Powerpoint Templates and Google slides for Security Management Technology
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enterprise Risk Management And Information Technology Security Complete Deck
Enterprise Risk Management And Information Technology Security Complete DeckDeliver an informational PPT on various topics by using this Enterprise Risk Management And Information Technology Security Complete Deck. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty two slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Risk Management Maturity Model Information Security Data Technology Culture
Risk Management Maturity Model Information Security Data Technology CultureDeliver a credible and compelling presentation by deploying this Risk Management Maturity Model Information Security Data Technology Culture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty eight slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Risk Management Maturity Model Information Security Data Technology Culture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Technology Security Process Framework Assessment Management Awareness
Technology Security Process Framework Assessment Management AwarenessThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Industrial security management evaluation technology structure
Industrial security management evaluation technology structureThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Industrial Security Management Evaluation Technology Structure and has templates with professional background images and relevant content. This deck consists of total of eleven slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Technological Trends Used For Enhancing Information Security Management
Technological Trends Used For Enhancing Information Security ManagementThis slide represents various technologies that help organizations enhance information security management and reduce data loss incidents. It includes strategies such as user behavior analytics, cloud access security brokers, etc. Presenting our well structured Technological Trends Used For Enhancing Information Security Management. The topics discussed in this slide are Security Testing Devops, User Behavior Analytics, Cloud Access Security Brokers. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of Network Security Management Tools
Comparative Analysis Of Network Security Management ToolsThis slide showcases the comparative analysis of network security management tools which helps an organization to carefully choose the best software to reduce risks. It include details such as ratings, real time data analysis, integrations, etc. Introducing our Comparative Analysis Of Network Security Management Tools set of slides. The topics discussed in these slides are Ratings, Integrations, Risk Score. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Management Tools Facilitating Structure
Network Security Management Tools Facilitating StructureThis slide showcases the network security management tools facilitating its structure which helps an organization to introduce comprehensive, updated policies. It include details such as deployment and implementation, team effectiveness, etc. Presenting our set of slides with Network Security Management Tools Facilitating Structure. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment Implementation, Team Effectiveness, Visibility Reporting.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Firewall Security Management Software Tools
Firewall Network Security Firewall Security Management Software ToolsThis slide highlights the top software solutions for firewall security management. The purpose of this slide is to showcase the different software tools for firewall security management, including their features and providers, such as Cisco Systems, Palo Alto Networks, Check Point, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Firewall Security Management Software Tools Dispense information and present a thorough explanation of General Features, Host-Level Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Containerization Technology Container Security Essentials To Manage Risks
Containerization Technology Container Security Essentials To Manage RisksThis slide represents the various important factors of container security to manage environmental risks. The purpose of this slide is to outline the essentials of container security to manage risks, such as configuration, automation, container security solutions, and cloud and network security. Present the topic in a bit more detail with this Containerization Technology Container Security Essentials To Manage Risks. Use it as a tool for discussion and navigation on Dashboard To Retrieve Ongoing, Time Series Data Metrics, Containers Operating,Container Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment For Data Security Management Tools
Comparative Assessment For Data Security Management ToolsThis slide represents the comparative analysis assisting businesses to choose correct tools to enhance data security management. It includes various tools such as oracle data safe, satori data security platform, etc. Introducing our Comparative Assessment For Data Security Management Tools set of slides. The topics discussed in these slides are Oracle Data Safe, Data Security Platform, Manager For Databases. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Leveraging Technologies To Enhance Data Security Management
Leveraging Technologies To Enhance Data Security ManagementThis slide represents the multiple technologies that assist companies to upgrade and enhance their data security management from threats. It includes technologies such as encryption, data masking, access control, data loss prevention, etc. Introducing our Leveraging Technologies To Enhance Data Security Management set of slides. The topics discussed in these slides are Data Loss Prevention, Access Control, Data Masking. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies And Tools To Enhance Big Data Security Management
Strategies And Tools To Enhance Big Data Security ManagementThis slide showcases the strategies and tools helping companies to effectively manage and monitor big data security from cyber threats. It includes strategies such as cloud security monitoring, centralized key management, incident investigation, etc. Introducing our Strategies And Tools To Enhance Big Data Security Management set of slides. The topics discussed in these slides are Cloud Security Monitoring, Centralized Key Management, Network Traffic Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Advanced Technologies In Automotive Sector For Cyber Security Management
