Powerpoint Templates and Google slides for Security Layer
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Tools Processing Model Visualization Layer Security Segment
Data Tools Processing Model Visualization Layer Security SegmentDeliver a lucid presentation by utilizing this Data Tools Processing Model Visualization Layer Security Segment. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Processing Model, Visualization Layer, Security Segment. All the twenty nine slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 7 layers campaign finance mortgage security customer acceptance
7 layers campaign finance mortgage security customer acceptanceIf you require a professional template with great design, then this 7 Layers Campaign Finance Mortgage Security Customer Acceptance is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using thirteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS
Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SSThis slide exhibits security architecture principles on device and communication layer. It showcases iot ecosystem elements such as user, devices, gateway, connection, cloud, and applications. Present the topic in a bit more detail with this Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS. Use it as a tool for discussion and navigation on Iot Solution Elements, Important Security Principles. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Storage Area Network San Checklist To Secure Storage Area Network Layers
Storage Area Network San Checklist To Secure Storage Area Network LayersThis Slide Represents The Checklist To Protect The SAN Architecture Layers. The Purpose Of This Slide Is To Showcase The Various Steps And Actions That Organizations Should Keep In Mind While Deploying Or Working With A SAN Environment. The Measures Include Changing Passwords, Setting Firewalls, Taking Inventory, Etc. Present The Topic In A Bit More Detail With This Storage Area Network San Checklist To Secure Storage Area Network Layers. Use It As A Tool For Discussion And Navigation On Organizations, Environment, Measures. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Secure Socket Layer SSl Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Socket Layer SSl Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Secure Socket Layer SSL monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Socket Layer SSL monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Encryption Implementation Strategies Secure Socket Layer SSL Security Technology
Encryption Implementation Strategies Secure Socket Layer SSL Security TechnologyThe purpose of this slide is to explain the role of HTTPS and the secure sockets layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake process. Present the topic in a bit more detail with this Encryption Implementation Strategies Secure Socket Layer SSL Security Technology. Use it as a tool for discussion and navigation on Secure Socket Layer, Security Technology, Symmetric And Asymmetric Encryption, Protocol For Secure Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake
Encryption Implementation Strategies Transport Layer Security Implementation Using HandshakeThis slide discusses a cryptographic system known as transport layer security TLS. The purpose of this slide is to explain how TLS enables safe communication over computer networks using handshake protocol and record protocol. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake. This template helps you present information on two stages. You can also present information on Transport Layer Security Implementation, Handshake And Record Protocol, Computer Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Multi Layered Defence To Secure Network
Cybersecurity Multi Layered Defence To Secure NetworkThis slide covers multi layered defence security to protect corporate network and to improve defensive mechanism. It involves firewall, patch management, multi factor authentication, email filtering and dark web monitoring. Introducing our premium set of slides with Cybersecurity Multi Layered Defence To Secure Network. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Patch Management, Web Content Filtering, Email Filtering. So download instantly and tailor it with your information.
-
 Layered Defence Approach To Security Risk
Layered Defence Approach To Security RiskThis slide mentions types of security risk in layered defence to avoid attacks on network of internet communication. It includes active attacks and passive attacks. Presenting our set of slides with Layered Defence Approach To Security Risk. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Active Attacks, Passive Attacks, Security Risk.
-
 Layered Defence Security Control Measures
Layered Defence Security Control MeasuresThis slide covers types of layered defence control parameters which provides safeguard and countermeasures for protecting crucial information. It involves preventive control, detective control and corrective control. Introducing our premium set of slides with Layered Defence Security Control Measures. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preventive Controls, Detective Controls, Corrective Controls. So download instantly and tailor it with your information.
-
 Layered Defence Security Icon For Threat Detection
Layered Defence Security Icon For Threat DetectionPresenting our set of slides with Layered Defence Security Icon For Threat Detection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Layered Defence Security, Icon For Threat Detection.
-
 Layered Defense Architecture For Secured Network
Layered Defense Architecture For Secured NetworkThis slide covers architecture of layer defense to protect integrity of information and to provide full enterprise security protection. It includes physical control, technical control and administrative control. Presenting our set of slides with Layered Defense Architecture For Secured Network. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Physical Control, Technical Control, Administrative Control.
