Powerpoint Templates and Google slides for Security Plan
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
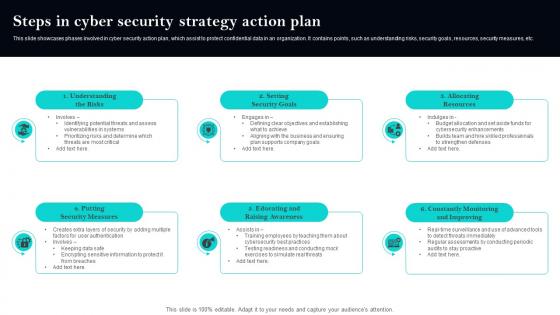 Steps In Cyber Security Strategy Action Plan
Steps In Cyber Security Strategy Action PlanThis slide showcases phases involved in cyber security action plan, which assist to protect confidential data in an organization. It contains points, such as understanding risks, security goals, resources, security measures, etc. Presenting our set of slides with Steps In Cyber Security Strategy Action Plan. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Measures, Raising, Improving.
-
 Strategic Cyber Security Action And Implementation Plan
Strategic Cyber Security Action And Implementation PlanThe slide showcases strategic cyber security action and implementation plan for protecting confidential data in an organization. It contains quarterly timeline with points, such as benchmark, analysis, vision, roadmap, mobilization, etc. Introducing our Strategic Cyber Security Action And Implementation Plan set of slides. The topics discussed in these slides are Analysis, Vision, Implementation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies For Effective Enterprise Cyber Security Action Plan
Strategies For Effective Enterprise Cyber Security Action PlanThis slide showcases strategies that involve in creating an effective enterprise cyber security action plan for better incident responses. It contains points such as assessment, protection, detect and respond to incidents, security and data protection, etc. Presenting our set of slides with Strategies For Effective Enterprise Cyber Security Action Plan. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protection, Assessment, Respond.
-
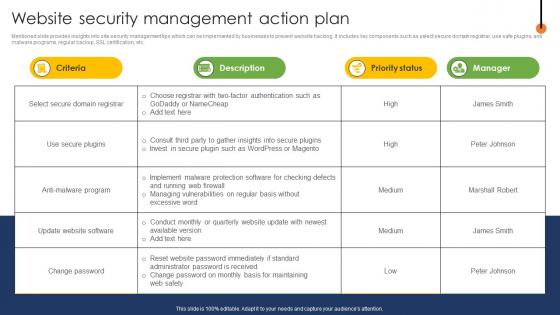
 Website Security Management Action Plan Enhance Business Global Reach By Going Digital
Website Security Management Action Plan Enhance Business Global Reach By Going DigitalMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Deliver an outstanding presentation on the topic using this Website Security Management Action Plan Enhance Business Global Reach By Going Digital. Dispense information and present a thorough explanation of Description, Priority Status, Manager using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Power Plant Cyber Security In Powerpoint And Google Slides Cpb
Power Plant Cyber Security In Powerpoint And Google Slides CpbPresenting Power Plant Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Power Plant Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Web Page Designing Website Security Management Action Plan
Web Page Designing Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Deliver an outstanding presentation on the topic using this Web Page Designing Website Security Management Action Plan Dispense information and present a thorough explanation of Criteria, Description, Priority Status, Manager using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Procedure For Successful Website Security Management Action Plan
Procedure For Successful Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Introducing Procedure For Successful Website Security Management Action Plan to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Themes And Plugin, Improve Loading Time, Implement CSS using this template. Grab it now to reap its full benefits.
