Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Internet Gateway Security IT Introduction To Next Generation Secure Web
Internet Gateway Security IT Introduction To Next Generation Secure WebThis slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Introducing Internet Gateway Security IT Introduction To Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Applications, Services, Risks Enabled, Vulnerability, Public Resources, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Secure Web Gateway Technology
Internet Gateway Security IT Introduction To Secure Web Gateway TechnologyThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Introducing Internet Gateway Security IT Introduction To Secure Web Gateway Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, Application Control, Website Content Inspection, Data Loss Prevention, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway
Internet Gateway Security IT Key Benefits Of Using Secure Web GatewayThis slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Introducing Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Improved Security, Increased Productivity, Reduced Risk Of Data Loss, Compliance, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Growth Drivers Of Next Generation
Internet Gateway Security IT Key Growth Drivers Of Next GenerationThis slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Introducing Internet Gateway Security IT Key Growth Drivers Of Next Generation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Growing Cloud Applications, Services, Rising Data Theft And Vulnerability, Cloud Dominated World, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Secure Web Gateway Solution Providers
Internet Gateway Security IT Key Secure Web Gateway Solution ProvidersThis slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Introducing Internet Gateway Security IT Key Secure Web Gateway Solution Providers to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cisco, Symantec, Forcepoint, Fortinet, Barracuda Networks, using this template. Grab it now to reap its full benefits.
-
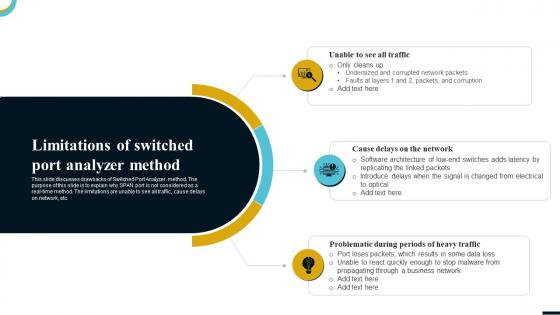 Internet Gateway Security IT Limitations Of Switched Port Analyzer Method
Internet Gateway Security IT Limitations Of Switched Port Analyzer MethodThis slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. Introducing Internet Gateway Security IT Limitations Of Switched Port Analyzer Method to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unable To See All Traffic, Cause Delays On The Network, Problematic During Periods Heavy Traffic, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Prominent Users Of Secure Web Gateway
Internet Gateway Security IT Prominent Users Of Secure Web GatewayThis slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Introducing Internet Gateway Security IT Prominent Users Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on IT Security Experts, Network Administrators, Compliance Officers, HR Managers, Business Executives, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway
Internet Gateway Security IT Reasons Behind Need For Secure Web GatewayThis slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Introducing Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Rise In Web-Based Threats, Non-Compliance To Security Policies, Need Of Access Control, Web Traffic Monitoring, Remote Worker Protection, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Relationship Between Secure Access Service
Internet Gateway Security IT Relationship Between Secure Access ServiceThis slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Introducing Internet Gateway Security IT Relationship Between Secure Access Service to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Administration Of Microservices, Distributed Environment, Visibility Control Over Traffic Passing, Cloud-Native Application, using this template. Grab it now to reap its full benefits.
