Powerpoint Templates and Google slides for Security Monitoring
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deck
Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Security Alarm And Monitoring Systems Company Profile Powerpoint Presentation Slides
Security Alarm And Monitoring Systems Company Profile Powerpoint Presentation SlidesEnthrall your audience with this Security Alarm And Monitoring Systems Company Profile Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising fourty two slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Effective security monitoring plan to eliminate cyber threats and data breaches complete deck
Effective security monitoring plan to eliminate cyber threats and data breaches complete deckEnthrall your audience with this Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Security breach monitoring research communications reporting security database
Security breach monitoring research communications reporting security databaseDeliver a lucid presentation by utilizing this Security Breach Monitoring Research Communications Reporting Security Database. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Monitoring, Research, Communications, Reporting Security, Database. All the twenty four slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Security Lock Internet Safety Desktop Monitor Network Through Financial
Security Lock Internet Safety Desktop Monitor Network Through FinancialEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Security Lock Internet Safety Desktop Monitor Network Through Financial is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fourteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Payment Icon Circle Arrow Dollar Monitor Secure
Payment Icon Circle Arrow Dollar Monitor SecureIt covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Payment Icon Circle Arrow Dollar Monitor Secure with well suited graphics and subject driven content. This deck consists of total of twelve slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below.
-
 Meta Data Organizational Securing Reporting Processing Development Monitoring
Meta Data Organizational Securing Reporting Processing Development MonitoringIf you require a professional template with great design, then this Meta Data Organizational Securing Reporting Processing Development Monitoring is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
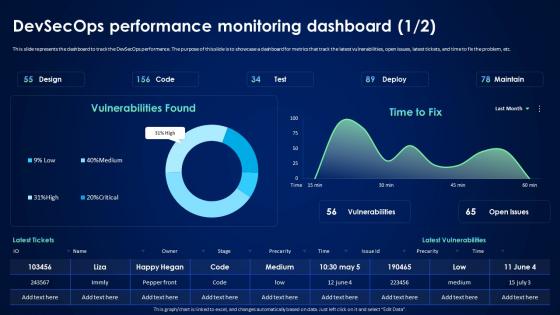 Devsecops Best Practices For Secure Devsecops Performance Monitoring Dashboard
Devsecops Best Practices For Secure Devsecops Performance Monitoring DashboardThis slide represents the dashboard to track the DevSecOps performance. The purpose of this slide is to showcase a dashboard for metrics that track the latest vulnerabilities, open issues, latest tickets, and time to fix the problem, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Devsecops Performance Monitoring Dashboard. Dispense information and present a thorough explanation of Devsecops Performance, Monitoring Dashboard, Track The Latest Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Web Security Upgradation Web Security Monitoring And Tracking Dashboard
Web Security Upgradation Web Security Monitoring And Tracking DashboardThis slide showcases the performance tracking dashboard for web security by including components such as overall progression, critical risk identified, etc. Present the topic in a bit more detail with this Web Security Upgradation Web Security Monitoring And Tracking Dashboard. Use it as a tool for discussion and navigation on Cybersecurity Initiatives, Compliance, Critical Risks Identified. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents
Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi Dashboard To Monitor Security Compliance Risk
Kpi Dashboard To Monitor Security Compliance RiskThis slide shows security compliance checklists KPI dashboard to track and analyze risk related to security and to mitigate it efficiently. It further includes details such as top offenders, violation trends etc. Presenting our well structured Kpi Dashboard To Monitor Security Compliance Risk. The topics discussed in this slide are Violation Trends, Selected Period.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Firewall Network Traffic Monitoring Dashboard
Firewall Network Security Firewall Network Traffic Monitoring DashboardPresent the topic in a bit more detail with this Firewall Network Security Firewall Configuration Challenges And Solutions Use it as a tool for discussion and navigation on Management Essential, Unauthorized Changes, Industry Data Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Performance Monitoring Dashboard
Web Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for web security based on various parameters such as attack types, event status, etc. Presenting our well structured Web Security Performance Monitoring Dashboard. The topics discussed in this slide are Web Security, Performance Monitoring, Dashboard, Event Status. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mobile Security Dashboard To Monitor Operating Systems
Mobile Security Dashboard To Monitor Operating SystemsThis slide illustrates KPI or Dashboard of mobile security to assess different operating systems and includes iOS, android, other and assigned devices, etc. Introducing our Mobile Security Dashboard To Monitor Operating Systems set of slides. The topics discussed in these slides are Ios Devices, Assigned Devices, Firmware Distribution Ios, Android Devices, Other Devices, Firmware Distribution Android. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Security Performance Monitoring Dashboard
Application Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Present the topic in a bit more detail with this Application Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Application Security, Performance, Monitoring Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Testing Tracking And Monitoring Dashboard
Security Testing Tracking And Monitoring DashboardThis slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc. Deliver an outstanding presentation on the topic using this Security Testing Implementation Training Program. Dispense information and present a thorough explanation of Security Testing Tracking, Monitoring Dashboard, Development, Testing, Project Budget using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Endpoint Security Performance Monitoring Dashboard
Endpoint Security Endpoint Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for endpoint security to analyze and monitor security of devices such as laptops. Deliver an outstanding presentation on the topic using this Endpoint Security Endpoint Security Performance Monitoring Dashboard. Dispense information and present a thorough explanation of Endpoint Security Performance, Monitoring Dashboard, Monitor Security Of Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Tokenization Performance Recording And Monitoring Dashboard