Advanced Technologies In Automotive Sector For Cyber Security ManagementFollowing slide exhibits embedded advanced software and tools used by automotive manufacturer for securing embedded systems against cyber-attacks. It includes gateways, body electronics, dashboard, connected car, hybrid electric vehicle, powertrain and chassis, etc. Presenting our set of slides with Advanced Technologies In Automotive Sector For Cyber Security Management. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Advanced Driver Assistance System, Hybrid Electric Vehicle, Connected Car.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Security Configuration Management Tools
Effective Security Configuration Management ToolsThis slide includes various tools for managing security configuration in the organisation. Its objective is to use the best available tool which is feature rich. This slide showcases tool such as solar winds, auvik, Microsoft intune, etc. Presenting our well structured Effective Security Configuration Management Tools. The topics discussed in this slide are Software, Endpoint Central Manage Engine, Network Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 Technological assessment of managing critical threat vulnerabilities and security threats
Technological assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Technological Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Industry Standard, Firms Standard, Customer Satisfaction Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technological assessment of firm current management corporate security management
Technological assessment of firm current management corporate security managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Management Corporate Security Management. Dispense information and present a thorough explanation of Incidents Handling Rate, Client Onboarding, Service Failure Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
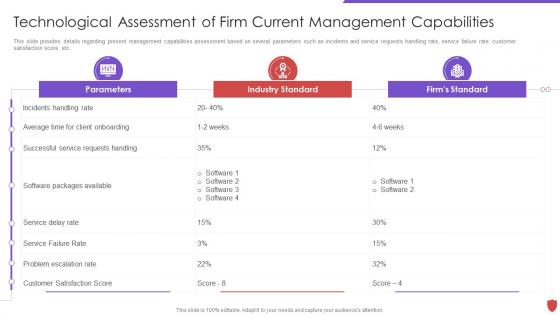 Technological assessment of firm current capabilities cyber security risk management
Technological assessment of firm current capabilities cyber security risk managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Capabilities Cyber Security Risk Management. Dispense information and present a thorough explanation of Parameters, Industry Standard, Firms Standard, Service Delay Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Managing Information Technology Security 90 Days Plan
Information Technology Security Managing Information Technology Security 90 Days PlanThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Information Technology Security Managing Information Technology Security 90 Days Plan. Dispense information and present a thorough explanation of Managing, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing Information Technology Security 30 Days Plan Information Technology Security
Managing Information Technology Security 30 Days Plan Information Technology SecurityThis slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Present the topic in a bit more detail with this Managing Information Technology Security 30 Days Plan Information Technology Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Enterprise Risk Management And Information Technology Security
Agenda Enterprise Risk Management And Information Technology SecurityIntroducing Agenda Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, IT Networks, IT Risk Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management And Information Technology Security Table Of Contents
Enterprise Risk Management And Information Technology Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Enterprise Risk Management And Information Technology Security Table Of Contents. This template helps you present information on one stages. You can also present information on Security Criteria, Control Measures, IT System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enterprise Risk Management And Information Technology Security
Icons Slide For Enterprise Risk Management And Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Enterprise Risk Management And Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Enterprise Risk Management And Information Technology Security
Table Of Contents For Enterprise Risk Management And Information Technology SecurityIntroducing Table Of Contents For Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with eleven stages, this template is a great option to educate and entice your audience. Dispence information on IT Risks, Threat Evaluation, IT Risk Management, Cost Estimation, using this template. Grab it now to reap its full benefits.
-
 IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems
IT Security Residual Risk Matrix With Risk Management Guide For Information Technology SystemsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Database Access, Evaluation Question, Response Action using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Project Management Timeline With Security And Technology
Project Management Timeline With Security And TechnologyThis slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Presenting our well structured Project Management Timeline With Security And Technology. The topics discussed in this slide are Security, Technology, People. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Icon In Information Technology
Cyber Security Risk Management Icon In Information TechnologyPresent the topic in a bit more detail with this Cyber Security Risk Management Icon In Information Technology. Use it as a tool for discussion and navigation on Cyber Security, Risk Management, Icon In Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security And Risk Management With Capabilities
Information Technology Security And Risk Management With CapabilitiesThis slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Deliver an outstanding presentation on the topic using this Information Technology Security And Risk Management With Capabilities. Dispense information and present a thorough explanation of Security Policy Compliance, Compliance, Enterprise Security Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Model For Information Technology Security Risk Management
Model For Information Technology Security Risk ManagementThis slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Introducing Model For Information Technology Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying, Protecting, Detecting, using this template. Grab it now to reap its full benefits.