-
 Strategic Website Development Website Security Management Action Plan
Strategic Website Development Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Strategic Website Development Website Security Management Action Plan. Use it as a tool for discussion and navigation on Criteria, Description, Priority Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Access Security Control Models Strategy SS V
Strategic Plan To Implement Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Key Access Security Control Models Strategy SS V Dispense information and present a thorough explanation of This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V
Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on IT Governance, Visualization, Resource Management using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V
Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V Dispense information and present a thorough explanation of Communication, Data Management, Marketing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
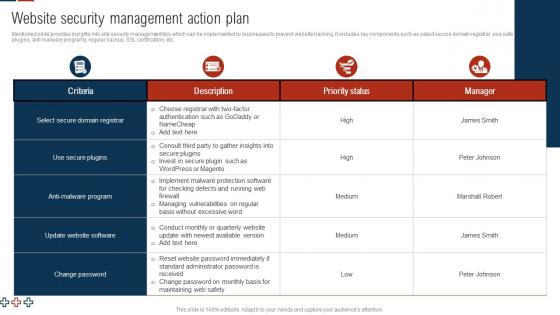 Comprehensive Guide For Digital Website Website Security Management Action Plan
Comprehensive Guide For Digital Website Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Comprehensive Guide For Digital Website Website Security Management Action Plan. Use it as a tool for discussion and navigation on Criteria, Priority Status, Manager. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pricing Plan Of IoT Security Improving IoT Device Cybersecurity IoT SS
Pricing Plan Of IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase pricing plan of Internet of Things IoT security awareness package offered by third party. The pricing plan varies according for total number of employees and includes silver, gold, platinum, and diamond. Present the topic in a bit more detail with this Pricing Plan Of IoT Security Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Security, Packages, Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 30 Days Plan AI In Manufacturing
Managing Cyber Security In Manufacturing 30 Days Plan AI In ManufacturingThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan AI In Manufacturing. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan AI In Manufacturing
Managing Cyber Security In Manufacturing 60 Days Plan AI In ManufacturingThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan AI In Manufacturing. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan AI In Manufacturing
Managing Cyber Security In Manufacturing 90 Days Plan AI In ManufacturingThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 90 Days Plan AI In Manufacturing. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Who Measures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Plan To Manage 5g Security Risks
Mitigation Plan To Manage 5g Security RisksThis slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Presenting our set of slides with Mitigation Plan To Manage 5g Security Risks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Operator Dependent, Unauthorized Data Access.
-
 Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management
Cyber Security Plan Implementation Timeline Improving Cyber Security Risks ManagementThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Perform Simulated, Phishing Exercise, using this template. Grab it now to reap its full benefits.
-
 Plan Useful Data Backup Schedule Improving Cyber Security Risks Management
Plan Useful Data Backup Schedule Improving Cyber Security Risks ManagementThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Present the topic in a bit more detail with this Plan Useful Data Backup Schedule Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Incremental Backup, Plan Useful, Data Backup Schedule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
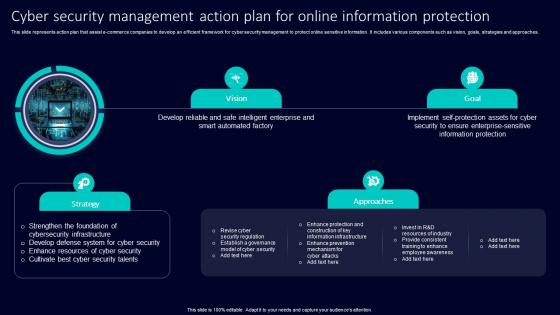 Cyber Security Management Action Plan For Online Information Protection
Cyber Security Management Action Plan For Online Information ProtectionThis slide represents action plan that assist e commerce companies to develop an efficient framework for cyber security management to protect online sensitive information. It includes various components such as vision, goals, strategies and approaches. Presenting our set of slides with Cyber Security Management Action Plan For Online Information Protection. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengthen Foundation Cybersecurity Infrastructure, Develop Defense System Cyber Security, Enhance Resources Cyber Security.
-
 Employee Training Action Plan For Information Security Management
Employee Training Action Plan For Information Security ManagementThis slide represents action plan assisting organizations to provide immense information security management training to employees for data risk assessment. It includes various elements such as courses, modules, hours to complete, and deadlines. Introducing our Employee Training Action Plan For Information Security Management set of slides. The topics discussed in these slides are Cybersecurity Risk Management, Risk Detection Response, Network Security Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Create Network Security Management Plan
Steps To Create Network Security Management PlanThis slide showcases the steps to create network security management plan which helps an organization to provides quick and fast response against cyber attacks. It include details such as create security policy, provide staff trainings, etc. Presenting our set of slides with Steps To Create Network Security Management Plan. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create Security Policy, Provide Staff Trainings, Apply Plan.