Tokenization For Improved Data Security Tokenization Performance Recording And Monitoring DashboardThis slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Tokenization Performance Recording And Monitoring Dashboard. Use it as a tool for discussion and navigation on Tokenization Performance Recording, Monitoring Dashboard, Tracking Dashboard, Key Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Performance Monitoring Dashboard
Application Security Implementation Plan Application Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Application Security, Performance, Monitoring Dashboard, Monitor Security Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hids Dashboard For Cyber Security And Real Time Monitoring
Hids Dashboard For Cyber Security And Real Time MonitoringThis slide represents HIDS dashboard for cyber security which assists to collect, aggregate and analyse security data. It includes key components such as alerts evolution, top tactics, authentication failures, etc Introducing our Hids Dashboard For Cyber Security And Real Time Monitoring set of slides. The topics discussed in these slides are Dashboard, Monitoring, Cyber Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Infrastructure As Code Security Monitoring Dashboard
Infrastructure As Code Security Monitoring DashboardThis slide represents the dashboard of Infrastructure as Code for monitoring and tracking security, the components include compliance status, etc. Presenting our well structured Infrastructure As Code Security Monitoring Dashboard. The topics discussed in this slide are Compliance Severity, Violations By Severity, IAC Resources. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat
Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates cyber incident tracking dashboard. It showcase number of open cases, resolved incidents, open tickets, resolved tickets, number of incidents per incident type and incidents by cyber attack type. Deliver an outstanding presentation on the topic using this Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Monitoring, Dashboard, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Monitor OT Cyber Security Parameters
Dashboard To Monitor OT Cyber Security ParametersThis slide represents dashboard that assist companies to trach and monitor their OT cyber security for enhancing data protection. It includes various OT cyber security indicators such as intrusion detection system alert, prohibited traffic allowed, etc. Introducing our Dashboard To Monitor OT Cyber Security Parameters set of slides. The topics discussed in these slides are Restricted Traffic, Over Time By DestinationThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Security Performance Monitoring And Tracking Dashboard
Application Security Performance Monitoring And Tracking DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Introducing our Application Security Performance Monitoring And Tracking Dashboard set of slides. The topics discussed in these slides are Discovered Apps, Risk LevelsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures
Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security MeasuresThe slide highlights the ways to track and analyze transaction patterns and log in attempts. It provide details about risk scoring, real time monitoring, account monitoring and behavioral analytics.Present the topic in a bit more detail with this Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Account Monitoring, Behavioral Analytics, Real Time Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 A248 Web Security Performance Monitoring Dashboard
A248 Web Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for web security based on various parameters such as open cases, event status, etc. Present the topic in a bit more detail with this A248 Web Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Web Security Performance, Monitoring Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Dashboard For User Activity Monitoring
Network Security Dashboard For User Activity MonitoringThis slide illustrates KPI dashboard of network security to monitor activity including load balancer, network security group, application gateway, protection plan, etc. Presenting our well structured Network Security Dashboard For User Activity Monitoring. The topics discussed in this slide are Load Balancer, Protection Plan, Firewall Policy, Application Gateway. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Security KPI Icon With Monitor
Digital Security KPI Icon With MonitorIntroducing our premium set of slides with Digital Security KPI Icon With Monitor. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitor, Security, Digital. So download instantly and tailor it with your information.
-
 Security Room Surveillance System Monitoring Icon
Security Room Surveillance System Monitoring IconIntroducing our premium set of slides with Security Room Surveillance System Monitoring Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Room Surveillance, System Monitoring Icon. So download instantly and tailor it with your information.
-
 Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS
Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SSThis slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Increase audience engagement and knowledge by dispensing information using Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS. This template helps you present information on three stages. You can also present information on Components, Features, Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Credit Security Monitoring Service In Powerpoint And Google Slides Cpb
Best Credit Security Monitoring Service In Powerpoint And Google Slides CpbPresenting our Best Credit Security Monitoring Service In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Best Credit Security Monitoring Service This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency Transactions
Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency TransactionsThis slide represents the ways we can track the transactions in the crypto market. Some essentials should be kept in mind before monitoring, such as tracking stored data with a public key is accessible, checking the senders and receivers addresses, etc. Introducing Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency Transactions to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cryptocurrency Transaction, Tracking Essentials, Timestamp, Public Blockchains, using this template. Grab it now to reap its full benefits.
