Powerpoint Templates and Google slides for Security Procedures
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Workplace Safety And Security Procedures Powerpoint Presentation Slides
Workplace Safety And Security Procedures Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Workplace Safety And Security Procedures Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Documentation Of Secure Data Backup And Restoration Procedures Training Ppt
Documentation Of Secure Data Backup And Restoration Procedures Training PptPresenting Documentation of Secure Data Backup and Restoration Procedures. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Procedure For Successful Website Security Management Action Plan
Procedure For Successful Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Introducing Procedure For Successful Website Security Management Action Plan to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Themes And Plugin, Improve Loading Time, Implement CSS using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Procedure Of Software Firewall In Network
Firewall Network Security Working Procedure Of Software Firewall In NetworkThis slide illustrates the working of a software firewall, including its architecture. The purpose of this slide is to showcase the working steps of a software firewall and its architecture. The architecture components include managed firewall as a service, a virtual firewall, and a containerized firewall. Present the topic in a bit more detail with this Firewall Network Security Working Procedure Of Software Firewall In Network Use it as a tool for discussion and navigation on Virtual Machine, Container, Private Cloud This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Ensuring Data Security In Onboarding Procedure
Icon For Ensuring Data Security In Onboarding ProcedureIntroducing our premium set of slides with Icon For Ensuring Data Security In Onboarding Procedure. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Data Onboarding, Digital Transformation. So download instantly and tailor it with your information.
-
 Security Audit Procedure Icon To Verify Company Data Protection
Security Audit Procedure Icon To Verify Company Data ProtectionPresenting our set of slides with Security Audit Procedure Icon To Verify Company Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Audit Procedure, Verify Company, Data Protection.
-
 Key Network Security Policies And Procedures
Key Network Security Policies And ProceduresThis slide demonstrates network security policies including access control, device control, account management, network usage and remote access policy. Presenting our set of slides with name Key Network Security Policies And Procedures. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Access Control Policy, Device Control Policy, Account Management Policy.
-
 Workplace security policy procedures ppt powerpoint presentation outline images cpb
Workplace security policy procedures ppt powerpoint presentation outline images cpbPresenting our Workplace Security Policy Procedures Ppt Powerpoint Presentation Outline Images Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Workplace Security Policy Procedures This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Security Checklist Policies And Procedures Cloud Information Security
Cloud Security Checklist Policies And Procedures Cloud Information SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Information Security This template helps you present information on four stages. You can also present information on Measures Organization, Technologies Security, Latest Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Policies And Procedures Cloud Computing Security
Cloud Security Checklist Policies And Procedures Cloud Computing SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Computing Security. This template helps you present information on five stages. You can also present information on Organization, Cloud Security, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit
It Security Audit With Risk Level Procedure To Perform Digital Marketing AuditThis slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Present the topic in a bit more detail with this It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit. Use it as a tool for discussion and navigation on Inactive User Accounts, Inactive Computer Accounts, Empty Security Groups. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Checklist Policies And Procedures Cloud Data Protection
Cloud Security Checklist Policies And Procedures Cloud Data ProtectionThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organization, On Boarding Employees, Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Data Protection And Information Security Policy And Procedure Staff Induction Training Guide
Data Protection And Information Security Policy And Procedure Staff Induction Training GuideThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Present the topic in a bit more detail with this Data Protection And Information Security Policy And Procedure Staff Induction Training Guide. Use it as a tool for discussion and navigation on Applicable, Enforcement, Organization Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Warehouse Security Policy And Procedure Icon
Data Warehouse Security Policy And Procedure IconIntroducing our Data Warehouse Security Policy And Procedure Icon set of slides. The topics discussed in these slides are Data Warehouse Security Policy, Procedure Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff
Data Protection And Information Security Policy And Procedure Corporate Induction Program For New StaffThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Introducing Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection, Information, Procedure, using this template. Grab it now to reap its full benefits.
