Powerpoint Templates and Google slides for Security Policies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Policy Powerpoint Presentation Slides
Cyber Security Policy Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Cyber Security Policy Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of sixty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Cyber Security Policies For Businesses Training Ppt
Cyber Security Policies For Businesses Training PptPresenting Cyber Security Policies for Businesses. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Cyber Security Policy Powerpoint Ppt Template Bundles
Cyber Security Policy Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Cyber Security Policy Powerpoint Ppt Template Bundles Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The Twenty slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Cyber Security Policy Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Must Have Cyber Security Policies Training Ppt
Must Have Cyber Security Policies Training PptPresenting Must Have Cyber Security Policies. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Overview Of Network Security Policy Training Ppt
Overview Of Network Security Policy Training PptPresenting Overview of Network Security Policy. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Security Awareness And Training Policy Training Ppt
Security Awareness And Training Policy Training PptPresenting Security Awareness and Training Policy. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Sample Cyber Security Policy Template Training Ppt
Sample Cyber Security Policy Template Training PptPresenting Sample Cyber Security Policy Template. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Security Officer Profile In Sample Cybersecurity Policy Template Training Ppt
Security Officer Profile In Sample Cybersecurity Policy Template Training PptPresenting Security Officer Profile in Sample Cybersecurity Policy Template. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Information Security Policy In Cybersecurity Training Ppt
Information Security Policy In Cybersecurity Training PptPresenting Information Security Policy in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Compare two options security policy orchestration computing market hybrid infographic
Compare two options security policy orchestration computing market hybrid infographicEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Compare Two Options Security Policy Orchestration Computing Market Hybrid Infographic is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fifteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
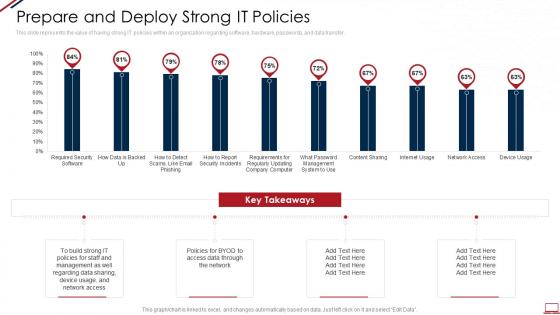
 Data security it prepare and deploy strong it policies ppt slides deck
Data security it prepare and deploy strong it policies ppt slides deckThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Data Security IT Prepare And Deploy Strong IT Policies Ppt Slides Deck. Use it as a tool for discussion and navigation on Build Strong, IT Policies, Required Security Software, Content Sharing, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security prepare and deploy strong it policies
Computer system security prepare and deploy strong it policiesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Computer System Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it implementation of strong password policy
Data security it implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Data Security IT Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Safety security policy workplace ppt powerpoint presentation gallery display cpb
Safety security policy workplace ppt powerpoint presentation gallery display cpbPresenting our Safety Security Policy Workplace Ppt Powerpoint Presentation Gallery Display Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Safety Security Policy Workplace This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Computer system security implementation of strong password policy
Computer system security implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Computer System Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Security Workplace Policy Guide For Employees
Security Workplace Policy Guide For EmployeesIntroducing Security Workplace Policy Guide For Employees to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Internet, Programs, Secure, using this template. Grab it now to reap its full benefits.
-
 Security Introduction To Human Resource Policy
Security Introduction To Human Resource PolicyIntroducing Security Introduction To Human Resource Policy to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security, using this template. Grab it now to reap its full benefits.
-
 Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS
Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SSThe following slide depicts KYC and AML policy checklist to prevent money laundering and ensure customer due diligence. It includes elements such as collect users personal data, verifying details, specifying duration for checking, defining actions for unverified clients, checking taxation laws, etc. Deliver an outstanding presentation on the topic using this Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Develop Checklist, Determine Whether, Verify User Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Methods To Implement Security Policies On Network Security Using Secure Web Gateway
Methods To Implement Security Policies On Network Security Using Secure Web GatewayThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Deliver an outstanding presentation on the topic using this Methods To Implement Security Policies On Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Organizational, Examination, Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Policy Best Practices In Powerpoint And Google Slides Cpb
Security Policy Best Practices In Powerpoint And Google Slides CpbPresenting Security Policy Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Policy Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Corporate Data Security Policy In Powerpoint And Google Slides Cpb
Corporate Data Security Policy In Powerpoint And Google Slides CpbPresenting our Corporate Data Security Policy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Corporate Data Security Policy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information Security Plan Policies Categorization
Information Security Plan Policies CategorizationThis slide covers three major types of information security plan policies to maintain confidentiality, integrity and availability of data. It includes program policies, Issue specific policies and system specific policies. Introducing our premium set of slides with Information Security Plan Policies Categorization. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Program Policies, Issue Specific Policies, System Specific Policies. So download instantly and tailor it with your information.
