Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Breach Prevention Security Breach Events Tracking Dashboard
Data Breach Prevention Security Breach Events Tracking DashboardThis slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks. Present the topic in a bit more detail with this Data Breach Prevention Security Breach Events Tracking Dashboard. Use it as a tool for discussion and navigation on Security Breach Events, Tracking Dashboard, Data Breach Attacks, Graphical Representation Of Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway
Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Increase audience engagement and knowledge by dispensing information using Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway. This template helps you present information on three stages. You can also present information on Deployment, Businesses, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Market Analysis Of Secure Web Gateway Network Security Using Secure Web Gateway
Global Market Analysis Of Secure Web Gateway Network Security Using Secure Web GatewayThis slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. Present the topic in a bit more detail with this Global Market Analysis Of Secure Web Gateway Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Analysis, Overview, Security Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Industry Wise Market Segmentation Of Swg Network Security Using Secure Web Gateway
Industry Wise Market Segmentation Of Swg Network Security Using Secure Web GatewayThis slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. Present the topic in a bit more detail with this Industry Wise Market Segmentation Of Swg Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Segmentation, Application, Considerably. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Web Gateway Performance Tracking Dashboard Network Security Using Secure Web Gateway
Secure Web Gateway Performance Tracking Dashboard Network Security Using Secure Web GatewayThis slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Deliver an outstanding presentation on the topic using this Secure Web Gateway Performance Tracking Dashboard Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Performance, Dashboard, Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Network Security Using Secure Web Gateway
Table Of Contents Network Security Using Secure Web GatewayDeliver an outstanding presentation on the topic using this Table Of Contents Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Working And Architecture, Architecture, Gateway Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway
Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Increase audience engagement and knowledge by dispensing information using Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway. This template helps you present information on five stages. You can also present information on Application Control, Website Content Inspection, Gateway Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dashboard Of Network Security For Identifying Risks
Dashboard Of Network Security For Identifying RisksThis slide showcase dashboard of network security. The main purpose of this slide is for identifying risks that can damage security of network. This includes different types of theft, Malware, authentication etc. Introducing our Dashboard Of Network Security For Identifying Risks set of slides. The topics discussed in these slides are Authentication, Theft Rate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 KPI Dashboard For Tracking Network Security
KPI Dashboard For Tracking Network SecurityThis slide showcase dashboard of security network. The main purpose of this template is to detect threats on time. This includes average no of threats, Devices that caused threats and total no. of threats. Introducing our KPI Dashboard For Tracking Network Security set of slides. The topics discussed in these slides are Average Threats Per Day, Threats Per Month. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistics Interpreting Threat On Network Security
Statistics Interpreting Threat On Network SecurityThis slide showcases weightage of threat to network security. The main purpose of this slide is to show different channels that cause threats to business security. This includes channels such as malware, phishing, bots, etc. Presenting our well structured Statistics Interpreting Threat On Network Security. The topics discussed in this slide are Steals Information, Credit Card Number.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS V
ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS V. Use it as a tool for discussion and navigation on Standard Control Issues, Control Review Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS V
Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS V. Use it as a tool for discussion and navigation on Security Measure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V
Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V. Use it as a tool for discussion and navigation on Issues By Control Type, Standard Control Issues. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V
Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Deliver an outstanding presentation on the topic using this Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V. Dispense information and present a thorough explanation of Survey Goal, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security
Confidential Computing Consortium Confidential Computing Market Driven By Cloud And SecurityThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Present the topic in a bit more detail with this Confidential Computing Consortium Confidential Computing Market Driven By Cloud And Security. Use it as a tool for discussion and navigation on Confidential Computing, Market Driven By Cloud, Security Initiatives, Security Specific Use Cases. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Security Plan To Prevent Cyber
Cyber Attacks Faced By Organization Security Plan To Prevent CyberThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cyber Attacks Faced By Organization Security Plan To Prevent Cyber. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
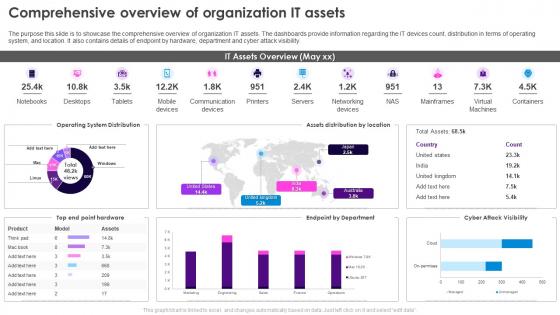 Security Plan To Prevent Cyber Comprehensive Overview Of Organization IT Assets
Security Plan To Prevent Cyber Comprehensive Overview Of Organization IT AssetsThe purpose this slide is to showcase the comprehensive overview of organization IT assets. The dashboards provide information regarding the IT devices count, distribution in terms of operating system, and location. It also contains details of endpoint by hardware, department and cyber attack visibility. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Comprehensive Overview Of Organization IT Assets. Dispense information and present a thorough explanation of Comprehensive Overview, Organization IT Assets, Dashboards, IT Devices Count, Operating System, Cyber Attack Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels
Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents
Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred
Security Plan To Prevent Cyber Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks, Phishing, Malware Attack, Denial Of Service, SQL Injections, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Management Of Cyber Security
Dashboard For Management Of Cyber SecurityThis slide highlights the dashboard for effective cybersecurity management within a firm. This slide aims to help the business executive determine vulnerabilities in the system to deploy effective mechanisms to correct them. It includes elements such as the total number of scans run, vulnerable target enlisting, etc.Introducing our Dashboard For Management Of Cyber Security set of slides. The topics discussed in these slides are High Priority Vulnerabilities, Medium Priority, Low Priority Vulnerabilities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
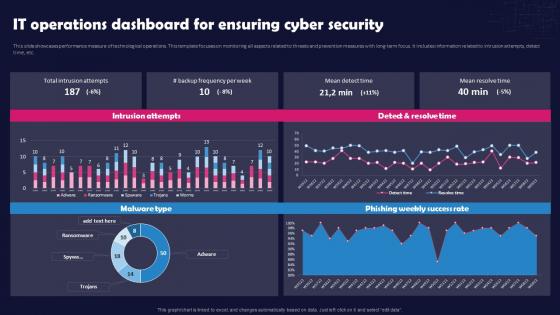 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption
Statistics Of Cloud Data Security Attacks In Organization Cloud Data EncryptionThis slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Dashboard To Measure Security System Performance
KPI Dashboard To Measure Security System PerformanceFollowing slide showcases security system performance measuring KPI dashboard for enhanced office security management. it further covers KPI such as new detection, prevented attacks, total leads, activity detection, etc. Introducing our KPI Dashboard To Measure Security System Performance set of slides. The topics discussed in these slides are Prevented Attacks, Remediated Detections, Current Crowdscore. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology
Confidential Driven By Cloud And Security Initiatives Confidential Computing System TechnologyThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Enterprise, Awareness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Survey Powerpoint Ppt Template Bundles Survey
Security Survey Powerpoint Ppt Template Bundles SurveyIntroduce your topic and host expert discussion sessions with this Security Survey Powerpoint Ppt Template Bundles Survey. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the Six slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard
Cloud Access Security Broker CASB V2 CASB Performance Tracking DashboardThis slide outlines the performance tracking dashboard for CASB deployment. The purpose of this slide is to showcase the status of various applications, IP addresses, users, machines, and web traffic. It also includes cloud discovery open alerts, risk levels, and top entities. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Machines And Web Traffic, Cloud Discover Open Alerts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download
Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics DownloadThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download. Dispense information and present a thorough explanation of Protection Against Threats, Secure Data, Upload Prevention And Encryption, Cloud Solutions With Transparency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration
Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design InspirationIntroducing Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Shadow IT Management Lifecycle, Threat Protection, Data Security, Emerging Cloud Security Risks And Threats, using this template. Grab it now to reap its full benefits.
