Powerpoint Templates and Google slides for Security Management Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Securing Systems With Identity And Access Management Powerpoint Presentation Slides
Securing Systems With Identity And Access Management Powerpoint Presentation SlidesWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Securing Systems With Identity And Access Management Powerpoint Presentation Slides deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Budget For Identity And Access Management Training Securing Systems With Identity
Budget For Identity And Access Management Training Securing Systems With IdentityThis slide showcases the breakdown cost for the IAM installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training Securing Systems With Identity Use it as a tool for discussion and navigation on Components, Training Cost Distribution This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity
Identity And Access Management Insights Reporting Dashboard Securing Systems With IdentityThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity Dispense information and present a thorough explanation of Failed Task Results, Syslog Errors, Certifications Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Us Identity And Access Management Market Size Securing Systems With Identity
Us Identity And Access Management Market Size Securing Systems With IdentityThis slide depicts the US IAM market size in global market. The purpose of this slide is to highlight the US market size of the IAM process in terms of revenue generation and compound annual growth rate. Deliver an outstanding presentation on the topic using this Us Identity And Access Management Market Size Securing Systems With Identity Dispense information and present a thorough explanation of Provisioning Access, Compromising Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security managing computer security 90 days plan
Computer system security managing computer security 90 days planThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Computer System Security Managing Computer Security 90 Days Plan. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security managing computer security 60 days plan
Computer system security managing computer security 60 days planThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Computer System Security Managing Computer Security 60 Days Plan. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security strategies to manage cyber risks
Computer system security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Computer System Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Vigilant, Resilient, Implementation, Awareness, using this template. Grab it now to reap its full benefits.
-
 Managing computer security 30 days plan computer system security
Managing computer security 30 days plan computer system securityPresent the topic in a bit more detail with this Managing Computer Security 30 Days Plan Computer System Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ERP Security Management System For Healthcare
ERP Security Management System For HealthcareThis slide showcases the management ERP security system for healthcare industry. Its aim is to help the industry in leave management, registration of patients and improving workflow efficiency. This slide includes compliance, pharmacy, research program, management of expenses, etc. Introducing our ERP Security Management System For Healthcare set of slides. The topics discussed in these slides are Build Project Team, Assessment, Technology Selection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS
Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SSThis slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Increase audience engagement and knowledge by dispensing information using Security System Used In Smart IoT Remote Asset Monitoring And Management IoT SS. This template helps you present information on three stages. You can also present information on Components, Features, Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring Security Compliance For Banking Systems With Patch Management Process
Ensuring Security Compliance For Banking Systems With Patch Management ProcessFollowing slide showcases process of patch management to ensure security of banking systems. The purpose of this slide is to outline a series of steps to align with industry regulations while maintaining the security and stability of financial operations. It includes steps such as regulatory framework, etc.Presenting our set of slides with Ensuring Security Compliance For Banking Systems With Patch Management Process. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Management, Compliance Validation, Documentation Improvement
-
 Security Patch Management Process For Healthcare IT Systems
Security Patch Management Process For Healthcare IT SystemsFollowing slide showcases the healthcare industry security patch management process. The purpose of this slide is to help healthcare organizations in ensuring that their IT systems are patched safely and effectively. It includes steps such as define, identify and prioritize, etc.Presenting our set of slides with Security Patch Management Process For Healthcare IT Systems. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roles Responsibilities, Ensure Introduced, Deployment Depends.
-
 Information Security Management System Workflow
Information Security Management System WorkflowThis slide represents the workflow that helps businesses to implement effective information security management system in organization. This workflow includes major phases , tasks and users responsible for each activity. Introducing our premium set of slides with Information Security Management System Workflow. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Develop ISMS, Document Policy Freme Work, Designate Internal Auditor. So download instantly and tailor it with your information.