-
 Cybersecurity Risk Trends For Security Policy Development
Cybersecurity Risk Trends For Security Policy DevelopmentThis slide highlights cybersecurity risk trends for enhancing organization security ensuring digital operations resilience. It includes developments such as attack surface expansion, identify system defense, digital supply chain risk, etc. Presenting our well structured Cybersecurity Risk Trends For Security Policy Development. The topics discussed in this slide are Attack Surface Expansion, Identify System Defense, Digital Supply Chain Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Importance Of 5G Network Security Policies
Importance Of 5G Network Security PoliciesThis slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security, core network security etc. Presenting our set of slides with Importance Of 5G Network Security Policies. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Access Network Security, Core Network Security.
-
 Human Resource Security Policy In Powerpoint And Google Slides Cpb
Human Resource Security Policy In Powerpoint And Google Slides CpbPresenting our Human Resource Security Policy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases Three stages. It is useful to share insightful information on Human Resource Security Policy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Internet Things Security Policy In Powerpoint And Google Slides Cpb
Internet Things Security Policy In Powerpoint And Google Slides CpbPresenting Internet Things Security Policy In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internet Things Security Policy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Deploy Network Layer Firewall For Enforcing Security Policies
Deploy Network Layer Firewall For Enforcing Security PoliciesThis slide focuses on network layer firewall by controlling and monitoring cyber threats and enforcing access policies. It includes aspects such as non web attack, web attack, legitimate traffic, etc. Introducing our Deploy Network Layer Firewall For Enforcing Security Policies set of slides. The topics discussed in these slides are Operation Mode, Transparent Mode, Routed Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Screenshot Security Policy In Powerpoint And Google Slides Cpb
Screenshot Security Policy In Powerpoint And Google Slides CpbPresenting our Screenshot Security Policy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Screenshot Security Policy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Bring Your Own Device Policy Information Security Policy For Employees
Bring Your Own Device Policy Information Security Policy For EmployeesThis slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Increase audience engagement and knowledge by dispensing information using Bring Your Own Device Policy Information Security Policy For Employees. This template helps you present information on two stages. You can also present information on Company Infrastructure, It Infrastructure, Data Processing Activities And Purposes, Discovery Of New Cyber Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Bring Your Own Device Policy Overview Of Network Security Policy For Workers
Bring Your Own Device Policy Overview Of Network Security Policy For WorkersThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Introducing Bring Your Own Device Policy Overview Of Network Security Policy For Workers to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policy, Software And Auditing Processes, Data On Firm Systems, using this template. Grab it now to reap its full benefits.
-
 Bring Your Own Device Policy Security Awareness And Training Policy Overview
Bring Your Own Device Policy Security Awareness And Training Policy OverviewThis slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Increase audience engagement and knowledge by dispensing information using Bring Your Own Device Policy Security Awareness And Training Policy Overview. This template helps you present information on six stages. You can also present information on Security Policy, Policy Protects The Business, Security Awareness, Training Policy Goals using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Policy Management Overview In Firewall Protection
Firewall Network Security Policy Management Overview In Firewall ProtectionThis slide provides an overview of policy management in a firewall protection system. The purpose of this slide is to showcase the multiple guidelines for policy management and various advantages such as reducing mistakes, eliminating conflicts, and the possibility of harmful attacks. Present the topic in a bit more detail with this Firewall Network Security Policy Management Overview In Firewall Protection Use it as a tool for discussion and navigation on SOCKS, IBM Db2, Proxy Server This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Of Security Policies For Privacy Framework
Different Types Of Security Policies For Privacy FrameworkThis slide showcases three different tiers of privacy framework. The main purpose of this template is focus on establishing policies, procedures and governance. This includes operational privacy, audit, management support, etc.Introducing our premium set of slides with Different Types Of Security Policies For Privacy Framework. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Management, Incident Management, Operational Management. So download instantly and tailor it with your information.