-
 Website Security Management Action Plan Strategic Guide For Web Design Company
Website Security Management Action Plan Strategic Guide For Web Design CompanyMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Deliver an outstanding presentation on the topic using this Website Security Management Action Plan Strategic Guide For Web Design Company. Dispense information and present a thorough explanation of Management, Security, Website using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
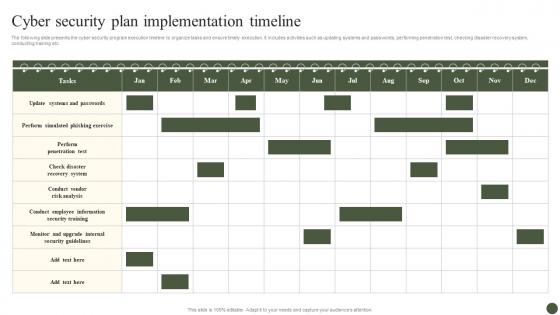 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security
Firewall Network Security 30 60 90 Days Plan To Implement Firewall SecurityThis slide outlines the 30-60-90 days plan to integrate firewalls in a business. The purpose of this slide is to showcase the various steps that should be taken at the interval of every 30 days, such as assessing the current security landscape, defining firewall requirements and selecting solutions, etc. Present the topic in a bit more detail with this Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security Use it as a tool for discussion and navigation on 30 Days, 60 Days, 90 Days This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS
Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SSPresent the topic in a bit more detail with this Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS. Use it as a tool for discussion and navigation on Software Features, Real Time, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Website Security Management Action Plan Website Launch Announcement
Website Security Management Action Plan Website Launch AnnouncementMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Website Security Management Action Plan Website Launch Announcement. Use it as a tool for discussion and navigation on Anti Malware Program, High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wealth Management Secure Retirement Planning With Key Activities Fin SS
Wealth Management Secure Retirement Planning With Key Activities Fin SSThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Increase audience engagement and knowledge by dispensing information using Wealth Management Secure Retirement Planning With Key Activities Fin SS This template helps you present information on Four stages. You can also present information on Lifestyle Assessment, Retirement Income Projection, Savings Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data Breaches
Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data BreachesThis slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data Breaches. This template helps you present information on three stages. You can also present information on Strengthen Access Controls, Conduct Regular Security Audits, Provide Data Security Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Response Plan Implementation Secure Operations
Data Breach Response Plan Implementation Secure OperationsThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Secure Operations. Use it as a tool for discussion and navigation on Secure Physical Areas, Assemble Expert Team, Consult With Legal Counsel, Secure Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Possible Impact Of Data Security Breach
Data Breach Response Plan Possible Impact Of Data Security BreachThis slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Present the topic in a bit more detail with this Data Breach Response Plan Possible Impact Of Data Security Breach. Use it as a tool for discussion and navigation on Customer Breach Notifications, Loss Of Customer Relationships, Operational Disruption, Damaged Brand Reputation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Responsibility Matrix For Secure Operations Phase
Data Breach Response Plan Responsibility Matrix For Secure Operations PhaseThis slide shows the matrix to assign multiple responsibilities to the different teams for the secure operations phase of data breach response plan. The responsibilities include secure physical area, contact search engines, document investigation, etc. Present the topic in a bit more detail with this Data Breach Response Plan Responsibility Matrix For Secure Operations Phase. Use it as a tool for discussion and navigation on Secure Physical Area, Contact Search Engines, Document Investigation, Responsibility Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation
Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops ImplementationThis slide represents the 30-60-90-day plan for DevSecOps implementation. The purpose of this slide is to showcase the approaches that need to be followed as short-term, medium, and long-term goals to implement the DevSecOps. Introducing Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Devsecops Implementation, Vulnerability Scanning, Relevant Security Standards, using this template. Grab it now to reap its full benefits.