-
 Business Strategic Objectives And Security Procedures
Business Strategic Objectives And Security ProceduresThis slide covers business strategic objectives and security procedures which includes security process controlling. Presenting our well structured Business Strategic Objectives And Security Procedures. The topics discussed in this slide are Business Strategic, Objectives Security, Procedures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Protection And Information Security Policy Company Policies And Procedures Manual
Data Protection And Information Security Policy Company Policies And Procedures ManualThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Increase audience engagement and knowledge by dispensing information using Data Protection And Information Security Policy Company Policies And Procedures Manual. This template helps you present information on one stage. You can also present information on Applicable, Enforcement, Policy And Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Procedure Compliance Security Illustration
Risk Procedure Compliance Security IllustrationThis colourful PowerPoint Illustration is a visual representation of the Risk Procedure. It is a helpful tool for quickly understanding the process and for making the procedure easier to remember.
-
 Cyber Security Policy Byod Procedure Device Protocols For Workers
Cyber Security Policy Byod Procedure Device Protocols For WorkersThis slide represents the device protocols that are the first step in the BYOD procedure. It also includes the software information that should be installed on the employees personal devices. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Byod Procedure Device Protocols For Workers. This template helps you present information on four stages. You can also present information on Software, Business, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
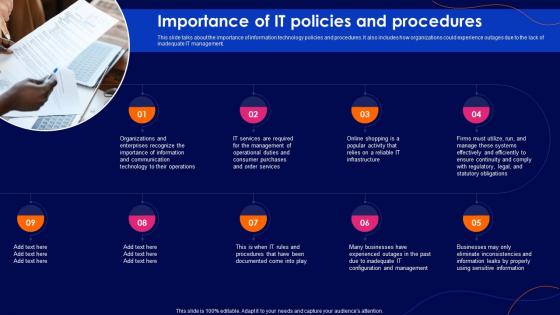 Cyber Security Policy Importance Of It Policies And Procedures
Cyber Security Policy Importance Of It Policies And ProceduresThis slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Importance Of It Policies And Procedures. This template helps you present information on nine stages. You can also present information on Services, Operational, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy What Happens In The Absence Of It Policies And Procedures
Cyber Security Policy What Happens In The Absence Of It Policies And ProceduresThis slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Introducing Cyber Security Policy What Happens In The Absence Of It Policies And Procedures to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Procedures, Information, Corporations, using this template. Grab it now to reap its full benefits.
-
 Hotel safety and security procedures with converging arrows and boxes
Hotel safety and security procedures with converging arrows and boxesPresenting hotel safety and security procedures with converging arrows and boxes. This is a hotel safety and security procedures with converging arrows and boxes. This is a six stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
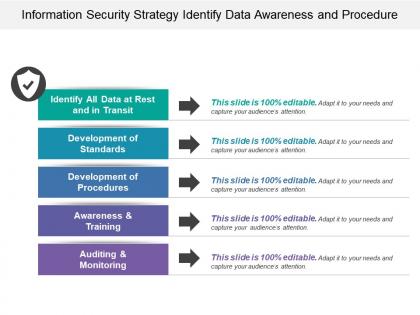 Information security strategy identify data awareness and procedure
Information security strategy identify data awareness and procedurePresenting this set of slides with name - Information Security Strategy Identify Data Awareness And Procedure. This is a five stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Cyber security audit procedures ppt powerpoint presentation infographics slides cpb
Cyber security audit procedures ppt powerpoint presentation infographics slides cpbPresenting this set of slides with name Cyber Security Audit Procedures Ppt Powerpoint Presentation Infographics Slides Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Audit Procedures to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Requirement for security planning and risk management procedure
Requirement for security planning and risk management procedurePresenting our well structured Requirement For Security Planning And Risk Management Procedure. The topics discussed in this slide are Requirement Security, Planning Risk, Management Procedure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Payroll security procedures ppt powerpoint presentation infographics slide portrait cpb
Payroll security procedures ppt powerpoint presentation infographics slide portrait cpbPresenting our Payroll Security Procedures Ppt Powerpoint Presentation Infographics Slide Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Payroll Security Procedures This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud security checklist policies and procedures cloud security it ppt tips
Cloud security checklist policies and procedures cloud security it ppt tipsThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Introducing Cloud Security Checklist Policies And Procedures Cloud Security IT Ppt Tips to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Considering Cloud Security, Procedures Strictly In The Organization, Security, using this template. Grab it now to reap its full benefits.
-
 Policy procedures security ppt powerpoint presentation inspiration templates cpb
Policy procedures security ppt powerpoint presentation inspiration templates cpbPresenting our Policy Procedures Security Ppt Powerpoint Presentation Inspiration Templates Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Policy Procedures Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.



