 Information Security Program Framework Key Components information Security Program
Information Security Program Framework Key Components information Security ProgramMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Key Components information Security Program. Dispense information and present a thorough explanation of Information, Framework, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Gap Identification Current Approach Process Flaws And Cost
Information Security Program Gap Identification Current Approach Process Flaws And CostPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Present the topic in a bit more detail with this Information Security Program Gap Identification Current Approach Process Flaws And Cost. Use it as a tool for discussion and navigation on Identification, Current Approach, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Key Security Controls To Be Addressed In The Program
Information Security Program Key Security Controls To Be Addressed In The ProgramPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an outstanding presentation on the topic using this Information Security Program Key Security Controls To Be Addressed In The Program. Dispense information and present a thorough explanation of Prevents Attacks, Limits Extent Of Attacks, Data Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Responsibility Matrix To Ensure Effective Risk Management
Information Security Program Responsibility Matrix To Ensure Effective Risk ManagementThis slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Present the topic in a bit more detail with this Information Security Program Responsibility Matrix To Ensure Effective Risk Management. Use it as a tool for discussion and navigation on Responsibility, Management, Accountable. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness
Information Security Program Scorecard To Check Cybersecurity And Digital Risk PreparednessFollowing slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Present the topic in a bit more detail with this Information Security Program Scorecard To Check Cybersecurity And Digital Risk Preparedness. Use it as a tool for discussion and navigation on Preparedness, Cybersecurity, Scorecard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Information Security Program For Effective Cybersecurity Risk Management
Table Of Contents Information Security Program For Effective Cybersecurity Risk ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Contents Information Security Program For Effective Cybersecurity Risk Management. This template helps you present information on eight stages. You can also present information on Requirements, Technologies, Gap Identification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Framework Key Components Risk Based Methodology To Cyber
Information Security Program Framework Key Components Risk Based Methodology To CyberMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Information Security Program Framework Key Components Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with one stage this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy using this template. Grab it now to reap its full benefits.
-
 Information Security Program Values To Business Risk Based Methodology To Cyber
Information Security Program Values To Business Risk Based Methodology To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management.Increase audience engagement and knowledge by dispensing information using Information Security Program Values To Business Risk Based Methodology To Cyber This template helps you present information on two stages. You can also present information on Undetectable By Current, Vulnerabilities In The Current, Threats To The Companys Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber
Key Security Controls To Be Addressed In The Program Risk Based Methodology To CyberPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications.Present the topic in a bit more detail with this Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Prevents Attacks, Limits Extent Of Attacks, Data Recovery This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security
Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables.Present the topic in a bit more detail with this Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Assess Security Requirements, Perform A Gap Analysis, Develop Gap Initiatives This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Values To Business Introducing A Risk Based Approach To Cyber
Information Security Program Values To Business Introducing A Risk Based Approach To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection AND response and attack surface management.Deliver an outstanding presentation on the topic using this Information Security Program Values To Business Introducing A Risk Based Approach To Cyber Dispense information and present a thorough explanation of Detection And Response, Attack Surface Management, Program Will Reduce using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Security Controls To Be Addressed In The Program Introducing A Risk Based Approach
Key Security Controls To Be Addressed In The Program Introducing A Risk Based ApproachPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications.Deliver an outstanding presentation on the topic using this Key Security Controls To Be Addressed In The Program Introducing A Risk Based Approach Dispense information and present a thorough explanation of Restrict Admin Privileges, Factor Authentication, Limits Extent Of Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hacking it use of security programs ppt slides design templates
Hacking it use of security programs ppt slides design templatesThis slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Increase audience engagement and knowledge by dispensing information using Hacking It Use Of Security Programs Ppt Slides Design Templates. This template helps you present information on three stages. You can also present information on Secure Sockets Layer, Web Application Firewall, Website And Software Scanners using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity and digital business risk management security program framework
Cybersecurity and digital business risk management security program frameworkMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Security Program Framework. Dispense information and present a thorough explanation of Framework, Information, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity digital business management information security program values business
Cybersecurity digital business management information security program values businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Deliver an outstanding presentation on the topic using this Cybersecurity Digital Business Management Information Security Program Values Business. Dispense information and present a thorough explanation of Environment, Management, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management workplace employee assistance program
Cyber security risk management workplace employee assistance programThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Workplace Employee Assistance Program. This template helps you present information on three stages. You can also present information on Clinical Services, Work And Life Services, Employer Services, Online Resources, Offline Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Iso 27001 Internal Isms Audit Program And Activities
Information Security And Iso 27001 Internal Isms Audit Program And ActivitiesMentioned slide portrays framework of internal ISMS audit program along with various activities. Activities covered in the slide are commissioning, initial meeting, information collection and evaluation, results and final meeting. Present the topic in a bit more detail with this Information Security And Iso 27001 Internal Isms Audit Program And Activities. Use it as a tool for discussion and navigation on Implementation, Monitoring, Improvement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Isms Training Program For Employees
Information Security And Iso 27001 Isms Training Program For EmployeesThis slide illustrates employee training program covering information about training title, short description, who should attend the training and duration. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Isms Training Program For Employees. Dispense information and present a thorough explanation of Introduction, Foundation, Implementer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Education Training Programs Your Area Ppt Powerpoint Presentation Model Backgrounds Cpb
Security Education Training Programs Your Area Ppt Powerpoint Presentation Model Backgrounds CpbPresenting Security Education Training Programs Your Area Ppt Powerpoint Presentation Model Backgrounds Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Education Training Programs Your Area. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Building organizational security strategy addressing workforce assistance program
Building organizational security strategy addressing workforce assistance programThe workforce assistance program will help firms in enhancing their well being at workplace and enable them to handle critical or emergence situations. This program will render services like clinical services, work and life services and employer services, etc. Increase audience engagement and knowledge by dispensing information using Building Organizational Security Strategy Addressing Workforce Assistance Program. This template helps you present information on five stages. You can also present information on Services, Resources, Assistance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enhancing overall project security it workplace employee assistance program
Enhancing overall project security it workplace employee assistance programThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Enhancing Overall Project Security It Workplace Employee Assistance Program to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Organizational, Management, Consultations, using this template. Grab it now to reap its full benefits.
-
 Incident Response Playbook Cyber Security Awareness Training Program
Incident Response Playbook Cyber Security Awareness Training ProgramPurpose of this slide is to provide information about the cyber security awareness training program to be conducted for in house team. It also provides the details about training types, content types and audience. Deliver an outstanding presentation on the topic using this Incident Response Playbook Cyber Security Awareness Training Program. Dispense information and present a thorough explanation of Training Types, Training Content Types, Team Members using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