-
 Business Continuity And Disaster Recovery Plan For Information Security
Business Continuity And Disaster Recovery Plan For Information SecurityThis slide represents the disaster recovery and business continuity plan that help companies to resolve information security issues effectively. It includes various threats such as injection, broken authentication, etc. Introducing our Business Continuity And Disaster Recovery Plan For Information Security set of slides. The topics discussed in these slides are Injection, Authentication, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Response Plan To Cloning Attacks In Cyber Security
Response Plan To Cloning Attacks In Cyber SecurityThis slide shows an incident response and recovery plan for cloning attacks. The purpose of this slide is to ensure cybersecurity for safeguarding business assets and customers trust. It covers four essential responses such as identification of threat, isolating affected systems, recovery, etc. Presenting our set of slides with name Response Plan To Cloning Attacks In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloning Attack, Malicious Elements, Security Measures.
-
 Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness
Cyber Security Plan Implementation Timeline Creating Cyber Security AwarenessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Malware Attacks, Breaches To Company, More Challenging This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Plan Useful Data Backup Schedule Creating Cyber Security Awareness
Plan Useful Data Backup Schedule Creating Cyber Security AwarenessThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Deliver an outstanding presentation on the topic using this Plan Useful Data Backup Schedule Creating Cyber Security Awareness Dispense information and present a thorough explanation of Security And Privacy, Web Application Security, Infrastructure Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
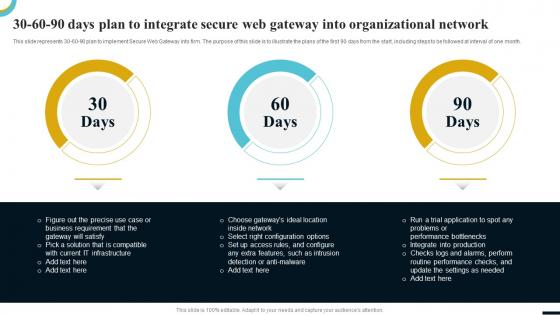 Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web
Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure WebThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Planning
Internet Gateway Security IT Secure Web Gateway Set Up PlanningThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Define Scope Of Project, Identify Network Architecture, Define Security Policy, Select Appropriate Hardware And Software, using this template. Grab it now to reap its full benefits.
-
 Components Of Business Security Incident Response Plans
Components Of Business Security Incident Response PlansThis slide highlights the components of business security incident response plan. The purpose of this slide is to help the business develop effective security incident response plans through the use of components use as incident taxonomy, data classification frameworks, etc. Introducing our premium set of slides with Components Of Business Security Incident Response Plans. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operating Models, Performance Objectives, Incident Taxonomy. So download instantly and tailor it with your information.
-
 Critical Teams During Security Incident Response Planning
Critical Teams During Security Incident Response PlanningThis slide highlights the critical teams required during security incident response planning. The purpose of this slide is to help ensure suitable teams and stakeholders are engaged to manage the security incident. It includes manager for incident response plan, security officer, etc. Introducing our premium set of slides with Critical Teams During Security Incident Response Planning. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Outsourced Cybersecurity, Key Decision, Analyzing Incidents. So download instantly and tailor it with your information.
-
 Examples Of Security Incident Response Plans
Examples Of Security Incident Response PlansThis slide highlights the examples of security incident response plans. The purpose of this slide is to help understand the importance of incident response plans. It includes computer security incident response team, security operations center, etc. Presenting our set of slides with Examples Of Security Incident Response Plans. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Response Team, Computer Security, Computer Emergency.
-
 Five Step Security Incident Response Plan
Five Step Security Incident Response PlanThis slide represents the primary use cases of a software defined wide area network. The use cases include geographical expansion, making better use of WAN bandwidth, improving WAN resilience, and cloud migration. Introducing our premium set of slides with Five Step Security Incident Response Plan. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Build Action Plan, Collate Information, Gather Resources. So download instantly and tailor it with your information.
-
 Implementation Checklist Plan For Security Incident
Implementation Checklist Plan For Security IncidentPresenting our set of slides with Implementation Checklist Plan For Security Incident. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation Checklist Plan, Security Incident.