-
 Kpi Dashboard To Monitor Security Compliance Risk
Kpi Dashboard To Monitor Security Compliance RiskThis slide shows security compliance checklists KPI dashboard to track and analyze risk related to security and to mitigate it efficiently. It further includes details such as top offenders, violation trends etc. Presenting our well structured Kpi Dashboard To Monitor Security Compliance Risk. The topics discussed in this slide are Violation Trends, Selected Period.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secops V2 Effective Implementation Impact On Security Breaches
Secops V2 Effective Implementation Impact On Security BreachesThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this Secops V2 Effective Implementation Impact On Security Breaches. Use it as a tool for discussion and navigation on Network Intrusion, Security Breaches, Sensitive Data Leakage, Configuration Information Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Security Dashboard To Prevent Data Theft
Password Security Dashboard To Prevent Data TheftThis slide highlights a performance dashboard to track data breach password security. The purpose of this slide is to show the key performance metrics that need to be tracked and managed to prevent data theft. It includes password assessment score, security pros, password actions, etc. Introducing our Password Security Dashboard To Prevent Data Theft set of slides. The topics discussed in these slides are Security, Prevent, Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Market Of Secure Access Service Edge Cloud Security Model
Global Market Of Secure Access Service Edge Cloud Security ModelThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this Global Market Of Secure Access Service Edge Cloud Security Model. Dispense information and present a thorough explanation of Global, Market, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model
Secure Access Service Edge Performance Tracking Dashboard Cloud Security ModelThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model. Dispense information and present a thorough explanation of Service, Secure, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Cloud Security Model Ppt Introduction
Table Of Contents For Cloud Security Model Ppt IntroductionIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cloud Security Model Ppt Introduction. This template helps you present information on five stages. You can also present information on Traditional, Network, Problems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Wallets Key Security Comprehensive Guide To Blockchain Wallets And Applications BCT SS
Mobile Wallets Key Security Comprehensive Guide To Blockchain Wallets And Applications BCT SSThis slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. Deliver an outstanding presentation on the topic using this Mobile Wallets Key Security Comprehensive Guide To Blockchain Wallets And Applications BCT SS. Dispense information and present a thorough explanation of Solutions, Risk Involved, Security Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SS
Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SSThe following slide showcases multiple Internet of Things IoT security issues faced by mining companies. The challenges mentioned in slide are IoT devices risk, lack of security update, insider threats, physical security, and distributed attack surfaces. Present the topic in a bit more detail with this Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SS. Use it as a tool for discussion and navigation on Iot Devices Vulnerabilities, Lack Security Update, Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Global Market Of Secure Access Service Edge
Sase Security Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Sase Security Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Service, Technologies, Advancements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Secure Access Service Edge Performance Tracking Dashboard
Sase Security Secure Access Service Edge Performance Tracking DashboardThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Sase Security Secure Access Service Edge Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance, Dashboard, Critical Network Alarms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Sase Security Ppt Show Designs Download
Table Of Contents For Sase Security Ppt Show Designs DownloadIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Sase Security Ppt Show Designs Download. This template helps you present information on five stages. You can also present information on SASE Overview, Traditional Network Security Problems, Importance Of SASE Model using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Market Of Secure Access Service Edge Secure Access Service Edge Sase
Global Market Of Secure Access Service Edge Secure Access Service Edge SaseThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Global Market Of Secure Access Service Edge Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Framework, Requirements, Advancements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Performance Tracking Dashboard Secure Access Service Edge Sase
Secure Performance Tracking Dashboard Secure Access Service Edge SaseThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Performance Tracking Dashboard Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Performance, Dashboard, Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Secure Access Service Edge Sase
Table Of Contents For Secure Access Service Edge SaseDeliver an outstanding presentation on the topic using this Table Of Contents For Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Traditional Network Security Problems, SASE Architecture And Working, Importance Of SASE Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V
Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V Use it as a tool for discussion and navigation on Organisational Capability Framework, Performance Appraisal, Feedback System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V
Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V Use it as a tool for discussion and navigation on Data Sets And Compliance, IT Service Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing V2 Market Driven By Cloud And Security Initiatives
Confidential Computing V2 Market Driven By Cloud And Security InitiativesThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Market Driven By Cloud And Security Initiatives. Dispense information and present a thorough explanation of Confidential Computing Market, Cloud And Security Initiatives, Total Addressable Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Security Dashboard With User Improving IoT Device Cybersecurity IoT SS
