Powerpoint Templates and Google slides for Security Implementation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security Model
Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security ModelThis slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Present the topic in a bit more detail with this Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Solutions, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security Model
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security ModelThis slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Present the topic in a bit more detail with this Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security Model. Use it as a tool for discussion and navigation on User And Device Identity, Applications And Data, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security ModelThis slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Deliver an outstanding presentation on the topic using this Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model. Dispense information and present a thorough explanation of Operational, Implement, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SS
Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SSThe following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Introducing Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Marketing Strategies, Potential Impact, Project Awareness, using this template. Grab it now to reap its full benefits.
-
 EHR Security Implementation Plan Icon
EHR Security Implementation Plan IconIntroducing our EHR Security Implementation Plan Icon set of slides. The topics discussed in these slides are Ehr Security Implementation Plan Icon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway
Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web GatewayThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Productivity, Enforcement, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway
Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Deliver an outstanding presentation on the topic using this Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Assessment, Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway
Checklist To Implement Secure Web Gateway Network Security Using Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Deliver an outstanding presentation on the topic using this Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Configure Solution, Plan Deployment, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Methods To Implement Security Policies On Network Security Using Secure Web Gateway
Methods To Implement Security Policies On Network Security Using Secure Web GatewayThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Deliver an outstanding presentation on the topic using this Methods To Implement Security Policies On Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Organizational, Examination, Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway
Secure Implementation Methodology Explicit Network Security Using Secure Web GatewayThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Deliver an outstanding presentation on the topic using this Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Methodology, Concentrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway Implementation Transparent Network Security Using Secure Web Gateway
Secure Web Gateway Implementation Transparent Network Security Using Secure Web GatewayThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Deliver an outstanding presentation on the topic using this Secure Web Gateway Implementation Transparent Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Methodology, Communications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway
Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web GatewayThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Present the topic in a bit more detail with this Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Implementation, Methodology, Analyzer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V
Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users finding and tracking business owned devices and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Installation Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V
Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Access Security Control Models Strategy SS V
Implementation Of Information Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Implementation Of Information Key Access Security Control Models Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V
Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Access Security, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
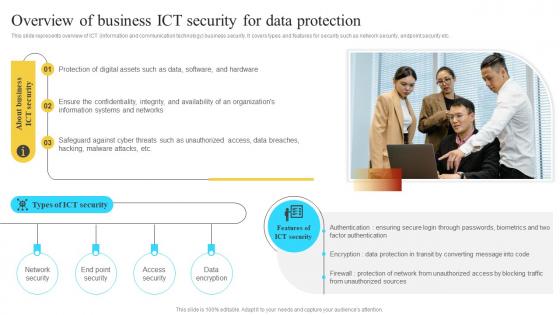 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
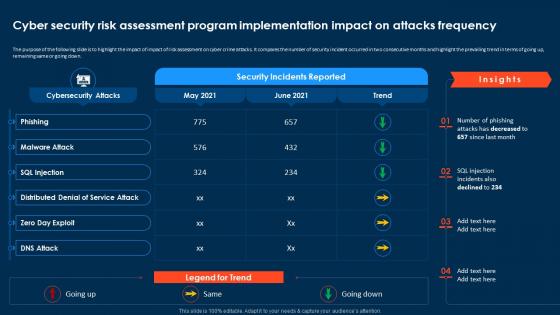
 Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact
Security Plan To Prevent Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation Impact
Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact
Compressive Planning Guide Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment Program, Attacks Frequency, Distributed Denial Of Service Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
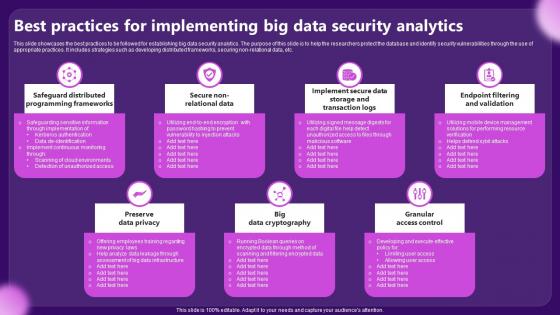 Best Practices For Implementing Big Data Security Analytics
Best Practices For Implementing Big Data Security AnalyticsThis slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non relational data, etc. Presenting our set of slides with Best Practices For Implementing Big Data Security Analytics. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserve Data Privacy, Granular Access Control.
