Powerpoint Templates and Google slides for Security Manager
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Security Crime Prevention Management Flowchart
Data Security Crime Prevention Management FlowchartThis slide depicts the internal data security crime prevention team. Its purpose is to understand duties of the heads to prevent internal crimes. This slide includes data security, technical security, crime prevention, security support, etc. Introducing our Data Security Crime Prevention Management Flowchart set of slides. The topics discussed in these slides are Security Director, Prevention Head, Security Support This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
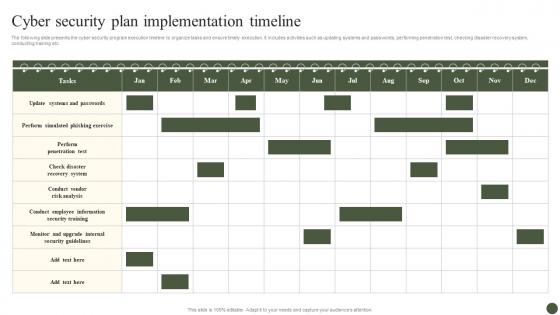 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Risk Management Training Program
Information Security And Risk Management Training ProgramThis slide showcases the successful information security and risk management training outline. It include details such as threats and vulnerabilities, etc. Presenting our well structured Information Security And Risk Management Training Program. The topics discussed in this slide are Training, Vulnerabilities, Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Next Generation Firewalls Vs Unified Threat Management
Firewall Network Security Next Generation Firewalls Vs Unified Threat ManagementThis slide showcases the comparison between Next-Generation Firewalls and United Threat Management. This slide aims to highlight the key differences between NGFWs and UTMs based on definition, market focus, features, scalability, customization, management complexity, deployment, and cost. Present the topic in a bit more detail with this Firewall Network Security Next Generation Firewalls Vs Unified Threat Management Use it as a tool for discussion and navigation on Firewall, Features, Providers This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Policy Management Overview In Firewall Protection
Firewall Network Security Policy Management Overview In Firewall ProtectionThis slide provides an overview of policy management in a firewall protection system. The purpose of this slide is to showcase the multiple guidelines for policy management and various advantages such as reducing mistakes, eliminating conflicts, and the possibility of harmful attacks. Present the topic in a bit more detail with this Firewall Network Security Policy Management Overview In Firewall Protection Use it as a tool for discussion and navigation on SOCKS, IBM Db2, Proxy Server This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organizational Security Risk Analysis And Management
Organizational Security Risk Analysis And ManagementThis slide shows organizational risk analysis by reviewing security threats and audit findings. The purpose of this slide is to help businesses in strengthening their security management system. Analysis is conducting by reviewing security threats, risk factors and management techniques. Presenting our well structured Organizational Security Risk Analysis And Management. The topics discussed in this slide are Security, Factors, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Unified Threat Management UTM Firewall System Overview
Firewall Network Security Unified Threat Management UTM Firewall System OverviewThis slide provides an introduction to the Unified Threat Management firewall system. The purpose of this slide is to showcase the features, benefits, and inspection methods of Unified Threat Management firewall systems, such as flow-based and proxy-based inspection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Understanding Critical Risks Of Firewall Absence This template helps you present information on Three stages. You can also present information on Content Filtering, Faster Security, Flexibility And Adaptability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Criteria To Compare Firewall Management Systems
Firewall Network Security Criteria To Compare Firewall Management SystemsThis slide describes some key features to look for in a firewall management system. The purpose of this slide is to showcase some of the criteria to compare a firewall management system, including ease of use, efficiency, built-in integrations, and scalability. Introducing Firewall Network Security Criteria To Compare Firewall Management Systems to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Ease Of Use, Efficiency, Scalability using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Features Of Distributed Firewall Management System
Firewall Network Security Features Of Distributed Firewall Management SystemThis slide represents the key characteristics of distributed firewall management system. The purpose of this slide is to showcase the different features of distributed firewalls, such as central management systems, security policy distribution, enhanced access control, and host-end execution. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Features Of Distributed Firewall Management System This template helps you present information on Four stages. You can also present information on Access Control, Concurrency Processing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Firewall Security Management Overview And Importance
