Powerpoint Templates and Google slides for Security Functions
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Hotel Security And Safety Department Functional Areas Training Ppt
Hotel Security And Safety Department Functional Areas Training PptPresenting Hotel Security and Safety Department Functional Areas. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizablealter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway SWG Functional Components Cloud Security Model
Secure Web Gateway SWG Functional Components Cloud Security ModelThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Secure Web Gateway SWG Functional Components Cloud Security Model. Use it as a tool for discussion and navigation on Components, Prevention, Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Secure Web Gateway Swg Functional Components
Sase Security Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Sase Security Secure Web Gateway Swg Functional Components. Use it as a tool for discussion and navigation on Functional, Components, Enforcement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Swg Functional Components Secure Access Service Edge Sase
Secure Swg Functional Components Secure Access Service Edge SaseThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this Secure Swg Functional Components Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Demonstrate, Enforcement, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway SWG Functional Components SASE Network Security
Secure Web Gateway SWG Functional Components SASE Network SecurityThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Secure Web Gateway SWG Functional Components SASE Network Security. Use it as a tool for discussion and navigation on Policy, Prevention, Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Working Functions Of Cloud Firewall System
Firewall Network Security Working Functions Of Cloud Firewall SystemThis slide talks about the different working functions that help cloud-based firewall systems to protect the user network and devices from malicious activities. The purpose of this slide is to showcase the various tasks of cloud firewalls, including packet filtering, stateful inspection, and proxy service. Introducing Firewall Network Security Working Functions Of Cloud Firewall System to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Stateful Inspection, Proxy Service, Packet Filtering using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Application Awareness Function In Next Generation Firewalls
Firewall Network Security Application Awareness Function In Next Generation FirewallsThis slide provides an overview of the application awareness function of Next Generation Firewalls. The purpose of this slide is to showcase how Next Generation Firewalls detect malicious content within the approved application packets through the DPI mechanism. Introducing Firewall Network Security Application Awareness Function In Next Generation Firewalls to increase your presentation threshold. Encompassed with Ten stages, this template is a great option to educate and entice your audience. Dispence information on App Packets, Malicious Code, Trusted Apps using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Different Firewall Types And Their Functions
Firewall Network Security Different Firewall Types And Their FunctionsThis slide outlines the various types of firewalls, including their functions. The purpose of this slide is to showcase the different firewall types, such as packet layer, proxy server, circuit level, application level, and software firewalls. Introducing Firewall Network Security Different Firewall Types And Their Functions to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Packet Layer, Proxy Server, Circuit Level using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Importance And Functions Of Firewall Network Security
Firewall Network Security Importance And Functions Of Firewall Network SecurityThis slide outlines the importance and functions performed by a firewall to protect a network. The purpose of this slide is to showcase the importance of a firewall by listing different features of it and functions performed by a firewall in a network, such as establishing a boundary, investigation, etc. Deliver an outstanding presentation on the topic using this Firewall Network Security Importance And Functions Of Firewall Network Security Dispense information and present a thorough explanation of Monitoring Network Traffic, Promotes Privacy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security IP Internet Protocol Reputation Function In NGFW
Firewall Network Security IP Internet Protocol Reputation Function In NGFWThis slide outlines the overview of the IP Reputation function used in Next Generation Firewalls. The purpose of this slide is to introduce the Internet Protocol IP reputation, including its features and limitations. This function blocks network traffic based on the reputation score of Ips. Introducing Firewall Network Security IP Internet Protocol Reputation Function In NGFW to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Network Visibility, Streamlined Adaptability using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Web Gateway Swg Functional Components
SD WAN Model Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Web Gateway Swg Functional Components. Dispense information and present a thorough explanation of Data Loss Prevention, Policy Enforcement, Secure Web Gateway, Functional Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Web Gateway SWG Functional Components
Sase Model Secure Web Gateway SWG Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Sase Model Secure Web Gateway SWG Functional Components. Use it as a tool for discussion and navigation on Components, Working, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Introducing Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Size Of Blockchain, Addition Blocks, Data Transmission, using this template. Grab it now to reap its full benefits.
