Powerpoint Templates and Google slides for Security Information
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Comparison Analysis Of Data Masking Tools For Information Security
Comparison Analysis Of Data Masking Tools For Information SecurityThis slide represents comparison analysis of data masking tools that assist companies to enhance their sensitive information security. It includes various tools such as K2View data masking, DATPROF data masking tool, Oracle data masking and subsetting, etc. Presenting our well structured Comparison Analysis Of Data Masking Tools For Information Security. The topics discussed in this slide are Virtualization, Synthetic Data Generation, Tokenization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Mapping Icon For Securing Online Customer Information
Data Mapping Icon For Securing Online Customer InformationPresenting our set of slides with Data Mapping Icon For Securing Online Customer Information. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Mapping Icon, Securing Online Customer Information.
-
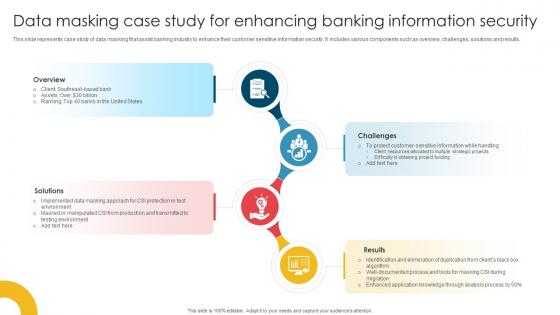 Data Masking Case Study For Enhancing Banking Information Security
Data Masking Case Study For Enhancing Banking Information SecurityThis slide represents case study of data masking that assist banking industry to enhance their customer sensitive information security. It includes various components such as overview, challenges, solutions and results. Introducing our premium set of slides with Data Masking Case Study For Enhancing Banking Information Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Overview, Solutions, Challenges.So download instantly and tailor it with your information.
-
 Data Masking Icon To Enhance Information Security
Data Masking Icon To Enhance Information SecurityPresenting our set of slides with Data Masking Icon To Enhance Information Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Masking Icon, Enhance Information Security.
-
 Physical Security Information Management Across Various Industries
Physical Security Information Management Across Various IndustriesThis slide showcases physical security information management solutions. It includes vendors, system integrations, applications such as retail, BFSI, energy and utility, transportations and hospitality. Presenting our well structured Physical Security Information Management Across Various Industries. The topics discussed in this slide are Vendors, System Integration, Physical Security Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
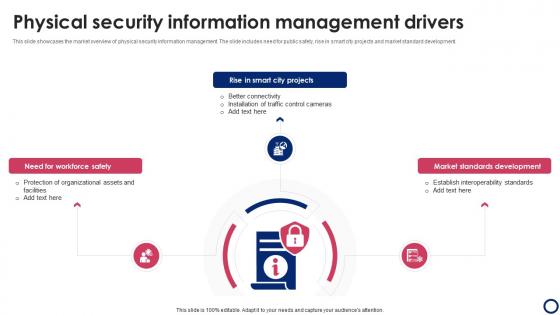 Physical Security Information Management Drivers
Physical Security Information Management DriversThis slide showcases the market overview of physical security information management. The slide includes need for public safety, rise in smart city projects and market standard development. Introducing our premium set of slides with Physical Security Information Management Drivers. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Market Standards Development, Need Workforce Safety, Rise Smart. So download instantly and tailor it with your information.
-
 Information Security Emergency Management Plan
Information Security Emergency Management PlanThis slide covers the information security management plan control by using firewall, backup drives and encrypted technology. Presenting our well structured Information Security Emergency Management Plan. The topics discussed in this slide are Compensation Control, Duration Required, Impact Level This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Based Regtech Icon For Enhancing Information Security
Cloud Based Regtech Icon For Enhancing Information SecurityIntroducing our premium set of slides with name Cloud Based Regtech Icon For Enhancing Information Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Based Regtech, Icon, Enhancing Information Security. So download instantly and tailor it with your information.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hackers Information Security In Powerpoint And Google Slides Cpp
Hackers Information Security In Powerpoint And Google Slides CppPresenting Hackers Information Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Hackers Information Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information Security In Powerpoint And Google Slides Cpp
Information Security In Powerpoint And Google Slides CppPresenting our Information Security In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Loss Prevention Icon To Optimize Information Security
Data Loss Prevention Icon To Optimize Information SecurityIntroducing our Data Loss Prevention Icon To Optimize Information Security set of slides. The topics discussed in these slides are Information, Security, Prevention. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Organizational Information Technology Security Budget Analysis
Organizational Information Technology Security Budget AnalysisThis slide provides the budget analysis for development of organizational security by installation of new services. The various cost estimation parameters are new license required, subscription cost, purchase status, etc. Introducing our Organizational Information Technology Security Budget Analysis set of slides. The topics discussed in these slides are Revenue, Security Goal, IT Security Budget. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon represents a client onboarding checklist, designed to streamline the process and optimize resource utilization. With its eye-catching design and clear visual cues, this icon is perfect for presentations and documents related to client onboarding procedures and strategies.