-
 Monitoring And Security Logging With Wireless Lan Standard Modes
Monitoring And Security Logging With Wireless Lan Standard ModesThis slide showcases wireless LANs standards and modes for defining communication protocols, frequency bands and data rates. It includes modes such as IEEE 802.11a, 802.11b, 802.11g, 802.11n and 802.11ac. Introducing our premium set of slides with Monitoring And Security Logging With Wireless Lan Standard Modes. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring, Security, Standard Modes . So download instantly and tailor it with your information.
-
 Cloud Security Event Monitoring Icon
Cloud Security Event Monitoring IconIncrease audience engagement and knowledge by dispensing information using Cloud Security Event Monitoring Icon. This template helps you present information on Three stages. You can also present information on Cloud Security Event Monitoring Icon using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improved Framework For Event Monitoring And Security
Improved Framework For Event Monitoring And SecurityThis slide contains the framework for monitoring events. Its objective is to track and evaluate monitoring events. This slide includes capturing data, analysing data, taking action, etc. Introducing Improved Framework For Event Monitoring And Security to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Capture Data, Analyse Data, Take Action, using this template. Grab it now to reap its full benefits.
-
 Security Monitoring Event Monitoring Roadmap
Security Monitoring Event Monitoring RoadmapThis slide contains the roadmap for enhancing security event roadmap. Its objective is to control the amount of users and reduce attacks on the network. This slide includes transaction security, monitoring, limit event, data leakage, etc. Increase audience engagement and knowledge by dispensing information using Security Monitoring Event Monitoring Roadmap. This template helps you present information on Four stages. You can also present information on Digital Twin Construction, Network Construction, Monitoring Centres using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Real Time Cyber Security Threat Monitoring Tools
Real Time Cyber Security Threat Monitoring ToolsThis slide showcases cyber security threat monitoring tool that helps in real-time spectating and identifies malicious behavior on network. It includes elements such as HoneyMap, Norse Map, Digital Attack Map, FireEye, Trend Micro and Akamai. Presenting our well structured Real Time Cyber Security Threat Monitoring Tools. The topics discussed in this slide are Visualization Tools, Real Time, Additional Features. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS
Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SSThis slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. Present the topic in a bit more detail with this Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Vulnerability Scanning, Auditing Reporting, Anomaly Detection . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture Of Cyber Security Monitoring
Architecture Of Cyber Security MonitoringFollowing slide showcases cyber security monitoring architecture for enhanced incident investigation. It further covers monitoring servers, wireless connections, web applications, web server, network monitoring, firewall configuration and allowed or blocked connections etc. Presenting our set of slides with Architecture Of Cyber Security Monitoring This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall Configurations, Network Monitoring, Web Server.
-
 Cyber Security Monitoring Framework In Organization
Cyber Security Monitoring Framework In OrganizationFollowing slide showcases organization framework of cyber security monitoring for improved network protection posture. It further covers identify, protect, detect, respond and recover, etc. Presenting our set of slides with Cyber Security Monitoring Framework In Organization This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Recovery Planning, Responsive Planning, Business Environment.
-
 Monitoring Computer Safety Lock Icon For Cyber Security
Monitoring Computer Safety Lock Icon For Cyber SecurityPresenting our set of slides with Monitoring Computer Safety Lock Icon For Cyber Security This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring Computer Safety, Cyber Security.
-
 Monitoring Cyber Risk Icon For Computer Security
Monitoring Cyber Risk Icon For Computer SecurityIntroducing our premium set of slides with Monitoring Cyber Risk Icon For Computer Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring Cyber Risk, Computer Security. So download instantly and tailor it with your information.