-
 Challenges Faced During Cyber Security Management Plan Implementation
Challenges Faced During Cyber Security Management Plan ImplementationThis slide highlights the challenges faced by businesses during the implementation of a cybersecurity management plan. The purpose of this slide is to help the business establish a suitable cyber security management plan through the elimination of structural vulnerabilities such as scarcity of skilled professionals, inability to adapt to evolving cyber attacks, etc.Presenting our well structured Challenges Faced During Cyber Security Management Plan Implementation. The topics discussed in this slide are Complicated Environments, Business Operations, Defending Against. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
 Implementing Security System In Organization
Implementing Security System In OrganizationThis slide highlights implementing security system in organization process. This further includes business model, threat assessment, security policies, incident response, security controls and maintain security. Presenting our set of slides with Implementing Security System In Organization. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Maintain Security, Managed Security, Security Controls.
-
 Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a Cloud Access Security Broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Cloud Access Security Broker, Business Operations, Building Visibility, Forecasting Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
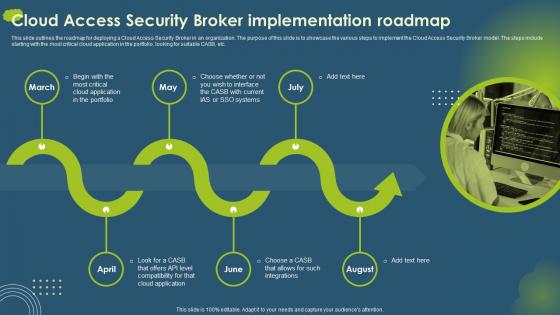 Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait
Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery PortraitThis slide outlines the roadmap for deploying a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to implement the Cloud Access Security Broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Critical Cloud Application, Compatibility, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a Cloud Access Security Broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Cloud Applications, Malware Detection And Removal, using this template. Grab it now to reap its full benefits.
-
 ERP Security Management Implementation Roadmap
ERP Security Management Implementation RoadmapThis slide showcases the ERP security management implementation roadmap in SMEs. Its objective is to make the management ready to reach predefined goals. This slide includes project team, assessment, technological selection, business blueprint, test, etc. Presenting our well structured ERP Security Management Implementation Roadmap. The topics discussed in this slide are Build Alignment, Define ERP, Plan Project. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementation Roadmap For ERP Security Management
Implementation Roadmap For ERP Security ManagementThis slide showcases the implementation of roadmap security management in ERP. Its objective is to formulate a team and figure out the configuration level. This slide includes training, hardware evaluation, scenario training, protocol, etc. Presenting our set of slides with Implementation Roadmap For ERP Security Management. This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resolution Protocol, Figure Out Configuration, Testing Scenario.
-
 Kpis For ERP Security Management Implementation
Kpis For ERP Security Management ImplementationThis slide showcases the important KPIs for implementation of ERP security management. Its objective is to check the key metrics and identify the problems. This slide includes inventory turnover, project margins, demand forecasting, business productivity, employee satisfaction, etc. Introducing our premium set of slides with Kpis For ERP Security Management Implementation. Ellicudate the Nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Inventory Turnover, Business Productivity, Customer Experience. So download instantly and tailor it with your information.