-
 Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to assist with client onboarding checklists, ensuring efficient resource utilization. With a sleek and minimalist design, this icon is perfect for presentations and documents related to client onboarding processes. It is a must-have for any business looking to streamline their onboarding procedures.
-
 Information Server Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Server Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your server security with our File Network Protection icon for PowerPoint. This eye-catching icon features a bold and vibrant design, making it easy to locate and use. Keep your files safe and secure with this essential tool for any business or organization.
-
 Information Server Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Server Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents File network protection through server security. It is designed to keep your files safe and secure by providing advanced security measures through the server. With this icon, you can easily identify and access the necessary tools to protect your files from unauthorized access and potential threats.
-
 Cyber Security Information Technology List
Cyber Security Information Technology ListThis slide showcases list of cyber security data technology. The purpose of this template is to help businesses in maintaining confidentiality of information systems for building trust of customers in digital age. It includes elements such as firewalls, antivirus, etc. Presenting our set of slides with name Cyber Security Information Technology List. This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewalls, Intrusion Detection And Prevention Systems, Antivirus, Access Control Systems.
-
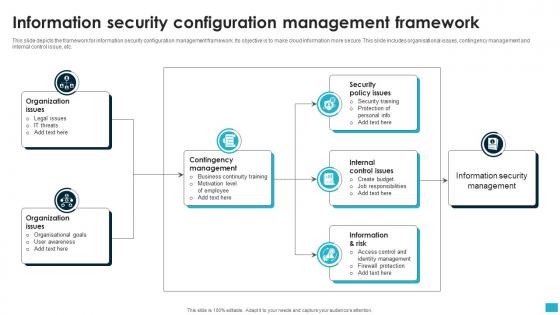 Information Security Configuration Management Framework
Information Security Configuration Management FrameworkThis slide depicts the framework for information security configuration management framework. Its objective is to make cloud information more secure. This slide includes organisational issues, contingency management and internal control issue, etc. Introducing our premium set of slides with name Information Security Configuration Management Framework. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organization Issues, Contingency Management, Internal Control Issues. So download instantly and tailor it with your information.
-
 Information Security Configuration Management Phases
Information Security Configuration Management PhasesThis slide depicts a set of activities for securing configuration management in phases. Its objective is to support information system and avoid organisational risk. This slide includes planning, implementing configuration, configuration changes, monitoring, etc. Introducing our premium set of slides with name Information Security Configuration Management Phases. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Controlling Configuration Changes, Monitoring. So download instantly and tailor it with your information.
-
 Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is designed to represent Firewall Audit, a crucial process for ensuring network security. With a bold and eye-catching design, this icon is perfect for presentations and documents related to network security, providing a visual representation of the importance of conducting regular audits to maintain a secure network.
-
 Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual representation for Firewall Audit Ensuring Network Security. It showcases the importance of conducting regular audits to ensure the safety and protection of your network. With its sleek and modern design, this icon will enhance any presentation on network security.
-
 Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on information security with this eye-catching PowerPoint icon. Featuring a bold and vibrant color, this icon represents the crucial aspect of information security audits. Perfect for IT professionals, consultants, and businesses looking to showcase their expertise in protecting sensitive data. Download now and make a lasting impression.
-
 Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with our Monotone PowerPoint icon on Information Security Audit. This sleek and professional icon represents the importance of safeguarding sensitive data and conducting thorough audits. Perfect for presentations on cyber security, compliance, and risk management. Grab your audiences attention and convey a message of security and diligence.