-
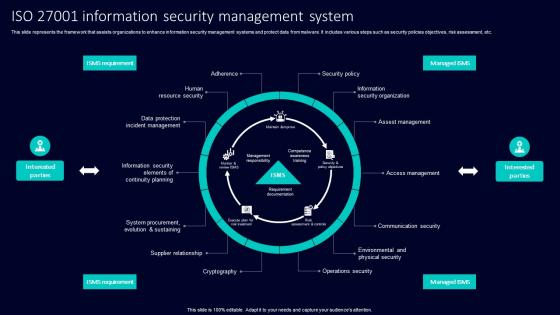 Iso 27001 Information Security Management System
Iso 27001 Information Security Management SystemThis slide represents the framework that assists organizations to enhance information security management systems and protect data from malware. It includes various steps such as security policies objectives, risk assessment, etc. Presenting our set of slides with Iso 27001 Information Security Management System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adherence, Security Policy, Assest Management.
-
 Roadmap To Implement Information Security Management System In Organization
Roadmap To Implement Information Security Management System In OrganizationThis slide represents roadmap that helps organizations implement system for information security management systems to protect sensitive data. It includes steps such as defining scope and objectives, identifying assets, recognizing risk, etc. Introducing our premium set of slides with Roadmap To Implement Information Security Management System In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recognize Risk, Make Improvement, Identify Mitigation Measures. So download instantly and tailor it with your information.
-
 Network Security Management System Icon
Network Security Management System IconPresenting our set of slides with Network Security Management System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security Management, System Icon.
-
 Parameters To Secure Network Security Management System
Parameters To Secure Network Security Management SystemThis slide showcases the safe security management system parameters which helps an organization to protect critical data and prevents unauthorized access to applications. It include details such as control removable media, smartly surf webpages, etc. Presenting our set of slides with Parameters To Secure Network Security Management System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Control Removable Media, Smartly Surf Webpages, Ensure Time Backups.
-
 Firewall Network Security Unified Threat Management UTM Firewall System Overview
Firewall Network Security Unified Threat Management UTM Firewall System OverviewThis slide provides an introduction to the Unified Threat Management firewall system. The purpose of this slide is to showcase the features, benefits, and inspection methods of Unified Threat Management firewall systems, such as flow-based and proxy-based inspection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Understanding Critical Risks Of Firewall Absence This template helps you present information on Three stages. You can also present information on Content Filtering, Faster Security, Flexibility And Adaptability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Criteria To Compare Firewall Management Systems
Firewall Network Security Criteria To Compare Firewall Management SystemsThis slide describes some key features to look for in a firewall management system. The purpose of this slide is to showcase some of the criteria to compare a firewall management system, including ease of use, efficiency, built-in integrations, and scalability. Introducing Firewall Network Security Criteria To Compare Firewall Management Systems to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Ease Of Use, Efficiency, Scalability using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Features Of Distributed Firewall Management System
Firewall Network Security Features Of Distributed Firewall Management SystemThis slide represents the key characteristics of distributed firewall management system. The purpose of this slide is to showcase the different features of distributed firewalls, such as central management systems, security policy distribution, enhanced access control, and host-end execution. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Features Of Distributed Firewall Management System This template helps you present information on Four stages. You can also present information on Access Control, Concurrency Processing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Importance And Benefits Of Distributed Firewall Management System
Firewall Network Security Importance And Benefits Of Distributed Firewall Management SystemThis slide outlines the importance of distributed firewall management system. It also includes the various advantages of distributed firewalls, including security from insider threats, intrusion detection, service exposure, and port scanning. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Importance And Benefits Of Distributed Firewall Management System This template helps you present information on Three stages. You can also present information on Network Address Translation, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Components Of Firewall Management System
Firewall Network Security Key Components Of Firewall Management SystemThis slide talks about the important elements of the firewall management system. The purpose of this slide is to showcase the vital components of a firewall management system, such as a graphical interface, policy control, threat management, device management, third-party integrations, and scalability. Introducing Firewall Network Security Key Components Of Firewall Management System to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service, Artificial Intelligence using this template. Grab it now to reap its full benefits.
