Powerpoint Templates and Google slides for Security Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 WIFI Security Network Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Network Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of WIFI security. It features a shield with a lock to represent the protection of your WIFI network. It is a great visual aid for presentations on WIFI security and can be used to highlight the importance of keeping your network secure.
-
 WIFI Security Network Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Network Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for illustrating the concept of WIFI Security. It features a simple, modern design that is sure to make your presentation stand out. It is perfect for any project related to WIFI Security, from educational materials to corporate presentations.
-
 Payment Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Payment Security Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a visual representation of payment security. It features a padlock symbolizing safety and security, with a green background to indicate trustworthiness and reliability. Perfect for presentations on secure payment systems and processes.
-
 Payment Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Payment Security Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon on Payment Security is perfect for presentations on online banking, credit card fraud prevention, and other financial security topics. It is simple yet effective, making it easy to convey your message to your audience. It is a great visual aid to help explain the importance of payment security.
-
 Supply Chain Security Risk Management Process
Supply Chain Security Risk Management ProcessThis slide showcases process that can help organization to manage supply chain security risks. Its key steps are document risks, develop framework, monitor risk and regular review. Introducing our premium set of slides with Supply Chain Security Risk Management Process Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Document Risks, Develop Framework. So download instantly and tailor it with your information.
-
 Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS
Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SSThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS Use it as a tool for discussion and navigation on Network Security, Node Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IaaS Security Protocol Customer Checklist
IaaS Security Protocol Customer ChecklistThis side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Presenting our well structured IaaS Security Protocol Customer Checklist. The topics discussed in this slide are Tasks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Policy Byod Procedure Device Protocols For Workers
Cyber Security Policy Byod Procedure Device Protocols For WorkersThis slide represents the device protocols that are the first step in the BYOD procedure. It also includes the software information that should be installed on the employees personal devices. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Byod Procedure Device Protocols For Workers. This template helps you present information on four stages. You can also present information on Software, Business, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
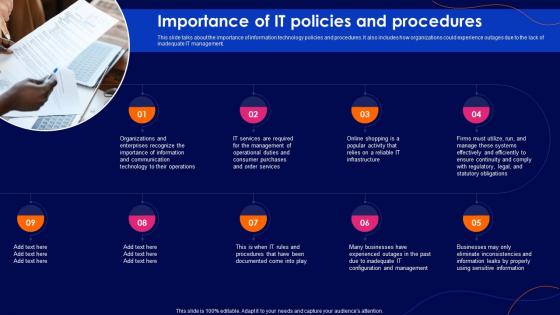 Cyber Security Policy Importance Of It Policies And Procedures
Cyber Security Policy Importance Of It Policies And ProceduresThis slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Importance Of It Policies And Procedures. This template helps you present information on nine stages. You can also present information on Services, Operational, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
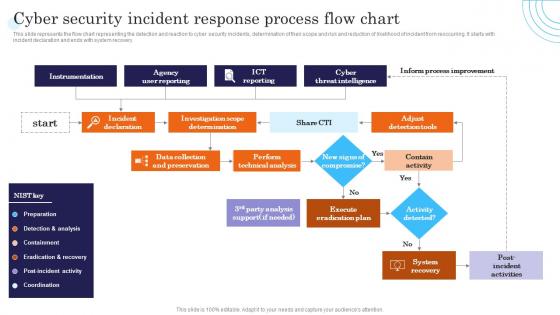 Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment
Cyber Security Incident Response Process Flow Chart Incident Response Strategies DeploymentThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Instrumentation, Agency, Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy What Happens In The Absence Of It Policies And Procedures
Cyber Security Policy What Happens In The Absence Of It Policies And ProceduresThis slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Introducing Cyber Security Policy What Happens In The Absence Of It Policies And Procedures to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Procedures, Information, Corporations, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan
Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response PlanThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Present the topic in a bit more detail with this Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Agency User Reporting, Instrumentation, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Audit And Testing Process
Cloud Security Audit And Testing ProcessThe slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation. Presenting our set of slides with Cloud Security Audit And Testing Processs. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Planning, Analyse, Recommendations, Remediation .