-
 Economics Information Security In Powerpoint And Google Slides CPP
Economics Information Security In Powerpoint And Google Slides CPPPresenting our Economics Information Security In Powerpoint And Google Slides CPP PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Economics Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Building Blocks Of Information Security Governance Framework
Building Blocks Of Information Security Governance FrameworkThis slide covers building elements for information security framework. It includes stakeholders, executives, security governance, oversee, monitor and direct. Introducing our Building Blocks Of Information Security Governance Framework set of slides. The topics discussed in these slides are Stakeholders, Report, Audit, Oversee, Evaluate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Governance Security Management Icon
Information Governance Security Management IconPresenting our set of slides with name Information Governance Security Management Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information, Governance Security Management.
-
 Information Technology Network Security Icon
Information Technology Network Security IconIntroducing our premium set of slides with name Information Technology Network Security Icon. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Network Security. So download instantly and tailor it with your information.
-
 Strategic Information Technology Security Plan
Strategic Information Technology Security PlanThis slide represents strategic plan for information technology security which includes security types such as network security, internet security, endpoint security, etc. Introducing our premium set of slides with name Strategic Information Technology Security Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Purpose, Person Responsible, Actions Required, Status. So download instantly and tailor it with your information.
-
 Economic Aspects Of Information Security In Powerpoint And Google Slides Cpp
Economic Aspects Of Information Security In Powerpoint And Google Slides CppPresenting Economic Aspects Of Information Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Economic Aspects Of Information Security This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information security management ppt examples
Information security management ppt examplesPresenting information security management ppt examples. This is a information security management ppt examples. This is a three stage process. The stages in this process are analyze, identify, process, validate, valuate, verbalize, visibility.
-
 Ppts information security system diagram powerpoint topics
Ppts information security system diagram powerpoint topicsPresenting ppts information security system diagram powerpoint topics. This is a information security system diagram powerpoint topics. This is a one stage process. The stages in this process are information, network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security.
-
 App information management security example ppt slides
App information management security example ppt slidesPresenting app information management security example ppt slides. This is a information management security example ppt slides. This is a three stage process. The stages in this process are identify, process, analyze.
-
 Information management security presentation powerpoint
Information management security presentation powerpointPresenting information management security presentation powerpoint. This is a information management security presentation powerpoint. This is a three stage process. The stages in this process are process, analyze, identify.
-
 Information security management presentation powerpoint example
Information security management presentation powerpoint examplePresenting information security management presentation powerpoint example. This is a information security management presentation powerpoint example. This is a five stage process. The stages in this process are applications, bpms, communications, information security, infrastructure and operations.
-
 Automated security information collection process diagram ppt slides
Automated security information collection process diagram ppt slidesPresenting automated security information collection process diagram ppt slides. This is a automated security information collection process diagram ppt slides. This is a five stage process. The stages in this process are hazard identification, exposure assessment, report progress, fix worst first, triage and analyze result.
-
 Process of information security management ppt presentation visuals
Process of information security management ppt presentation visualsPresenting process of information security management ppt presentation visuals. This is a process of information security management ppt presentation visuals. This is a six stage process. The stages in this process are security policy, access control, compliance, business continuity, operations security, physical security.
-
 Information security management cycle presentation deck
Information security management cycle presentation deckPresenting information security management cycle presentation deck. This is a information security management cycle presentation deck. This is three stage process. The stages in this process are reviewing and improving, assessing security risks, implementing and maintaining a secure framework, monitoring and recording.
-
 Information security assessment ppt background designs
Information security assessment ppt background designsPresenting information security assessment ppt background designs. This is a information security assessment ppt background designs. This is a four stage process. The stages in this process are assess, control, monitor, respond, assets, technology, people, processes.