-
 Information Security System Icon For Business Management
Information Security System Icon For Business ManagementIntroducing our premium set of slides with Information Security System Icon For Business Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security System, Business Management. So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Food Safety In Online Restaurant Online Order Management System
Securing Food Safety In Online Restaurant Online Order Management SystemThis slide covers integrating online order management software to track details such as bill number, order ID, customer name, amount paid and status. Present the topic in a bit more detail with this Securing Food Safety In Online Restaurant Online Order Management System. Use it as a tool for discussion and navigation on Duration, Channel, Preparing, Ready For Delivery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Utilizing Food Delivery Management System
Securing Food Safety In Online Utilizing Food Delivery Management SystemThis slide covers utilizing food delivery management software to keep track of deliveries. It involves bill number, channel and estimated duration. Introducing Securing Food Safety In Online Utilizing Food Delivery Management System to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Bill Number, Channel, Customer Location, Estimated Duration, using this template. Grab it now to reap its full benefits.
-
 Access Management Components Authentication Securing Systems With Identity
Access Management Components Authentication Securing Systems With IdentityThis slide gives an overview of access management of the Identity and Access Management process. The purpose of this slide is to explain access management that primarily focuses on authentication and authorization. Increase audience engagement and knowledge by dispensing information using Access Management Components Authentication Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Securing Systems With Identity And Access Management
Agenda For Securing Systems With Identity And Access ManagementIntroducing Agenda For Securing Systems With Identity And Access Management to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Architecture Of Identity And Access Management Process Securing Systems With Identity
Architecture Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the architecture structure of the Identity and Access Management process. The purpose of this slide is to explain the architecture of IAM that is capable of offering multiple data views and enables single sign-on. Present the topic in a bit more detail with this Architecture Of Identity And Access Management Process Securing Systems With Identity Use it as a tool for discussion and navigation on Internet, Corporate Demilitarized Zone, Customers Partners This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Basic Capabilities Of Identity And Access Management System Securing Systems With Identity
Basic Capabilities Of Identity And Access Management System Securing Systems With IdentityThis slide discusses the Identity and Access Management basic capabilities. The purpose of this slide is to explain the various capabilities of IAM these are identity management, user provisioning and de-provisioning, authentication, and so on. Deliver an outstanding presentation on the topic using this Basic Capabilities Of Identity And Access Management System Securing Systems With Identity Dispense information and present a thorough explanation of Identity Management, User Provisioning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Impact Of Identity And Access Management Securing Systems With Identity
Before Vs After Impact Of Identity And Access Management Securing Systems With IdentityThis slide showcases the comparative analysis of the before versus after IAM implementation. The purpose of this slide is to discuss the different performance aspects and how IAM has proved beneficial for these aspects. Present the topic in a bit more detail with this Before Vs After Impact Of Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Aspect, Self Registration, Policy Enforcement This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Identity And Access Management System Securing Systems With Identity
Benefits Of Identity And Access Management System Securing Systems With IdentityThis slide highlights the Identity and Access Management benefits. The purpose of this slide is to discuss the various advantages these include proper access for the right people, unhindered productivity, protection from data breaches, data encryption, etc. Deliver an outstanding presentation on the topic using this Benefits Of Identity And Access Management System Securing Systems With Identity Dispense information and present a thorough explanation of Collaboration And Efficiency, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Identity And Access Management Securing Systems With Identity
Checklist To Implement Identity And Access Management Securing Systems With IdentityThis slide represents the checklist to implement the Identity and Access Management plan in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying IAM in an enterprise environment. Deliver an outstanding presentation on the topic using this Checklist To Implement Identity And Access Management Securing Systems With Identity Dispense information and present a thorough explanation of Iam Policy And Strategy, User Lifecycle Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Components Of Identity And Access Management Process Securing Systems With Identity
Components Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management components. The purpose of this slide is to highlight the various components, including the IAM framework, access and roles, IAM system function, centralized directory services, and so on. Introducing Components Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Iam Framework Purpose, Access And Roles, Iam System Functions using this template. Grab it now to reap its full benefits.