-
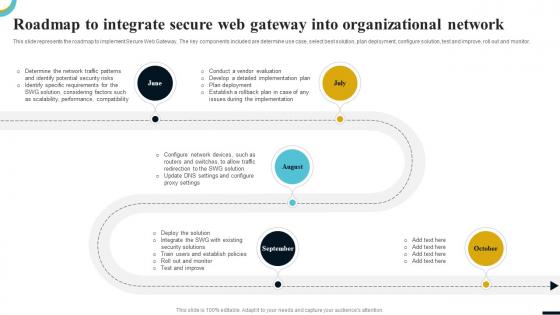 Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway
Internet Gateway Security IT Roadmap To Integrate Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Performance, Compatibility, Implementation, Plan Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Architecture And Working
Internet Gateway Security IT Secure Web Gateway Architecture And WorkingThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Introducing Internet Gateway Security IT Secure Web Gateway Architecture And Working to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Malware Detection, Web Proxy, Public Internet, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Challenges And Solutions
Internet Gateway Security IT Secure Web Gateway Challenges And SolutionsThis slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Challenges And Solutions. Use it as a tool for discussion and navigation on Increasingly, Sophisticated Threats, Encrypted Traffic, Cloud-Based Applications, Mobile Devices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Secure Web Gateway For Remote And On Site
Internet Gateway Security IT Secure Web Gateway For Remote And On SiteThis slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Introducing Internet Gateway Security IT Secure Web Gateway For Remote And On Site to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Remote Users, Internet, Cloud Based Secure Web Gateway, Secure Web Gateway, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation
Internet Gateway Security IT Secure Web Gateway ImplementationThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Secure Web Gateway Implementation to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway, Internet Connected Network Site, Administrative Costs, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation Scenarios
Internet Gateway Security IT Secure Web Gateway Implementation ScenariosThis slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. Introducing Internet Gateway Security IT Secure Web Gateway Implementation Scenarios to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Inline, Transparent, Explicit, SPAN, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Configuration
Internet Gateway Security IT Secure Web Gateway Set Up ConfigurationThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Configuration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Configure Web Gateway Software, Install And Configure SSL, TLS Certificates, Establish Security Policies, Set Up Access Restrictions, Test The Web Gateway, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Ongoing
Internet Gateway Security IT Secure Web Gateway Set Up OngoingThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Ongoing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Inspect Web Gateway, Examine Security Policies, Train Staff And Users, Update And Patch Software, Perform Routine Security Audits, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Planning
Internet Gateway Security IT Secure Web Gateway Set Up PlanningThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Define Scope Of Project, Identify Network Architecture, Define Security Policy, Select Appropriate Hardware And Software, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Training Program
Internet Gateway Security IT Secure Web Gateway Training ProgramThis slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Training Program. Use it as a tool for discussion and navigation on Agenda, System Requirements, Mode, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Steps To Integrate Secure Web Gateway
Internet Gateway Security IT Steps To Integrate Secure Web GatewayThis slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Introducing Internet Gateway Security IT Steps To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Steps To Select Next Generation Secure Web
Internet Gateway Security IT Steps To Select Next Generation Secure WebThis slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Introducing Internet Gateway Security IT Steps To Select Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Adopt Real Cloud Architecture, Decodes Apps And Cloud Services, Adapts To New Threats, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Swg Implementation Methodology Span Switched
Internet Gateway Security IT Swg Implementation Methodology Span SwitchedThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Swg Implementation Methodology Span Switched to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway Rules, Deployment, Monitoring, Transparent Modes, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Table Of Contents
Internet Gateway Security IT Table Of ContentsIntroducing Internet Gateway Security IT Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Secure Web Gateway Technology, Industries, using this template. Grab it now to reap its full benefits.
-
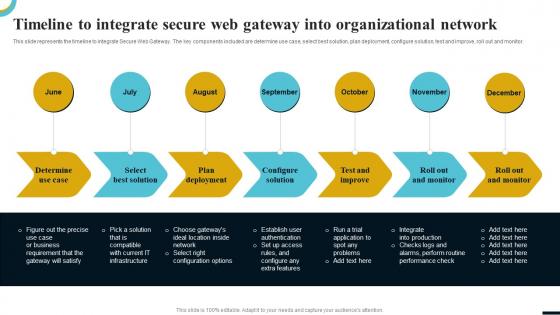 Internet Gateway Security IT Timeline To Integrate Secure Web Gateway
Internet Gateway Security IT Timeline To Integrate Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Timeline To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Understanding Real World Use Cases Of Secure
Internet Gateway Security IT Understanding Real World Use Cases Of SecureThis slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. Introducing Internet Gateway Security IT Understanding Real World Use Cases Of Secure to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Real Time Web Traffic Surveillance, Blocking Of Harmful, Websites And Programs, Access Management, Rule Enforcement, On-Site And Remote Personnel, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Working Components Of Secure Web Gateway
Internet Gateway Security IT Working Components Of Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Introducing Internet Gateway Security IT Working Components Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, URL Filtering, Application Control, Website Content Inspection, Secure Socket Layer SSL Inspection, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Implementation Internet Gateway Security IT
Secure Web Gateway Implementation Internet Gateway Security ITThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Secure Web Gateway Implementation Internet Gateway Security IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Manages Network Connection, Concentrates Most Sensitive, Protocols And Channels, Fewer Possible Disturbances Network, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Internet Gateway Security IT
Secure Web Gateway Internet Gateway Security ITThis slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Secure Web Gateway Internet Gateway Security IT to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Implement, Process And Manage, HTTP Traffic Connected, Internet, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Internet Gateway Security IT
Table Of Contents Internet Gateway Security ITIntroducing Table Of Contents Internet Gateway Security IT to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on SWG Budget And Training, Case Study And Use Cases, SWG Market And Trends, using this template. Grab it now to reap its full benefits.
