Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Based ATP Cyber Security Solution
Cloud Based ATP Cyber Security SolutionThis slide depicts the cloud based ATP cyber security solution system. Its objective is to use cloud platforms for security solution in advanced threat protection. This slide includes network service, cloud, email and endpoints. Presenting our set of slides with name Cloud Based ATP Cyber Security Solution. This exhibits information on One stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Service, Learning Algorithm, Machine Learning.
-
 Comparative Analysis Of ATP Cyber Security Tools
Comparative Analysis Of ATP Cyber Security ToolsThis slide depicts the comparative analysis of ATP cyber security tools. Its aim is to use the tools to protect the system from advanced threats. This slide include Microsoft defender, ESET endpoint, Palo Alto network, Fortinet sandbox. Presenting our set of slides with name Comparative Analysis Of ATP Cyber Security Tools. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Microsoft Defender, ESET Endpoint, Palo Alto Network, Fortinet Sandbox.
-
 Essential Components Of ATP Cyber Security
Essential Components Of ATP Cyber SecurityThis slide depicts the essential components of ATP cyber security. Its aim is to use these components to safeguard organisational system against any threats. This slide include detection of stealthy threats, software behaviour and analysis of data. Presenting our set of slides with name Essential Components Of ATP Cyber Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Stealthy Threats, Analysis Of Data, Benign Software Behaviour.
-
 Impact Of ATP Cyber Security Automation
Impact Of ATP Cyber Security AutomationThis slide depicts the ATP cyber security automation to detect virus. Its aim is to help prevent the virus in the system. This slide includes prevention, detection and mitigate. Presenting our set of slides with name Impact Of ATP Cyber Security Automation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prevent, Detec, Mitigate.
-
 Implement ATP Cyber Security Strategies In Organisation
Implement ATP Cyber Security Strategies In OrganisationThis slide depicts the strategies for cyber security ATP. Its objective is to help formulate advanced strategies for threat protection. This slide includes broad test repository, benign software behaviour, analysis of data, etc. Presenting our set of slides with name Implement ATP Cyber Security Strategies In Organisation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Broad Test Repository, Benign Software Behaviour, Analysis Of Data.
-
 Measure ATP Cyber Security Solution Metrics
Measure ATP Cyber Security Solution MetricsThis slide showcases the measures taken for ATP cyber security solution metrics. Its aim is to detect and calculate the amount of response generated by metrics. This slide includes false positive rate, time to detection, threat coverage, incident response, etc. Presenting our set of slides with name Measure ATP Cyber Security Solution Metrics. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Coverage, Incident Response, Detection Rate, False Positive Rate, Time To Detection.
-
 Shift Left Testing Security Implementation Methods
Shift Left Testing Security Implementation MethodsThis slide showcases the tools for shift left testing.Its aim is to deploy and reinforce security code base and increase security.This slide includes static application system testing, dynamic application security.Presenting our set of slides with Shift Left Testing Security Implementation Methods This exhibits information on four stages of the process.This is an easy to edit and innovatively designed PowerPoint template.So download immediately and highlight information on Remediate Seamlessly, Immediate Remediation, Environment.
-
 How Does Secure Blockchain Network Operates Ultimate Handbook For Blockchain BCT SS V
How Does Secure Blockchain Network Operates Ultimate Handbook For Blockchain BCT SS VThis slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Deliver an outstanding presentation on the topic using this How Does Secure Blockchain Network Operates Ultimate Handbook For Blockchain BCT SS V Dispense information and present a thorough explanation of Transaction Requested, Transaction Is Completed, Blockchain using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Enhance Cyber Security Of SCADA Networks
Checklist To Enhance Cyber Security Of SCADA NetworksThis slide represents checklist that assist IT companies to enhance their SCADA networks cyber security for improving data protection. It includes various elements such as recognizing connections, disconnecting irrelevant networks, etc. Introducing our Checklist To Enhance Cyber Security Of SCADA Networks set of slides. The topics discussed in these slides are Essential Connections, Inadvertent Disclosure, SCADA Network This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison Analysis Of SCADA Cyber Security Solutions
Comparison Analysis Of SCADA Cyber Security SolutionsThis slide represents comparison analysis of various solutions that assist IT companies to enhance their SCADA cyber security and data protection. It includes various solutions such as Indegy, clarity, Nozomi networks, and Dragos. Presenting our well structured Comparison Analysis Of SCADA Cyber Security Solutions The topics discussed in this slide are Anomaly Detection, Asset Discovery, Vulnerability Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Framework For SCADA Cyber Security Policy
Framework For SCADA Cyber Security PolicyThis slide represents framework of various policies that assist IT companies to optimize their SCADA cyber security for effective data protection. It includes policies related to data security, platform security, communication security, audit, etc. Introducing our Framework For SCADA Cyber Security Policy set of slides. The topics discussed in these slides are System Security Program, Cyber Security Policy This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Gantt Chart To Optimize SCADA Cyber Security