-
 Concepts Of Identity And Access Management Securing Systems With Identity
Concepts Of Identity And Access Management Securing Systems With IdentityThis slide discusses the terms Identity and Access Management individually. The purpose of this slide is to explain that identity and access are two parts that govern how your users interact with data and applications across your information systems, networks, databases, and software. Increase audience engagement and knowledge by dispensing information using Concepts Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Identity, Access, Entitlements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Core Services Of Identity And Access Management Securing Systems With Identity
Core Services Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management core services. The purpose of this slide is to highlight the core services of IAM these include identifying, authentication, authorizing, auditing, and verifying the accounts. Introducing Core Services Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification, Authentication, Authorization using this template. Grab it now to reap its full benefits.
-
 Customer Identity And Access Management Vs IAM Securing Systems With Identity
Customer Identity And Access Management Vs IAM Securing Systems With IdentityThis slide showcases the comparison of Customer Identity and Access Management and the Identity and Access Management process. The purpose of this slide is to highlight the purpose and features of the CIAM and IAM process. Deliver an outstanding presentation on the topic using this Customer Identity And Access Management Vs IAM Securing Systems With Identity Dispense information and present a thorough explanation of Ciam Software, Iam Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Analytics Importance In Identity And Access Management Securing Systems With Identity
Data Analytics Importance In Identity And Access Management Securing Systems With IdentityThis slide showcases the importance of Identity and Access Management based data analytics. The purpose of this slide is to explain the benefits, which are anomaly detection, account monitoring, policy violation detection, and so on. Increase audience engagement and knowledge by dispensing information using Data Analytics Importance In Identity And Access Management Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Anomaly Detection, Identity Certification Campaigns using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Examples Of Identity And Access Management Securing Systems With Identity
Examples Of Identity And Access Management Securing Systems With IdentityThis slide highlights the Identity and Access Management examples. The purpose of this slide is to discuss the examples these include multi-factor authentication tools, access provisioning and de-provisioning, and user monitoring for access control. Introducing Examples Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Tools, Provisioning And Deprovisioning, Monitoring For Access Control using this template. Grab it now to reap its full benefits.
-
 Features Of Identity And Access Management Process Securing Systems With Identity
Features Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management features. The purpose of this slide is to explain the various features, including stored information authentication and authorization, external user registration, and so on. Present the topic in a bit more detail with this Features Of Identity And Access Management Process Securing Systems With Identity Use it as a tool for discussion and navigation on Stored Information, External User Registration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Framework Of Identity And Access Management Process Securing Systems With Identity
Framework Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management framework. The purpose of this slide is to highlight the procedure that includes outlining how IAM architecture components work together, define user access to resources, and so on. Increase audience engagement and knowledge by dispensing information using Framework Of Identity And Access Management Process Securing Systems With Identity This template helps you present information on Eight stages. You can also present information on Employee Movements, Security Threat Reduction, Standard Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functions Of Identity And Access Management Process Securing Systems With Identity
Functions Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management process functions. The purpose of this slide is to highlight the various functions, including identification in the system, roles in the design, assigning access levels, protecting sensitive data, and so on. Introducing Functions Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification In System, Roles In System using this template. Grab it now to reap its full benefits.