-
 Layered Defense Security Model For Enterprises
Layered Defense Security Model For EnterprisesThis slide highlights different layers of defence security model for organizations to manage security risk through multiple defensive strategies. It includes perimeter defence, host protection, application protection and data protection. Introducing our premium set of slides with Layered Defense Security Model For Enterprises. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Perimeter Defense, Host Protection, Application Protection. So download instantly and tailor it with your information.
-
 Security Layered Defence Pyramid Structure
Security Layered Defence Pyramid StructureThis slide highlights seven stages of layered defence for securing access to application and to providing internal security. It includes critical assets, data security, application security, endpoint security, network security, perimeter security and human layer. Presenting our set of slides with Security Layered Defence Pyramid Structure. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Mission Critical Assets, Application Security.
-
 Deploy Network Layer Firewall For Enforcing Security Policies
Deploy Network Layer Firewall For Enforcing Security PoliciesThis slide focuses on network layer firewall by controlling and monitoring cyber threats and enforcing access policies. It includes aspects such as non web attack, web attack, legitimate traffic, etc. Introducing our Deploy Network Layer Firewall For Enforcing Security Policies set of slides. The topics discussed in these slides are Operation Mode, Transparent Mode, Routed Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Establish Effective Internet Security Protocols In Network Layer
Establish Effective Internet Security Protocols In Network LayerThis slide exhibits network layer security architecture for providing virtual private network between two locations. It includes protocols such as encapsulating security payload, authentication header and internet key exchange. Presenting our set of slides with Establish Effective Internet Security Protocols In Network Layer. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Header, Authentication Methods, Encapsulating Security Payload.
-
 Security Consideration Issues For Network Layer Design
Security Consideration Issues For Network Layer DesignThis slide exhibits network layer design challenges for translating logical into physical addresses. It includes issues such as forward packet switching, transport layer services, etc. Presenting our well structured Security Consideration Issues For Network Layer Design. The topics discussed in this slide are Forward Packet Switching, Implement Connectionless Service, Implement Connection Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secure Sockets Layer Protocol In Powerpoint And Google Slides Cpb
Secure Sockets Layer Protocol In Powerpoint And Google Slides CpbPresenting Secure Sockets Layer Protocol In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Sockets Layer Protocol. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Firewall Network Security Ngfws Inspecting Traffic Across Layers
Firewall Network Security Ngfws Inspecting Traffic Across LayersThis slide talks about the inspection of traffic throughout the OSI model layers by Next Generation Firewalls. The purpose of this slide is to describe how Next Generation Firewalls examine network traffic across different layers 2-7 of the OSI model. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Ngfws Inspecting Traffic Across Layers This template helps you present information on Nine stages. You can also present information on Features, Benefits, Specify Hidden Risks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security About Stateful Multi Layer Inspection SMLI Firewall
Firewall Network Security About Stateful Multi Layer Inspection SMLI FirewallThis slide gives an overview of the Stateful Multi-layer Inspection firewall system, including its benefits and limitations. The purpose of this slide is to introduce Stateful Multi-layer Inspection firewall systems to secure networks and its benefits include enhanced protection, session awareness, granular control, etc. Introducing Firewall Network Security About Stateful Multi Layer Inspection SMLI Firewall to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Protection, Network Session, Destination Port Numbers using this template. Grab it now to reap its full benefits.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age It
Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age ItThis slide demonstrates the different forms of Secure Sockets Layer certificates such as single domain, wildcard and multi-domain. This slide also discusses the types of SSL certificates based on validation such as domain, organization and extended validation. Deliver an outstanding presentation on the topic using this Types Of Secure Sockets Layer Certificates Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Domain Validation, Organization Validation, Extended Validation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS
Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Present the topic in a bit more detail with this Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Storage Communication, Network Management, Routing Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SS
IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide showcases edge computing architecture that helps in improving performance and reduce latency through real time data processing. It includes three layers such as cloud layer, edge layer, and device layer. Deliver an outstanding presentation on the topic using this IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Data Processing, Data Catching, Critical Data Storage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS
IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide exhibits a multi layer architecture aimed at enhancing data processing and communication. It includes layers such as the application layer, processing layer, transport layer, and perception layer.Increase audience engagement and knowledge by dispensing information using IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Communication Technologies, Processing Layer, Network Layer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Primary Layers Of Web Security Approach
Primary Layers Of Web Security ApproachThis slide outlines the seven layers of web security which include endpoint security, application security, network security layer, etc. Introducing our premium set of slides with name Primary Layers Of Web Security Approach. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security Layer, Application Security Layer, Endpoint Security Layer. So download instantly and tailor it with your information.