Firewall Network Security Firewall Security Management Overview And ImportanceThis slide outlines the overview of firewall management in an organization and its significance. The purpose of this slide is to give an overview of firewall management and its importance, such as protecting against data breaches, enhancing network security, and so on. Introducing Firewall Network Security Firewall Security Management Overview And Importance to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Service Control, Direction Control, User Control using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Firewall Security Management Software Tools
Firewall Network Security Firewall Security Management Software ToolsThis slide highlights the top software solutions for firewall security management. The purpose of this slide is to showcase the different software tools for firewall security management, including their features and providers, such as Cisco Systems, Palo Alto Networks, Check Point, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Firewall Security Management Software Tools Dispense information and present a thorough explanation of General Features, Host-Level Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Importance And Benefits Of Distributed Firewall Management System
Firewall Network Security Importance And Benefits Of Distributed Firewall Management SystemThis slide outlines the importance of distributed firewall management system. It also includes the various advantages of distributed firewalls, including security from insider threats, intrusion detection, service exposure, and port scanning. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Importance And Benefits Of Distributed Firewall Management System This template helps you present information on Three stages. You can also present information on Network Address Translation, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Components Of Firewall Management System
Firewall Network Security Key Components Of Firewall Management SystemThis slide talks about the important elements of the firewall management system. The purpose of this slide is to showcase the vital components of a firewall management system, such as a graphical interface, policy control, threat management, device management, third-party integrations, and scalability. Introducing Firewall Network Security Key Components Of Firewall Management System to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service, Artificial Intelligence using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool
Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking ToolThis slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy-to-use user interface, built-in compliance reports, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Solarwinds Security Event, Ethical Hacking Tool, Built In Compliance Reports using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Of Information In Big Data Big Data Analytics And Management
Security Of Information In Big Data Big Data Analytics And ManagementThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Introducing Security Of Information In Big Data Big Data Analytics And Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encrypting Data, Separation Of Data, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SS
Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SSThis slide presents the strategy for involving top management in security initiatives. It includes educate top management, present potential risks, highlight financial and reputational damages, emphasize the need for proactive measures and collaborate with top management. Introducing Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Investment, Cybersecurity, Business Objectives, using this template. Grab it now to reap its full benefits.
-
 Website Security Management Action Plan Website Launch Announcement
Website Security Management Action Plan Website Launch AnnouncementMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Website Security Management Action Plan Website Launch Announcement. Use it as a tool for discussion and navigation on Anti Malware Program, High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
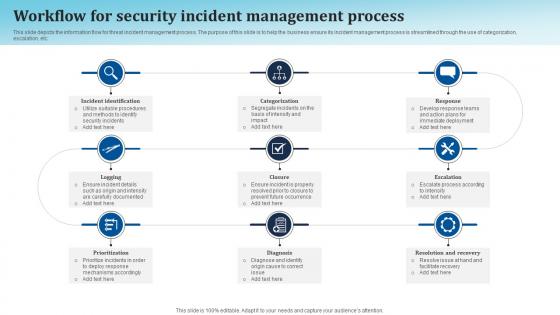 Workflow For Security Incident Management Process
Workflow For Security Incident Management ProcessThis slide depicts the information flow for threat incident management process. The purpose of this slide is to help the business ensure its incident management process is streamlined through the use of categorization, escalation, etc. Presenting our set of slides with Workflow For Security Incident Management Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Categorization, Escalation.