-
 Comparison Between Security Incident And Security Breach
Comparison Between Security Incident And Security BreachThis slide showcases the comparison between security incident and security breaches. The purpose of this slide is to help the business deploy suitable responses in order to control the damage. It includes comparison on the basis of description, scope, etc. Introducing our premium set of slides with Comparison Between Security Incident And Security Breach. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Risk, Minor Inconveniences, Organization Networks. So download instantly and tailor it with your information.
-
 Comparison Between Security Incident And Security Event
Comparison Between Security Incident And Security EventThis slide highlights the comparison between security incident and security event. The purpose of this slide is to help ensure the business undertakes suitable actions in order to resolve the security lapse. It includes comparison on the basis of severity, nature of occurrence, etc. Presenting our set of slides with Comparison Between Security Incident And Security Event. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business Confidentiality, Malware Attempts, Unintentional Occurrence.
-
 Components Of Business Security Incident Response Plans
Components Of Business Security Incident Response PlansThis slide highlights the components of business security incident response plan. The purpose of this slide is to help the business develop effective security incident response plans through the use of components use as incident taxonomy, data classification frameworks, etc. Introducing our premium set of slides with Components Of Business Security Incident Response Plans. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operating Models, Performance Objectives, Incident Taxonomy. So download instantly and tailor it with your information.
-
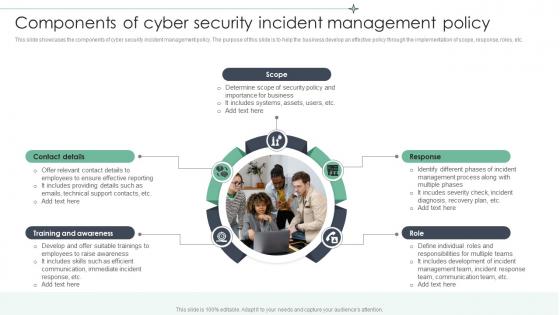 Components Of Cyber Security Incident Management Policy
Components Of Cyber Security Incident Management PolicyThis slide showcases the components of cyber security incident management policy. The purpose of this slide is to help the business develop an effective policy through the implementation of scope, response, roles, etc. Presenting our set of slides with Components Of Cyber Security Incident Management Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Contact Details, Training And Awareness, Includes Systems.
-
 Critical Teams During Security Incident Response Planning
Critical Teams During Security Incident Response PlanningThis slide highlights the critical teams required during security incident response planning. The purpose of this slide is to help ensure suitable teams and stakeholders are engaged to manage the security incident. It includes manager for incident response plan, security officer, etc. Introducing our premium set of slides with Critical Teams During Security Incident Response Planning. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Outsourced Cybersecurity, Key Decision, Analyzing Incidents. So download instantly and tailor it with your information.
-
 Examples Of Security Incident Response Plans
Examples Of Security Incident Response PlansThis slide highlights the examples of security incident response plans. The purpose of this slide is to help understand the importance of incident response plans. It includes computer security incident response team, security operations center, etc. Presenting our set of slides with Examples Of Security Incident Response Plans. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Response Team, Computer Security, Computer Emergency.
-
 Five Step Security Incident Response Plan
Five Step Security Incident Response PlanThis slide represents the primary use cases of a software defined wide area network. The use cases include geographical expansion, making better use of WAN bandwidth, improving WAN resilience, and cloud migration. Introducing our premium set of slides with Five Step Security Incident Response Plan. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Build Action Plan, Collate Information, Gather Resources. So download instantly and tailor it with your information.