-
 Different Security Layers In Sql Server Environments
Different Security Layers In Sql Server EnvironmentsFollowing slide showcases SQL server security layers, also including layers such as physical security, network security, database security, application security and operating system security, etc. Introducing our premium set of slides with Different Security Layers In Sql Server Environments. Ellicudate the fivestages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Network Security, Operating System Security. So download instantly and tailor it with your information.
-
 Multi Layered Server Security System Flowchart
Multi Layered Server Security System FlowchartFollowing slide highlights flowchart of multi layered server security, also including elements such as host authentication, server network access, physical access, data masking, etc. Introducing our Multi Layered Server Security System Flowchart set of slides. The topics discussed in these slides are Physical Access, Host Access, Data Masking. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Crucial Layers Of Security Technology Stack
Crucial Layers Of Security Technology StackThis slide showcases the key layers of security technology stack which helps an organization to provide standardized and organized technique for developing software and tools. It include details such as operating system, server-side programming, web server and database. Presenting our well structured Crucial Layers Of Security Technology Stack The topics discussed in this slide are Operating System, Web Server, Database. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Four Layers Of Cyber Security Mesh
Four Layers Of Cyber Security MeshThe following slide features essential elements such as security analytics, consolidated policy management, Distributed identity fabric, and unified dashboards to depict the four layers of cybersecurity mesh. This aids in understanding the comprehensive structure and capabilities of cyber mesh. Presenting our set of slides with Four Layers Of Cyber Security Mesh This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Posture Management, Distributed Identity Fabric, Consolidated Dashboards
-
 IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Secure Communications, Secure Cloud, Secure Device, Messaging Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ecommerce Multi Layer Security Measure
Ecommerce Multi Layer Security MeasureThis slide shows ensuring comprehensive protection against diverse cyber threats for secure online transactions and data integrity in e-commerce operations. The multilayer security components are set up strong passwords, multifactor authentication, etc. Presenting our set of slides with Ecommerce Multi Layer Security Measure. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multifactor Authentication, Security Measure, Authentication .
-
 Multi Layered Managed Organization Security Services
Multi Layered Managed Organization Security ServicesThe following slide provides the various types of managed security services provided by company for different risk categories. The various security requirements are endpoint. Application, cloud, etc. Presenting our set of slides with Multi Layered Managed Organization Security Services. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Endpoint Security, Application Security, Cloud Security.
-
 IOT Technology Security Layer Architecture
IOT Technology Security Layer ArchitectureThis slide showcases IoT security architecture along with three layers. It includes IoT application and support layer, local area network, core network, access network and perception node. Introducing our IOT Technology Security Layer Architecture set of slides. The topics discussed in these slides are Secure Service, System Security, Secure Connection, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Features Of Perimeter Layer In Web Security Solution
Features Of Perimeter Layer In Web Security SolutionThis slide outlines the characteristics of perimeter layer in web security such as access control, data protection, active monitoring, etc. Introducing Features Of Perimeter Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Access Control, Data Protection, Active Monitoring, Device Security, using this template. Grab it now to reap its full benefits.
-
 Introduction Of Data Layer In Web Security Solution
Introduction Of Data Layer In Web Security SolutionThis slide discusses the overview of the sixth layer of web security, which is the data layer for enhancing security in the web. Introducing Introduction Of Data Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Data Integrity, Employing Data Encryption Is Crucial, Safeguard Against Unintentional Data Loss Deletion, using this template. Grab it now to reap its full benefits.