-
 Software Defined Virtual Infrastructure For Cloud Management And Data Security
Software Defined Virtual Infrastructure For Cloud Management And Data SecurityThis slide represents the virtual infrastructure framework assisting companies to enhance data security and maintain business continuity. It includes various key components such as cloud management layer, physical layer, storage, etc. Presenting our well structured Software Defined Virtual Infrastructure For Cloud Management And Data Security. The topics discussed in this slide are Service Management, Business Continuity, Security Compliance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Wealth Management Secure Retirement Planning With Key Activities Fin SS
Wealth Management Secure Retirement Planning With Key Activities Fin SSThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Increase audience engagement and knowledge by dispensing information using Wealth Management Secure Retirement Planning With Key Activities Fin SS This template helps you present information on Four stages. You can also present information on Lifestyle Assessment, Retirement Income Projection, Savings Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V
Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS VIntroducing Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cyber Security, Risk Management Process, using this template. Grab it now to reap its full benefits.
-
 Strategies To Secure Device Network Management
Strategies To Secure Device Network ManagementThis slide consists of security measures for device network management. Its purpose is to use various method to secure device network. This slide includes multi factor authentication, privileged access, credentials. Presenting our set of slides with Strategies To Secure Device Network Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Privileged, Credentials.
-
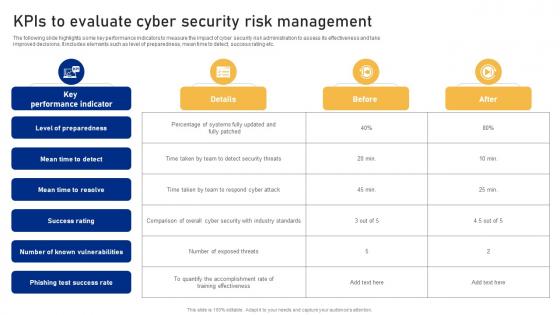 KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment
KPIS To Evaluate Cyber Security Risk Management Cyber Risk AssessmentThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment Use it as a tool for discussion and navigation on Performance Indicator, Success Rating, Risk Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Automated Patch Management Solution Creating Cyber Security Awareness
Implement Automated Patch Management Solution Creating Cyber Security AwarenessThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back-up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Cyber Attack Type, Ransomware Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness
Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security AwarenessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Minimizes Malware Infection, Security Requirements, Internal Risks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Creating Cyber Security Awareness
Leverage Strong And Complex Password Management Creating Cyber Security AwarenessThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Increase audience engagement and knowledge by dispensing information using Leverage Strong And Complex Password Management Creating Cyber Security Awareness This template helps you present information on Four stages. You can also present information on Issue Status Summary, It Costs And Revenue, Security Budget Spent using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness
Reduce Attack Surface With Privilege Access Management Creating Cyber Security AwarenessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Time Consuming Process, Incremental Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
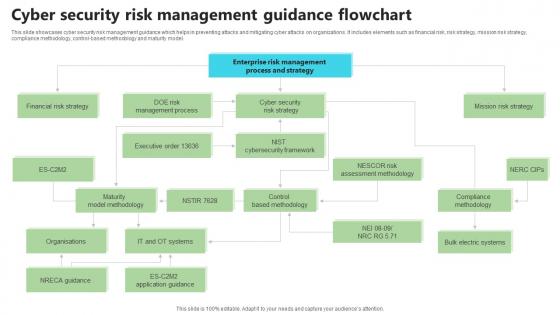 Cyber Security Risk Management Guidance Flowchart
Cyber Security Risk Management Guidance FlowchartThis slide showcases cyber security risk management guidance which helps in preventing attacks and mitigating cyber attacks on organizations. It includes elements such as financial risk, risk strategy, mission risk strategy, compliance methodology, control-based methodology and maturity model. Introducing our Cyber Security Risk Management Guidance Flowchart set of slides. The topics discussed in these slides are Financial Risk Strategy, Compliance Methodology, Mission Risk Strategy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Automated Patch Management To Increase IoT Security And Privacy Safeguarding IoT SS
Automated Patch Management To Increase IoT Security And Privacy Safeguarding IoT SSThis slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results. Introducing Automated Patch Management To Increase IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Deploy Patches, Report Results, Management Process, using this template. Grab it now to reap its full benefits.