Gantt Chart To Optimize SCADA Cyber SecurityThis slide represents Gantt chart that assist IT companies to optimize their SCADA network cyber security for improving their data protection. It includes various steps such as disconnecting systems, identifying connections, etc. Presenting our well structured Gantt Chart To Optimize SCADA Cyber Security The topics discussed in this slide are Identify Connections, Conduct Technical Audits. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Pillars Of SCADA Cyber Security Framework
Pillars Of SCADA Cyber Security FrameworkThis slide represents various pillars of SCADA cyber security framework assisting companies to enhance their data protection. It includes various pillars such as governance control, SCADA control, system assurance, etc. Presenting our set of slides with Pillars Of SCADA Cyber Security Framework This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance Control, SCADA Controls, Peripheral Controls
-
 SCADA Cyber Security Elements Structure
SCADA Cyber Security Elements StructureThis slide represents structured overview of various SCADA cyber security elements and strategies to enhance layer protection effectively. It includes various layers such as physical protection, network protection, end-point protection, etc. Presenting our well structured SCADA Cyber Security Elements Structure The topics discussed in this slide are SCADA Security, SCADA Cybersecurity, Application Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Training Schedule For Enhancing SCADA Cyber Security
Training Schedule For Enhancing SCADA Cyber SecurityThis slide represents training schedule that helps IT companies to plan education sessions on SCADA cyber security for their IT employees effectively. It includes various components such as course, details, duration, etc. Introducing our Training Schedule For Enhancing SCADA Cyber Security set of slides. The topics discussed in these slides are Duration, Platform, Deadline This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Simulation Based Cyber Security Training Program
Simulation Based Cyber Security Training ProgramThis slide represents simulation based training program for cyber security awareness including components such as session name, expected impact, duration, etc. Introducing our premium set of slides with Simulation Based Cyber Security Training Program Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Customer Data Protection, Attack Mitigation, Duration. So download instantly and tailor it with your information.
-
 Analyzing Mobile Application Security Checklist
Analyzing Mobile Application Security ChecklistThis slide covers checklist to analyze mobile security for long-term scenarios and includes tasks, applicable and not applicable. Presenting our set of slides with name Analyzing Mobile Application Security Checklist. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Tasks, Applicable, Not Applicable.
-
 Challenges And Solutions Of Mobile Device Security
Challenges And Solutions Of Mobile Device SecurityThis slide highlights challenging solutions for mobile security and includes diverse ecosystems, data leakage, and evolving threats. Presenting our set of slides with name Challenges And Solutions Of Mobile Device Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Challenges, Solutions, Impact, Diverse Ecosystems.
-
 Comparative Analysis Of Mobile Security Tools
Comparative Analysis Of Mobile Security ToolsThis slide showcases mobile security software applications comparison matrix and includes anti-theft protection, remote SMS control, call blocking, web protection, and wi-fi protection. Introducing our Comparative Analysis Of Mobile Security Tools set of slides. The topics discussed in these slides are Anti- Theft Protection, Remote Sms Control, Call Blocking, Web Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison Of Mobile Security Solution Capabilities
Comparison Of Mobile Security Solution CapabilitiesThis slide highlights mobile security solutions comparative assessment and includes core expertise, mobile threat detection and response. Presenting our set of slides with name Comparison Of Mobile Security Solution Capabilities. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unified Device Management, Threat Detection And Response, Mobile Security Solutions.
-
 Developing Holistic Approach Using Mobile Security Framework
Developing Holistic Approach Using Mobile Security FrameworkThis slide represents mobile security framework approaches and includes secure devices, safeguard applications, and content protection. Presenting our set of slides with name Developing Holistic Approach Using Mobile Security Framework. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Devices, Safeguard Applications, Content Protection.
-
 Impactful Areas Of Mobile Application Security
Impactful Areas Of Mobile Application SecurityThis slide exhibits key areas of testing applications based on mobile security and includes customer information, financial information, and cloning. Presenting our set of slides with name Impactful Areas Of Mobile Application Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Customer Information, Financial Information, Cloning.
-
 Key Best Practices Of Mobile Security
Key Best Practices Of Mobile SecurityThis slide depicts mobile security practices to protect devices and includes device protection passwords, install anti-malware software, avoid public wi-fi, and update software. Presenting our set of slides with name Key Best Practices Of Mobile Security. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Device Protection Passwords, Install Anti-Malware Software, Avoid Public Wi-Fi, Update Software.