-
 Variations And Functions Of Infrastructure Security System
Variations And Functions Of Infrastructure Security SystemThis slide showcases the implementation of various infrastructure security system. Its aim is to maintain function successfully and efficiently. This slide includes access control, application security, behavioural analytics, firewall and virtual private network. Introducing our premium set of slides with Variations And Functions Of Infrastructure Security System. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Sensitive, Security, Analytics. So download instantly and tailor it with your information.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Function Activities In Cyber Security Framework
Identify Function Activities In Cyber Security FrameworkThis slide is an introduction to the key activities of identify function in cyber security framework which includes identify physical and software assets. Increase audience engagement and knowledge by dispensing information using Identify Function Activities In Cyber Security Framework. This template helps you present information on five stages. You can also present information on Identify Physical And Software Assets, Assess Asset Vulnerabilities, Conduct Risk Response Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
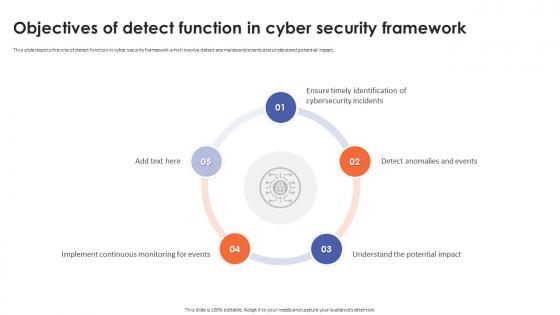 Objectives Of Detect Function In Cyber Security Framework
Objectives Of Detect Function In Cyber Security FrameworkThis slide depicts the role of detect function in cyber security framework which involve detect anomalies and events and understand potential impact. Introducing Objectives Of Detect Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Continuous Monitoring For Events, Understand The Potential Impact, Detect Anomalies And Events, using this template. Grab it now to reap its full benefits.
-
 Purpose Of Response Function In Cyber Security Framework
Purpose Of Response Function In Cyber Security FrameworkThis slide highlights the functions of response in cyber security framework which includes execute response plans, manage communications, analyze incidents, etc. Introducing Purpose Of Response Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Event Expansion, Coordinate Communications, Cyber Security Framework, using this template. Grab it now to reap its full benefits.
-
 Recovery Function In Cyber Security Framework
Recovery Function In Cyber Security FrameworkThis slide gives an overview of role of recovery function which includes implement recovery plans, improve strategies and coordinate communications. Increase audience engagement and knowledge by dispensing information using Recovery Function In Cyber Security Framework. This template helps you present information on four stages. You can also present information on Coordinate Communications, Implement Recovery Plans, Cyber Security Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Protect Function In Cyber Security Framework
Role Of Protect Function In Cyber Security FrameworkThis slide gives an outline of role of protect function in cyber security framework which controls identity management and secure resources. Introducing Role Of Protect Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness Training, Data Security With Risk Strategy, Maintain Information System Protections, using this template. Grab it now to reap its full benefits.
-
 Vital Functions Of Cyber Security Framework
Vital Functions Of Cyber Security FrameworkThis slide gives an overview of the vital functions of cyber security framework which includes identify, protect, detect and respond. Introducing Vital Functions Of Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Recognizes Cybersecurity Incidents, Potential Threats, Structured Cybersecurity Approach, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Functions Of Firewall In Endpoint Security Solutions
Endpoint Security Functions Of Firewall In Endpoint Security SolutionsThis slide represents the objectives of second component of endpoint security that is firewall which is used to monitor traffic of devices. Increase audience engagement and knowledge by dispensing information using Endpoint Security Functions Of Firewall In Endpoint Security Solutions. This template helps you present information on six stages. You can also present information on Decides Traffic Allowance, Creates Network Barrier, Applies Security Rules, Monitors Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functionality Of Endpoint Cyber Security Solutions
Functionality Of Endpoint Cyber Security SolutionsThis slide presents core functions of cyber security solutions for ensuring endpoint protection. The purpose of this slide is to help businesses in ensuring digital security through threat intelligence and endpoint cyber protection. It covers functions such as prevention, detection, threat intelligence integration, etc. Presenting our well structured Functionality Of Endpoint Cyber Security Solutions The topics discussed in this slide are Threat Hunting, Threat Intelligence Integration, Prevention This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Functions Performed By Hids Cyber Security In Devices
Functions Performed By Hids Cyber Security In DevicesThis slide represents functions performed by HIDS cyber security which assists to detect suspicious activity which can cause damage to system network. It includes functions performed by HIDS cyber security in devices such as evaluate traffic, threat intelligence, etc Presenting our set of slides with Functions Performed By Hids Cyber Security In Devices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Traffic, Signature Based Detection, Threat Intelligence .