-
 Security Incident Response Plan Checklist
Security Incident Response Plan ChecklistThis slide showcases the security incident response plan checklist. The purpose of this slide is to help the business ensure all the tasks are completed in order to prevent security incident. It includes elements such as incident identification, containment and mitigation, etc. Presenting our well structured Security Incident Response Plan Checklist. The topics discussed in this slide are Incident Identification, Incident Categorization, Containment And Mitigation. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Incident Response Plan Checklist Icon
Security Incident Response Plan Checklist IconIntroducing our premium set of slides with Security Incident Response Plan Checklist Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Incident, Response Plan Checklist. So download instantly and tailor it with your information.
-
 Security Incident Response Plan Icon
Security Incident Response Plan IconPresenting our set of slides with Security Incident Response Plan Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident Response, Plan Checklist.
-
 Security Incident Response Plan Lifecycle
Security Incident Response Plan LifecycleThis slide showcases the security incident response plan lifecycle. The purpose of this slide is to help the business deploy suitable incident response plans through the use of following lifecycle. It includes elements such as digital forensics, preparations, etc. Introducing our Security Incident Response Plan Lifecycle set of slides. The topics discussed in these slides are Security Incident, Response Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategic Plan To Enhance IoT Security In Manufacturing Boosting Manufacturing Efficiency With IoT
Strategic Plan To Enhance IoT Security In Manufacturing Boosting Manufacturing Efficiency With IoTThe following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Enhance IoT Security In Manufacturing Boosting Manufacturing Efficiency With IoT. This template helps you present information on five stages. You can also present information on Assessment, Planning, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emergency Response Security Plan Icon
Emergency Response Security Plan IconPresenting our well structured Emergency Response Security Plan Icon. The topics discussed in this slide are Emergency Response, Security Plan. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
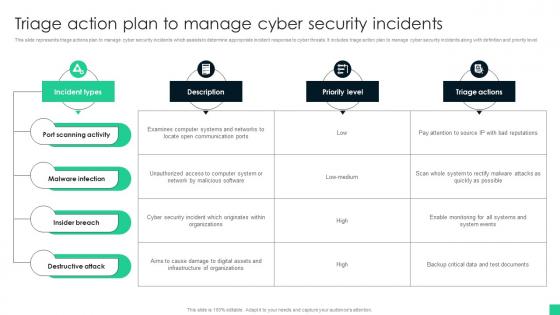 Triage Action Plan To Manage Cyber Security Incidents
Triage Action Plan To Manage Cyber Security IncidentsThis slide represents triage actions plan to manage cyber security incidents which assists to determine appropriate incident response to cyber threats. It includes triage action plan to manage cyber security incidents along with definition and priority level. Introducing our Triage Action Plan To Manage Cyber Security Incidents set of slides. The topics discussed in these slides are Port Scanning Activity, Malware Infection, Insider Breach. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Emergency Response Plan Icon For Security Threats
Emergency Response Plan Icon For Security ThreatsPresenting our set of slides with name Emergency Response Plan Icon For Security Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Emergency Response Plan, Icon For Security Threats.
-
 Data Center Facility Security Plan
Data Center Facility Security PlanThe purpose of this slide is to ensure comprehensive protection against unauthorized access, physical threats, and data breaches including security aspects such as data center layout, environmental controls, etc. Introducing our premium set of slides with name Data Center Facility Security Plan. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Environmental Controls, Data Center Layout, Network Security, Vendor And Contractor Access. So download instantly and tailor it with your information.
-
 Facility Security Recovery Management Plan For Transportation Hubs
Facility Security Recovery Management Plan For Transportation HubsThe purpose of this slide is to develop a comprehensive facility security recovery management plan for transportation hubs to ensure rapid response, resilience, and restoration of operations including aspects such as cargo tracking, vehicle inspection, etc. Presenting our well structured Facility Security Recovery Management Plan For Transportation Hubs. The topics discussed in this slide are Physical Access Control, Vehicle Inspection, Cargo Tracking, Training And Drills. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Food Plant Security Measures To Enhance Facility Safety
Food Plant Security Measures To Enhance Facility SafetyThe purpose of this slide is to implement comprehensive access control systems, surveillance cameras, and employee training to safeguard food plant facilities through fencing, single entrance, security cameras, etc. Presenting our set of slides with name Food Plant Security Measures To Enhance Facility Safety. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Fencing, Single Entrance, Security Cameras, Enhance Facility Safety.