-
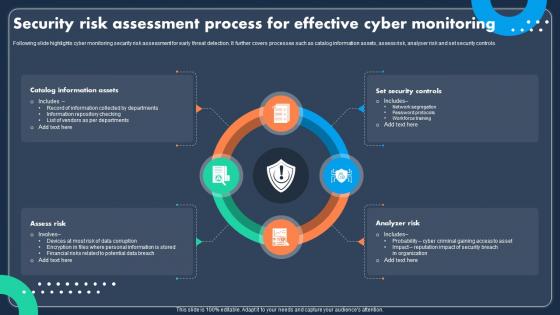 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 File Integrity Monitoring Best Practices For Host And Container Security
File Integrity Monitoring Best Practices For Host And Container SecurityThis slide covers File Integrity Monitoring FIM best practices. The purpose of this template is to provide a structured approach to implementing FIM in host and container environments. It includes preparing asset inventory, detecting drift, and establishing protocols for notification, investigation, and response to security incidents. Presenting our set of slides with File Integrity Monitoring Best Practices For Host And Container Security This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Asset Inventory, Drift Detection, Investigation
-
 Security And Compliance Objectives Of File Integrity Monitoring
Security And Compliance Objectives Of File Integrity MonitoringThis slide covers the Security and Compliance Objectives of File Integrity Monitoring. The purpose of this template is to outline the key objectives that File Integrity Monitoring FIM. It includes unauthorized changes, preventing data breaches, incident response, adherence to regulatory standards, and reducing audit risks and penalties. Presenting our set of slides with Security And Compliance Objectives Of File Integrity Monitoring This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Objectives, Compliance Objectives
-
 Security Monitoring Home Safety Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Monitoring Home Safety Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon features a smoke detector, making it perfect for presentations on fire safety, home security, and emergency preparedness. The icon is designed with vibrant colours and clear graphics to grab the audiences attention and effectively convey the importance of having a smoke detector in every home.
-
 Security Monitoring Home Safety Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Monitoring Home Safety Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon features a smoke detector, perfect for presentations related to fire safety and prevention. The simple design and neutral color make it suitable for a variety of themes and backgrounds. Add this icon to your slides to enhance the visual appeal and convey important information about smoke detectors.
-
 Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS V
Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS VThis slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Introducing Security System Used In Smart Monitoring Patients Health Through IoT Technology IoT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Interworking Devices, Wireless Cameras, Protects Data, using this template. Grab it now to reap its full benefits.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Monitoring And Management Icon
Cyber Security Monitoring And Management IconPresenting our set of slides with Cyber Security Monitoring And Management Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Monitoring And Management Icon.
-
 Cyber Security Crisis Monitoring Solutions
Cyber Security Crisis Monitoring SolutionsThe purpose of this slide is to help cybersecurity professionals in monitoring potential threats and implementing proactive solutions such as detecting security incidents, assessing account activity, monitoring network traffic, etc. Presenting our set of slides with Cyber Security Crisis Monitoring Solutions This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Security Incidents, Cyber Risk Management, Assess Account Activity
-
 Comparative Analysis Of SIEM Cyber Security Monitoring Tools
Comparative Analysis Of SIEM Cyber Security Monitoring ToolsThis slide showcases the comparative analysis of SIEM cyber security tools. Its objective is to detect threats and log analysis. This slide includes log analysis, LogPoint, ExaBeam infusion, ManageEngine and DataDog security. Presenting our well structured Comparative Analysis Of SIEM Cyber Security Monitoring Tools. The topics discussed in this slide are Datadog Security, Logpoint, Manageengine Log. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Maturity Model To Monitor OT Cyber Security Adoption
Maturity Model To Monitor OT Cyber Security AdoptionThis slide represents maturity model that assist companies to monitor and track cyber security adoption for enhancing OT protection. It includes various phases such as secure, defend, contain, monitor and manage phase. Presenting our well structured Maturity Model To Monitor OT Cyber Security Adoption The topics discussed in this slide are Secure, Defend, Contain, MonitorThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Data Security In Remote Healthcare Monitoring
Best Practices For Data Security In Remote Healthcare MonitoringThe slide outlines best practices to safeguard sensitive patient information on remote healthcare monitoring system. It include tips such as using data encryption, implementing strong access control and security testing. Presenting our set of slides with Best Practices For Data Security In Remote Healthcare Monitoring. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Utilize Data Encryption, Security Testing And Patching, Strong Access Controls .
-
 Organizational Physical Security Monitoring Icon
Organizational Physical Security Monitoring IconPresenting our set of slides with Organizational Physical Security Monitoring Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Organizational, Physical Security Monitoring, Icon.
-
 Monitor Security Configuration Management System
Monitor Security Configuration Management SystemThis slide depicts the security configuration management flow. Its aim is to manage the configuration system efficiently. This slide includes publisher, automatic checks, configuration guide, rule implementation, administrator monitoring, etc. Presenting our well structured Monitor Security Configuration Management System. The topics discussed in this slide are Administrator, System Testing, Legend, Implement Rules. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Vulnerability Monitoring For Application Security Icon
Vulnerability Monitoring For Application Security IconIntroducing our Vulnerability Monitoring For Application Security Icon set of slides. The topics discussed in these slides are Vulnerability Monitoring, Application Security IconThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is designed to represent Firewall Audit, a crucial process for ensuring network security. With a bold and eye-catching design, this icon is perfect for presentations and documents related to network security, providing a visual representation of the importance of conducting regular audits to maintain a secure network.
-
 Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual representation for Firewall Audit Ensuring Network Security. It showcases the importance of conducting regular audits to ensure the safety and protection of your network. With its sleek and modern design, this icon will enhance any presentation on network security.




