Powerpoint Templates and Google slides for Security Of Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Table Of Contents Encryption For Data Security Cybersecurity SS
Table Of Contents Encryption For Data Security Cybersecurity SSIntroducing Table Of Contents Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Team For Encryption, Encryption Costs Analysis, Pre Implementation Best Practices, using this template. Grab it now to reap its full benefits.
-
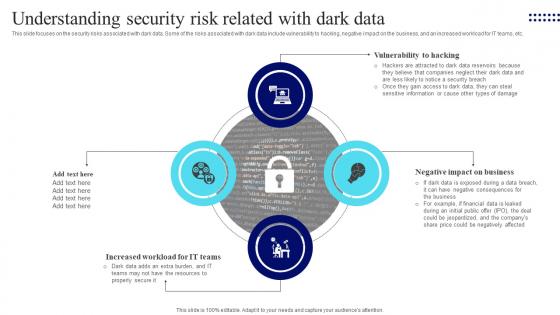 Management Of Redundant Data Understanding Security Risk Related With Dark Data
Management Of Redundant Data Understanding Security Risk Related With Dark DataThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Management Of Redundant Data Understanding Security Risk Related With Dark Data to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Workload For IT Teams, Negative Impact On Business, Vulnerability To Hacking, using this template. Grab it now to reap its full benefits.
-
 Big Data Model Of Security Sharing Based On Blockchain
Big Data Model Of Security Sharing Based On BlockchainThis slide gives an overview of the big data model of security sharing based on blockchain which include citizen, government, school, student, individual, etc. Presenting our set of slides with Big Data Model Of Security Sharing Based On Blockchain. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collect Data, Smart Contract, Query Data.
-
 Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS
Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding focusing on proactive security for successful data loss prevention execution. It will include initiatives such as infiltration, exfiltration, automated protection, etc.Increase audience engagement and knowledge by dispensing information using Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Exhibited Behavior, Objective, Customization, High Risk Events using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction Of Cyber Threat Intelligence For Data Security
Introduction Of Cyber Threat Intelligence For Data SecurityThis slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Introducing Introduction Of Cyber Threat Intelligence For Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Evolving Threats Demand Intelligence, Vital For Security Architecture, Proactively Blocks Attacks, using this template. Grab it now to reap its full benefits.
-
 Generic Database Architecture Of Mobile Security Mobile Security
Generic Database Architecture Of Mobile Security Mobile SecurityThis slide illustrates the key database architecture of mobile security which include mobile worker, internet, mobile server, firewall and database server. Present the topic in a bit more detail with this Generic Database Architecture Of Mobile Security Mobile Security Use it as a tool for discussion and navigation on Logical Device Access, Mobile Functions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 Introduction Of Data Layer In Web Security Solution
Introduction Of Data Layer In Web Security SolutionThis slide discusses the overview of the sixth layer of web security, which is the data layer for enhancing security in the web. Introducing Introduction Of Data Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Data Integrity, Employing Data Encryption Is Crucial, Safeguard Against Unintentional Data Loss Deletion, using this template. Grab it now to reap its full benefits.
-
 Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS
Mobile Device Security For Data Protection Table Of Contents Cybersecurity SSIntroducing Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Target Devices, Target Employees, Encryption Technique Used using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS
Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS This template helps you present information on Five stages. You can also present information on Financial Companies, Million Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods Of Cloud Data Network Security
Methods Of Cloud Data Network SecurityThis slide focuses on cloud data network security techniques including methods, strategic actions, and illustrations. Introducing our Methods Of Cloud Data Network Security set of slides. The topics discussed in these slides are Strategic Actions, Illustrations, Methods. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security software data services example of ppt
Security software data services example of pptThis PowerPoint design can be used for expressing your business strategies and Security Software Data Services related ideas in an attractive manner. The colors shown in star figure can be altered in any PowerPoint software. The text shown in the slide can also be according to your analytics. Downloading this slide will give you access to its full version. The stages in this process are web acceleration, security software, shopping carts, data services.
-
 Model of governance and security of big data diagram ppt presentations
Model of governance and security of big data diagram ppt presentationsPresenting model of governance and security of big data diagram ppt presentations. This is a model of governance and security of big data diagram ppt presentations. This is a three stage process. The stages in this process are confidentiality, integrity, availability, security model.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security
Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Employees, Security, Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security
Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Present the topic in a bit more detail with this Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Awareness, Social Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness
Table Of Contents For Preventing Data Breaches Through Cyber Security AwarenessDeliver an outstanding presentation on the topic using this Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness. Dispense information and present a thorough explanation of Cyber Security Awareness, Online Courses, Automation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
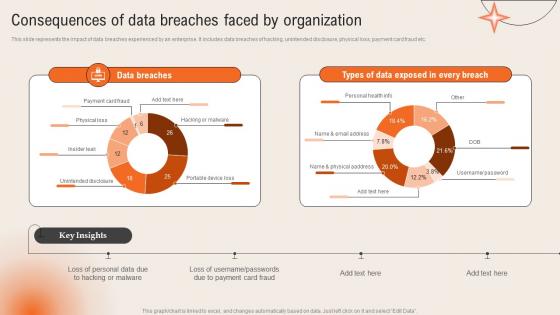 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless security icon of cloud servers to secure data
Wireless security icon of cloud servers to secure dataPresenting our set of slides with Wireless Security Icon Of Cloud Servers To Secure Data. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Wireless Security Icon Of Cloud Servers To Secure Data.