-
 Physical Security Control Methods And Its Functions
Physical Security Control Methods And Its FunctionsThis slide showcases security control system types that are physical, technical and administrative controls. These help to prevent unauthorized access, maintain confidentiality, etc. Introducing our premium set of slides with Physical Security Control Methods And Its Functions. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Controls, Technical Controls, Administrative Controls. So download instantly and tailor it with your information.
-
 Applications Of SIEM Cyber Security With Functions
Applications Of SIEM Cyber Security With FunctionsThis slide showcases the applicational theory of SIEM cyber security. Its aim is to collect and normalise and prove SIEM capabilities. This slide includes collection, normalisation, enrichment, correlation, etc. Introducing our Applications Of SIEM Cyber Security With Functions set of slides. The topics discussed in these slides are Collection, Enrichment, Correlation . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Functions Of Identity And Access Management Process Securing Systems With Identity
Functions Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management process functions. The purpose of this slide is to highlight the various functions, including identification in the system, roles in the design, assigning access levels, protecting sensitive data, and so on. Introducing Functions Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification In System, Roles In System using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Introduction And Functions Securing Systems With Identity
Identity And Access Management Introduction And Functions Securing Systems With IdentityThis slide gives an overview of the Identity and Access Management process. The purpose of this slide is to explain the IAM and its functions in ensuring authentication, reporting, authorization, workflow, access management, and so on. Introducing Identity And Access Management Introduction And Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Company Data And Resources, Streamline Workflows using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Features And Functionalities Offered By Email Security Tools
Email Security Best Practices Features And Functionalities Offered By Email Security ToolsThis slide represents the properties and tasks performed by email security tools. The functionalities discussed in this slide are malware and antivirus, spam and phishing detection, email encryption, anti-spoofing, data loss prevention, etc. Introducing Email Security Best Practices Features And Functionalities Offered By Email Security Tools to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Reporting And Analytics, Data Loss Prevention, Anti-Spoofing, Email Encryption, using this template. Grab it now to reap its full benefits.
-
 Security functions outsourced ppt powerpoint presentation layouts design templates cpb
Security functions outsourced ppt powerpoint presentation layouts design templates cpbPresenting our Security Functions Outsourced Ppt Powerpoint Presentation Layouts Design Templates Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Functions Outsourced. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Outsource security functions ppt powerpoint presentation gallery influencers cpb
Outsource security functions ppt powerpoint presentation gallery influencers cpbPresenting Outsource Security Functions Ppt Powerpoint Presentation Gallery Influencers Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Outsource Security Functions. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Addressing critical business functions recovery priorities corporate security management
Addressing critical business functions recovery priorities corporate security managementThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Introducing Addressing Critical Business Functions Recovery Priorities Corporate Security Management to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Addressing Critical Business Functions Recovery Priorities, using this template. Grab it now to reap its full benefits.