-
 Cloud Security Audit Assessment Process
Cloud Security Audit Assessment ProcessThe slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Introducing our premium set of slides with Cloud Security Audit Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Calculate Score, Validate Controls, Understand The Model . So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Internet Security Protocols In Powerpoint And Google Slides Cpb
Internet Security Protocols In Powerpoint And Google Slides CpbPresenting Internet Security Protocols In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internet Security Protocols. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Essential Initiatives To Safeguard Streamlining Employee Verification Process To Ensure People Security
Essential Initiatives To Safeguard Streamlining Employee Verification Process To Ensure People SecurityThis slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. Present the topic in a bit more detail with this Essential Initiatives To Safeguard Streamlining Employee Verification Process To Ensure People Security. Use it as a tool for discussion and navigation on Academic Verification, Database Screening, Vendor Due Diligence This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Five Step Process To Create Cyber Security Raising Cyber Security Awareness In Organizations
Five Step Process To Create Cyber Security Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees and retesting. Increase audience engagement and knowledge by dispensing information using Five Step Process To Create Cyber Security Raising Cyber Security Awareness In Organizations. This template helps you present information on six stages. You can also present information on Assess, Build, Choose, Deploy, Educate, Retest using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Four Stage Cyclic Process Of Building Cyber Security
Four Stage Cyclic Process Of Building Cyber SecurityThis slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Introducing our premium set of slides with Four Stage Cyclic Process Of Building Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Safe State, Strengthen Protection, Remediation. So download instantly and tailor it with your information.
-
 Blockchain Technology For Efficient Security Initiatives Protecting Recruitment Process
Blockchain Technology For Efficient Security Initiatives Protecting Recruitment ProcessThis slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Increase audience engagement and knowledge by dispensing information using Blockchain Technology For Efficient Security Initiatives Protecting Recruitment Process. This template helps you present information on four stages. You can also present information on Candidate Information, Decentralized Job Listing, Candidate Qualifications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Process Of Network Infra Security
Implementation Process Of Network Infra SecurityThe following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Introducing Implementation Process Of Network Infra Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Segmentation, Hardware, Software, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Implementation Process Of Software Defined Networking SDN
SDN Security IT Implementation Process Of Software Defined Networking SDNThis slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. Increase audience engagement and knowledge by dispensing information using SDN Security IT Implementation Process Of Software Defined Networking SDN. This template helps you present information on four stages. You can also present information on Process, Implementation, Software using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Photo Editing Company Profile Canva Security Processes And Systems CP SS V
Photo Editing Company Profile Canva Security Processes And Systems CP SS VThis slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Introducing Photo Editing Company Profile Canva Security Processes And Systems CP SS V to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Encryption, Processes, Systems, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb
Cyber Security Risk Management Process In Powerpoint And Google Slides CpbPresenting our Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Risk Management Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Methods To Secure Cloud Migration Process Roadmap
Methods To Secure Cloud Migration Process RoadmapThe following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Introducing our premium set of slides with Methods To Secure Cloud Migration Process Roadmap. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phased Migration, Encrypt Data, Centralize Monitoring. So download instantly and tailor it with your information.