-
 Introduction Of Endpoint Layer In Web Security Solution
Introduction Of Endpoint Layer In Web Security SolutionThis slide discusses the introduction of endpoint layer in web security for security of devices connected to the network. Introducing Introduction Of Endpoint Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Specialized Software Is Employed, Protects The Overall Network, Secures All Devices Connected To Network, using this template. Grab it now to reap its full benefits.
-
 Objectives Of Application Layer In Web Security Solution
Objectives Of Application Layer In Web Security SolutionThis slide outlines the goals of application layer in web security which include incorporating authentication, authorization, encryption, etc. Introducing Objectives Of Application Layer In Web Security Solution to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Focus On, Incorporating, using this template. Grab it now to reap its full benefits.
-
 Overview Of Application Layer In Web Security Solution
Overview Of Application Layer In Web Security SolutionThis slide highlights the introduction of application layer in web security which involves designing of code and configuring software application. Introducing Overview Of Application Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Involves The Design Of Code, Enhances Security, Configures Software Application, using this template. Grab it now to reap its full benefits.
-
 Overview Of Network Layer In Web Security Solution
Overview Of Network Layer In Web Security SolutionThis slide outlines the introduction of network layer in web security. It also includes the encompassed measures. Introducing Overview Of Network Layer In Web Security Solution to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Encompasses Safeguarding Network Infrastructure, Refers To Interconnected Devices, Involves The Establishment Of Security Policies, using this template. Grab it now to reap its full benefits.
-
 Overview Of Perimeter Layer In Web Security Solution
Overview Of Perimeter Layer In Web Security SolutionThis slide highlights the introduction of perimeter layer in web security that controls the access to the network at outer edge. Introducing Overview Of Perimeter Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Controls Network Access, Prevents Unauthorized Entry, Responsibility At Outer Edge, Initial Defense Against Threats, using this template. Grab it now to reap its full benefits.
-
 Overview Of Physical Layer In Web Security Solution
Overview Of Physical Layer In Web Security SolutionThis slide discusses the introduction of the first layer of web security, that is the physical layer which controls the access of users. Introducing Overview Of Physical Layer In Web Security Solution to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Involves Controlling Access To Areas, Safeguard Physical Assets, Provides Restricted Access To Computer Systems, using this template. Grab it now to reap its full benefits.
-
 User Education Layer In Web Security Solution
User Education Layer In Web Security SolutionThis slide outlines the introduction of seventh layer of web security, which is the user education layer in web security. Introducing User Education Layer In Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Educates On Cybersecurity Best Practices, Instruct To Implement Two-Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 3 layer secure database server icon
3 layer secure database server iconPresenting our set of slides with 3 Layer Secure Database Server Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on 3 Layer Secure Database Server Icon.
-
 Network layer security protocols ppt powerpoint presentation pictures layout ideas cpb
Network layer security protocols ppt powerpoint presentation pictures layout ideas cpbPresenting our Network Layer Security Protocols Ppt Powerpoint Presentation Pictures Layout Ideas Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Network Layer Security Protocols This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through Iot
Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through IotThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an outstanding presentation on the topic using this Strategy To Provide Layered Security Across Networks Enabling Smart Shipping And Logistics Through Iot. Dispense information and present a thorough explanation of Applications, Bandwidth Access Limitation, Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pros Cons Layered Security Ppt Powerpoint Presentation Portfolio Graphics Pictures Cpb
Pros Cons Layered Security Ppt Powerpoint Presentation Portfolio Graphics Pictures CpbPresenting Pros Cons Layered Security Ppt Powerpoint Presentation Portfolio Graphics Pictures Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Payment Withholding Tax. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Three Layers Of Cyber Security Management Process
Three Layers Of Cyber Security Management ProcessThe following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting our set of slides with name Three Layers Of Cyber Security Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on People, Process, Technology.