-
 Risk Management Matrix For Information Technology Security
Risk Management Matrix For Information Technology SecurityThis slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Present the topic in a bit more detail with this Risk Management Matrix For Information Technology Security. Use it as a tool for discussion and navigation on Corporate Workflow, Risks, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Methodology In Information Technology Security
Risk Management Methodology In Information Technology SecurityThis slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Deliver an outstanding presentation on the topic using this Risk Management Methodology In Information Technology Security. Dispense information and present a thorough explanation of Assessment, Mitigation, Continual Evaluation Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
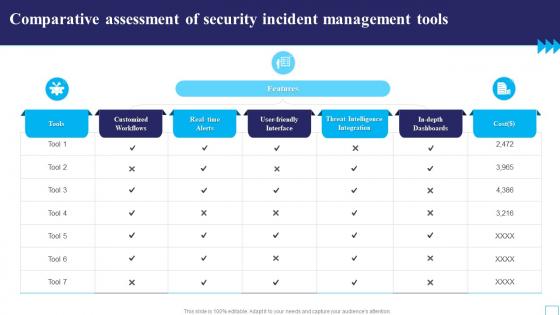 Comparative Assessment Of Security Incident Management Tools
Comparative Assessment Of Security Incident Management ToolsPresenting our well structured Comparative Assessment Of Security Incident Management Tools. The topics discussed in this slide are Customized Workflows, User Friendly Interface, Threat Intelligence Integration. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better Logistics
IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better LogisticsThe following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Present the topic in a bit more detail with this IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better Logistics. Use it as a tool for discussion and navigation on Multiple Positioning, Multiple Alarm, Behavior Alarm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Management Technology Framework
Cyber Security Management Technology FrameworkThis slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Introducing our premium set of slides with Cyber Security Management Technology Framework. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protect, Identify, Detect, Respond, Recover. So download instantly and tailor it with your information.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V
Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Present the topic in a bit more detail with this Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Assessment, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information technology security risk management ppt powerpoint presentation portfolio cpb
Information technology security risk management ppt powerpoint presentation portfolio cpbPresenting this set of slides with name Information Technology Security Risk Management Ppt Powerpoint Presentation Portfolio Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Information Technology Security Risk Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security event management tools ppt powerpoint presentation file background images cpb
Security event management tools ppt powerpoint presentation file background images cpbPresenting this set of slides with name Security Event Management Tools Ppt Powerpoint Presentation File Background Images Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Security Event Management Tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Operational technology security network framework with change management
Operational technology security network framework with change managementPresenting this set of slides with name Operational Technology Security Network Framework With Change Management. This is a four stage process. The stages in this process are Change Management, E2EE Encryption, Threat Forensics, Secure Backup Disaster Recovery, Real Time Incident Reporting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security incident management tools ppt powerpoint presentation icon background image cpb
Security incident management tools ppt powerpoint presentation icon background image cpbPresenting this set of slides with name Security Incident Management Tools Ppt Powerpoint Presentation Icon Background Image Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Security Incident Management Tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security risk management tools ppt powerpoint presentation infographics icon cpb
Security risk management tools ppt powerpoint presentation infographics icon cpbPresenting this set of slides with name Security Risk Management Tools Ppt Powerpoint Presentation Infographics Icon Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Security Risk Management Tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Five years security technology roadmap for supply chain management
Five years security technology roadmap for supply chain managementPresenting Five Years Security Technology Roadmap For Supply Chain Management PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Half yearly security technology roadmap for supply chain management
Half yearly security technology roadmap for supply chain managementPresenting Half Yearly Security Technology Roadmap For Supply Chain Management PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Quarterly security technology roadmap for supply chain management
Quarterly security technology roadmap for supply chain managementPresenting Quarterly Security Technology Roadmap For Supply Chain Management PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Six months security technology roadmap for supply chain management
Six months security technology roadmap for supply chain managementPresenting Six Months Security Technology Roadmap For Supply Chain Management PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Three months security technology roadmap for supply chain management
Three months security technology roadmap for supply chain managementPresenting Three Months Security Technology Roadmap For Supply Chain Management PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Major data security technologies used for risk management
Major data security technologies used for risk managementIntroducing our premium set of slides with Major Data Security Technologies Used For Risk Management. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Major Data, Security Technologies, Used Risk Management. So download instantly and tailor it with your information.
-
 Enhanced security event management various technologies for effective secops process ppt gallery
Enhanced security event management various technologies for effective secops process ppt galleryThis slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Introducing Enhanced Security Event Management Various Technologies For Effective Secops Process Ppt Gallery to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Basic Tools, Advanced Tools, using this template. Grab it now to reap its full benefits.
-
 Information technology dashboard to manage and monitor security vulnerabilities
Information technology dashboard to manage and monitor security vulnerabilitiesPresenting our well structured Information Technology Dashboard To Manage And Monitor Security Vulnerabilities. The topics discussed in this slide are Information Technology Dashboard To Manage And Monitor Security Vulnerabilities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data management security tools with major segments
Data management security tools with major segmentsThis slide showcase data management security tools with major segments. It includes major outcomes such as-privacy design and development, beardless identity administration etc. Presenting our well-structured Data Management Security Tools With Major Segments. The topics discussed in this slide are Security Segment, Expected Enterprise Outcomes, Required Security Controls. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.