-
 Corporate security management ensuring collaboration among various functional areas
Corporate security management ensuring collaboration among various functional areasThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Ensuring Collaboration Among Various Functional Areas. This template helps you present information on three stages. You can also present information on Plan And Collet, Review And Analyze, Develop Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring collaboration among various functional corporate security management
Ensuring collaboration among various functional corporate security managementThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Increase audience engagement and knowledge by dispensing information using Ensuring Collaboration Among Various Functional Corporate Security Management. This template helps you present information on ten stages. You can also present information on Data Privacy, Internal Communication, External Communication, Business Continuity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management addressing critical business functions recovery priorities
Cyber security risk management addressing critical business functions recovery prioritiesThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Addressing Critical Business Functions Recovery Priorities. This template helps you present information on two stages. You can also present information on Priorities, Department, Maximum Allowable Downtime, Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring collaboration among various functional areas cyber security risk management
Ensuring collaboration among various functional areas cyber security risk managementThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Functional Areas Cyber Security Risk Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Legal, Compliance, Public Relations, Human Resources, Procurement, Board And Risk Committee, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan critical business functions recovery priorities
Building organizational security strategy plan critical business functions recovery prioritiesAfter the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Critical Business Functions Recovery Priorities. Use it as a tool for discussion and navigation on Information, Business, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functional Chart Of Cyber Security Team Building A Security Awareness Program
Functional Chart Of Cyber Security Team Building A Security Awareness ProgramThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Present the topic in a bit more detail with this Functional Chart Of Cyber Security Team Building A Security Awareness Program. Use it as a tool for discussion and navigation on Security Operations, Threat Intelligence, Cyber Business Liaison. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
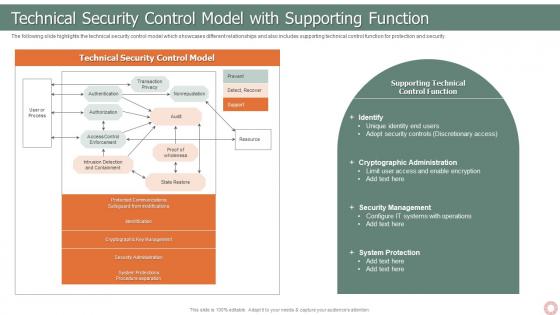 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Technical Security Control Model With Supporting Function
Enterprise Risk Management Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing Enterprise Risk Management Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Cryptographic Administration, Security Management, System Protection, using this template. Grab it now to reap its full benefits.
-
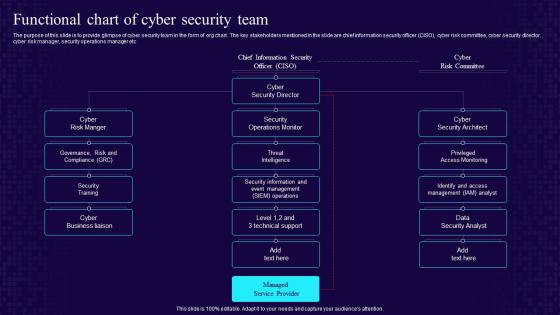 Functional Chart Of Cyber Security Team Developing Cyber Security Awareness Training Program For Staff
Functional Chart Of Cyber Security Team Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Increase audience engagement and knowledge by dispensing information using Functional Chart Of Cyber Security Team Developing Cyber Security Awareness Training Program For Staff. This template helps you present information on seven stages. You can also present information on Compliance, Security Training, Cyber Business Liaison, Security Operations Monitor using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Architecture In 5G Technology Architecture And Functioning Of 5G
Security Architecture In 5G Technology Architecture And Functioning Of 5GThis slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Deliver an outstanding presentation on the topic using this Security Architecture In 5G Technology Architecture And Functioning Of 5G. Dispense information and present a thorough explanation of User ID Administration, Apps And Cloud Infrastructure, Access And Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security In 5G Technology Architecture Architecture And Functioning Of 5G
Security In 5G Technology Architecture Architecture And Functioning Of 5GThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Present the topic in a bit more detail with this Security In 5G Technology Architecture Architecture And Functioning Of 5G. Use it as a tool for discussion and navigation on Service Delivery Process, Mobile Technologys, Security Procedures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functional Chart Of Cyber Security Team Conducting Security Awareness
Functional Chart Of Cyber Security Team Conducting Security AwarenessThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Deliver an outstanding presentation on the topic using this Functional Chart Of Cyber Security Team Conducting Security Awareness. Dispense information and present a thorough explanation of Cyber Risk Manger, Security Training, Cyber Business Liaison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
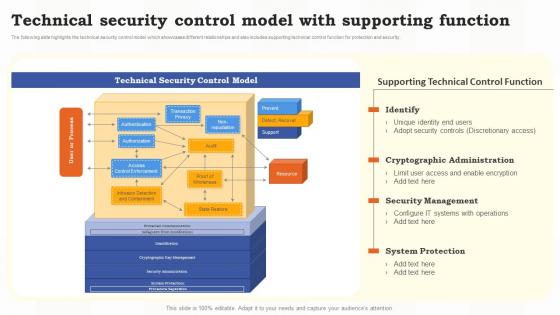 Technical Security Control Model With Supporting Function Risk Assessment Of It Systems
Technical Security Control Model With Supporting Function Risk Assessment Of It SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Supporting Function Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Technical, Security Management, System Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation Tools With Functions And Cost
Security Automation Tools With Functions And CostThe following slide highlights various tools that can assist company to automate security process. The various tools could be Robotic process automation security orchestration, automation and response and extended detection Introducing our premium set of slides with Security Automation Tools With Functions And Cost. Elucidate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Expected Cost, Key Functions. So download instantly and tailor it with your information.