-
 Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business
Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping BusinessThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business. Use it as a tool for discussion and navigation on Strategy, Authentication, Appropriate Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt Themes
Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt ThemesThis slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Deliver an outstanding presentation on the topic using this Secure Sockets Layer SSL Proxy Server And Its Architecture Reverse Proxy Load Balancer Ppt Themes. Dispense information and present a thorough explanation of Conjunction, Engine Position, Architecture, Secure Sockets Layer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations
Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security OperationsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Alert Monitoring, Attack Investigation, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
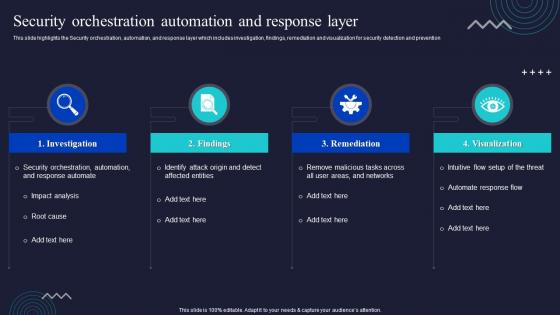 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Sockets Layer SSL Proxy Server And Its Architecture Ppt Powerpoint Presentation Icon Grid
Secure Sockets Layer SSL Proxy Server And Its Architecture Ppt Powerpoint Presentation Icon GridThis slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Present the topic in a bit more detail with this Secure Sockets Layer SSL Proxy Server And Its Architecture Ppt Powerpoint Presentation Icon Grid. Use it as a tool for discussion and navigation on Web Server, Additional Security Against Attacks, Suitable For Businesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
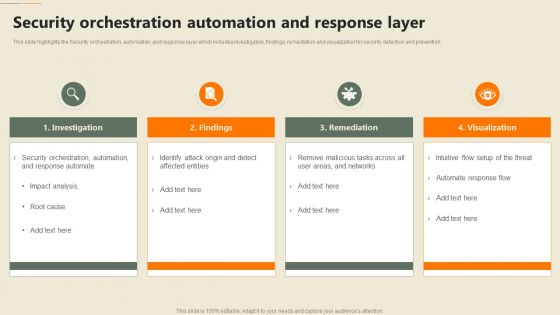 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
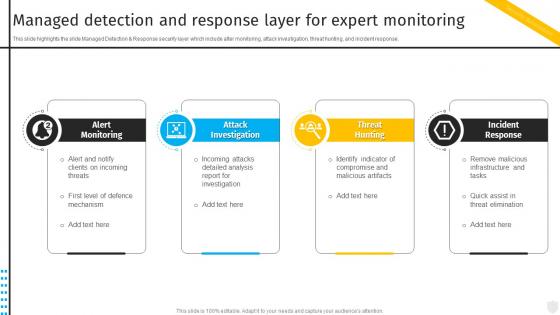 Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate Cyberthreats
Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Attack Investigation, Incident Response, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
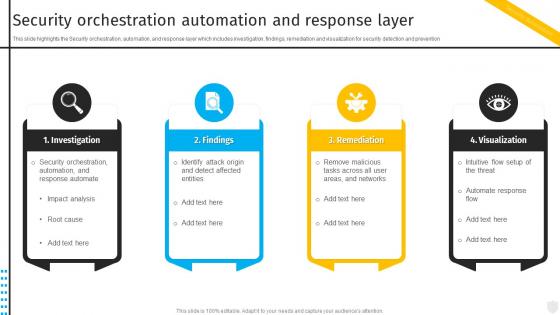 Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate Cyberthreats
Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Orchestration Automation And Response Layer Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on four stages. You can also present information on Orchestration, Automation, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
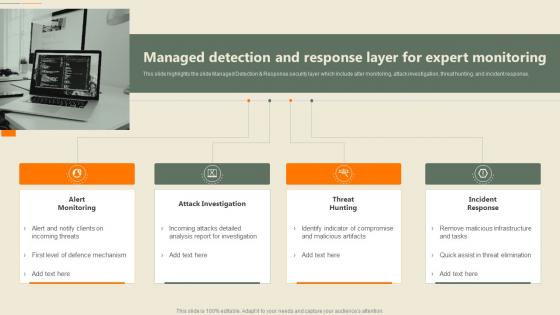 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations
Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient OperationsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an outstanding presentation on the topic using this Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations. Dispense information and present a thorough explanation of Strategy, Information, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics
Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better LogisticsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics. Use it as a tool for discussion and navigation on Profile Authentication, Allocation Appropriate, Particular Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.