-
 IoT Device Management Platforms Comparison IoT Security And Privacy Safeguarding IoT SS
IoT Device Management Platforms Comparison IoT Security And Privacy Safeguarding IoT SSThis slide displays the most popular IoT device management platforms that help to automate connected device monitoring. It includes platforms such as Bytebeam, Cico IoT, Azure IoT Hub, and AWS IoT Core. Deliver an outstanding presentation on the topic using this IoT Device Management Platforms Comparison IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Cloud Integration, Device Connectivity, Pricing Flexibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS
IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SSThis slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Introducing IoT Device Management Process To Enhance Security IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Robust Authentication, Registering Devices, Device Management, using this template. Grab it now to reap its full benefits.
-
 IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SS
IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SSThis slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re testing. Present the topic in a bit more detail with this IoT Incident Response Management Process IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Disconnect Infected, Mitigate Malicious, Infected Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS
Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SSThe following slide depicts details about security tokens to offer benefits to investors. It includes elements such as stocks, bonds, real world assets, improved liquidity, foster innovation, transparency, automated payments, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS This template helps you present information on Four stages. You can also present information on Improved Liquidity, Foster Innovation, Offers Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
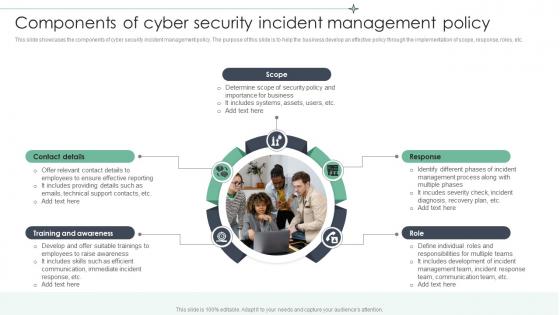 Components Of Cyber Security Incident Management Policy
Components Of Cyber Security Incident Management PolicyThis slide showcases the components of cyber security incident management policy. The purpose of this slide is to help the business develop an effective policy through the implementation of scope, response, roles, etc. Presenting our set of slides with Components Of Cyber Security Incident Management Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Contact Details, Training And Awareness, Includes Systems.
-
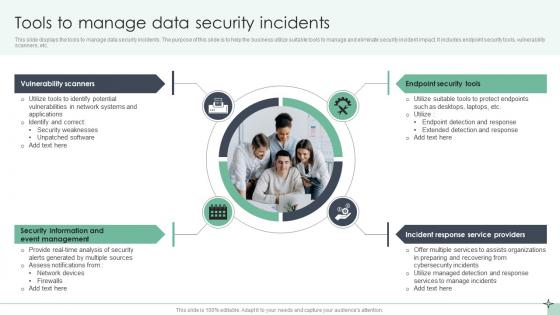 Tools To Manage Data Security Incidents
Tools To Manage Data Security IncidentsThis slide displays the tools to manage data security incidents. The purpose of this slide is to help the business utilize suitable tools to manage and eliminate security incident impact. It includes endpoint security tools, vulnerability scanners, etc. Presenting our set of slides with Tools To Manage Data Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Scanners, Endpoint Security Tools, Incident Response.
-
 Best Practices For Managing Network Media Security
Best Practices For Managing Network Media SecurityThis slide highlights best practices for controlling network media security such as conducting regular firmware, implementing access control, using network segmentation, etc ensures the confidentiality, integrity, and availability of digital assets in a networked environment. Presenting our set of slides with Best Practices For Managing Network Media Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Regular Firmware, Implement Strong Access Control, Use Network Segmentation.