IoT Security Dashboard With User Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline key performance indicator KPI metrics dashboard of IoT security. The major metrics mentioned in slide are alert severity, alert breakdown, entity breakdown, user notification, reset password, authentications request, etc. Present the topic in a bit more detail with this IoT Security Dashboard With User Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Security, Notifications, Notification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Market Size Of IoT Security Market Improving IoT Device Cybersecurity IoT SS
Market Size Of IoT Security Market Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase statistical representation of Internet of Things IoT security market across globe. The market size is covered from the period of 2020 2025 which outlines continuous increase in market size. Present the topic in a bit more detail with this Market Size Of IoT Security Market Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Market, Security, Market. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Results Of IoT Security Training Improving IoT Device Cybersecurity IoT SS
Results Of IoT Security Training Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display result of IoT security assessment test. Information covered in this slide is related to total number of participants participated in assessment test, percentage of employees who passed and failed in test, etc. Present the topic in a bit more detail with this Results Of IoT Security Training Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Assessment, Training, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SS
Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight various techniques through which companies can increase Internet of Things IoT cyber security awareness level. The strategies mentioned in slide are getting top level management involved, building robust security awareness plan, etc. Present the topic in a bit more detail with this Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Management, Develop, Guidelines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global 5G Security Market Size Analysis
Global 5G Security Market Size AnalysisThis slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33 persent increase in CAGR because of international funding. Presenting our well structured Global 5G Security Market Size Analysis. The topics discussed in this slide are Security Market, Market Size Increased.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Top 5G Network Security Concerns In Business
Top 5G Network Security Concerns In BusinessThis slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Introducing our Top 5G Network Security Concerns In Business set of slides. The topics discussed in these slides are Scope Management, Network Access. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cryptographic Cloud Security Solution Providers Cloud Cryptography
Cryptographic Cloud Security Solution Providers Cloud CryptographyThis slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Present the topic in a bit more detail with this Cryptographic Cloud Security Solution Providers Cloud Cryptography. Use it as a tool for discussion and navigation on Cryptographic, Solution Providers, Management Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyse Cyber Security With KPI Dashboard Improving Cyber Security Risks Management
Analyse Cyber Security With KPI Dashboard Improving Cyber Security Risks ManagementThe following slide showcases the cyber security vulnerability overview to better plan actions. It includes elements such as domains, subdomains, discovered assets, schedule assets, , issues found etc. Present the topic in a bit more detail with this Analyse Cyber Security With KPI Dashboard Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Entry Point Breakdown, Scheduled Assets, Discovered Assets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V
Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents It covers details regarding issues by control type, risk categories, etc Deliver an outstanding presentation on the topic using this Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V Dispense information and present a thorough explanation of Risk Categories, Control Review Status, Standard Control Issues using the slides given This template can be altered and personalized to fit your needs It is also available for immediate download So grab it now
-
 Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS V
Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use It covers strong password authentication, data backup, network access control, etc Presenting our well structured Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS V The topics discussed in this slide are Authentication Security, Most Businesses, Protect Against This is an instantly available PowerPoint presentation that can be edited conveniently Download it right away and captivate your audience
-
 SASE Network Security Global Market Of Secure Access Service Edge
SASE Network Security Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this SASE Network Security Global Market Of Secure Access Service Edge. Dispense information and present a thorough explanation of Service, Secure, Global using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard SASE Network Security
Secure Access Service Edge Performance Tracking Dashboard SASE Network SecurityThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard SASE Network Security. Dispense information and present a thorough explanation of Service, Performance, Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For SASE Network Security Ppt Guidelines
Table Of Contents For SASE Network Security Ppt GuidelinesIncrease audience engagement and knowledge by dispensing information using Table Of Contents For SASE Network Security Ppt Guidelines. This template helps you present information on five stages. You can also present information on Architecture, Network, Working using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V
Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Increase audience engagement and knowledge by dispensing information using Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V. This template helps you present information on five stages. You can also present information on Digital, Security, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