-
 Cia triad of information security in data availability
Cia triad of information security in data availabilityThis slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting our set of slides with Cia Triad Of Information Security In Data Availability. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Confidentiality, Integrity, Availability.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents for data center security data center it ppt powerpoint presentation file show
Table of contents for data center security data center it ppt powerpoint presentation file showPresent the topic in a bit more detail with this Table Of Contents For Data Center Security Data Center It Ppt Powerpoint Presentation File Show. Use it as a tool for discussion and navigation on Data Center Management, Data Center Security, Technologies, Roadmap, Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Planning And Implementation Of Crm Software Securing Our Data With Crm
Planning And Implementation Of Crm Software Securing Our Data With CrmThis slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. Deliver an outstanding presentation on the topic using this Planning And Implementation Of Crm Software Securing Our Data With Crm. Dispense information and present a thorough explanation of User Role Based Security, Profile Based Security, Record Sharing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With Crm Planning And Implementation Of Crm Software
Securing Our Data With Crm Planning And Implementation Of Crm SoftwareThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Present the topic in a bit more detail with this Securing Our Data With Crm Planning And Implementation Of Crm Software. Use it as a tool for discussion and navigation on Securing Our Data With CRM. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Big data it security of information in big data
Big data it security of information in big dataThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Introducing Big Data It Security Of Information In Big Data to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Information, Companies, Professionals, using this template. Grab it now to reap its full benefits.
-
 Distributed computing security of data and networks in distributed computing
Distributed computing security of data and networks in distributed computingThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Present the topic in a bit more detail with this Distributed Computing Security Of Data And Networks In Distributed Computing. Use it as a tool for discussion and navigation on Element, Computing, Protection, System, Network, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Of Data And Networks In Edge Computing Distributed Information Technology
Security Of Data And Networks In Edge Computing Distributed Information TechnologyThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Deliver an outstanding presentation on the topic using this Security Of Data And Networks In Edge Computing Distributed Information Technology. Dispense information and present a thorough explanation of Security Of Data And Networks In Edge Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefit Of Block Chain Technology For Securing Confidential Data Icon
Benefit Of Block Chain Technology For Securing Confidential Data IconPresenting our set of slides with Benefit Of Block Chain Technology For Securing Confidential Data Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Block Chain Technology, Securing Confidential Data.
-
 Cloud Security Threats Loss Of Data Cloud Information Security
Cloud Security Threats Loss Of Data Cloud Information SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Administrations, Protection Frameworks, Technology Advances using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Loss Of Data Cloud Computing Security
Cloud Security Threats Loss Of Data Cloud Computing SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Computing Security. This template helps you present information on four stages. You can also present information on Service Providers, Organization, Backup Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery
Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation galleryThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Increase audience engagement and knowledge by dispensing information using Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery. This template helps you present information on two stages. You can also present information on Challenges, Solution, Data Collections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Approaches Of Cloud Disaster Recovery For Data Security
Approaches Of Cloud Disaster Recovery For Data SecurityThis slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Introducing our premium set of slides with Approaches Of Cloud Disaster Recovery For Data Security. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Backup And Restore, Warm Standby, Pilot Light. So download instantly and tailor it with your information.
-
 Architecture Of Cloud Security Cloud Data Protection
Architecture Of Cloud Security Cloud Data ProtectionThis slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an outstanding presentation on the topic using this Architecture Of Cloud Security Cloud Data Protection. Dispense information and present a thorough explanation of Infrastructure Security, Monitoring, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Data Protection Architecture Of Cloud Security
Cloud Data Protection Architecture Of Cloud SecurityThis slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Architecture Of Cloud Security. This template helps you present information on two stages. You can also present information on Customer Data, Customer Responsibility, Cloud Service using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Data Protection Essential Pillars Of Cloud Security
Cloud Data Protection Essential Pillars Of Cloud SecurityThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security. Introducing Cloud Data Protection Essential Pillars Of Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Process Based Security, Network Security, Identity Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Data Protection
Cloud Security Threats Loss Of Data Cloud Data ProtectionThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Data Protection. This template helps you present information on four stages. You can also present information on Storage Locations, Organization, Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Identity Security Cloud Data Protection
Pillars Of Cloud Security Identity Security Cloud Data ProtectionThis slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Identity Security Cloud Data Protection. This template helps you present information on four stages. You can also present information on Pillars Of Cloud Security Identity Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Network Security Cloud Data Protection
Pillars Of Cloud Security Network Security Cloud Data ProtectionThis slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Introducing Pillars Of Cloud Security Network Security Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Micro Segmentation, Operations, Security, using this template. Grab it now to reap its full benefits.