-
 Mobile Application Security Risk Assessment
Mobile Application Security Risk AssessmentThis slide demonstrates mobile application security to assess risks and includes improper platform usage, insecure data storage, and insecure communication. Presenting our set of slides with name Mobile Application Security Risk Assessment. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Improper Platform Usage, Insecure Data Storage, Insecure Communication.
-
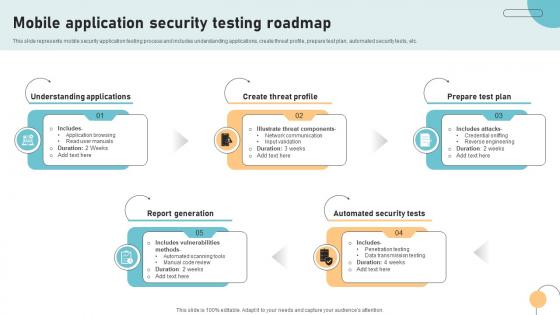 Mobile Application Security Testing Roadmap
Mobile Application Security Testing RoadmapThis slide represents mobile security application testing process and includes understanding applications, create threat profile, prepare test plan, automated security tests, etc. Presenting our set of slides with name Mobile Application Security Testing Roadmap. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understanding Applications, Report Generation, Create Threat Profile, Automated Security Tests, Prepare Test Plan.
-
 Mobile Device Security Methods For Advanced Protection
Mobile Device Security Methods For Advanced ProtectionThis slide displays mobile device security methods to protect networks and includes CASB, endpoint protection, VPN, and secure web gateway. Presenting our set of slides with name Mobile Device Security Methods For Advanced Protection. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Endpoint Protection, Casb, Vpn, Secure Web Gateway.
-
 Mobile Security Architecture On Android Platform
Mobile Security Architecture On Android PlatformThis slide illustrates architectural diagram of mobile security for android users and includes tools, software framework, modules, and kernel space. Introducing our Mobile Security Architecture On Android Platform set of slides. The topics discussed in these slides are Tools, Software Framework, Modules, Kernel Space. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Security Awareness Training Program
Mobile Security Awareness Training ProgramThis slide exhibits training program for mobile security to spread awareness along with training topics, session details, number of employees, and cases before and after training. Introducing our Mobile Security Awareness Training Program set of slides. The topics discussed in these slides are Cybersecurity Awareness, Phishing, Password Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Security For Securing Communication Channel Icon
Mobile Security For Securing Communication Channel IconPresenting our set of slides with name Mobile Security For Securing Communication Channel Icon. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mobile Security For Securing, Communication Channel Icon.
-
 Mobile Security Icon For Implementing Authentication Measures
Mobile Security Icon For Implementing Authentication MeasuresPresenting our set of slides with name Mobile Security Icon For Implementing Authentication Measures. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mobile Security Icon For Implementing, Authentication Measures.
-
 Mobile Security Icon To Safeguard Sensitive Data
Mobile Security Icon To Safeguard Sensitive DataPresenting our set of slides with name Mobile Security Icon To Safeguard Sensitive Data. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mobile Security Icon, Safeguard Sensitive Data.
-
 Mobile Security Threats And Risk Assessment
Mobile Security Threats And Risk AssessmentThis slide showcases risk and threat evaluation of mobile security and includes security breaches, phishing attacks, and mobile ransomware. Introducing our Mobile Security Threats And Risk Assessment set of slides. The topics discussed in these slides are Security Breaches, Phishing Attacks, Mobile Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Security Two Factor Authentication Process
Mobile Security Two Factor Authentication ProcessThis slide showcases roadmap for 2FA mobile security and includes assessment, select solutions, planning and integration, implementation, etc. Presenting our set of slides with name Mobile Security Two Factor Authentication Process. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment, Select Solution, Implementation, Testing And Optimization.
-
 Mobile SMS Phishing Security Attacks
Mobile SMS Phishing Security AttacksThis slide focuses on different SMS phishing attacks to hamper mobile security and include financial fraud, sense of urgency, and compromised security. Introducing our Mobile SMS Phishing Security Attacks set of slides. The topics discussed in these slides are Financial Fraud, Sense Of Urgency, Compromised Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Crisis Evaluation For Workplace Safety And Security
Crisis Evaluation For Workplace Safety And SecurityThe purpose of this slide is to emphasize how crisis evaluation for workplace safety and security ensures a systematic assessment, facilitating the implementation of measures to enhance workplace safety, security, and effective response during emergencies. Introducing our premium set of slides with Crisis Evaluation For Workplace Safety And Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Emergency Response Planning, Workplace Violence Prevention. So download instantly and tailor it with your information.