-
 Dashboard snapshot threat tracking electronic information security
Dashboard snapshot threat tracking electronic information securityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Dashboard Snapshot Threat Tracking Electronic Information Security. Use it as a tool for discussion and navigation on Most Monthly Threat Status, Threat Dashboard, Current Risk Status, Threats Based Role, Risk By Threats, Threat Report, Threats Owners. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security cyber attacks experienced company previous
Electronic information security cyber attacks experienced company previousThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver an outstanding presentation on the topic using this Electronic Information Security Cyber Attacks Experienced Company Previous. Dispense information and present a thorough explanation of Cyber Attacks, Massive Increase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security update and installation antivirus software
Electronic information security update and installation antivirus softwareThis slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an outstanding presentation on the topic using this Electronic Information Security Update And Installation Antivirus Software. Dispense information and present a thorough explanation of Choose best antivirus software organization, To install antivirus software devices, antivirus software periodically, Antivirus software usage chart across US using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Requirement of electronic information security in different sectors
Requirement of electronic information security in different sectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Requirement Of Electronic Information Security In Different Sectors. Dispense information and present a thorough explanation of Cyber Attacks, Past 12 Months, Devices Business Transactions, Organizations Transfer, Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information dashboard security information and event management
Security information dashboard security information and event managementThis slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Present the topic in a bit more detail with this Security Information Dashboard Security Information And Event Management. Use it as a tool for discussion and navigation on Security Information And Event Management Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security event management security information and event management
Security event management security information and event managementThis slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Present the topic in a bit more detail with this Security Event Management Security Information And Event Management. Use it as a tool for discussion and navigation on Security Information And Event Management Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management security management dashboard
Security information and event management security management dashboardThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Present the topic in a bit more detail with this Security Information And Event Management Security Management Dashboard. Use it as a tool for discussion and navigation on Security Information And Event Management Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compliance dashboard snapshot of electronic information security
Compliance dashboard snapshot of electronic information securityThis slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Present the topic in a bit more detail with this Compliance Dashboard Snapshot Of Electronic Information Security. Use it as a tool for discussion and navigation on Asset Type Control, Compliance Dashboard, Control Issues By Regulation, Control Issues By Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security highest number malware attacks departments
Electronic information security highest number malware attacks departmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Present the topic in a bit more detail with this Electronic Information Security Highest Number Malware Attacks Departments. Use it as a tool for discussion and navigation on Development Dept, Accounts Dept, HR Dept, Other, IT Dept. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security problems faced by the organization
Electronic information security problems faced by the organizationThis slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver an outstanding presentation on the topic using this Electronic Information Security Problems Faced By The Organization. Dispense information and present a thorough explanation of Worms, Botnets, Daniel Service, Phishing, Online Attacks, Malware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current security infrastructure effective information security risk management process
Current security infrastructure effective information security risk management processMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Current Security Infrastructure Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset Management, Incident Mitigation Plan, Incident Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security dashboard effective information security risk management process
Information security dashboard effective information security risk management processFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Present the topic in a bit more detail with this Information Security Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Analysis Progress Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security current security infrastructure performance analysis
Effective information security current security infrastructure performance analysisMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an outstanding presentation on the topic using this Effective Information Security Current Security Infrastructure Performance Analysis. Dispense information and present a thorough explanation of Performance, Actual Target Met, Target To Be Met, Asset Management, Data Security, Incident Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security impact on security infrastructure performance
Effective information security impact on security infrastructure performanceMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Effective Information Security Impact On Security Infrastructure Performance. Dispense information and present a thorough explanation of NIST Core Functions, Performance, Actual Target met using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security information security risk management dashboard
Effective information security information security risk management dashboardFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Effective Information Security Information Security Risk Management Dashboard. Dispense information and present a thorough explanation of Risk Threshold, Risk Analysis, Progress Response, Progress Risks Threshold using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact of information security risk management on company
Impact of information security risk management on companyMentioned slide graphically depicts before and after impact of information security risk management on a company. The various points covered in the slide are increased costs, operational disruption, reputational damage, improved company credentials, faster recovery time etc. Introducing our Impact Of Information Security Risk Management On Company set of slides. The topics discussed in these slides are Network, Security, Risk. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk management challenges and solutions
Information security risk management challenges and solutionsMentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber adversaries, tracking sensitive data flows. Introducing our Information Security Risk Management Challenges And Solutions set of slides. The topics discussed in these slides are Measuring, Service, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Certified information systems security professional cissp examination details
Certified information systems security professional cissp examination detailsThis slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an outstanding presentation on the topic using this Certified Information Systems Security Professional CISSP Examination Details. Dispense information and present a thorough explanation of Asset Security, Security Operations, Communications And Network Security, Security Engineering, Security Assessment And Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Certified information systems security professional cissp salary and job details
Certified information systems security professional cissp salary and job detailsThis slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an outstanding presentation on the topic using this Certified Information Systems Security Professional CISSP Salary And Job Details. Dispense information and present a thorough explanation of Information Security Analyst, Information Security Manager, Chief Information Security Officer, Security Architect, Security Engineer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Real time analysis of security alerts information and event management dashboard
Real time analysis of security alerts information and event management dashboardThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an outstanding presentation on the topic using this Real Time Analysis Of Security Alerts Information And Event Management Dashboard. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