-
 Impact Of Cyber Security Policies And Practices Cyber Risk Assessment
Impact Of Cyber Security Policies And Practices Cyber Risk AssessmentThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Introducing Impact Of Cyber Security Policies And Practices Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Guidelines, Management, Privacy Policies using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Security Policies And Practices Creating Cyber Security Awareness
Impact Of Cyber Security Policies And Practices Creating Cyber Security AwarenessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Creating Cyber Security Awareness Dispense information and present a thorough explanation of Lost Revenue, Operational Disruption, Reputational Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
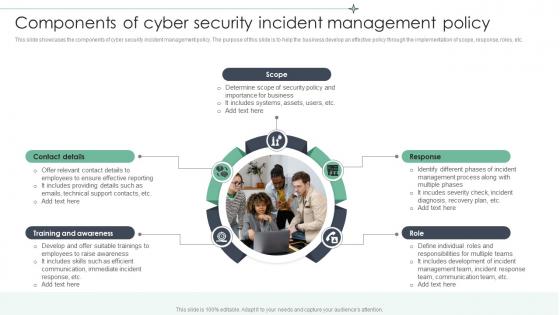 Components Of Cyber Security Incident Management Policy
Components Of Cyber Security Incident Management PolicyThis slide showcases the components of cyber security incident management policy. The purpose of this slide is to help the business develop an effective policy through the implementation of scope, response, roles, etc. Presenting our set of slides with Components Of Cyber Security Incident Management Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Contact Details, Training And Awareness, Includes Systems.
-
 Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Management Policies To Mitigate Internal Data Threats
Security Management Policies To Mitigate Internal Data ThreatsThis slide focuses on the policies for security management helping companies to mitigate internal data threats efficiently. It includes policies for metadata, backup, internal protocol, emails, etc. Introducing our premium set of slides with Security Management Policies To Mitigate Internal Data Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protocol For Visitors, Internet Protocol, Security Audit. So download instantly and tailor it with your information.
-
 Cyber Security Policies For Employee Safety
Cyber Security Policies For Employee SafetyThis slide covers crucial cybersecurity policies designed to ensure employee safety. The purpose of this template is to provide a concise reference for stakeholders. It includes BYOD Policy, Remote Work Policy, E-Commerce Policy, Password Policy, and Email Policy. Presenting our set of slides with Cyber Security Policies For Employee Safety This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on BYOD Policy, Email Policy, Password Policy
-
 Cyber Security Policies For Robust Organizational Network
Cyber Security Policies For Robust Organizational NetworkThis slide covers essential cybersecurity policies. The purpose of this template is to provide a focused understanding of the intrusion prevention policy, host integrity policy, live update policy, and information security policy. Introducing our premium set of slides with Cyber Security Policies For Robust Organizational Network Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Prevention Policy, Host Integrity Policy, Information Security Policy. So download instantly and tailor it with your information.
-
 Cyber Security Policies Safeguarding Network Infrastructure
Cyber Security Policies Safeguarding Network InfrastructureThis slide covers essential security policies. The purpose of this template is to provide a comprehensive overview of essential IT security policies, including Program, Issue-Specific, and System-Specific policies. Presenting our set of slides with Cyber Security Policies Safeguarding Network Infrastructure This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Program Policy, System-Specific Policy
-
 Cyber Security Policy Icon For Data Theft Prevention
Cyber Security Policy Icon For Data Theft PreventionIntroducing our Cyber Security Policy Icon For Data Theft Prevention set of slides. The topics discussed in these slides are Cyber Security Policy, Icon For Data Theft Prevention. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Policy Icon For Securing Digital Assets
Cyber Security Policy Icon For Securing Digital AssetsPresenting our set of slides with Cyber Security Policy Icon For Securing Digital Assets This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Policy Icon, Securing Digital Assets
-
 Global Cyber Security Policy Components
Global Cyber Security Policy ComponentsThis slide covers the key components of a National Cyber Security Strategy NCSS. The purpose of this template is to provide a succinct overview of the main pillars of the NCSS including strengthening the regulatory framework, promoting research and development, etc. Introducing our premium set of slides with Global Cyber Security Policy Components Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Framework, Encourage Open Standards, Assurance Framework. So download instantly and tailor it with your information.
-
 Global Cyber Security Policy Icon
Global Cyber Security Policy IconPresenting our set of slides with Global Cyber Security Policy Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Global Cyber Security Policy Icon
-
 Impact Of Cyber Security Threats On Organisational Policy
Impact Of Cyber Security Threats On Organisational PolicyThis slide covers the negative impacts of prevalent cybersecurity threats. This template aims to highlight two key negative impacts of threats, including DNS Attacks, SQL Injection, Malware, Phishing, and Ransomware. Presenting our set of slides with Impact Of Cyber Security Threats On Organisational Policy This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malware, DNS Attack, SQL Injection
-
 Importance Of Cyber Security Policy For IT Organisation
Importance Of Cyber Security Policy For IT OrganisationThis slide covers the essential importance of a cybersecurity policy for IT organizations. The purpose of this template is to emphasize the role of a cybersecurity policy in safeguarding sensitive data, preventing cyber threats, ensuring regulatory adherence, and maintaining uninterrupted business operations. Introducing our premium set of slides with Importance Of Cyber Security Policy For IT Organisation Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Threat Mitigation, Regulatory Compliance. So download instantly and tailor it with your information.