-
 Cyber Security Mesh Applications For Business
Cyber Security Mesh Applications For BusinessThe following slide features key elements like IAM support, MSSPS, identity-proofing tools, standards, and demographic bias in illustrating the diverse applications of cybersecurity mesh for business. This aids in understanding its potential impact on security and operations. Presenting our set of slides with Cyber Security Mesh Applications For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mesh Supporting Iam Requests, Identity Life Cycle, Decentralized Identity Standards
-
 Cyber Security Mesh Architecture
Cyber Security Mesh ArchitectureThe following slide highlights components like centralized dashboard, alerting, investigation, reporting, users, robotics, and processes in the cybersecurity mesh architecture. It aids in illustrating the structure and functionalities of the system. Presenting our well structured Cyber Security Mesh Architecture The topics discussed in this slide are Centralized Dashboard, Centralized Alerting, Centralized Reporting This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Mesh Benefits For Business
Cyber Security Mesh Benefits For BusinessThe following slide emphasizes IAM support, MSSPS, identity-proofing tools, standards, and addressing demographic bias to illustrate the business benefits of cybersecurity mesh. It aids in recognizing the advantages it offers to businesses in enhancing security and inclusivity. Presenting our set of slides with Cyber Security Mesh Benefits For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iam Support, Identity Standards, Identity Proofing
-
 Cyber Security Mesh Improved Scalability
Cyber Security Mesh Improved ScalabilityIntroducing our Cyber Security Mesh Improved Scalability set of slides. The topics discussed in these slides are Cyber Security Mesh, Improved Scalability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Four Layers Of Cyber Security Mesh
Four Layers Of Cyber Security MeshThe following slide features essential elements such as security analytics, consolidated policy management, Distributed identity fabric, and unified dashboards to depict the four layers of cybersecurity mesh. This aids in understanding the comprehensive structure and capabilities of cyber mesh. Presenting our set of slides with Four Layers Of Cyber Security Mesh This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Posture Management, Distributed Identity Fabric, Consolidated Dashboards
-
 Key Considerations Before Implementing Cyber Security Mesh
Key Considerations Before Implementing Cyber Security MeshThe following slide emphasizes essential factors like connecting to VMs, developing tooling, observability, multi-cluster security, and mesh capabilities in pre-implementation considerations for cybersecurity mesh. This aids in preparing a robust strategy for successful cyber mesh integration. Presenting our set of slides with Key Considerations Before Implementing Cyber Security Mesh This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment Tooling, Exposing Mesh Capabilities, Observability
-
 Reducing Attack Surface By Cyber Security Mesh Icon
Reducing Attack Surface By Cyber Security Mesh IconIntroducing our premium set of slides with Reducing Attack Surface By Cyber Security Mesh Icon Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Reducing Attack Surface, Cyber Security Mesh Icon. So download instantly and tailor it with your information.
-
 Addressing Mobile Application Security Gap For Risk Protection
Addressing Mobile Application Security Gap For Risk ProtectionFollowing slide showcases application security vulnerabilities of mobiles for risk protection. It further includes factors such as poor server-side controls, accidental data leak, poor authorization alongside description, solution, etc. Introducing our Addressing Mobile Application Security Gap For Risk Protection set of slides. The topics discussed in these slides are Poor Server Side Controls, Accidental Data Leak, Poor Authorization, Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Security Gap In Network Business
Best Practices For Security Gap In Network BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with name Best Practices For Security Gap In Network Business. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prioritize Data Encryption, Regular Security Audits, Ensure Compliance.
-
 Checklists For Security Gap Web Application
Checklists For Security Gap Web ApplicationThis slide highlights a security vulnerability web application checklist for mitigation of risks. It further covers authentication of all files for configuration and authentication of all cyber variables alongside priority and responsible person. Introducing our Checklists For Security Gap Web Application set of slides. The topics discussed in these slides are Data Received, Semantics For Exception Handling, Cyber Variables. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Security Gap Software Application
Comparative Analysis Of Security Gap Software ApplicationFollowing slide highlights software applications security gap analysis for enhanced user trust. It further covers tools, best used for, free trial, price and rating along with deployment such as desktop app, on-premise and web hosted etc. Introducing our Comparative Analysis Of Security Gap Software Application set of slides. The topics discussed in these slides are Tool, Deployment, Free Trial, Price, Our Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Gap Analysis Process
Cyber Security Gap Analysis ProcessThis slide covers procedure for cyber security gap analysis such as establishing security goal, assembling skilled team, and gathering documentation to identify and address vulnerabilities and shortcomings in an organizations security measures to enhance overall resilience against cyber threats. Presenting our set of slides with name Cyber Security Gap Analysis Process. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Establish Security Goal, Assemble Skilled Team, Gather Necessary Documentation.