-
 Fundamentals Of Identity And Access Management Securing Systems With Identity
Fundamentals Of Identity And Access Management Securing Systems With IdentityThis slide discusses the fundamentals of the Identity and Access Management process. The purpose of this slide is to highlight the fundamental concepts of IAM, including authentication, authorization, administration, and audit. Increase audience engagement and knowledge by dispensing information using Fundamentals Of Identity And Access Management Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Authentication, Authorization, Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Historical Evolution Of Identity And Access Management Securing Systems With Identity
Historical Evolution Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management historical evolution. The purpose of this slide is to explain the historical background of IAM, including the historical roots of IAM, early IAM solutions, the role of tools, challenges with the directory, and so on. Introducing Historical Evolution Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Historical Roots Of Iam, Early Iam Solutions, Role Of Tools using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Securing Systems With Identity And Access Management
Icons Slide For Securing Systems With Identity And Access ManagementIntroducing our well researched set of slides titled Icons Slide For Securing Systems With Identity And Access Management It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identity And Access Management Challenges And Solutions Securing Systems With Identity
Identity And Access Management Challenges And Solutions Securing Systems With IdentityThis slide highlights the challenges associated with IAM. The purpose of this slide is to discuss the solutions provided to different challenges related to IAM. These include distributed workforce, distributed application, productive provisioning, BYOD, etc. Present the topic in a bit more detail with this Identity And Access Management Challenges And Solutions Securing Systems With Identity Use it as a tool for discussion and navigation on Challenges, Description, Solutions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Introduction And Functions Securing Systems With Identity
Identity And Access Management Introduction And Functions Securing Systems With IdentityThis slide gives an overview of the Identity and Access Management process. The purpose of this slide is to explain the IAM and its functions in ensuring authentication, reporting, authorization, workflow, access management, and so on. Introducing Identity And Access Management Introduction And Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Company Data And Resources, Streamline Workflows using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Process In Workplace Securing Systems With Identity
Identity And Access Management Process In Workplace Securing Systems With IdentityThis slide discusses the Identity and Access Management process in the workplace. The purpose of this slide is to highlight the various usages of IAM in the workplace these include increasing the number of applications, managing identity data, and complex access scenarios. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Process In Workplace Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Increasing Number Of Applications, Managing Identity Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Training Schedule For Staff Securing Systems With Identity
Identity And Access Management Training Schedule For Staff Securing Systems With IdentityThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Identity And Access Management Training Schedule For Staff Securing Systems With Identity Dispense information and present a thorough explanation of Policies And Procedures, Infrastructure And Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Impact Of Identity And Access Management On Business Securing Systems With Identity
Impact Of Identity And Access Management On Business Securing Systems With IdentityThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Deliver an outstanding presentation on the topic using this Impact Of Identity And Access Management On Business Securing Systems With Identity Dispense information and present a thorough explanation of Enhanced Security, Cost Savings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Focus Areas Of Identity And Access Management Securing Systems With Identity
Major Focus Areas Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management focus area. The purpose of this slide is to explain the focus area of IAM these include access management, privilege management, and identity governance. Increase audience engagement and knowledge by dispensing information using Major Focus Areas Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Access Management, Privilege Management, Identity Governance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For The Identity And Access Management Securing Systems With Identity
Need For The Identity And Access Management Securing Systems With IdentityThis slide discusses the requirement for Identity and Access Management process. The purpose of this slide is to highlight the needs these include secure user access, strong authentication, IAM solutions, IAM tasks, an evolving IT environment, etc. Present the topic in a bit more detail with this Need For The Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Secure User Access, Strong Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Systems With Identity And Access Management Table Of Content
Securing Systems With Identity And Access Management Table Of ContentIntroducing Securing Systems With Identity And Access Management Table Of Content to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Introduction And Functions, Biometric Authentication using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity
Steps To Implement Identity And Access Management In Enterprises Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing process in enterprises. The purpose of this slide is to highlight the implementation process, including usage assessment, environment understanding, key IAM considerations, and so on. Introducing Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Usage Assessment, Environment Understanding using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management Securing Systems With Identity
Steps To Implement Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing program. The purpose of this slide is to highlight the implementation process of IAM, including scope identification, evaluating the right IAM approach, finding the best solution, and so on. Increase audience engagement and knowledge by dispensing information using Steps To Implement Identity And Access Management Securing Systems With Identity This template helps you present information on Six stages. You can also present information on Scope Identification, Define A Strategy, Assess Cost Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