-
 Best Practices For Effective Server Security Management
Best Practices For Effective Server Security ManagementFollowing slide highlights server security management best practices, also including elements such as server management, physical security, update software, etc. Introducing our Best Practices For Effective Server Security Management set of slides. The topics discussed in these slides are Server Management, Physical Security, Update Software. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 It Infrastructure Management To Enhance Server Security
It Infrastructure Management To Enhance Server SecurityFollowing slide highlights enhancing server security with IT infrastructure management, also including server support, assistance of incidents, handling of issues, configuration oversight, etc. Introducing our premium set of slides with It Infrastructure Management To Enhance Server Security. Ellicudate the fourstages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Supervised Network Functions, Storage Management Solutions, Management Of Change. So download instantly and tailor it with your information.
-
 Category Of Threads Managed By Triage Cyber Security
Category Of Threads Managed By Triage Cyber SecurityThis slide represents category of threats managed by triage cyber security which assists to identify and prioritize response to cyber threats. It includes category of threats managed by triage cyber security which includes low, medium and high priority Introducing our premium set of slides with name Category Of Threads Managed By Triage Cyber Security Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Low Priority, Medium Priority, High Priority . So download instantly and tailor it with your information.
-
 Managing Cyber Incidents With Triage Security
Managing Cyber Incidents With Triage SecurityThis slide represents management of cyber incidents with triage cyber security which assists to focus on threats encountered on regular basis. It includes managing cyber incidents with triage security such as determine incident technique, etc Presenting our set of slides with name Managing Cyber Incidents With Triage Security This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Incident Technique, Identify Affected Areas, Measure Attack Density
-
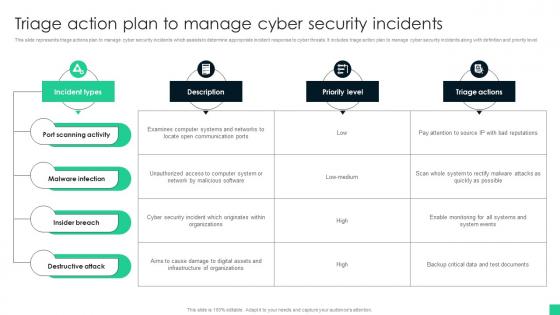 Triage Action Plan To Manage Cyber Security Incidents
Triage Action Plan To Manage Cyber Security IncidentsThis slide represents triage actions plan to manage cyber security incidents which assists to determine appropriate incident response to cyber threats. It includes triage action plan to manage cyber security incidents along with definition and priority level. Introducing our Triage Action Plan To Manage Cyber Security Incidents set of slides. The topics discussed in these slides are Port Scanning Activity, Malware Infection, Insider Breach. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Emerging Security Trends In Facility Management
Emerging Security Trends In Facility ManagementThe purpose of this slide is to to enhance overall security measures and streamline operational processes inclding trends such as IoT and remote monitoring, drone technologies, etc. Presenting our set of slides with name Emerging Security Trends In Facility Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Drone Technologies, Emerging Security Trends, Facility Management, Streamline Operational Processes.
-
 Facility Security Recovery Management Plan For Transportation Hubs
Facility Security Recovery Management Plan For Transportation HubsThe purpose of this slide is to develop a comprehensive facility security recovery management plan for transportation hubs to ensure rapid response, resilience, and restoration of operations including aspects such as cargo tracking, vehicle inspection, etc. Presenting our well structured Facility Security Recovery Management Plan For Transportation Hubs. The topics discussed in this slide are Physical Access Control, Vehicle Inspection, Cargo Tracking, Training And Drills. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 EDR Work Flowchart For Managing Security Incidents
EDR Work Flowchart For Managing Security IncidentsThis slide highlights EDR working flowchart and includes endpoints, database, restoration, IT analysts, and attackers. Introducing our EDR Work Flowchart For Managing Security Incidents set of slides. The topics discussed in these slides are Realtime Endpoint Behavior, Restoration, Behavioral Data, Managing Security Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats
Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability Assessment, Request Cancelled, Asset Inventory This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats
Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Password Test, Password Encryption, Multi Factor Authentication using this template. Grab it now to reap its full benefits.