-
 Key Aspects Of Various Cyber Security Policies
Key Aspects Of Various Cyber Security PoliciesThis slide covers the key elements of various cybersecurity policies. The purpose of this template is to provide a comprehensive overview of specific cybersecurity policies, including Cloud Policy, Information Policy, Physical Policy, Data Retention Policy, and Access Control Policy. Presenting our set of slides with Key Aspects Of Various Cyber Security Policies This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Retention Policy, Cloud Policy, Information Policy
-
 Key Elements Of Cyber Security Policy
Key Elements Of Cyber Security PolicyThis slide covers the key elements of an effective security policy. The purpose of this template is to provide a concise overview of the essential components, emphasizing the need for a clear purpose and objectives, defining scope and applicability, etc. Presenting our set of slides with Key Elements Of Cyber Security Policy This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Clear Objectives, Scope And Applicability
-
 Key Factors For Updating Cyber Security Policy
Key Factors For Updating Cyber Security PolicyThis slide covers key reasons for updating cybersecurity policies. The purpose of this template is to serve as a quick reference for stakeholders, outlining the pivotal circumstances that necessitate policy revisions. It includes regulatory changes, technology upgrades, security incidents, and organizational shifts. Introducing our premium set of slides with Key Factors For Updating Cyber Security Policy Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Changes, Technology Upgrades, Security Incidents. So download instantly and tailor it with your information.
-
 Key Phases Of Cyber Security Policy Framework
Key Phases Of Cyber Security Policy FrameworkThis slide covers key components of a robust cybersecurity framework. The purpose of this template is to provide a comprehensive overview of essential cybersecurity components, including Asset Management, Data Encryption, IT Security Review, Cyber Risk Reporting, Employee Training, and Password Management System. Presenting our set of slides with Key Phases Of Cyber Security Policy Framework This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Framework, Data Encryption
-
 Policy Framework For Cyber Information Security
Policy Framework For Cyber Information SecurityThis slide covers key components of an information security policy. The purpose of this template is to serve as a quick reference guide for each component including purpose, audience, information security objectives, data classification, data operations, and responsibilities of personnel. Presenting our set of slides with Policy Framework For Cyber Information Security This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Purpose, Audience, Information Security Objectives
-
 Process To Create Cyber Security Policy
Process To Create Cyber Security PolicyIntroducing our premium set of slides with Process To Create Cyber Security Policy Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Legal Compliance Review, Stakeholder Collaboration. So download instantly and tailor it with your information.
-
 Requirement For Effective Cyber Security Policy
Requirement For Effective Cyber Security PolicyThis slide covers the imperative reasons for the need of cybersecurity policies. The purpose of this template is to articulate the significance of policies in ensuring legal compliance, data protection, effective risk management, employee training, and incident response. Presenting our set of slides with Requirement For Effective Cyber Security Policy This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Legal Compliance, Data Protection, Risk Management
-
 Steps In Cyber Security Policy Cycle
Steps In Cyber Security Policy CycleThis slide covers the essential steps in a cybersecurity policy. The purpose of this template is to guide the establishment of a robust cybersecurity framework. It includes identifying assets, evaluating threats and risks, implementing safeguards, ongoing monitoring, incident response plan, and the importance of adjustments. Presenting our set of slides with Steps In Cyber Security Policy Cycle This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Assets, Apply Safeguards, Monitor Safeguards
-
 Various Types Of Essential Cyber Security Policy Plans
Various Types Of Essential Cyber Security Policy PlansThis slide covers essential cybersecurity policies for every company. The purpose of this template is to provide a quick reference for stakeholders, detailing the importance of an Acceptable Use Policy AUP, Incident Response Plan IRP, Configuration Management Plan CMP, and ContingencyDisaster Recovery Plan DRP. Introducing our premium set of slides with Various Types Of Essential Cyber Security Policy Plans Ellicudate the Six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Incident Response Plan, Configuration Management, Acceptable Use Policy. So download instantly and tailor it with your information.