-
 Implementation Checklist Plan For Security Incident
Implementation Checklist Plan For Security IncidentPresenting our set of slides with Implementation Checklist Plan For Security Incident. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation Checklist Plan, Security Incident.
-
 Methods To Prevent And Mitigate Security Incidents
Methods To Prevent And Mitigate Security IncidentsThis slide depicts the multiple methods to prevent and mitigate security incidents. The purpose of this slide is to help the business identify a suitable approach to eliminate current and future security incidents. It includes security incident detection, tracking suspicious activity, etc. Presenting our set of slides with Methods To Prevent And Mitigate Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident, Account Behavior, Monitor Network Traffic.
-
 Multiple Response Strategies To Security Incidents
Multiple Response Strategies To Security IncidentsThis slide depicts the multiple response strategies to security incidents. The purpose of this slide is to help the business ensure suitable responses are deployed to in order to mitigate the threats. It includes recover and restore, notification of affected parties, etc. Introducing our premium set of slides with Multiple Response Strategies To Security Incidents. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Gather Suitable Team, Contain Event, Recover And Restore. So download instantly and tailor it with your information.
-
 Security Incident Icon To Prevent Cyber Attacks
Security Incident Icon To Prevent Cyber AttacksPresenting our set of slides with Security Incident Icon To Prevent Cyber Attacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident, Prevent Cyber Attacks.
-
 Security Incident Response Plan Checklist
Security Incident Response Plan ChecklistThis slide showcases the security incident response plan checklist. The purpose of this slide is to help the business ensure all the tasks are completed in order to prevent security incident. It includes elements such as incident identification, containment and mitigation, etc. Presenting our well structured Security Incident Response Plan Checklist. The topics discussed in this slide are Incident Identification, Incident Categorization, Containment And Mitigation. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Incident Response Plan Checklist Icon
Security Incident Response Plan Checklist IconIntroducing our premium set of slides with Security Incident Response Plan Checklist Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Incident, Response Plan Checklist. So download instantly and tailor it with your information.
-
 Security Incident Response Plan Icon
Security Incident Response Plan IconPresenting our set of slides with Security Incident Response Plan Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident Response, Plan Checklist.
-
 Security Incident Response Plan Lifecycle
Security Incident Response Plan LifecycleThis slide showcases the security incident response plan lifecycle. The purpose of this slide is to help the business deploy suitable incident response plans through the use of following lifecycle. It includes elements such as digital forensics, preparations, etc. Introducing our Security Incident Response Plan Lifecycle set of slides. The topics discussed in these slides are Security Incident, Response Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Solutions To Overcome Security Incident Response Challenges
Solutions To Overcome Security Incident Response ChallengesThis slide showcases the challenges faced during incident response deployment. The purpose of this slide is to overcome these challenges through the use of given solutions. It includes, challenges such as lack of preparedness, limited visibility, etc. Presenting our well structured Solutions To Overcome Security Incident Response Challenges. The topics discussed in this slide are Recovery Processes, Lessons Identified, Digital Forensics. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strategies To Prevent Network Security Incidents
Strategies To Prevent Network Security IncidentsThis slide highlights the strategies to prevent network security incidents. The purpose of this slide is to help the business utilize these strategies in order to prevent future security incidents. It includes IT audits, employee trainings, etc. Introducing our premium set of slides with Strategies To Prevent Network Security Incidents. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Lack Of Preparedness, Insufficient Resources, Limited Visibility. So download instantly and tailor it with your information.
-
 Tools To Manage Data Security Incidents
Tools To Manage Data Security IncidentsThis slide displays the tools to manage data security incidents. The purpose of this slide is to help the business utilize suitable tools to manage and eliminate security incident impact. It includes endpoint security tools, vulnerability scanners, etc. Presenting our set of slides with Tools To Manage Data Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Scanners, Endpoint Security Tools, Incident Response.