-
 SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration
SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint DemonstrationThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration. This template helps you present information on one stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SecOps Security Operations Threat Management Process Ppt Professional
SecOps Security Operations Threat Management Process Ppt ProfessionalThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Present the topic in a bit more detail with this SecOps Security Operations Threat Management Process Ppt Professional. Use it as a tool for discussion and navigation on External Threat Intelligance, Behavioral Analytics . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Funds Transferring Process Mobile Banking For Convenient And Secure Online Payments Fin SS
Funds Transferring Process Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide contains detailed information about funds transferring process steps using mobile banking. It includes steps such as login into app, select transfer money, enter amount, verify details, enter PIN etc. Present the topic in a bit more detail with this Funds Transferring Process Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Transferring, Process, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process To Complete Banking Mobile Banking For Convenient And Secure Online Payments Fin SS
Process To Complete Banking Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows details regarding how transactions are conducted through mobile payments. This process includes various key components such customer, mobile application, payment gateway, merchant and issuing bank. Deliver an outstanding presentation on the topic using this Process To Complete Banking Mobile Banking For Convenient And Secure Online Payments Fin SS. Dispense information and present a thorough explanation of Process, Verification, Mechanism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For Remote Deposit Capture Process Mobile Banking For Convenient And Secure Online Payments Fin SS
Steps For Remote Deposit Capture Process Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide contains the detailed information about card management process steps using mobile banking as medium. It includes steps such as login into app, search cards option, select card which you want to manage, etc. Present the topic in a bit more detail with this Steps For Remote Deposit Capture Process Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Process, Management, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SS
Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain Security Protocol List Icon
Blockchain Security Protocol List IconIntroducing our premium set of slides with Blockchain Security Protocol List Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Blockchain Security, Protocol List, Icon. So download instantly and tailor it with your information.
-
 Process To Formulate Cyber Security Communication Plan
Process To Formulate Cyber Security Communication PlanThis slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Introducing our premium set of slides with Process To Formulate Cyber Security Communication Plan Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Formulate Committee, Draft Statement, Rehearse, Plan, Regulatory Compliance So download instantly and tailor it with your information.
-
 Cloud Access Security Broker Working Process Ppt Ideas Grid
Cloud Access Security Broker Working Process Ppt Ideas GridThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Ppt Ideas Grid. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Security Protocols Standards Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Protocols Standards Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon depicts a safety standard symbol with a checkmark in the center, surrounded by a green circle. It is a visual representation of safety compliance and a reminder to stay vigilant in following safety protocols. Perfect for presentations, reports, and other documents.
-
 Security Protocols Standards Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Protocols Standards Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is a perfect visual representation of safety standards. It features a silhouette of a person wearing a hard hat and safety vest, conveying the importance of safety in the workplace. It can be used to highlight key safety topics in presentations.
-
 Credit Card Payment Processing Security
Credit Card Payment Processing SecurityThis slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting our set of slides with Credit Card Payment Processing Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Data Storage, Payment Data Encryption.
-
 Credit Card Security Processing Icon
Credit Card Security Processing IconIntroducing our Credit Card Security Processing Icon set of slides. The topics discussed in these slides are Credit Card Security Processing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Requirement In Credit Card Processing
Security Requirement In Credit Card ProcessingThis slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Introducing our Security Requirement In Credit Card Processing set of slides. The topics discussed in these slides are Payment Card Industry, Security Standard Requirements. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Process In Powerpoint And Google Slides Cpb
Security Process In Powerpoint And Google Slides CpbPresenting our Security Process In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Process. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Communication Plan Of Security Crisis Management Process
Communication Plan Of Security Crisis Management ProcessThis slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Presenting our well structured Communication Plan Of Security Crisis Management Process. The topics discussed in this slide are Strengthening Continued, Implement Stronger Defences, Improve Incidents. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Action Plan Process
Cyber Security Action Plan ProcessThis slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc Introducing our premium set of slides with Cyber Security Action Plan Process. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Action, Security, Process. So download instantly and tailor it with your information.
-
 Information Security Program Action Plan Process
Information Security Program Action Plan ProcessThis slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc Introducing our Information Security Program Action Plan Process set of slides. The topics discussed in these slides are Security, Program, Process. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Workplace Emergency Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Workplace Emergency Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon is a bright and vibrant illustration of a workplace emergency action plan. It is perfect for presentations on communication and safety in the workplace. It is a great visual aid for highlighting the importance of emergency preparedness.
-
 Workplace Emergency Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Workplace Emergency Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is perfect for illustrating a workplace emergency action plan. Its a simple, yet effective way to communicate the importance of emergency preparedness in the workplace.