-
 Pillars Of Cloud Security Process Based Security Cloud Data Protection
Pillars Of Cloud Security Process Based Security Cloud Data ProtectionThis slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Data Protection. This template helps you present information on four stages. You can also present information on Operational Security, Management, Operations using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Visibility And Consistency Cloud Data Protection
Pillars Of Cloud Security Visibility And Consistency Cloud Data ProtectionThis slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Introducing Pillars Of Cloud Security Visibility And Consistency Cloud Data Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Framework, Data Security, Asset Inventory, using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Data Protection
Roadmap Of Cloud Security Implementation Cloud Data ProtectionThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Introducing Roadmap Of Cloud Security Implementation Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services Monitoring, Services Management, Database Security Measures, Network Security, using this template. Grab it now to reap its full benefits.
-
 Segmentation Of Cloud Security Responsibilities Cloud Data Protection
Segmentation Of Cloud Security Responsibilities Cloud Data ProtectionThis slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS. Increase audience engagement and knowledge by dispensing information using Segmentation Of Cloud Security Responsibilities Cloud Data Protection. This template helps you present information on three stages. You can also present information on Segmentation Of Cloud Security Responsibilities using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Types Of Cloud Security Solutions Cloud Data Protection
Types Of Cloud Security Solutions Cloud Data ProtectionThis slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. Increase audience engagement and knowledge by dispensing information using Types Of Cloud Security Solutions Cloud Data Protection. This template helps you present information on three stages. You can also present information on Enterprise Cloud Security, Hybrid Cloud Security, Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 What Are The Benefits Of A Cloud Security System Cloud Data Protection
What Are The Benefits Of A Cloud Security System Cloud Data ProtectionThis slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Introducing What Are The Benefits Of A Cloud Security System Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Efficient Recovery, Efficient Data Security, Business Capacity, using this template. Grab it now to reap its full benefits.
-
 Security Of Information In Big Data Ppt Sample
Security Of Information In Big Data Ppt SampleThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real time, and so on.Increase audience engagement and knowledge by dispensing information using Security Of Information In Big Data Ppt Sample This template helps you present information on one stage. You can also present information on Securing Massive, Data Collections, Comprehending, Preserving using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
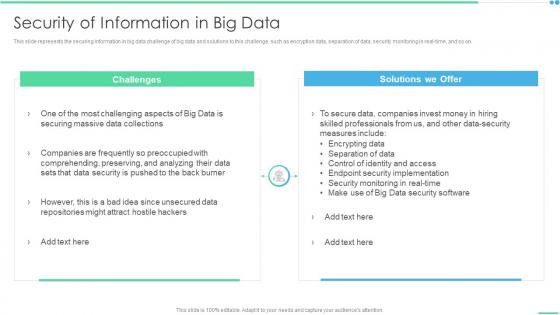 Security Of Information In Big Data Ppt Layouts Layouts
Security Of Information In Big Data Ppt Layouts LayoutsThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Increase audience engagement and knowledge by dispensing information using Security Of Information In Big Data Ppt Layouts Layouts. This template helps you present information on two stages. You can also present information on Challenges, Solutions We Offer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Current Information And Data Security Capabilities Of Firm Information Security Risk Management
Current Information And Data Security Capabilities Of Firm Information Security Risk ManagementThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Introducing Current Information And Data Security Capabilities Of Firm Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Risk Management Functions, Required Standard Rating, Actual Standard Rating, using this template. Grab it now to reap its full benefits.
-
 Icon Of Security Incident Management For Data Protection
Icon Of Security Incident Management For Data ProtectionIntroducing our premium set of slides with Icon Of Security Incident Management For Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Security Incident, Management For Data ProtectionIcon Of Security Incident, Management For Data Protection. So download instantly and tailor it with your information.
-
 Key Components Of Data Security And Privacy Policies
Key Components Of Data Security And Privacy PoliciesThe following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting our set of slides with name Key Components Of Data Security And Privacy Policies. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scan Vulnerabilities, Manage Patches, Response To Incidents.
-
 Four Steps Of Cyber Security Data Breach Risk Process
Four Steps Of Cyber Security Data Breach Risk ProcessThis slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Introducing our premium set of slides with name Four Steps Of Cyber Security Data Breach Risk Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initial Attack, Expanded Attack, Breach Risk Process. So download instantly and tailor it with your information.
-
 Information System Security And Risk Administration Current Information And Data Security Capabilities Of Firm
Information System Security And Risk Administration Current Information And Data Security Capabilities Of FirmThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Information System Security And Risk Administration Current Information And Data Security Capabilities Of Firm. Dispense information and present a thorough explanation of Risk Management Functions, Required Standard Rating, Actual Standard Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Applications Of Data Masking Security Technology
Applications Of Data Masking Security TechnologyThis slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Introducing our premium set of slides with Applications Of Data Masking Security Technology. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Date Aging, Encryption, Scrambling, Nulling Out, Substitution. So download instantly and tailor it with your information.
-
 Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan
Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity PlanThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Identify, Protect, Detect, Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Statistics Of It Security And Data Breach
Key Statistics Of It Security And Data BreachThe following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Presenting our well structured Key Statistics Of It Security And Data Breach. The topics discussed in this slide are Mobile, Data, Breach. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