-
 Types Of Security Incidents Observed In Company Networks
Types Of Security Incidents Observed In Company NetworksThis slide showcases the types of security incidents observed in company networks. The purpose of this slide is to help understand the multiple types of security incidents in order to easily identify and eliminate them. It includes unauthorized access, insider threat attacks, etc. Introducing our premium set of slides with Types Of Security Incidents Observed In Company Networks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Insider Threat Attacks, Phishing Attacks, Escalation Attacks. So download instantly and tailor it with your information.
-
 Case Study For Cryptocurrency Exchange Security Navigating The Anti Money Laundering Fin SS
Case Study For Cryptocurrency Exchange Security Navigating The Anti Money Laundering Fin SSThe following slide provides the financial institution compliance case study that helps to understand the various challenges and solutions of AML implementation. Key components are aim, challenges, the result achieved, and conclusion. Increase audience engagement and knowledge by dispensing information using Case Study For Cryptocurrency Exchange Security Navigating The Anti Money Laundering Fin SS. This template helps you present information on three stages. You can also present information on Challenges, Solutions Implemented, Result Achieved using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SS
Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SSThis slide highlights the application of digital wallets to enhance the security of e-commerce platforms. Key technologies are tokenization, biometric authentication, and two-factor authentication. Increase audience engagement and knowledge by dispensing information using Enhancing E Commerce Security With Unlocking Digital Wallets All You Need Fin SS. This template helps you present information on three stages. You can also present information on Biometric Authentication, Two-Factor Authentication, Tokenization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SS
Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SSThis slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Introducing Future Of Digital Wallet Security And Safety Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Government Regulations, Biometric Authorization, Decentralized Wallets, using this template. Grab it now to reap its full benefits.
-
 Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SS
Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SSThe following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Introducing Security In IoT Payment For Digital Wallet Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Credentials, Device Authentication, Consumer Authentication, using this template. Grab it now to reap its full benefits.
-
 Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS V
Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS VThis slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Increase audience engagement and knowledge by dispensing information using Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS V. This template helps you present information on one stages. You can also present information on Biometric Technology, Enhancing Online Security, Commercial Banking, Data Is Encrypted using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Fintech And Banking App Checklist For Secure Messaging
Fintech And Banking App Checklist For Secure MessagingThis slide covers checklist for fintech and banking app to build customer trust such as ensuring data privacy, maintain compliance with regulations, etc. Introducing our Fintech And Banking App Checklist For Secure Messaging set of slides. The topics discussed in these slides are Data Privacy, Proactive In Communication, Secured Encrypted Pushes. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Measures In Fintech App Icon
Security Measures In Fintech App IconPresenting our set of slides with Security Measures In Fintech App Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Measures, Fintech App.
-
 Advantages And Disadvantages Of Csirt Cyberse S Cybersecurity Security
Advantages And Disadvantages Of Csirt Cyberse S Cybersecurity SecurityThis slide provides functions of CSIRT in cyber security. The main purpose of this template is highlighting ways of strengthening overall cyber security. This includes rapid incident response, enhance security, etc. Introducing our Advantages And Disadvantages Of Csirt Cyberse S Cybersecurity Security set of slides. The topics discussed in these slides are Rapid Incident Response, Enhanced Security Measure, Regulatory Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Managing Network Media Security
Best Practices For Managing Network Media SecurityThis slide highlights best practices for controlling network media security such as conducting regular firmware, implementing access control, using network segmentation, etc ensures the confidentiality, integrity, and availability of digital assets in a networked environment. Presenting our set of slides with Best Practices For Managing Network Media Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Regular Firmware, Implement Strong Access Control, Use Network Segmentation.
-
 Key Elements Of Network Media Security
Key Elements Of Network Media SecurityThis slide showcases major elements of network media security such as firewalls, encryption, network segmentation etc to safeguard digital communication channels and data integrity through encryption, authentication, and access control measures., Presenting our set of slides with Key Elements Of Network Media Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intrusion Prevention System, Encryption, Network Segmentation.
-
 Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS
Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SSThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Efficient Sales Processes With CRM Add Roles And Enable Security In CRM System CRP DK SS. Use it as a tool for discussion and navigation on Enable Security, Lead Generation, Emails For Contact Management. This template is free to edit as deemed fit for your organization. Therefore download it now.