-
 Functional Chart Of Cyber Security Team Implementing Security Awareness Training
Functional Chart Of Cyber Security Team Implementing Security Awareness TrainingThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Present the topic in a bit more detail with this Functional Chart Of Cyber Security Team Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Cyber Risk Manger, Security Operations Monitor, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring Retail Store Functions Strategies To Enhance Retail Store Security
Measuring Retail Store Functions Strategies To Enhance Retail Store SecurityThis slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. Introducing Measuring Retail Store Functions Strategies To Enhance Retail Store Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Utilizes Electronic, Article Surveillance, Install Monitored Alarms, using this template. Grab it now to reap its full benefits.
-
 Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber Security
Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Deliver an outstanding presentation on the topic using this Functional Chart Of Cyber Security Team Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Cyber Risk Manger, Security Training, Cyber Business Liaison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs Download
Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs DownloadThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs Download. This template helps you present information on five stages. You can also present information on Technology, Architecture, Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Secure Web Gateway SWG Functional Components Ppt Powerpoint Demonstration
SASE IT Secure Web Gateway SWG Functional Components Ppt Powerpoint DemonstrationThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this SASE IT Secure Web Gateway SWG Functional Components Ppt Powerpoint Demonstration. Dispense information and present a thorough explanation of Web Proxy, Traffic Inspection, Web Proxy, Malware Detection, Policy Enforcement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Core Team Members Associated With It Functional Strategic Plan To Secure It Infrastructure Strategy SS V
Core Team Members Associated With It Functional Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding core team members of IT functional areas un terms of VP for application, enterprise architecture, and creative. Other members include directors, etc. Increase audience engagement and knowledge by dispensing information using Core Team Members Associated With It Functional Strategic Plan To Secure It Infrastructure Strategy SS V. This template helps you present information on nine stages. You can also present information on Associated, Operations, Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
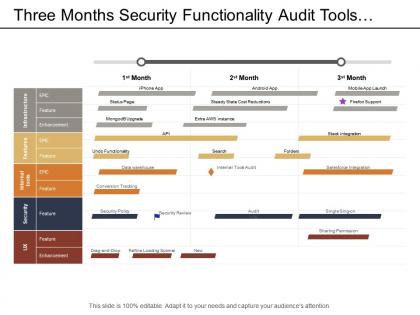 Three months security functionality audit tools development timeline
Three months security functionality audit tools development timelinePresenting this set of slides with name - Three Months Security Functionality Audit Tools Development Timeline. This is a three stage process. The stages in this process are Development Timeline, Development Roadmap, Production Timeline.
-
 Mobile testing application with security and functional
Mobile testing application with security and functionalPresenting this set of slides with name Mobile Testing Application With Security And Functional. This is a eight stage process. The stages in this process are Application, Financial Segment, Performance Testing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Non functional requirements security ppt powerpoint presentation model layout ideas cpb
Non functional requirements security ppt powerpoint presentation model layout ideas cpbPresenting this set of slides with name Non Functional Requirements Security Ppt Powerpoint Presentation Model Layout Ideas Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Non Functional Requirements Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security strategies five year functional roadmap
Security strategies five year functional roadmapPresenting Security Strategies Five Year Functional Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Security strategies four quarter functional roadmap
Security strategies four quarter functional roadmapPresenting Security Strategies Four Quarter Functional Roadmap PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Security strategies half yearly functional roadmap
Security strategies half yearly functional roadmapPresenting Security Strategies Half Yearly Functional Roadmap PowerPoint slide which is percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.