-
 Seven staged circular process network security planning ppt slides
Seven staged circular process network security planning ppt slidesVisually stunning PowerPoint Presentation slides. Clearly describes the various security strategies which could be beneficial to cope up with the risks. Offers Wide screen view for more clarity and better vision. Compatible with Google Framework. Being spacious enough to Include Description of Security groups and other vital information. Easily amendable PPT patterns.The stages in this process are security.
-
 Security of iot operations powerpoint slide rules
Security of iot operations powerpoint slide rulesPresenting security of iot operations powerpoint slide rules. This is a security of iot operations powerpoint slide rules. This is a one stage process. The stages in this process are security program, security configuration management, vulnerability scanning, application scanning, threat management, cloud assessment, authentication and privacy.
-
 Billing customer security e source control circular process with icon in centre
Billing customer security e source control circular process with icon in centrePresenting billing customer security e source control circular process with icon in centre. This is a billing customer security e source control circular process with icon in centre. This is a seven stage process. The stages in this process are billing process, billing procedure, billing cycle.
-
 Cloud governance define roles security policies and processes
Cloud governance define roles security policies and processesPresenting this set of slides with name - Cloud Governance Define Roles Security Policies And Processes. This is a five stage process. The stages in this process are Cloud Governance, Cloud Computing, Cloud Management.
-
 Pick pack inventory management reporting secure payment processing
Pick pack inventory management reporting secure payment processingPresenting this set of slides with name - Pick Pack Inventory Management Reporting Secure Payment Processing. This is an editable four stages graphic that deals with topics like Pick Pack, Inventory Management Reporting, Secure Payment Processing to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Skill matrix table identifying technical security and transaction processing
Skill matrix table identifying technical security and transaction processingPresenting this set of slides with name - Skill Matrix Table Identifying Technical Security And Transaction Processing. This is a three stage process. The stages in this process are Skill Matrix, Skill Mapping, Intelligence.
-
 Management experience process control advanced training privacy security
Management experience process control advanced training privacy securityPresenting this set of slides with name - Management Experience Process Control Advanced Training Privacy Security. This is an editable four graphic that deals with topics like Management Experience, Process Control, Advanced Training, Privacy Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security management integration directory process composer lifecycle management
Security management integration directory process composer lifecycle managementPresenting this set of slides with name - Security Management Integration Directory Process Composer Lifecycle Management. This is an editable three stages graphic that deals with topics like Security Management, Integration Directory, Process Composer, Lifecycle Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Major internet security technologies internet protocol stack stateful inspection
Major internet security technologies internet protocol stack stateful inspectionPresenting this set of slides with name - Major Internet Security Technologies Internet Protocol Stack Stateful Inspection. This is an editable four graphic that deals with topics like Major Internet Security Technologies, Internet Protocol Stack, Stateful Inspection to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Insurance claim process cashless intimate submit documents security pay
Insurance claim process cashless intimate submit documents security payPresenting this set of slides with name - Insurance Claim Process Cashless Intimate Submit Documents Security Pay. This is a five stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Insurance claim process intimate submit document security pay
Insurance claim process intimate submit document security payPresenting this set of slides with name - Insurance Claim Process Intimate Submit Document Security Pay. This is a four stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Insurance claim process intimate submit documents security pay
Insurance claim process intimate submit documents security payPresenting this set of slides with name - Insurance Claim Process Intimate Submit Documents Security Pay. This is a four stage process. The stages in this process are Insurance Claim Process, Insurance Claim Steps, Insurance Claim Procedure.
-
 Hotel safety and security emergency process with 5 boxes
Hotel safety and security emergency process with 5 boxesPresenting hotel safety and security emergency process with 5 boxes. This is a hotel safety and security emergency process with 5 boxes. This is a five stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Hotel safety and security procedures with converging arrows and boxes
Hotel safety and security procedures with converging arrows and boxesPresenting hotel safety and security procedures with converging arrows and boxes. This is a hotel safety and security procedures with converging arrows and boxes. This is a six stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.