-
 Cyber Security Threat Icon To Prevent Gap
Cyber Security Threat Icon To Prevent GapPresenting our set of slides with name Cyber Security Threat Icon To Prevent Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Threat, Icon Prevent Gap.
-
 Different Types Of Security Gap Mitigation Techniques
Different Types Of Security Gap Mitigation TechniquesThis slide showcases various types of security gaps for data protection to showcase data encryption for shared data. This includes role-based access control, encrypted file sharing, regular security audits, etc. Presenting our set of slides with name Different Types Of Security Gap Mitigation Techniques. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Role Based Access Control, Data Encryption Techniques, Secure Data Access Methods.
-
 Implementing Security Gap Visualization In System
Implementing Security Gap Visualization In SystemThis slide showcases process of implementing visualization security. The main purpose of this template is to showcase various steps of data visualization in business. This includes data assessment, access control policies, train employees, etc. Presenting our set of slides with name Implementing Security Gap Visualization In System. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Assessment, Select Secure Visualization Tools, Establish Access Control Policies, Regular Security Monitoring.
-
 Methods To Test Security Gaps For Enhanced Safety
Methods To Test Security Gaps For Enhanced SafetyThis slide covers slide showcases security gap analysis test methods for enhanced safety. It further covers testing techniques such as active, passive, network and distributed testing. Presenting our set of slides with name Methods To Test Security Gaps For Enhanced Safety. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Active Testing, Network Testing, Passive Testing, Distributed Testing.
-
 Security Gap Analysis Icon For IT Team
Security Gap Analysis Icon For IT TeamPresenting our set of slides with name Security Gap Analysis Icon For IT Team. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Gap Analysis Icon, IT Team.
-
 Security Gap Measurement Tools Comparative Analysis
Security Gap Measurement Tools Comparative AnalysisThis slide outlines represents security vulnerability performance by comparative analysis tools for choosing the best option. It further covers tools, free trials, prices, reviews, and features such as scanning global and local network ranges, custom extensions, etc. The following. Introducing our Security Gap Measurement Tools Comparative Analysis set of slides. The topics discussed in these slides are Scan Global, Local Network Ranges, Automate Vulnerabilities, Custom Extension. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Gap Report Analysis For Business
Security Gap Report Analysis For BusinessThis slide covers security gap analysis report for companies to To identify vulnerabilities and weaknesses in the current security infrastructure, enabling proactive measures to safeguard business assets and sensitive information. Introducing our Security Gap Report Analysis For Business set of slides. The topics discussed in these slides are Improvement Required, Improvement Recommended, Improvement Available, Improvement Completed. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies For Identifying Security Gap In Network
Strategies For Identifying Security Gap In NetworkThe following slide represents identifying tactics of gaps in security network for improving data structure. It further covers run network audit, analyse system log data and audit IT supply chain. Introducing our Strategies For Identifying Security Gap In Network set of slides. The topics discussed in these slides are Run Network Audit, Analyse System Log Data, Audit IT Supply Chain. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat Detection Icon To Manage Security Gap
Threat Detection Icon To Manage Security GapPresenting our set of slides with name Threat Detection Icon To Manage Security Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Detection Icon, Manage Security Gap.
-
 Icon For Role Of 5g Technology In Retail Cyber Security
Icon For Role Of 5g Technology In Retail Cyber SecurityIntroducing our Icon For Role Of 5g Technology In Retail Cyber Security set of slides. The topics discussed in these slides are Icon For Role Of 5G Technology, Retail Cyber Security This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Utilization Of Blockchain In Retail Cyber Security
Icon For Utilization Of Blockchain In Retail Cyber SecurityPresenting our well structured Icon For Utilization Of Blockchain In Retail Cyber Security The topics discussed in this slide are Icon For Utilization Of Blockchain, Retail Cyber Security This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Monitoring Home Safety Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Monitoring Home Safety Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon features a smoke detector, making it perfect for presentations on fire safety, home security, and emergency preparedness. The icon is designed with vibrant colours and clear graphics to grab the audiences attention and effectively convey the importance of having a smoke detector in every home.
-
 Security Monitoring Home Safety Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Monitoring Home Safety Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon features a smoke detector, perfect for presentations related to fire safety and prevention. The simple design and neutral color make it suitable for a variety of themes and backgrounds. Add this icon to your slides to enhance the visual appeal and convey important information about smoke detectors.