-
 Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network
Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into NetworkThe purpose of this slide is to outline the steps involved in implementing a security protocol into a network. These are access network requirements, plan and design, select the right protocol, prepare the network infrastructure, configure devices, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network. Dispense information and present a thorough explanation of Assess Network Requirements, Implement User Authentication, Suitable Security Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Security Concerns Faced By Company
Encryption Implementation Strategies Data Security Concerns Faced By CompanyThis slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies. These concerns are unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Security Concerns Faced By Company. Dispense information and present a thorough explanation of Data Security Concerns, Phishing Attacks, Data Protection Technologies, Compliance And Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Database Encryption Methods For Business Security
Encryption Implementation Strategies Database Encryption Methods For Business SecurityThis slide discusses the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources. The database encryption levels are application-level encryption, plug-in method, TDE, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Database Encryption Methods For Business Security. Use it as a tool for discussion and navigation on Database Encryption Methods, Business Security, Sales And Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Impact Of Encryption Implementation On Application Security
Encryption Implementation Strategies Impact Of Encryption Implementation On Application SecurityThis slide represents the various factors which showcase the improvement of application security after adopting encryption. The parameters discussed are data privacy, confidentiality, authentication, compliance, trust and reputation, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Impact Of Encryption Implementation On Application Security. Dispense information and present a thorough explanation of Confidentiality, Data Privacy, Trust And Reputation, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Key Components Of Internet Protocol Security
Encryption Implementation Strategies Key Components Of Internet Protocol SecurityThe purpose of this slide is to discuss the main components of internet protocol security IPsec architecture. These three components are encapsulating security payload ESP, authentication header AH, and internet key exchange IKE. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Key Components Of Internet Protocol Security. Dispense information and present a thorough explanation of Data Integrity, Encryption, Anti Replay, Payload Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Organizational Compliance Regulations For Information Security
Encryption Implementation Strategies Organizational Compliance Regulations For Information SecurityThe purpose of this slide is to summarize the most common regulations that organizations need to comply with, and their requirements. These regulations are HIPAA Health Insurance Portability and Accountability Act, SOX, PCI DSS, breach laws in all US states, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Organizational Compliance Regulations For Information Security. Use it as a tool for discussion and navigation on Health Insurance Portability, Accountability Act, Payment Card Industry, Data Security Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Secure Socket Layer SSL Security Technology
Encryption Implementation Strategies Secure Socket Layer SSL Security TechnologyThe purpose of this slide is to explain the role of HTTPS and the secure sockets layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake process. Present the topic in a bit more detail with this Encryption Implementation Strategies Secure Socket Layer SSL Security Technology. Use it as a tool for discussion and navigation on Secure Socket Layer, Security Technology, Symmetric And Asymmetric Encryption, Protocol For Secure Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Secure Socket Shell Encryption Protocol
Encryption Implementation Strategies Secure Socket Shell Encryption ProtocolThis slide represents the working process of SSH Secure Socket Shell protocol to secure data sharing between unsecured networks. This slide also illustrates the before and after scenario of using SSH protocol for data encryption. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Secure Socket Shell Encryption Protocol. Dispense information and present a thorough explanation of Secure Socket Shell, Encryption Protocol, Unsecured Networks, Protocol For Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Security Protocols Required According To Type Of Network
Encryption Implementation Strategies Security Protocols Required According To Type Of NetworkThe purpose of this slide is to outline different security protocols used in various types of networks, and their specific applications. These network types are wired, wireless networks, Local Area Networks LANs, Wide Area Networks WANs, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Security Protocols Required According To Type Of Network. Use it as a tool for discussion and navigation on Local Area Networks, Wide Area Networks, Wired Networks, Wireless Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections
Encryption Implementation Strategies Steps Followed By Internet Protocol Security ConnectionsThe purpose of this slide is to outline the working steps of internet protocol security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections. Use it as a tool for discussion and navigation on Protocol Security Connections, Packet Authentication, Encryption, Data Transmission, Decryption Of Data Packets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake
Encryption Implementation Strategies Transport Layer Security Implementation Using HandshakeThis slide discusses a cryptographic system known as transport layer security TLS. The purpose of this slide is to explain how TLS enables safe communication over computer networks using handshake protocol and record protocol. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Transport Layer Security Implementation Using Handshake. This template helps you present information on two stages. You can also present information on Transport Layer Security Implementation, Handshake And Record Protocol, Computer Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget To Implement Secure Access Service Edge Cloud Security Model
Budget To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Budget To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Implement, Network, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges And Solutions For SASE Implementation Cloud Security Model
Challenges And Solutions For SASE Implementation Cloud Security ModelThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Present the topic in a bit more detail with this Challenges And Solutions For SASE Implementation Cloud Security Model. Use it as a tool for discussion and navigation on Solutions, Implementation, Challenges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Secure Access Service Edge Cloud Security Model
Checklist To Implement Secure Access Service Edge Cloud Security ModelPresent the topic in a bit more detail with this Checklist To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Service, Access, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Implementation Models Cloud Security Model
Cloud Access Security Broker Implementation Models Cloud Security ModelThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Scanning, Forward, Reverse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap To Implement Secure Access Service Edge Cloud Security Model
Roadmap To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Discover, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Access Service Edge Implementation Steps Cloud Security Model
Secure Access Service Edge Implementation Steps Cloud Security ModelThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD WAN backbone, incorporating zero trust solutions, etc. Introducing Secure Access Service Edge Implementation Steps Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Requirements, Solutions, Optimize, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.





